mfaAuthenticated with AWS Assume Role
Needs a change to enforce MFA on actions taken by IAM roles
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Bugs | AWS Security | Secure Code
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I’m passing this one along to the #AWSWishList on Twitter.
One thing I noticed while trying to get IAM conditions to work on cross-account roles is that even though I’m passing in an MFA code required to assume an IAM role, once I take an action with that role it says “mfaAutethenticated: false” in the CloudTrail logs.
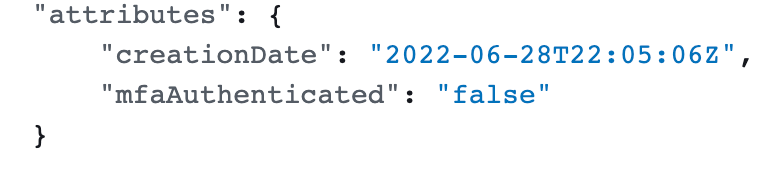
It seems like this should say “true” if the user was required to use MFA to assume the role. That way you could require MFA on actions completed by that role. The original role assumption was by a user with MFA and so in theory MFA had to be used to initiate the action subsequently taken by that role.
Maybe this is why conditions related to MFA were failing in my previous blog posts where I tried to use IAM conditions, organizational conditions and MFA conditions to with S3 bucket policies.
Related post:
Subsequently while testing a bucket in the same account where a role existed, I realized that I was also having issues accessing a KMS key assigned to a bucket with a cross-account role and was getting an “Access Denied” message. I couldn’t use a policy that enforce MFA here either.
While testing I couldn’t find the logs where the action occurred that triggered this message, nor did the individual actions show up in AWS IAM access tab for the role or find a way to validate that the MFA condition in the policy was the issue or whether it was something else.
It seems like there is a need for additional and more complete test cases for QA teams involved in testing this functionality and a common structure for useful error messages across the cloud platform. I wrote a blog post on thoughtful error handling which will probably be part of my next book if it is helpful in thinking a bit more about the these challenges:
Issues:
- Error messages are not accurate or helpful.
- Conditions with cross-account roles are either not working or not well-documented.
- The fact that the MFA attribute does not get set in cross-account roles seems to make policies that enforce MFA impossible.
- Haven’t been able to get organizational conditions working at all, such as allowing a role to have access to all S3 buckets in an OU or to have KMS key access to decrypt all buckets in an OU where the buckets have different KMS keys but all the keys are in a single account.
- IAM access tab needs to show all actions in detail taken by a role, even when used in a cross-account capacity — in the account where the role exists.
- Logs need to exist for KMS cross-account access where the bucket, key and role are in a separate account or better document how to find them.
- Logs should show when MFA is required and not provided. There should be a separate error message for external ID, invalid token, etc.
More time-consuming issues I’ve hit trying to implement security for an organization exist in other posts in this blog and these issues drive developers to drop security in favor of “getting things done.” If it’s ambiguous and full of trial and error for a person with over 25 years of experience and over 10 on AWS, how would one expect a newbie to implement things securely?
I’m not picking on AWS here. It’s my favorite cloud platform. My recent experience on Azure was much more painful. In general, developers everywhere need to write better error messages and QA teams need to write better test cases. Having worked on a lot of financial systems, I understand what good test cases look like. You need to be thorough with money and the same care should be taken in relation to logging and security. Error messages need to make sense and hopefully be aligned with a code developers can search on to find the answer to why their code is not working.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab