Automation Credentials Versus Console Credentials
ACM.344 Creating the resources to test an EC2 init script that assumes a role with MFA and passes them to a container
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: AWS Security | Secure Code | IAM
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I wrote about how I am thinking about assuming a role with MFA and passing it to a container.
A modification to the prior post
Now as I worked though this post, I discovered a slight problem with my approach. We really need to be able to assign permissions to a specific set of keys, but we can’t assign permissions to keys, only to users. What we need is a separate set of keys that can only assume other roles, otherwise those credentials that can assume a role can do all the other things a developer’s credentials can do.
For this reason, I need to create two users:
- A developer user who is allowed to start an EC2 instance with his or her own specific role.
- An IAM user with credentials that can only assume a specific list of roles. The sole purpose of the second user is to run automation jobs.
This way, we have a set of credentials we can use with the role assumption that can only assume assigned roles, and the Developer can log into the console and do whatever they need to do which is likely more than assume a role.
Take, for example, user credentials. Users generally need to reset their own username and password. We don’t want the automation credentials to have all the permissions a user has, only the ability to assume roles for defined automation batch jobs.
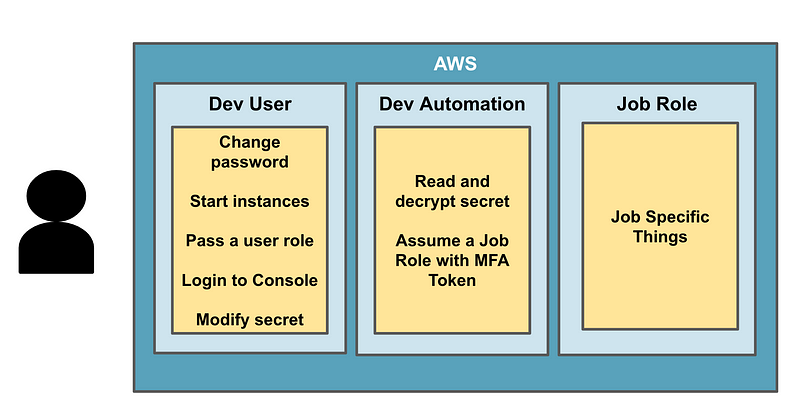
So with that change in mind, I set up the users, roles, secret, policies, the EC2 instance role and modified the batch job role so we can use all that with the EC2 init script.
Create the SandboxDev user
Create the SandboxDev user. Grant the user access to the console.
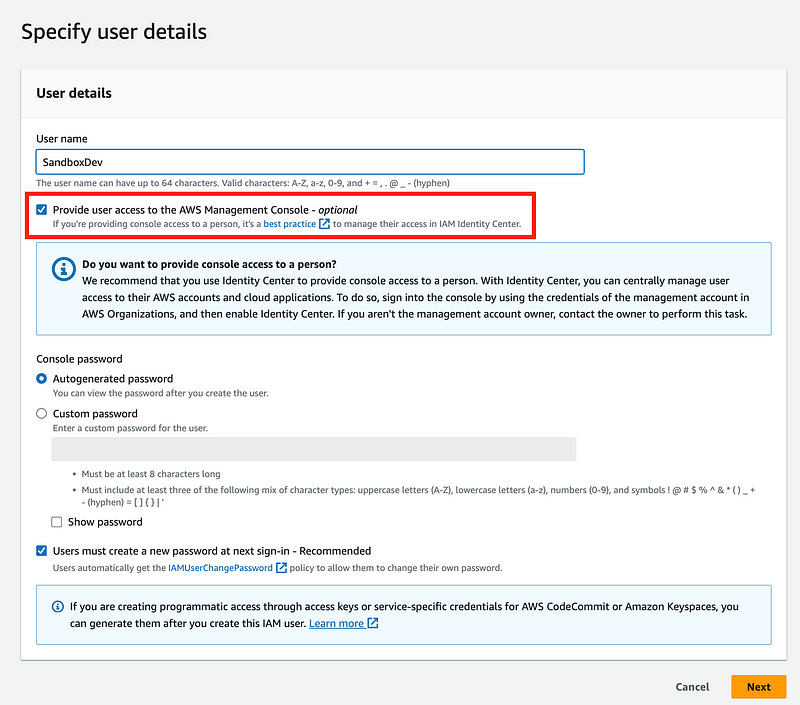
The User needs to be able to do the following:
- Modify their own password and add a hardware MFA device to their own IAM account.
- Create developer credentials (AWS Access Key ID and Secret Access Key) for the SandboxDevAutomation user account.
- Assign a virtual MFA device to the SandboxDevAutomation.
- Edit the SandboxDevAutomation Secret.
- Launch an instance with the user-specific role — SandboxAdminEC2Role.
I have many other posts explaining how to do those things in AWS IAM:
I have a post on how to create a user-specific EC2 instance here:
I covered user-specific secrets here:
Create the user-specific Secret to store the automation credentials
Next I create SandboxDevAutomationSecret in Secrets Manager, encrypted with my Sandbox KMS key.
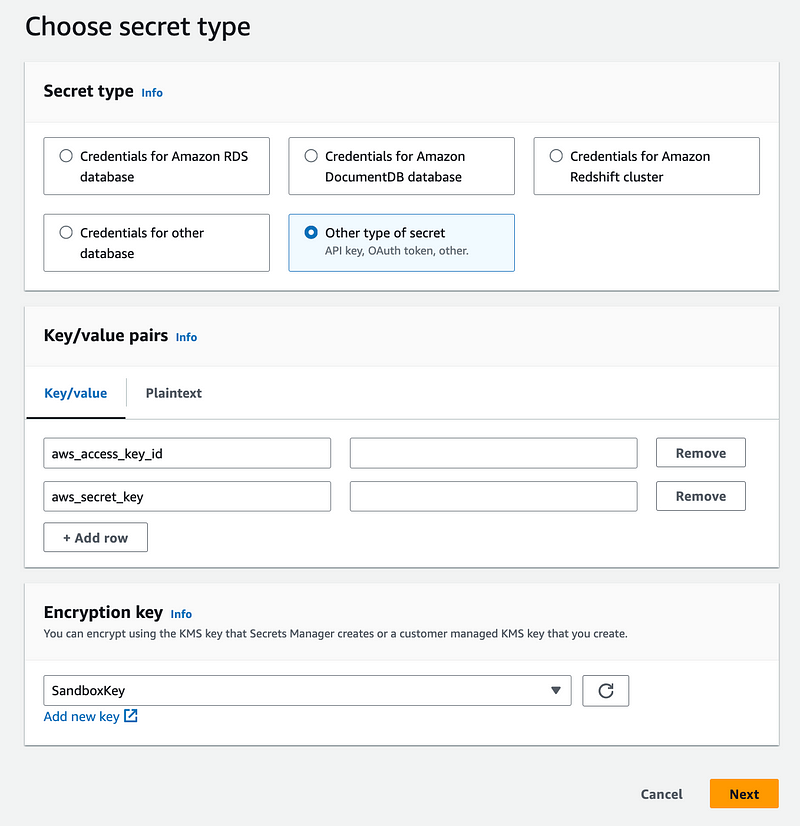
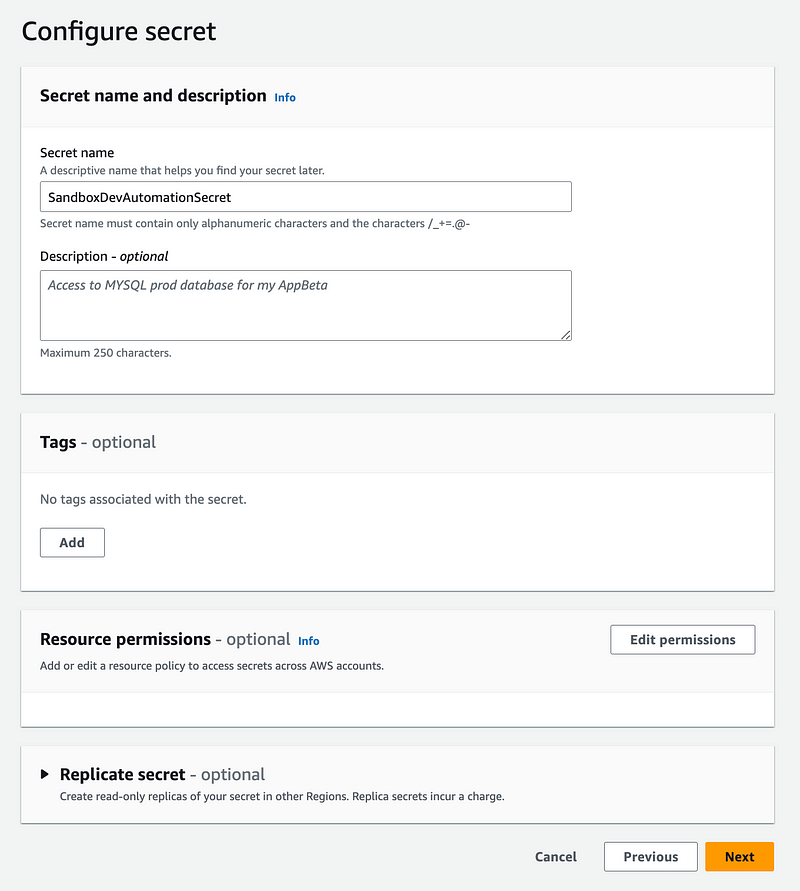
