AWS CodeCommit Triggers
ACM.345 Seeking an AWS CodeCommit trigger event for GitPush
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Deploying a Static Website | Git Security | AppSec
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I finally got a batch job working that requires MFA to execute. That took way longer than I expected. I added all the links to the sub-series on deploying a static website above. I’m not quite done with that but proved it works and want to move on to finish the website deployment.
In this post I’m going to explain how I’m going to automatically push code to an S3 bucket when the code is checked into AWS CodeCommit. It’s similar to GitHub actions but as I explained, those have too many security risks for my liking with a GitHub cloud hosted repository.
If you still want to use them, I provided some security best practices here to do the best you can…
If you run them in a completely private network and host your own instance of GitHub you may be able to create a lower risk implementation but I don’t want to manage all that.
We should be able to trigger actions with AWS CodeCommit that hopefully remain on a private network and leverage fine grained permissions without giving credentials to third-party clouds.
AWS CodeCommit Triggers
My objective is to have any files I check into my test AWS CodeCommit repository for dev.rainierrhododendrons.com get automatically copied to the corresponding S3 bucket for the website.
There are multiple ways to potentially achieve this objective. The first approach I’m going to try is using AWS CodeCommit triggers. Let’s take a look at the documentation.
AWS provides the following documentation to create triggers for AWS CodeCommit.
We need to figure out how to automate the trigger described in the documentation and add it to our CloudFormation scripts. We will also change the CodeCommit actions and what happens when the trigger fires.
The CloudFormation resource we need to use is a RepositoryTrigger.
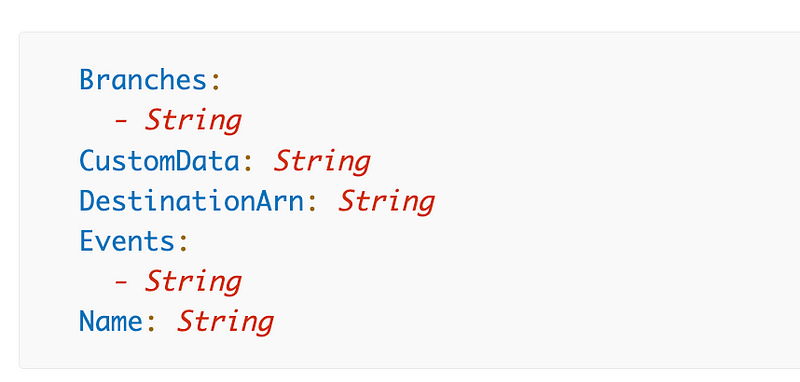
Name — Yes, we will give our trigger a name.
Branches — I’m just going to apply this to all branches which is the default if you don’t include this option. As mentioned in prior posts I have a different plan for AWS CodeCommit and may not use branches.
CustomData — This is an optional field to pass data to the trigger. This field is optional and is not for parameters. It seems to be used for metadata. I’m not going to add this to my configuration.
DestinationArn — The Lambda function ARN in this case. This field is required.
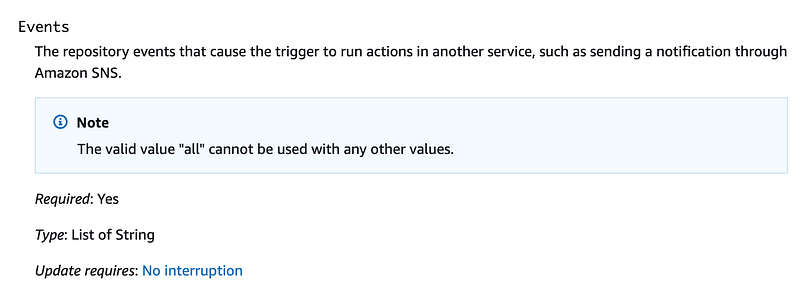
Events — These are the events that will trigger the action. We can take a look at the actions for AWS CodeCommit in this list:
Here’s where we run into a problem. The likely action we want to trigger on is a push to CodeCommit. However, it says GitPush is [permission only]. What does that mean?
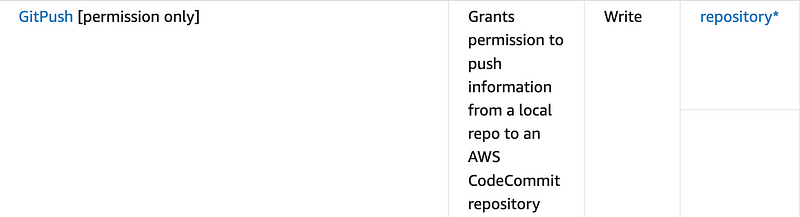
If we click on the GitPush link, we get the following documentation:
Scrolling down it once again says:
GitPullandGitPushare IAM policy permissions. They are not API actions.
