Investigating, Containing, and Removing Malware on a Mac
A very basic explanation of incident response and digital forensics — Do as I say not as I do
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Apple Mac Security | Network Security | Data Breaches
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Let me start by saying this is not the correct way to do incident response and digital forensics exactly. I could risk infecting my entire network and everything on it the way I’m doing this but I’ve got a fairly tight network. I have a separate more restrictive network for my work that is separate from the other parts of my network.
And hey, I live life on the edge. And in the cloud. Almost everything I have is in the cloud so if I do something bad on this laptop I’ll just rebuild it. Which I plan to do anyway. Also, the particular item I’m researching actually failed to connect.
I am also going to preface this post with that although I am certified in incident response and digital forensics and reverse engineering malware, I’m not going through all those steps completely below. But I’ll explain how it would work and point you in the right direction.
This is not what I wanted to do for the past two days but since the “opportunity” presented itself I thought I would look into it.
The other thing is, when I faced my first breach back when I had an e-commerce business, I became a Windows expert. I knew all the ins and outs of Windows and exactly which services did not did not need to be running and how to set every setting. Then I moved to Mac. And Windows changed and I’ve been so busy with other things that I wouldn’t consider myself a Mac expert.
But this post will help. I dug through a bunch of things and figured them out. Still more to do but I have a lot more knowledge than when I started.
Along the way you’ll get a lot of things you can check on your own Mac if you use one to see if it has been compromised or lock it down if it has not been.
I apologize in advance for the stream of consciousness because I already spent too much time on this — and the typos. I’m not going to log back into my Google account at the moment to spell check. Just going to wipe the machine and move on.
How did this happen?
I have a pretty new computer I haven’t used much. I wrote a start up script to disable a bunch of things on a Mac but hadn’t gotten around to installing it yet. Lesson learned.
I configure the script here:
And added to it here:
And after this little run-in with maliciousness I’m going to add a few more things below.
The other thing is…well…it got sunny here. The first couple sunny days and I wanted to work outside and I was lazy. I used my mobile hotspot device instead of my private network. Yep. That’s all it took. Luckily I also run a host-based firewall but normally my other firewall blocks a whole bunch of known bad networks I never connect to — like things in Asia where Alibaba is mostly located. That connection to Alibaba is what tipped me off, and the fact that the process looked suspicious. More on that below.
Incident Response and Digital Forensics For Real
I just have a little company and one server with not much on it, but it does have access if and when I’m logged in and my cloud systems are logged in to things I’d like to protect. But I can see the attacker’s didn’t get very far. Except that depending on what they did they might have accessed some passwords.
Luckily I have MFA on most everything — but if the attackers got into a process on my browser there’s a chance they could read passwords and get access to active sessions while I log in. I’m going to have to go through the process of resetting all my passwords just to be safe.
If I were in a larger company there would be a whole lot of other steps like dealing with legal to report the breach to any required jurisdictions. Working with your public relations team to talking to the news media if and when appropriate. Interacting with law enforcement if applicable. You would probably have a plan for how to do all that before this incident ever occurred and then you’d follow your plan to handle the incident appropriately.
The first thing I did was further lock down the machine from the network. If you are not well versed in the rest go ahead and just wipe the machine and start over from scratch. That is the best thing to do. Factory reset. Do not re-download any files potentially containing malware back to your machine.
If this were a real incident, I should first make a forensic image of this laptop and then put that image in a VM and do all my investigation from there. I should take constant backups as I’m making each change so if the malware gets loose and destroys my image I can go back to the previous backup.
I don’t do this for a living, nor do I want to, and they never trained us how to do that with Macs in the classes I took. The classes only taught Windows. And I don’t want to spend an eternity here. You can search for how to perform a forensic image of a Mac laptop on Google and if I wanted to spend enough time doing that I would figure it out. But I don’t. I know some people who do this for a living if you need help.
I didn’t watch this video but I presume it would help. It’s two years old so there may be updated information.
So this is my quick and not really safe means of checking out what is going on with this weird thing I found in my firewall logs that leads me to suspect my system may have possibly been compromised — but not completely I hope.
What tipped me off that something was gong on
What tipped me off to this problem was a strange process trying to connect to the Alibaba CDN. I don’t use Alibaba so this was strange. Also I noticed it because I was looking for the Google Update process in my list and I couldn’t find it. I only slaw this weird processes, supposedly for Chrome.
Why would a Chrome process be accessing? They don’t. This is something pretending to be a Google process.
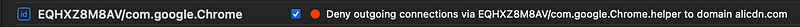
I see the Google Chrome process separately connecting to a zillion things (redacted here). Every web page I visit appears in this other list.
Firewall and Network Inspection
I looked at packet captures both on my firewall and localhost for anything suspicious and further locked things down to only what was required to review this incident.
I noticed my local firewall settings were different. I disallow any traffic on the local network to or from my laptop except traffic to and from the device it needs to connect to in order to get to connect to the Internet and only on required ports (67/68 for DHCP and an admin port).
Somehow those settings were different on this machine. Did I forget to set them after the last refresh or did they get changed? Not sure. I set them back.
Well as you will see a lot of things were different than I originally set them.
Unfortunately some logs were also deleted so I couldn’t tell exactly what happened.
Some general inspection of the details of the process and connection
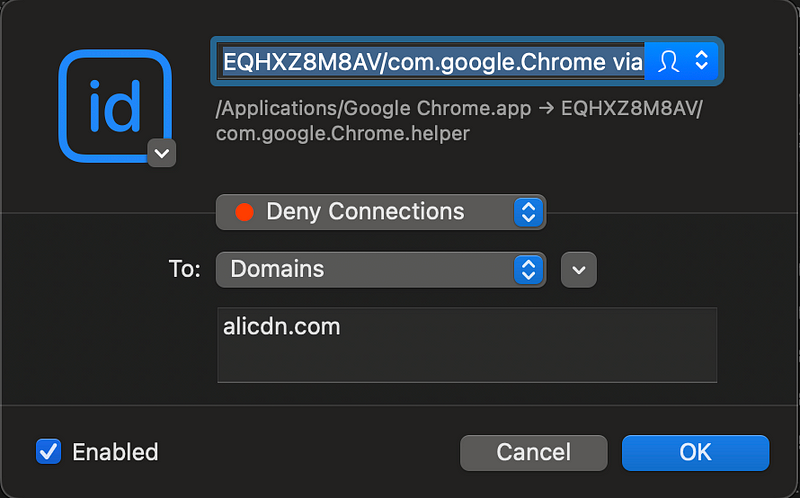
When I pull up the details of the above process connection I see this:
What is that logo? I try using Google to search for related images.
I couldn’t find that logo and I tried adding keywords to refine my search.
So is the generative AI helpful? Um no.
It appears this has something to do with Chrome because it’s associated with the Google Chrome Application folder. I can take a look at that:
So here’s where I had to do some digging because I am not a Mac developer or expert.
What does this arrow mean and what are those gobbledegook letters? is that a subprocess?
I tried searching around for an answer to that question and did not find one initially.
I looked around a bit but didn’t see that particular helper file inside that folder.
I searched and did not find a file:
sudo find / EQHXZ8M8AV | grep EQHXZ8M8AV
I didn’t find any processes with that name.

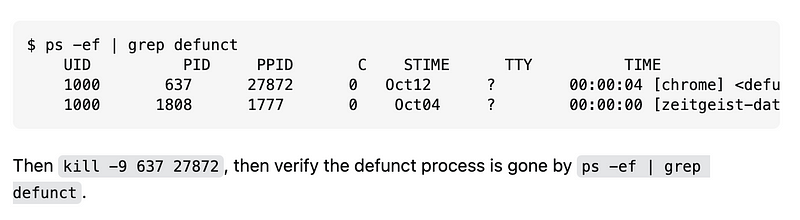
Side note: How to kill defunct processes
I did notice some
I used the guidance in this post to kill those processes and ended up killing Chrome three times before they went away.
Specifically this part of the post:
Turned off httpd service
One thing I noticed which I don’t believe was running before was the httpd process (in other words a web server.) WHAT? I never want a web server running on my laptop.
Now there are some things that require a webserver. Zoom used to run one and I don’t know if it still does, but that’s one of many reasons why I don’t want to run Zoom on my development workstation. I also used a program called Camtasia on a computer that required an http server, but that’s never been run on this laptop. So why is that running and is it expected? Not sure but it’s not running anymore.
I ran this command to terminate it:
sudo launchctl unload -w /System/Library/LaunchDaemons/org.apache.httpd.plistAnd added it to my Mac startup script:
And by the way Google got much faster after I did that.
Understanding Chrome helper
What is com.google.Chrome.helper anyway?
Oh here we go:
“Google Chrome Helper” is the generic name for embedded content that runs outside the browser. Browser plug-ins aren’t features that are rendered by HTML code; they involve content that needs to be pulled in from elsewhere. The “Google Chrome Helper” is the interface between the embed code in the browser and a remote server, and it’s set to run automatically with Chrome’s default settings. In many cases, the plug-ins and processes they’re handling aren’t listed by name because the APIs don’t allow it. Google Chrome Helper is a martyr.
I’m not using any plugins or extensions. So how does that work.
Checking some Chrome settings
That post is old and doesn’t match my version of Chrome. I went into settings and searched for advanced.
It led me to security and privacy where I noticed somehow this setting got turned off. This was on before.
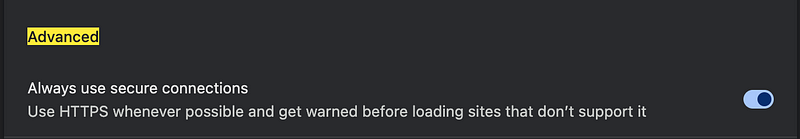
And this was off. No Google I don’t want you reading my passwords but thanks anyway.
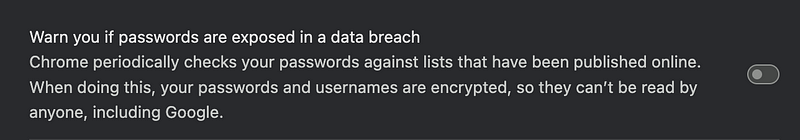
Nothing here about plugins. I also searched for plugins.
In addition I don’t have any extensions installed.
Checking Activity Monitor for clues
There’s another place I can look to see what processes are running on my Mac. I head over to Activity Monitor.
On the network tab I can sort by which program is sending and receiving the most data:
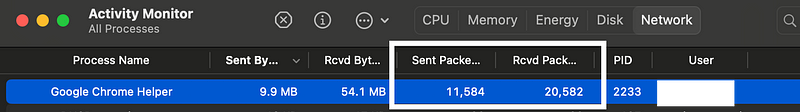
On the CPU tab I can see which processes are using the most CPU or threads.

On the memory tab we can see which programs are using the most memory.
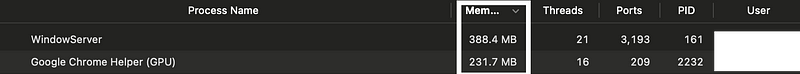
There’s our Google Chrome Helper. It’s highest on both the Memory tab and the Network tab. There’s another useful piece of information — the PID.
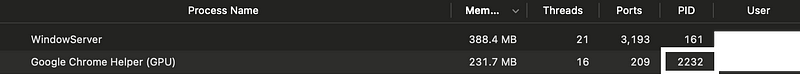
Using the ps command to get information about the PID
We can try to get some other information about that PID.

Interesting. Ok so what does that even mean.
Well because there’s a couple of equal signs at the end I’m going to guess that is encoded data that I can decode. I explained that in my book. I’m going to copy the encoded contents into a file that is *not executable*.
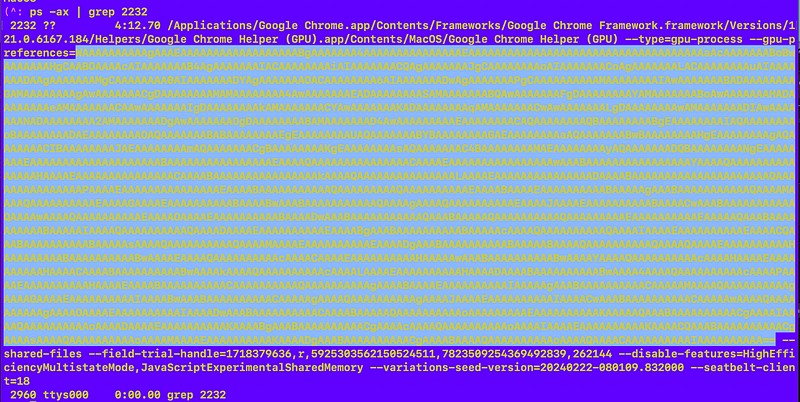
Didn’t work.

OK next I try killing the process. It restarts, and I look at it again. Now it looks different:
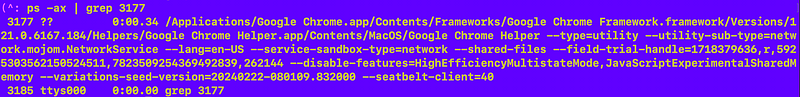
I now we might be getting somewhere. This site explains process injection with Google Chrome:
I found it searching for this in the information above: network.mojom.NetworkService
Once a process named
chrome.exeis found its process id will be passed to theIsNetworkProcfunction which will determine if it is actually the network service. This is done by using theNtQueryInformationProcesssyscall to get the address of the process environment block (PEB) in the remote process and then walk the PEB until it finds the command line arguments the process was launched with. If the flag--utility-sub-type=network.mojom.NetworkServicewas used when launching thechrome.exeprocess then that process is going to be the network service.
and…
Once the network process has been found, it will then use the below code to inject the DLL, which has now been turned into position independent shellcode thanks to sRDI, into the process.
In the above example the injected code is on Windows since it’s a DLL but a similar approach could work on a Mac.
Is that what happened here? Maybe. I don’t know. But that process of finding the network process and then injecting some code might explain why after restarting that process there’s less code in it.
I don’t know because I would have to figure out how to reverse engineer that blob of code to see if it is benign or malicious. If anyone figures that out drop me a line on LinkedIn.
How would I do that? Well more on that in a minute. I was jumping around at this point because I wasn’t sure how much time I really want to put into this.
Memory analysis
I could also try to do some memory analysis. Here are some tools you can use to do that.
For memory analysis you get a dump of the machine contents and you essentially query the memory on the machine looking for clues about the malware. I wrote about searching through memory in this post which is kind of related.
In order to do that I need to dump the machine and run a bunch of tools I haven’t used in a while (and never really used a ton) and get that all working and then query for the malware…it’s more than I want to do at this moment.
But essentially when you find the malware in memory you can carve it out and disassemble it or inspect it just like you would if it was in a file.
Logs in the Mac Console
I could also dig through the logs on my Mac using the Console app (or grep these files in a terminal.)
I don’t see any crash reports. That’s good. It also aligns with my theory with process injection, I think.
Nothing in Spin Reports.
But AHA.
Here under Diagnostics I find something with a “Team ID” that matches that string of characters above.
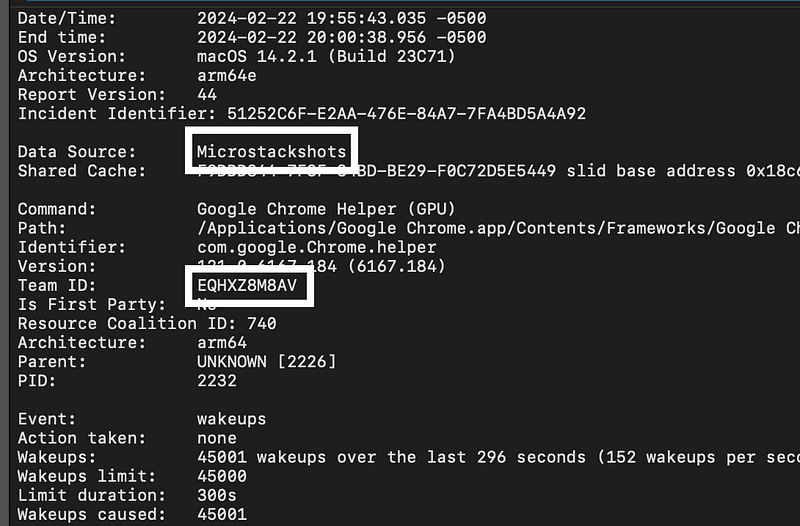
The number of wakeups are kind of odd. Is that because the malware is beaconing back to a C2 server or getting commands from it? Google also has some kind of beacon service I think (which I very much dislike). More information is needed.
What are Microstackshots?
Looks like Google has a patent on that dumps information about a process:
A method and apparatus of a device that captures a stackshot of an executing process is described. In an exemplary embodiment, the device detects an interrupt of the process occurring during the execution of the process, where the process execution can be in a kernel space and user space, and the interrupt occurs during the user space. The device further determines whether to capture a stackshot during the interrupt using a penalty function. If the stackshot is to be captured, the device captures the stackshot and saves the stackshot.
I can see the start and end time:
And a bunch of weird code.
I looked at some of the other diagnostic dumps and they look similar. What are diagnostic logs if not crash dumps?
Apple describes the different types of logs in the console here:
Diagnostic Reports: System and user reports with information about hardware resources, system response times, and more. Diagnostic report names have an extension such as .diag or .dpsub.
Well it’s still not super clear what caused this diagnostic log to be created.
About that random string of characters…Aha
So what’s a Team ID?
There’s that weird string that got captured by LittleSnitch. I can see it’s a called a Team ID in that Microstackshot. Turns out it’s an Apple ID for a developer of an app or extension.
A Team ID is a unique 10-character string generated by Apple that’s assigned to your team. You’ll need to provide your Team ID for certain activities, such as transferring your app to another developer in App Store Connect.
You can have multiple apps for a Team ID.
Ok so who’s the owner of that Team ID?
After looking at a few different sites it seems to be a Google Team ID:
But is that really the proper use of a team id in that firewall entry or is someone trying to trick us?
A weird Google LLC startup item
What is interesting is that the question in the above forum relates to me. I saw that strange Google LLC app but I disabled it because it looked odd. I figured I’d turn it back on if it seemed that it was required later.
This person is asking the same question, but I’m not so sure the answer is helpful. If you really want to know if this is a legitimate item you can take some additional steps I’ll explain below, and as far as I can see, it is not. But I never enabled it and not going to reverse engineer what it does right now.
You can find Login Items that execute when you start your system in settings.
Someone ran a tool over it to get information on it — that might come in handy for situations like this in the future:
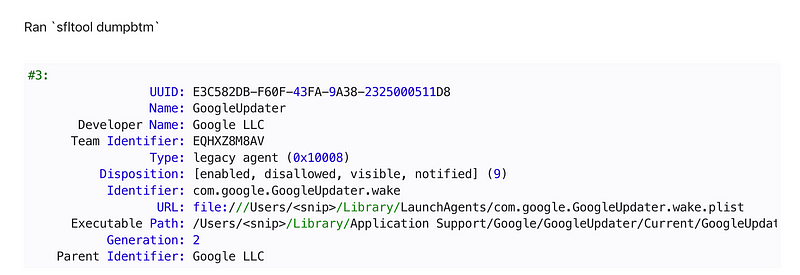
sfltool dumpbtmOh but wait…that tool says it wants to make changes. Hang on.
I searched around a bit. Seems to be legit.
Well my output looks different than the output above. There is no Team ID, no URL, and on executable path.
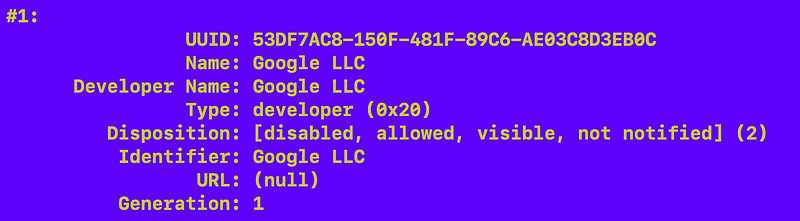
Not sure these are right either. They have the same name but the second one doesn’t have all the information. Is that right?
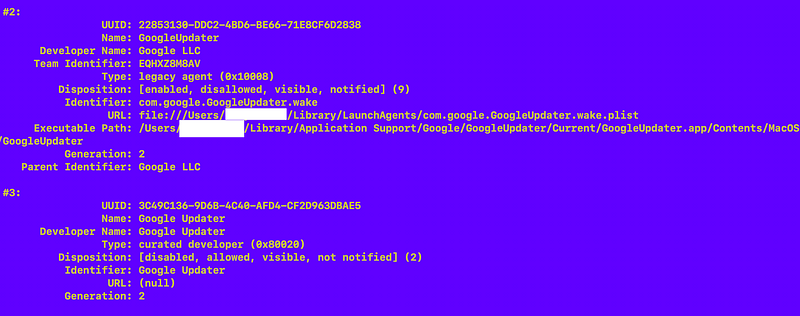
A lot of people are questioning these files:
https://www.reddit.com/r/mac/comments/154r28p/comment/kenkyp4/
I wish it was easier to find Apple Mac documentation on all these thigngs so it would be easier to tell if this is normal or not. I read something about multipole versions being stored. Was there a legit version overridden by one that is not?
Verifying Code Signatures
How do you really know if these are legit? Well I figured out later that the Team ID is related to code signing and you can check to see if the code is properly signed.
If you want to verify the signatures of apps on your system this post should help. I was planning to write one but not specifically for Mac and this looks pretty good.
So without knowing more at this point it seems like the things in my list without a valild Team Id might not be legit but are pretending to be Google. Also, I wrote my own start up script which does not have a Team Id because I’m not installing it through Apple. So you could have things that you want running that do not have a Team Id. I didn’t got through all that I got rid of the things that didn’t look right for now. I intend to rebuild anyway.
Back to activity monitor
I restarted my system and looked at that GPU process again.
You can click on the process and open it up and look at the files involved. I wonder what those /dev/null’s are doing in this list.
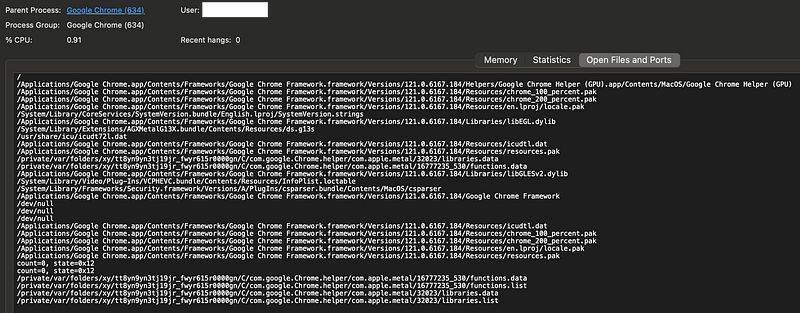
Once again I see this:

Alright I’m back to this. What is it. I was trying to find documentation on gpu-preferences but can’t find it. I wonder if it is something to do with the settings you set when you type chrome:flags in your browser.
I read this:
Any time you see an encoding with lots of
AAAAin it, you can bet that it's a Base64 encoding of a binary with lots of nulls in it.
>>> a=b'KAAAAAAAAAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAADgBAAAmAAAAM=='
>>> base64.b64decode(a).hex()
'2800000000000004000000000000000001800000000000000000002000000000000000e004000098000000'(And speaking more generally, any encoding that uses both upper- and lowercase letters is quite likely Base64. For example, a SHA256 is often given in Base64 compared to hexadecimal for SHA1.)
There are certain types of malware that will insert a bunch of things to get access to memory spaces and such but I’ve also seen binaries with images in them and lots of white space.
Ok that’s what I thought. But I didn’t get hex out of it but oh yeah — this person converting it to hex above.
So I can try something like this to convert the malware into the binary:
echo -n $(cat 2232.txt) | base64 -d | hexdump -v -e '1/1 "%02x"'I studied all this stuff but I don’t do it every day so I forget. I also forgot the command to lop off the extra character in one of my certification tests. One little bit at the end of a command caused me to miss a very complicated question having to do with carving malware out of a web page. I forgot it again. I got everything right but that tidbit.
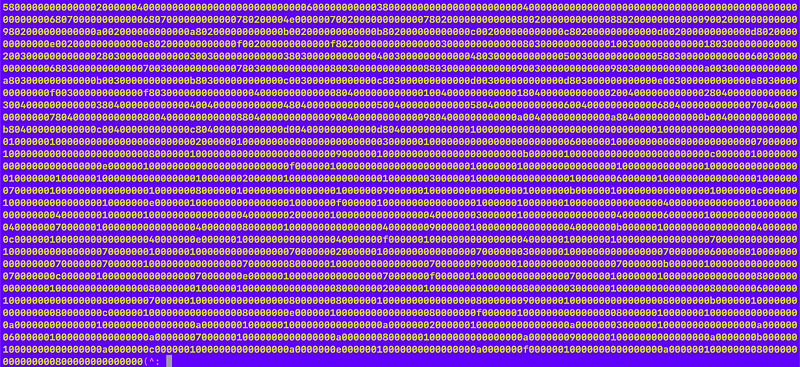
OK now I have this format and I can see if it’s a binary executable or what.
Again — I should do this on a locked down VM. Never do this on a company network or in a production environment!
If it is a binary executable the next step might be to try to decompile it with a tool like Ghidra from the NSA.
You can take malware and turn it into byte codes and then the real hard work begins. You’re looking at all these memory addresses and machine code and trying to sort it all out.
You can find samples of what that looks like in Google by searching on machine code Ghidra:
Of you can use online tools. I was just looking at this one called Joe’s Sandbox. There are others like this all like LastLine purchased by VMWare or VirusTotal acquired by Google.
Well, I tried sticking my output in this online tool I found that can run a bunch of decompilers which I don’t really recommend for reasons I wrote about in my Target Breach paper. You may be handing over sensitive data to who knows and you could also provide evidence for a later lawsuit. But anyway, I tried this site:
And…the code was not binary. I don’t know what it is exactly. I could spend hours trying to figure that out. Maybe it’s just Google configuration in an encrypted or hashed format or something.
I search around to try to understand the parameter for which that blob was a variable. Dropping it for now.
By the way I later tried the a file in a directory which was related to that. It was a binary that says it is an “App” but when I tried to open it (kind of by accident) on my Mac it said the file was from an unknown developer, even though it is labeled as coming from Google. Hmm. Google Chrome Helper (GPU).
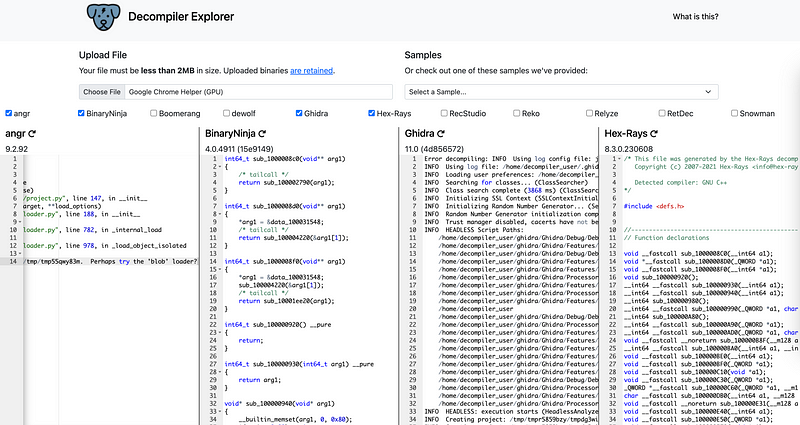
angr and Ghidra failed to parse the file. This will look familiar to people familiar with Ida Pro from Hex-Rays:
Here’s the output from BinaryNinja:
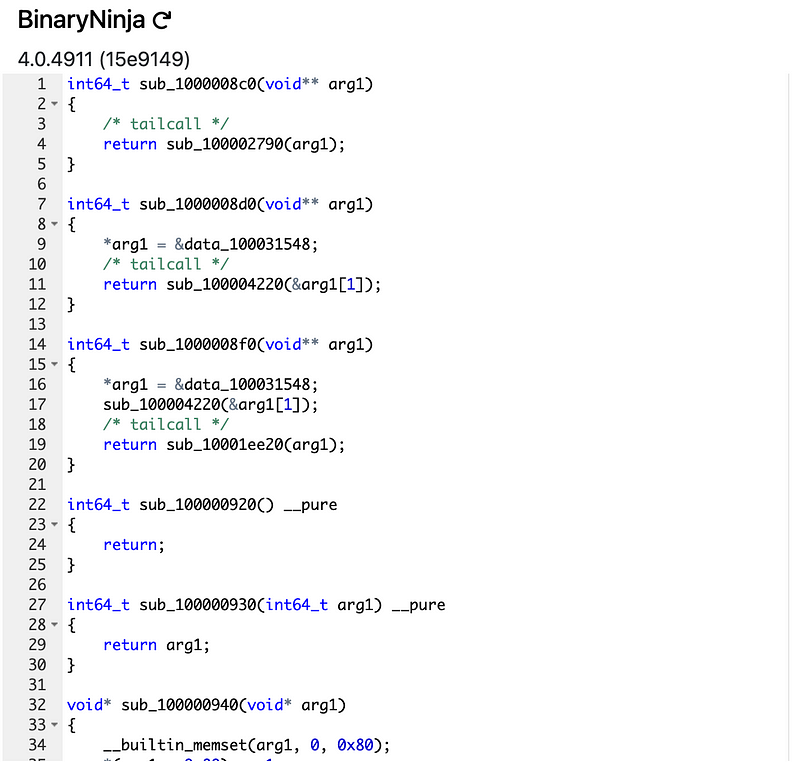
As you can see, once you decompile a binary executable, you still have a lot more work to do to sort out exactly what the program is doing, and it is tedious and time consuming for most people. And, it might not even be malware.
I got 86 out of 100 on the reverse engineering certification and I usually got scores in the 90’s for almost all my certs. Let’s say by the time I got to advanced pentesting I had one foot out the door. If you don’t do this every day it’s hard to do it once in a blue moon and not my focus at the moment so not going to spend more time on this for now.
So, so, so many things to do in security.
What if it is not the problem?
So if that is not the actual problem, then we could have bigger problems. There is some crafty malware that embeds itself so deep into systems you won’t see it like kernel mode root kits and malware that gets into a machine before it fully boots up. That type of malware can bypass kernel restrictions. What that means is, it won’t show up in activity monitor. It will basically be invisible.
So how do you find it? It’s very difficult. One way would be to look at the memory as explained above. The malware has to be in there somewhere in order to execute by virtue of how a computer works. Except in a few special cases…where it exists in some separate device on the computer like the hardware used to boot up the machine. I’m not even going to try to get into all that. It’s easier to restore the computer to factory default and hope there’s no way it can persist.
What if it does persist? Well, then you can tell the malware is on the machine by inspecting your network traffic. In order for the malwer to do anything useful it has to connect to something. It needs to get commands from a C2 server or exfiltrate data to an attacker host. Otherwise, what’s the point.
So yeah, I’m pretty much just going to rebuild this machine as I have other things to do. But wait! There’s more! I want to see what else I can find first.
Reinstalling Chrome may reinstall malware…
Next I tried uninstalling and reinstalling Google Chrome but the process persists with that extra code. And on that note, I read that if you just uninstall and reinstall Google Chrome and you have malware in some extension in your profile, Google happily redownloads it for you. I read something about deleting files and turning off syncing, but I’m going to wipe this whole machine and start from scratch as soon as I’m through looking at this.
Random Google user content connections
So as I’m digging into this and mostly working in bash I get popups for various subdomains of googleusercontent.com so I finally temporarily just blocked that domain. That domain is related to Google Drive and other user content that could facilitate a C2 channel probably so no thanks. I really should not be doing what I’m doing I should be running this on a VM like I explained above.
Weird socket in the temp directory listening for SSH connections
By chance I dumped out my binary code to the /tmp directory and I found this:
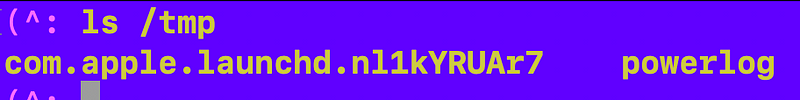
I tried to look int that “file” but it was actually a socket.
Ok what’s using that socket?
After digging around I finally checked out the man page of launchctl which helps you run commands related to launchd (which launches things, as the name suggests.)
I discovered the dumpstate command which dumps out the current cache.
I ran this command:
launchctl dumpstate | grep com.apple.launchd.nl1kYRUAr7Which gave me this:
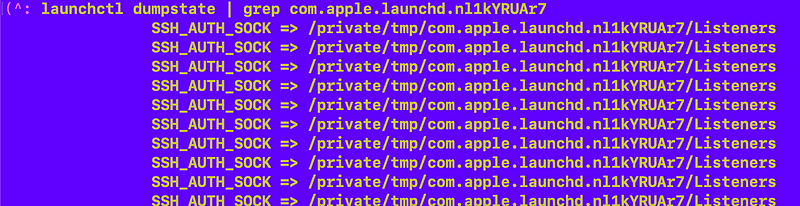
SSH_AUTH_SOCK sounds like it’s listening for SSH connections.
So this socket is listening for SSH connections apparently. However I don’t see any port 22 in nestat.
Anyway is SSH even running? How can I tell?
I kept digging…
Took at look at the routes
Ran netstat in various ways including -r to see routing information. What is all that IPv6 junk?
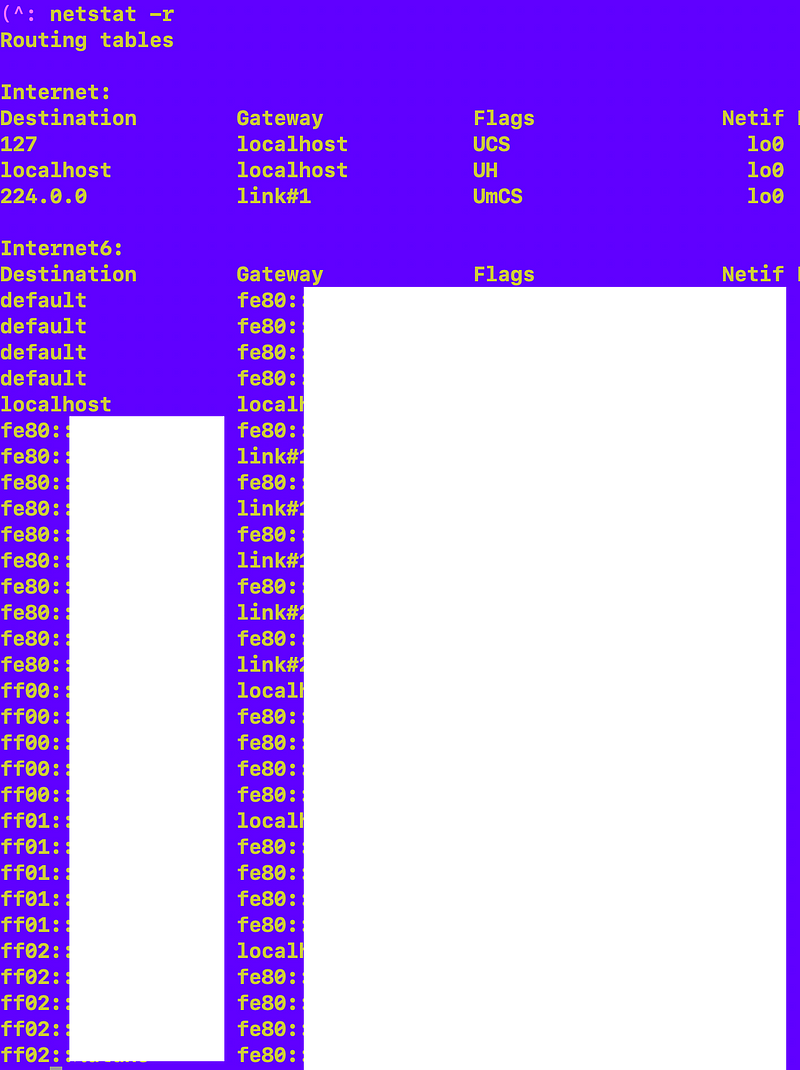
Here’s where I find utun that I was trying to understand the purpose of before. Something to do with routes.