Create a user-specific EC2 instance role for the SandboxDev user
Next I create an EC2 instance role that the developer is allowed to pass to EC2 instances named SandboxDevEC2Role.
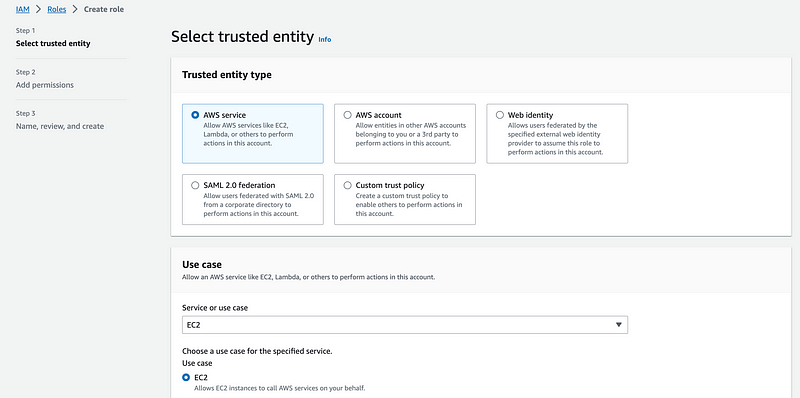
The role will have a prefix with the username:
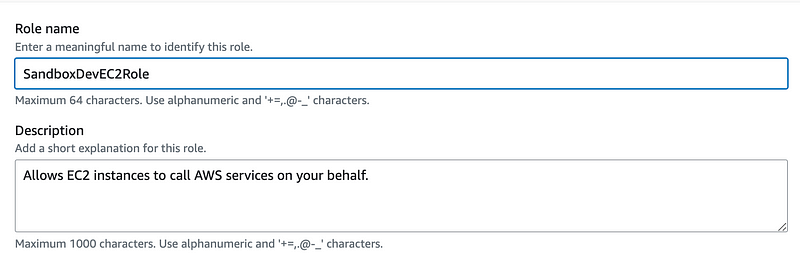
This role is granted access to:
- Read the SandboxDevSecret.
- Pull containers from the sandbox Elastic Container Repository.
- Use the sandbox KMS key to access decrypt the secret and the container in the repository
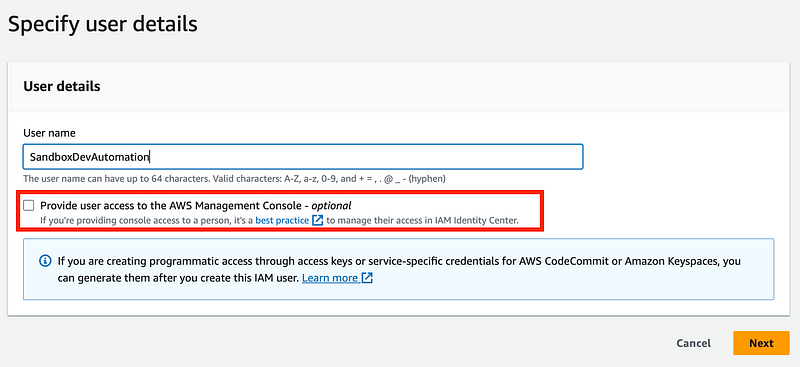
Create the Automation user
Create the SandboxDevAutomation user. Do not give this user console access.
