Friends On Facebook Writing About Fraudulent Transactions In Their Bank Accounts
Here’s what you need to do to protect yourself
This is a free post — no paywall. If you want to keep reading my other related posts you might need a subscription but hopefully the $5 per month will be worth it to read not must my stories but everyone else’s!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Data Breaches | Home Network Security | OS & IoT Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I’ve been reading about a lot of people’s financial accounts getting hacked on Facebook. One of my friends had hackers in his using his debit or credit card. He changed all his bank accounts. He got a new phone. Just as he finished that process, someone was in his bank account again!
What’s happening?
Well, the attackers have access somewhere in his systems and getting a new phone was not enough to stop it. Whatever caused this breach is not gone. The attackers are still in the systems. I’ll explain the likely culprits and how to eject the unwanted inhabitants, and how to protect yourself even if they are still there in some cases.
Another person said she changed her IP address and that stopped it. Well, I can tell you right now that’s not enough to stop an attack. It may have temporarily kicked malware off the system (even just restarting your network equipment or web browser might do that) but whatever allowed them get into systems in the first place is likely still there. They will be back if the vulnerability that allowed them to get into the systems hasn’t been fixed, and changing an IP address doesn’t fix it.
I wrote about how attackers scan the Internet looking for vulnerable systems here:
Scanners lead to scammers
Sources of unrequested network traffic from the past few months
medium.com
What can you do?!?! It seems impossible right? Well, I’m going to tell you what you need to do but first I’m going to tell you how the most common attacks work so you understand what does and does not fix the problem.
Report the Crime
Before I get into the technical details, if you’re not that technical the very least you can do is report the crime. Once people who deal with these types of crimes at the FBI and elsewhere they will investigate and try to fix the problem.
The types of crimes to report here generally involve monetary loss due to something on the Internet — a website, your phone was hacked, malware got downloaded onto your computer, money was stolen from your bank account, and so on.
How attackers steal your login credentials even when you use MFA
You know how some websites allow you to add your phone number and when you login, they text you a code and then you use that code to log into something? That is called Multi-Factor Authentication (MFA). It is supposed to make it harder to steal access to your account and it does help — especially if you are logging in on your laptop and getting the code from your phone. The attackers may have infected one device or the other but don’t have access to both. But it’s not foolproof. Here’s when it doesn’t work:
Attackers got malware onto your laptop because you are running some outdated software. They installed a key logger and can read everything you type — like your credentials and codes when you enter them on a website. That’s what happened in a recent Lastpass breach. Once on your system, they may be able to read any passwords in your password manager as well, if you use one.
Attackers got malware on your phone and you log into everything and get codes on your phone. The problem is that if you login and get the code on the same device (your phone) and the attacker has malware on your phone that extra step isn’t helping that much.
They hack the phone company or another company that transmits the codes to you. They get the code as it’s traversing the network. That’s what they did to get into some Signal accounts people use for secure messaging when Twillio was hacked. I wrote about that here:
They hack your home router if the code is coming to you over your wifi network. Attackers have been hacking into home networking equipment for years and using them to carry out attacks. The FBI recently removed more Chinese malware off a number of routers. I wrote bout that topic here:
They trick you into visiting an evil website that looks like the legitimate website. There is some software out there that creates login pages that look like the legitimate pages you normally log into. You give the attackers your credentials when you login and then they send off to the legitimate website so you never know it happened. In this case, the URL that you log into will be slightly different than the one you should log into in most places.
They perform some kind of attack where they get between you and the server you’re logging into. Once they do that they can read all your data and any codes or credentials you are sending back and forth to login. That’s called a man-in-the-middle attack and I wrote about that here.
Attackers compromise your phone via sim-swapping or a stolen e-sim. If you use your phone to get MFA codes attackers might try to perform sim-swapping by going into a store, saying they need a phone, and trying to get the clerk in the store to give them your phone number on a new phone with a new sim card. Laws may be enacted soon to help prevent this. In some cases vendors are starting to use software instead of hardware SIM cards in cell phones. Attackers are finding ways to attack those too.
In all of the above the key point is the attackers can steal your credentials and your MFA code using the above tactics.
Get Hardware MFA wherever possible — especially for your email
Here’s the first and best thing you can do for every account that supports it — and unfortunately most banks do not. Add hardware MFA to any account you can. The device I trust most at the moment is a Yubikey — and I very, very, very rarely recommend products. I am not getting paid for this. I don’t even know a single person that works for the company.
A Yubikey is a device that you plug into your computer or phone. You log into a website. After you enter your user name and password, you have to push a button on the device to get into the site. I’m sure hackers will find a way to compromise these too but for the moment, this is your very best defense against someone getting into your accounts with a stolen password.

This severely limits the ways the attacker can access the second factor you use to log into websites. It’s not foolproof but it helps. A lot.
But what if I lose it?
Some sites will allow you to set up multiple devices on your account. You use one and put the other in a safe.
Worst case, you can leave the phone number on your account as a backup but only use it in case of emergency.
The biggest problem is this: Most financial vendors still do not support Yubikeys. But most email providers do and one of the ways to break into accounts is by getting into your email and resetting passwords. So definitely use these devices on your email accounts.
Best bet — restore the system from factory default
If you have a problem with a system your best bet is to restore the system to factory default and start over. Once the attackers have a foothold it’s very hard to ensure you got every bit of malware off the system and they won’t be back. I wrote about how that fixed my husband’s slow iPhone here.
Set a strong password
When you restore your system make sure you set a new, strong password. If you reset your router but don’t change the password to something other than the default — then you might just be letting the attackers right back in. Anyone can look up default passwords for older routers on the Internet. Attackers can tell what router version and model you’re running most of the time just by scanning it as I explained above in my post about scanners that lead to scammers.
Don’t reinstall what’s infected
When you restore your system make sure you aren’t just reinstalling whatever is infected. I wrote about how I searched for malware on one of my Apple computers that got infected here. If you reinstall Google Chrome it will re-download anything in your profile, including any infected extensions. If you reinstall the vulnerable software that let the attackers in originally, or redownload a file that’s been infected with malware, you’ll have the same problem all over again. Consider limiting what you reinstall.
By the way, if you use an Apple computer, this post has tips for checking to see if malware is on your system, as do some of the related posts, and how to check for configurations that allow access.
A similar approach would apply to Windows and other operating systems.
Make sure all your software is up to date
Sometimes there’s an attack you can’t stop. The vendor has to fix their software. Today, Apple is releasing a big security update for vulnerabilities in iPhone software that has been recently exploited. Make sure you always run the latest software. If you’re not highly technical and don’t want to monitor your network traffic, that’s the best thing you can do.
For any software you run — including all the applications on your phone, your computer, all the “things” that connect to your network in your house like your TV, thermostat, doorbell, and so on — make sure it is running the latest version. This also includes your networking equipment like the device you got from your Internet provider to connect to their network and the device that runs the wifi in your home.
What happens is that security researchers such as myself inspect systems and software and find bugs or vulnerabilities in the software that allow attackers to break in. Or…an attacker exploited something in a system and someone discovered that and figured out how they did it. Then, the vendor fixes the problem and assigns it what is called a “CVE number.” They send the software to you and they may include information about which CVEs were fixed in the update. You can read about CVEs here:
You want to get all your systems updated with any fixes available from the vendor as soon as possible.
An example — checking to see if the software on an Apple Macintosh computer is up to date
Check what the latest version of your software is for your device if you want to make sure you’ve got the latest version when something seems off. I’ve had scenarios where my software didn’t update even though it said it did.
You can read what’s in the latest updates here for Sonoma.