I would like to get rid of all the IPv6 routes except what is required to send the IPv6 traffic to a black hole.
The one thing I don’t know is if Apple requires any of these to operate on localhost so I need to look into that.
This was a newish computer, BTW, and I hadn’t yet disabled IPv6 so…refer to my IPv6 attack scenarios as to why I do that. And, if attackers are able to use IPv6 sometimes it is invisible on your network.
Finding things active in the launch cache
Oh randomly found this to get the things that are active in launchd cache.
grep -B 1 -A 4 "active count = 1$" <<< "$(launchctl dumpstate)"But that didn’t really help. But it might help someone so leaving it in here.
Getting stream sockets from netstat
Here’s how to get streams /sockets from netstat:
netstat -tul | grep 'Address\|stream'Using that I could see the socket in the temp folder and also this weird socket:
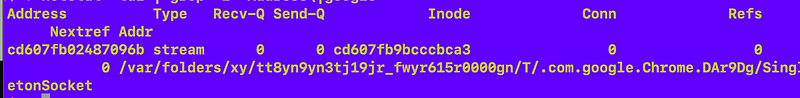
Is that normal? I don’t know.
Found this on a really interesting named GitHub page:
The about says:
Automatically exported from code.google.com/p/chromedriverThat site says the code is now here:
https://chromedriver.storage.googleapis.com/index.html
And that page is hosted on Amazon…?
Well maybe it’s all fine. I don’t know.
Along the way ran across this great definition of port vs. socket:
So finaly I think I noticed something.
The socket thing has this at the front:
/System/Library/LaunchDaemonsSo I went to that folder.
And at the end of the list I noticed three plist files that don’t look like the others and these are the three things I am wondering why are running on my system:
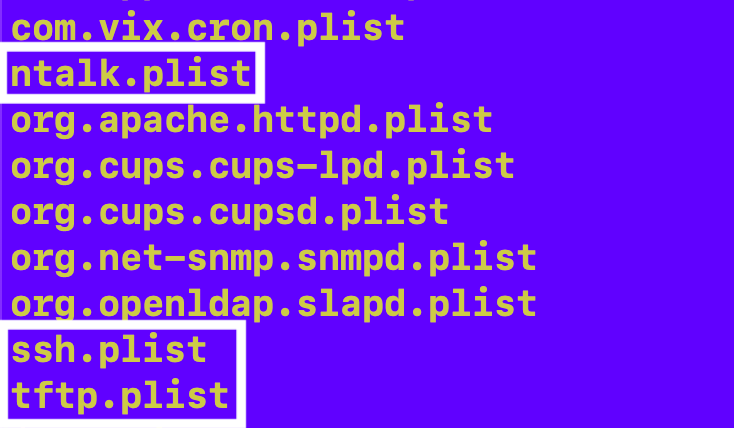
Here’s the ssh file.
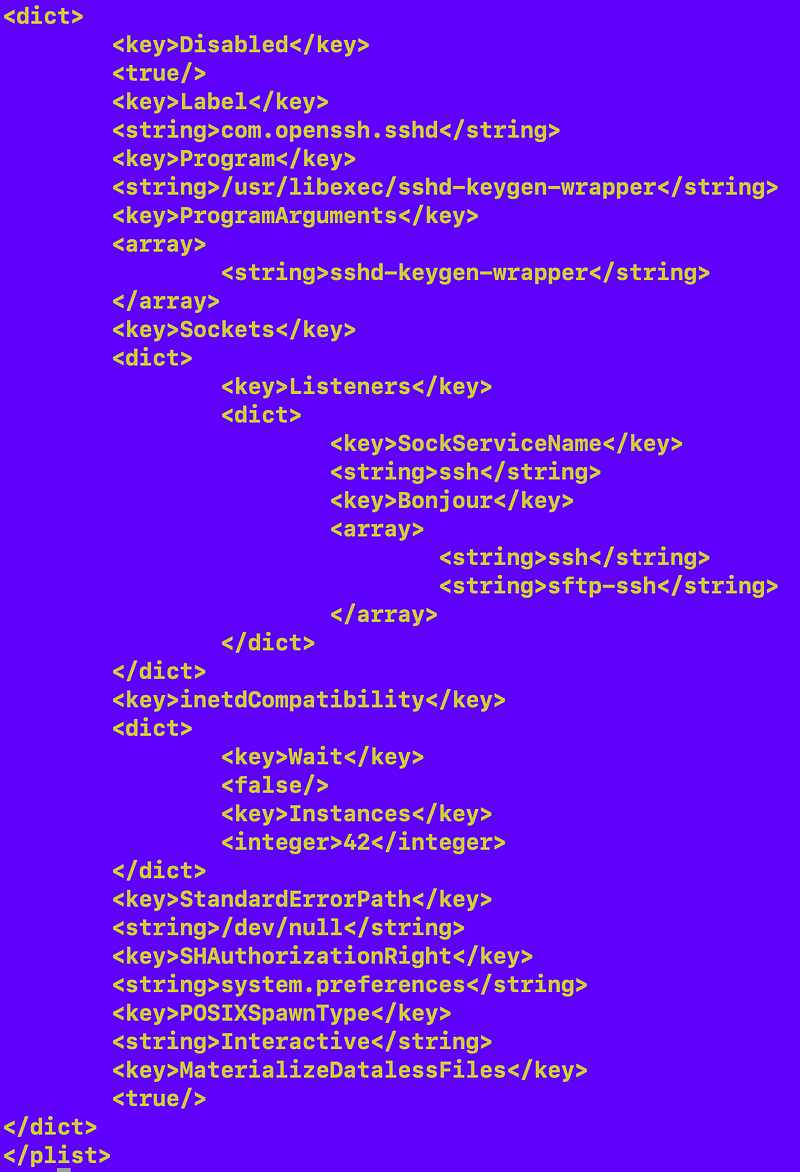
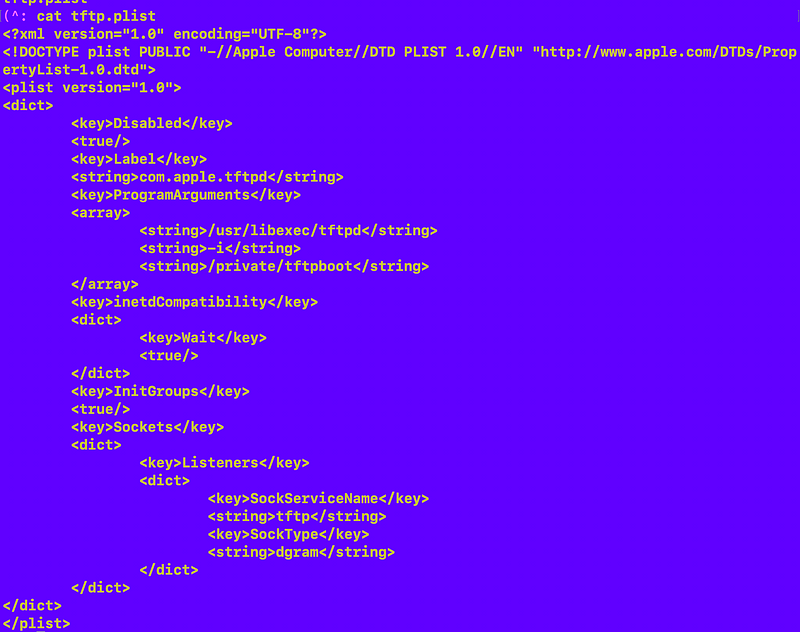
tftp
ntalk
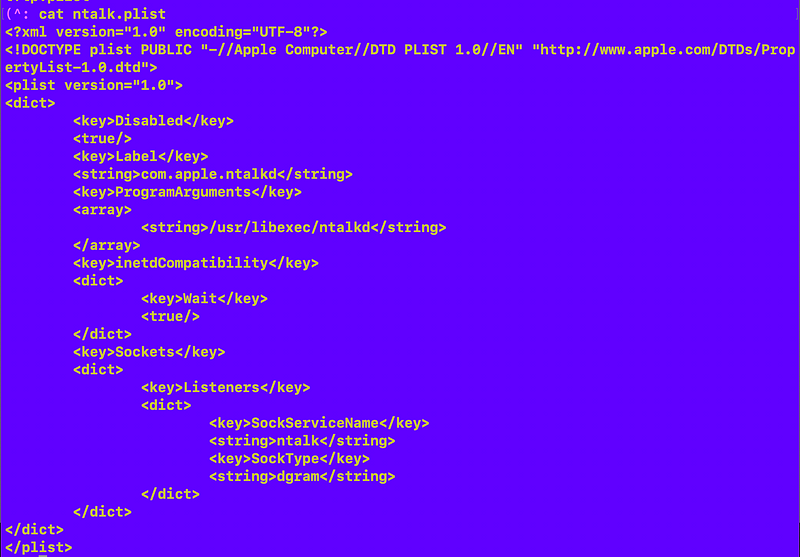
These are the only three files in this directory with those keywords in them: ssh, ntalk, tftp.
Ok but what is launching them?
I’m not sure if those are legitimate or just there to waste people’s time like me who doesn’t really know a lot about this. After a while I finally figured out those files have nothing to do with my problem. The names aren’t even in the right format.
Looking for the SSH service again
Use this command to find each of those related plist apps:
launchctl list | grep 'ssh\|PID'Well. That command indicates there is no pid and the status is 0 for com.openssh.ssh-agent. The other two are not in the list.
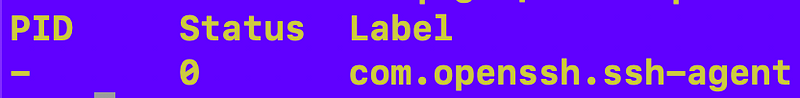
Hmmm. The other two are running. SSH doesn’t seem to be. Weird.
Well, I was looking in LaunchDaemons above. I switched over to LaunchAgents and took a look at what was in there:
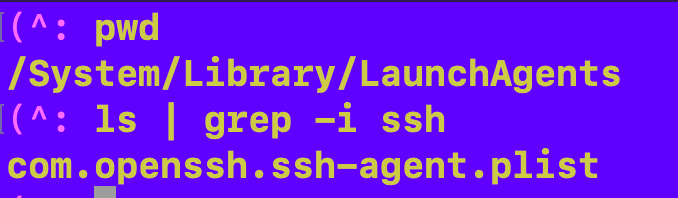
Hmm. Maybe that’s what’s running that strange socket.
Use remove instead of unload:
sudo launchctl remove com.openssh.ssh-agent.plistThat didn’t remove the ssh-agent from the list above.
I ended up looking in all these places:
Try checking these locations:
/Users/your username/Library/LaunchAgents/
/Users/your username/Library/LaunchDaemons/
/Library/LaunchAgents/
/Library/LaunchDaemons/
/System/Library/LaunchAgents/
/System/Library/LaunchDaemons/I removed everything in the Users directory because there was a weird Google updater in that didn’t look like it was properly signed. I’m not sure but going to start over anyway.
No other instances of SSH found.
I ended up must deleting the file in the tmp directory. I don’t use SSH except to contact AWS and nothing else should be adding it there. If it comes back I’ll figure it out. But I need to move on.
I verified that does not exist on another computer used to do the exact same work and running basically the same software.
Looked at this chronod service which had a strange port next to it
I think this may be unrelated but not sure:
There is malware named Chronod: This is a credential stealer and clipper. It is responsible for intercepting browser activity to steal information from the user.
On your mac there’s a service called chronod has something to do with widgets on your desktop.
I turned off widgets because I don’t think I’m using them anyway:
I killed the chronod service that was associated with a port.
Side note on looking up information about a service
Use id -u to look up your user id:
id -uReplace 501 in this line to look up information about the apple chronod service.
launchctl print gui/501/com.apple.chronodWhat if I try that with the process above? Didn’t really help.
Turned off ftp proxy
Figured out this is ftp proxy and shut it down with this command:
https://apple.stackexchange.com/questions/404346/what-is-intu-ec-client-listening-on-tcp-port-8021Also added that to my startup script.
Turned off open directory
DEC_DLM in my port list is related to OpenDirectory. I don’t need that running.
Open Directory, Server app, Workgroup Manager; DirectoryServices in OS X Lion and earlier. Note: This port is registered to DEC DLM.
By the way I’ve run across the person giving these answers a few times telling people to move apps to the trash and delete them. Not a typical response is it? IDK.
This was buried beneath those odd instructions:
sudo launchctl list I manually parsed through the results looking for things related to open directory. I found com.apple.opendirectoryd (which I believe should be left alone). I also found “com.apple.odproxy.” This was associated with a error status.
Reading on, I ran this and added to my startup list:
sudo launchctl unload -w /System/Library/LaunchDaemons/com.apple.odproxyd.plistNow I am down to the following listening services. I don’t allow any incoming traffic besides when I have to allow the printer to connect so all the rest is pointless.
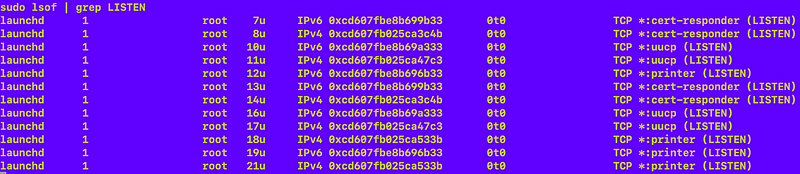
Turned off UUCP — an only unix to unix copy protocol
Well I certainly don’t think I need this running:
Followed by:
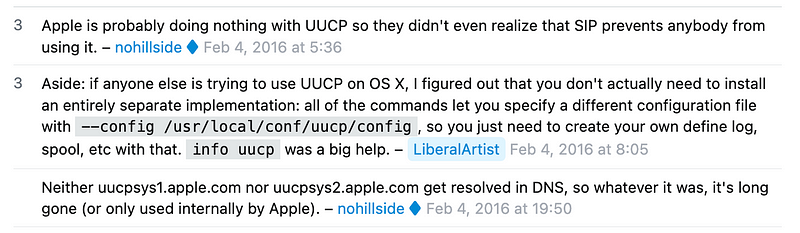
2016…
Turned that off and added it to the start up script.
sudo launchctl unload -w /System/Library/LaunchDaemons/com.apple.uucp.plistProfiles and certificates for PKI / 802.1X I presume
So here’s something interesting. I kept getting a lot of weird requests that aren’t really aligned with my area of expertise through IANS — specifically related to PKI. I know what it is but never managed that for a large organization and I focus on cloud and application security — so I’m not exactly sure how I was supposed to be a PKI expert. I used certs to identify IoT devices in an architecture for firewalls but still. I declined the questions.
So here I am looking at this service exposed to the Internet for cert enrollment. And I’m trying to think of one good reason why this is exposed to the Internet and wondering if it’s running on every Mac by default (scary) or got turned on by the malware that got onto this machine. All a big coincidence that I got those call requests, I suppose.
This is an interesting post to enroll a Mac with a Microsoft CA. I didn’t read it closely as I’m not using Microsoft except when I have to for a client project so can’t tell you if good or bad. Just interesting.
Anyway this certificate service is in all these lists of well known Mac ports.
It says it has to do with profile manager and SCEP — both of which are used to basically remotely administer your host. So yeah this can go until if and when I actually need it:
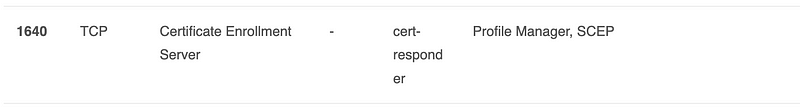
At some point I might administer hosts with some tool that uses these things but not today.
If someone could get ahold of you remote management of your system:
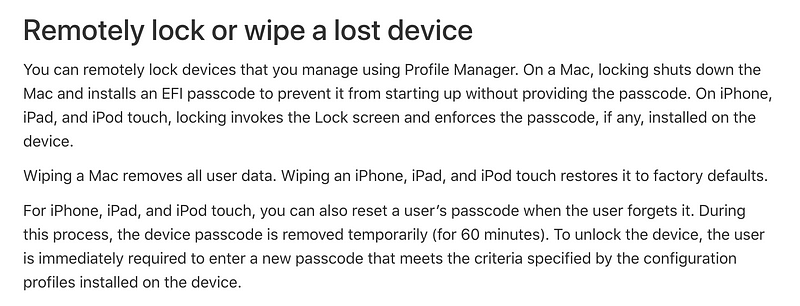
That’s an old version but you get the idea.
I don’t have a profile configured on my laptop at the moment:
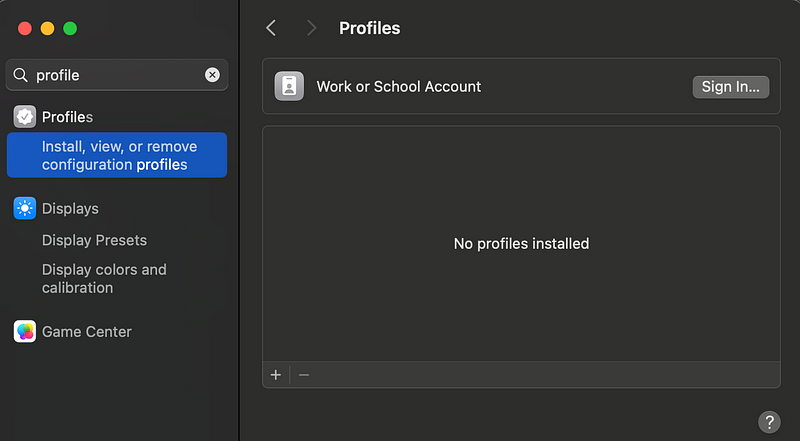
Here’s some information on SCEP:
Oh and by the way it looks like you should use ACME now.
I’m not seeing the specified item here: com.apple.security.scep
I tried disabling this:
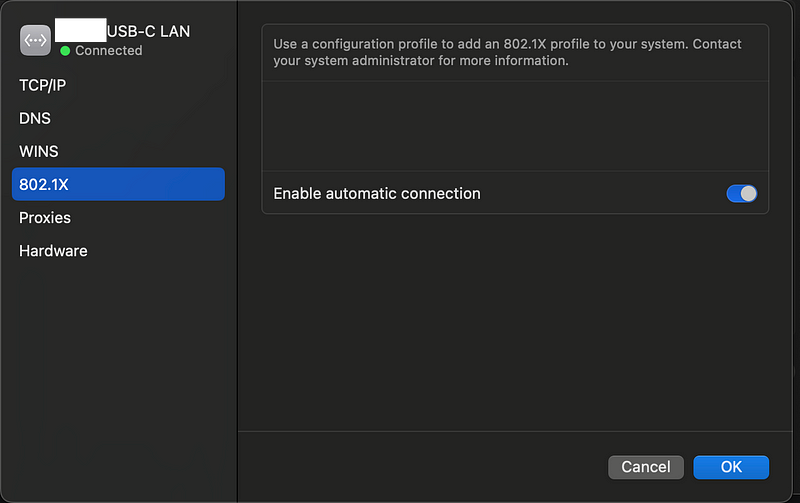
Disabled:
Didn’t work.
Well I’m not going to spend more time on this right now.
Keychain
Side note: Helpful information on Key Chain.
Check for cron jobs
I just checked this because I heard someone used it in a pentesting exercise. I checked for cron jobs on my system to see if there were any automate jobs that shouldn’t be running:
crontab -lMissing and Truncated Logs
By the way, I couldn’t figure out exactly what happened because I didn’t have enough logs. And that’s why you need logs. If you have an incident you want to be able to see what happened like:
- When did that Login Items application get installed?
- What was the IP address that installed it?
- I know it came with a Google update but was it really part of the Google update or the attackers timed their installation?
- Was the Google update process infected like SolarWinds?
- Or is it legitimate but there’s something I don’t understand about those login items?
- What other network activity may have been attributed to any weird software components on my system?
- How did that SSH socket get installed?
I have so many more questions but I really need to get back to my actual job. So now it’s time to rebuild and move on. Hopefully this will help some other people find issues on their computers and fix them. Maybe someone who does this for a living will have better logs and more details to determine exactly what is going on. If you find out more about this drop me a note on LinkedIn. I’m way behind though now so won’t have a ton of time to discuss at the moment.
Summary:
- Use network and host-based firewalls.
- Limit your network traffic to only what is required.
- Disable any services you don’t need.
- Monitor your network.
- Watch for unusual activity.
- When all else fails, rebuild.
- But make sure your firewalls and networking gear are not infected.
On that note, I did inspect my networking gear but going to be monitoring that closely as well. I have other ideas on that but never enough time. May write more on that subject in the future. Here are my posts on network security:
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