Does that mean that these actions cannot be used in triggers and are not logged to CloudTrail?
Also, this documentation is confusing, just like the AWS Batch documentation, because it seems to be duplicative. I would suggest some of the same recommendations I wrote about here:
The documentation under AWS CodeCommit monitoring provides some useful insights:
All CodeCommit actions are logged by CloudTrail, including some (such as
GetObjectIdentifier) that are not currently documented in the AWS CodeCommit API Reference but are instead referenced as access permissions and documented in CodeCommit permissions reference. For example, calls to theListRepositories(in the AWS CLI,aws codecommit list-repositories),CreateRepository(aws codecommit create-repository) andPutRepositoryTriggers(aws codecommit put-repository-triggers) actions generate entries in the CloudTrail log files, as well as Git client calls toGitPullandGitPush.
That seems to indicate we can use the GitPush action as our event in this case.
Now on the CloudFormation page, there is no example code. Do we use this:
[GitPush]or this?
[CodeCommit:GitPush]It’s not really clear.
Well the example that shows how to do this manually has the following selection:
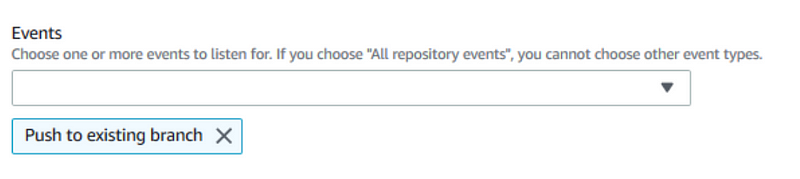
However, a related API documentation page shows that these are valid values:
Valid Values: all | updateReference | createReference | deleteReference
Here’s yet another documentation page with some confusing information.
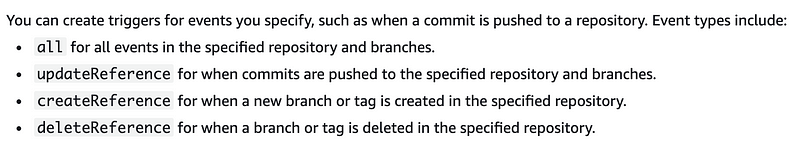
You can create triggers for events you specify, such as when a commit is pushed to a repository. Event types include:
allfor all events in the specified repository and branches.
updateReferencefor when commits are pushed to the specified repository and branches.
createReferencefor when a new branch or tag is created in the specified repository
deleteReferencefor when a branch or tag is deleted in the specified repository.
To see the full list of valid event types, at the terminal or command prompt, enter aws codecommit put-repository-triggers help.
Here’s what gets returned by that command:
…
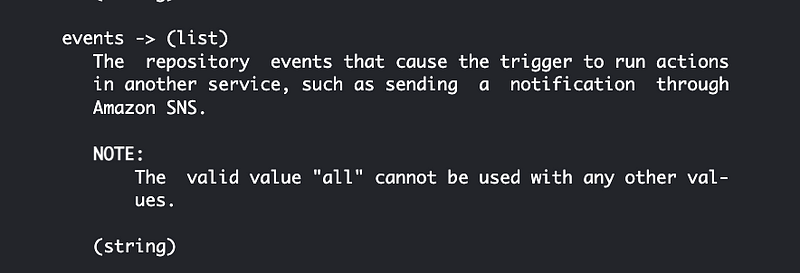
…
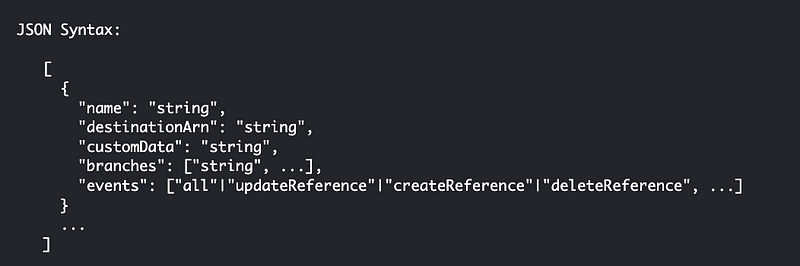
Finally, I find this documentation on a CodeCommit trigger for an SNS topic that describes AWS CodeCommit Trigger Events as follows:
So apparently updateReference is the same as a GitPush?
Why is this so hard to find and not in the CloudFormation and API documentation? Am I even interpreting this correctly?
Presuming that my interpretation is correct and this event will work, I am going to do the following in upcoming posts:
I already created the CodeCommit repository:
- Deploy a Lambda function with my custom bash container that gets triggered on the git push (via the update reference event).
- The Lambda will clone the data from the repository and copy it to the S3 bucket using the aws s3 cp command.
- Create a CodeCommit Repository Trigger with CloudFormation as described above.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