Note that some older hardware won’t let you install the latest version. That’s when it’s a good time to update your hardware, unfortunately. Hardware sometimes has security bugs too. If you are running very outdated networking equipment in your home, it may be time to update it.
Click on the Apple icon in the top left.
Click About This Mac from the menu.
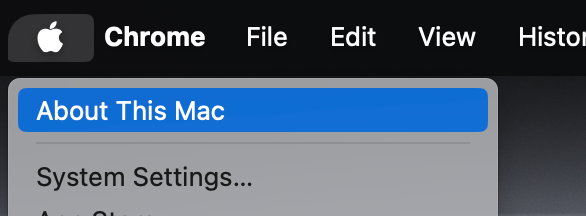
Note the current version on the screen.
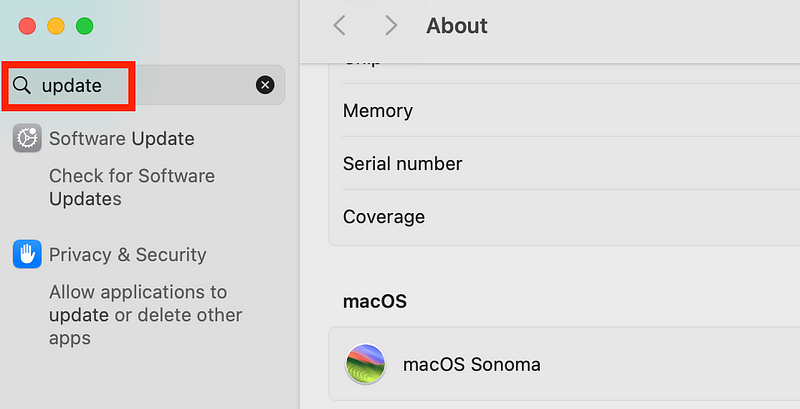
Click More Info…

Search for update.
Note that most other software you use has a similar feature to search for the update process.
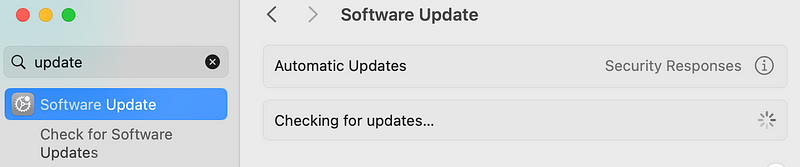
Click on Software Update. Your system will check for updates and if there are any, you can install them from here.
Almost every device you own that runs software has a process similar to this. I would highly, highly recommend you make sure the software for the following is up to date:
- Your router, modem and wifi devices
- Any operating systems (Windows or Apple software running on your computer)
- All your phones (including the kids — everything is connected!)
- All your web browsers (Google Chrome, Safari, Mozilla Firefox, or anything else you use to surf the web).
Get into the habit of checking to see if your software is up to date once a month if you can. If you have the option to automatically install updates its a good idea to enable that.
Are you a bit techy? Consider installing a more secure home network
If you are a bit techy one of the best things you can do is to install a more secure home network.
Learn how to run a firewall on your laptop. The software you run like Windows or your Apple operating system come with a firewall. Turn it on and configure it. I also use something called Little Snitch on my Mac but I don’t use all the features. I only use the firewall.
I have posts explaining how to do that here:
Do you run a business?
If you run a business consider having someone come in and run what is called a vulnerability scan on your network to see if they are secure. That’s something I offer through my business.
https://2ndsightlab.com/network-security-scan.html
There are other types of scans that can scan individual systems with agents running on the machine to inspect the software.
If you run a website there are ways to test that too including a simple scan:
https://2ndsightlab.com/web-application-scan.html
Or a more advanced penetration test:
https://2ndsightlab.com/cloud-penetration-testing.html
Those vulnerabilities are how the attackers get into the systems in the first place. Finding them and getting recommendations to help get them fixed can help prevent access to your systems and data.
If you liked this post you may also be interested in these:
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
