If You Delete and Redeploy a Principal Referenced in an AWS Policy, Will Your Policy Still Work?
ACM.414 Will your CloudFormation stack update the policy if you redeploy it?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: AWS Organizations | IAM | Deploying a Static Website
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I deployed one account.
I wanted to fix a naming issue before I deployed the rest of the accounts but that led me down another rabbit hole of problems. Here’s one of them.
I’ve had this recurring issue on AWS and I’m not sure I like the way it is implemented.
This issue happens in role trust policies, resource policies like KMS and I presume the same would happen in other types of policies as well.
You have deployed a role with a trust policy that allows a particular principal to assume the role.
What happens when you delete the principal?
Does AWS give you a warning to tell you that principal is referenced in policies? No.
AWS silently changes the ARN in your policy to what I presume is the logical ID of the principal rather than the ARN without asking or telling you that this is happening.
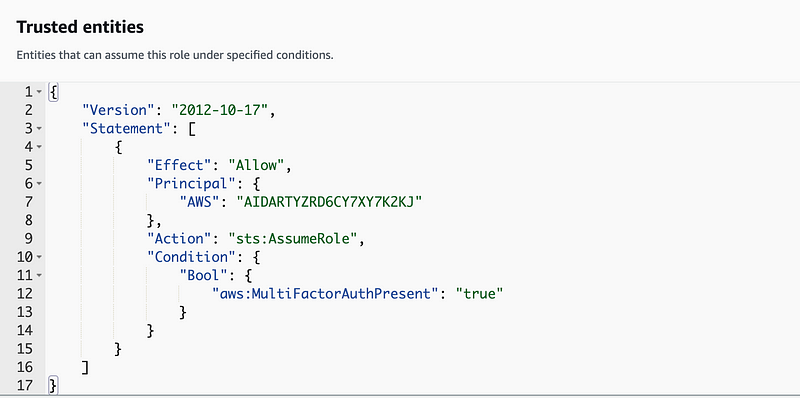
Let’s say you want to fix that.
I’ll just redeploy the principal. Does that work? No because the principal ARN in the policy is now invalid. AWS doesn’t magically restore the ARN when you restore the principal (which is a good thing, but why does it magically change the policy without telling you in the first place?)
I’ll just redeploy the CloudFormation stack that contains the policy, you think. CloudFormation will fix it. Does that work?
No. Refer to my last post on deleted resources and how CloudFormation handles them. It only sees that the template has not changed and won’t do anything.
You can use drift detection to find these problems as explained in the above post.
So what can you do? You can delete and redeploy your stack with the role. This is where micro-templates come in handy because you only have to delete and redeploy specific resources, not an entire stack that deploys a number of different resources.
But then that’s still kind of a pain.
Here’s where the timestamp in my prior post comes in handy — sometimes. I got this to work when updating certain resources, but at the moment it is not working for my trust policy anymore. Not sure if something changed with the way CloudFormation works or it only works with KMS Key policies.
I add a timestamp parameter:

I add the timestamp to my outputs:
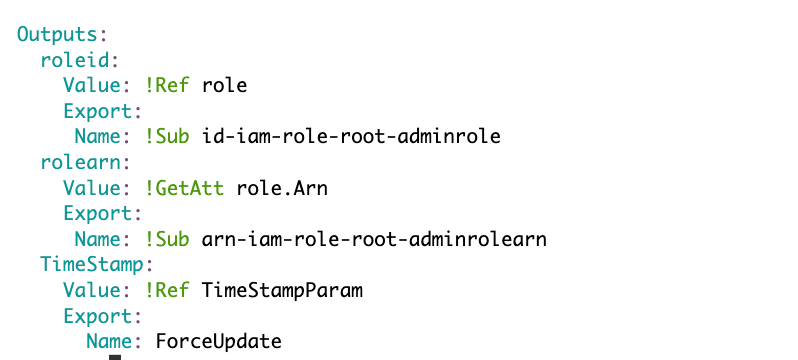
That causes CloudFormation to think I’m deploying something new because I changed a parameter and an output. My stack redeploys and the ARN in my role gets updated.
Well, it was working. But it’s not working for my current role trust policy issue.
We can try another approach. Can we change the SID?
Let’s try that. I didn’t have a Sid (statement identifier) in this policy so I added one:
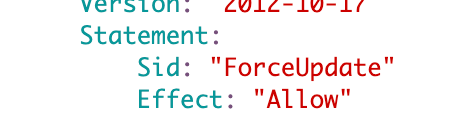
That worked. That change caused CloudFormation to deploy the stack over again and update my trust policy. I didn’t actually update the policy permissions, but I was able to get the policy to redeploy by changing the SID and get the correct ARN back in the policy.
If you have a policy that repeatedly causes you problems perhaps you can add a unique value to the SID each time you redeploy it, but note that SIDs do not allow certain characters in them so a timestamp is likely not going to work. I haven’t tried that approach with multiple updates for an existing SID, but I solved my immediate problem.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






