No KMS Cross-Account Logs?
Testing access to a bucket with a cross-account KMS key.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Bugs | AWS Security | Secure Code
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Update — this could be due to the fact that certain KMS actions occur in an unexpected region. I’ve revisted in this in later blog posts in my series above.
I wrote about an access denied message related to PutObject on an S3 bucket. As it turned out and I demonstrated in my last post the error was due to encryption. When I turned doff encryption, no problem. Now I want to figure out exactly what policy I need.
I already showed that I checked the Key Policy in that last post and my account (including the role in it that I’m assuming) has full access to the key used to encrypt the files in the bucket.
Danger — KMS.*
As before to get this working I added KMS * to my IAM Policy as I did with S3 and added the KMS key back to the S3 bucket. That worked. But we’re not done here! As before we want to create a zero-trust policy so let’s see what permissions we really need.
Let’s review IAM Access Analyzer again. Well, this is not helpful. It just shows that KMS was accessed but not which actions.
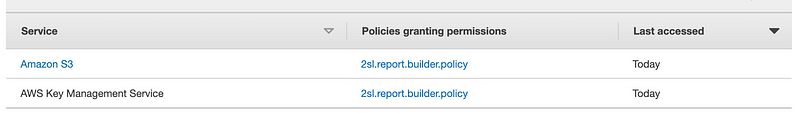
Fix: ^^^ Show which specific actions on KMS this role used so we can create an appropriate policy.Well, we can look at CloudTrail again. The question is, will the encryption action be in the local or remote account? Maybe it’s in the remote account and that’s why there’s no link above. But since the role doesn’t exist in the other account we can’t use IAM Access Analyzer over there.
Fix: ^^^ Show the actions taken in other accounts with IAM access analyzer.Well, when I look in the CloudTrail logs in the other account for anything with that key ID I only find the key creation record and no access failure.
When I look in the CloudTrail logs in the account where I’m using the key, I find nothing.
I turned on S3 event logs as noted in my last post.
Those don’t show any KMS actions either, unfortunately.
Fix: Better documentation or logging for cross-account KMS actions.I guess I need to figure out by trial and error, the minimal actions I need to add to my policy to use the key.
Am I looking in the wrong place, are the logs not there yet, or do they simply not exist? If the logs simply don’t exist for this scenario, that’s a bug.
I think the issue may be that these logs are object-level logs that need to be enabled.
I’m going to keep looking for these logs but that’s it for now.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab