Create an AWS Code Commit Repository With CloudFormation
ACM.260 Automated creation and governance for source control repositories
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: GitHub Security | Application Security | Secure Code | AWS Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I pondered GitHub vs. AWS Code Commit and proposed — why not both? You may have a use case better suited to one or the other or you might opt to use a combination of the two, or something else. In any case, you’ll need to consider the security of your source control system and who can access them. That includes the cloud provide themselves, external actors, and the people you entrust to work with your source code.
In this post I want to deploy an AWS Code Commit with CloudFormation. AWS CodeCommit is essentially a service offering managed Git repositories and you can use your favorite Git commands with it. You can find the documentation here:
Creating a repository looks pretty simple:
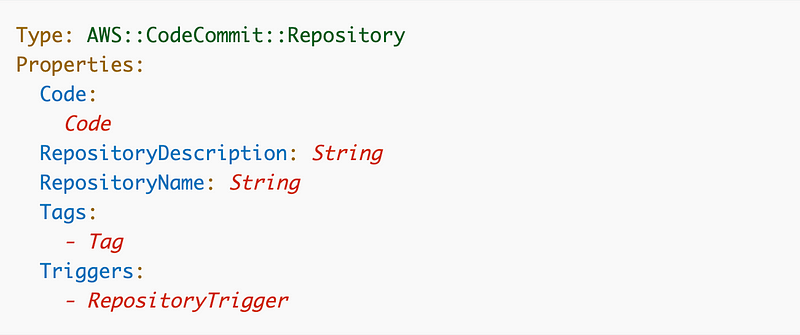
Here are the values we can set when creating an AWS CodeCommit repository.
Code: Optionally add code when creating the repository.
Description, Name, and Tags: Should be self-explanatory if you’ve been following along.
Triggers: This is the fun part. You can trigger an action when someone checks code into your responsitory like sending notifications or kicking off a deployment.
We’ll look more at triggers in a later post. In this post I want to create a simple repository and test checking in code.
Where to deploy an AWS CodeCommit repository
The question is — where should I deploy this repository? I’ve been setting up a number of AWS accounts and considering governance throughout the process.
The answer to that question comes down to who can do what with your repositories and how much work do you want to spend on setting up trust boundaries?
What I mean by that is, if you have people who are allowed to manage repositories then you could put your repositories into a separate account and only give those people access to the account. You can create cross account roles with policies defining who can access the various repositories.
In my case, I like to have separate repositories for Dev, QA, and Prod rather than branches. I find that merging and branching often leads to complicated errors. Also, it’s not easy to remove history from git repositories even though it is possible.
I mentioned in the prior post this tendency, which is not the norm, comes from using a source control system named AccuRev that I found to have an interesting approach. We’ll try it out with AWS CodeCommit to see how it works out.
Where to deploy an AWS CodeCommit repository
Should I put the developer GitHub repository in the developer account, QA in the QA account, etc? What if I created a separate account for GitHub repositories and granted everyone cross account access to that? Then if I only allow CodeCommit in that particular account I know where I can find all the code.
Well, since I’m just trying a few things out here, I’m going to start by simply deploying the repository in my SandBox account — because that’s what a SandBox environment is useful for — trying out new services before you roll them out to your entire organization and ending up with an architecture you regret later and is hard to change.
I’ll have the SandBox administrator deploy the repository and grant the web admin permission to use it in order to deploy websites. How that will work exactly is a work in progress.
We’ll look at policies for deploying AWS CodeCommit in the next post, but for now the SandBox admin has full access to our SandBox account so we don’t have to deal with permissions just yet. We can change the CloudTrail logs as I’ve shown you before to determine what permissions were required to deploy the repository.
CodeCommit code location
I renamed my Git folder to SourceControl and put my Git folder in it, along with a Codecommit folder for my AWS CodeCommit deployment code.
SecurityMetricsAutomation/SourceControl/CodeCommit/stacksFunction to deploy the CodeCommit repository stack
Basically I’m just going to give my CodeCommit repository a name but I want the name to include the environment and the app name. You’ll see why in the in an upcoming post.
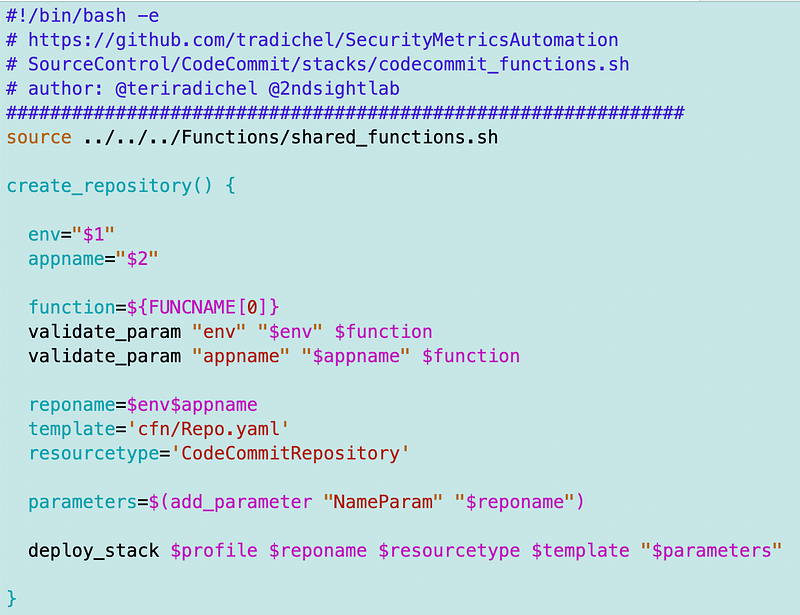
Template to deploy an AWS CodeCommit repository
Here’s the template to deploy the AWS CodeCommit repository. The template is pretty simple. Most of the code consists of outputing the results of the deployment. We’ll use that information to test our repository.
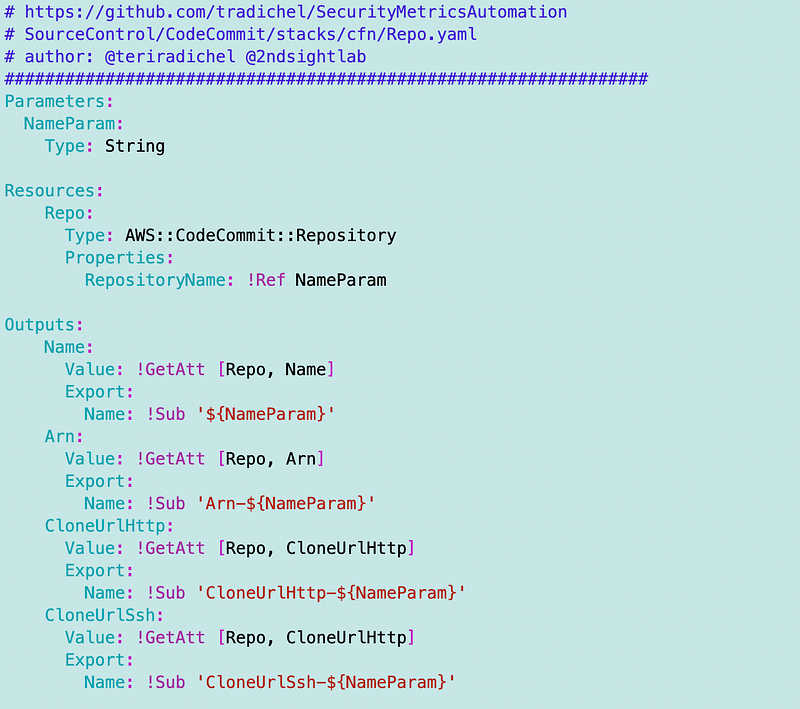
Alter the change_dir function
I had to alter the change_dir function for the github functions and add the codecommit functions file.
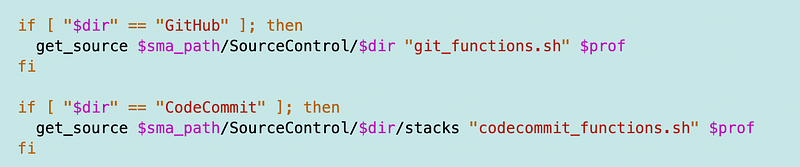
Add the code to deploy the repository to the web deploy script
View the Repository in the AWS CodeCommit dashboard
You can navigate to AWS CodeCommit in the console and view the repository.
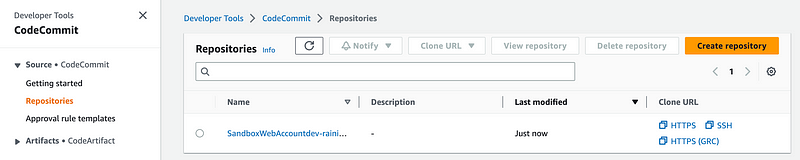
Click on the repository to get connection steps.
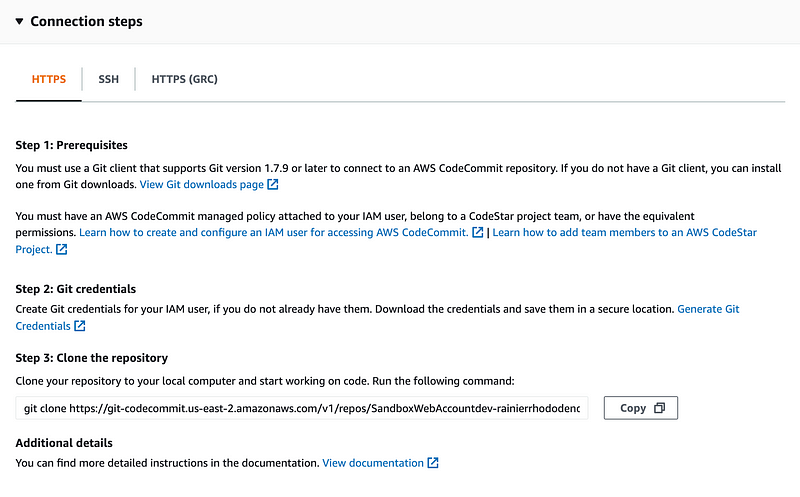
It’s essentially a Git repository so we can use git commands. But where do we get our credentials?
I’ll cover that next.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