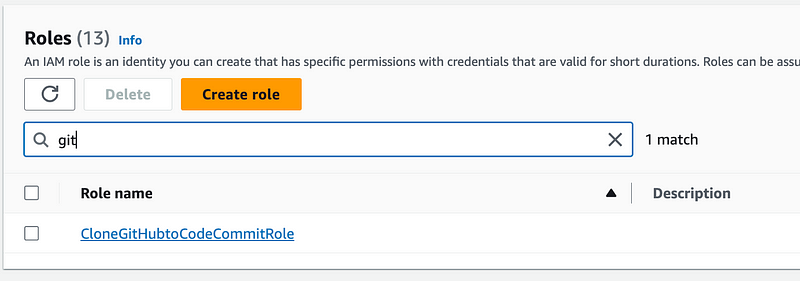
Remember that I already have a role (CloneGitHubtoCodeCommitRole) used by my batch job from prior posts. Create a policy that allows the SandboxDevAutomation user to use STS to assume that role.
The SandboxDev user needs permission to change the credentials and MFA device of the SandboxDevAutomation user.
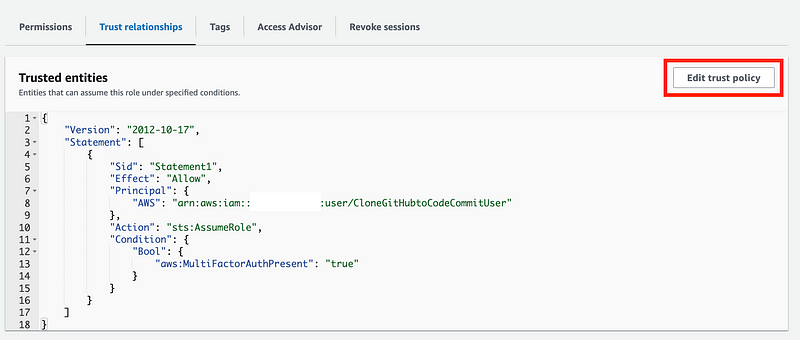
Edit the batch job role trust policy to allow the SandboxDevAutomation role to assume it
We need to modify the trust policy to allow the SandboxDevAutomation user to assume the CloneGitHubtoCodeCommitRole role with MFA.
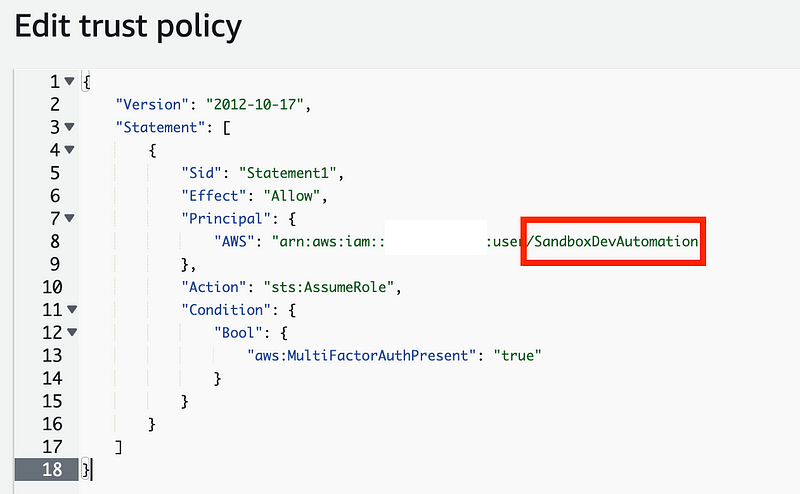
Edit the trust policy:
Change the user to SandboxDev:
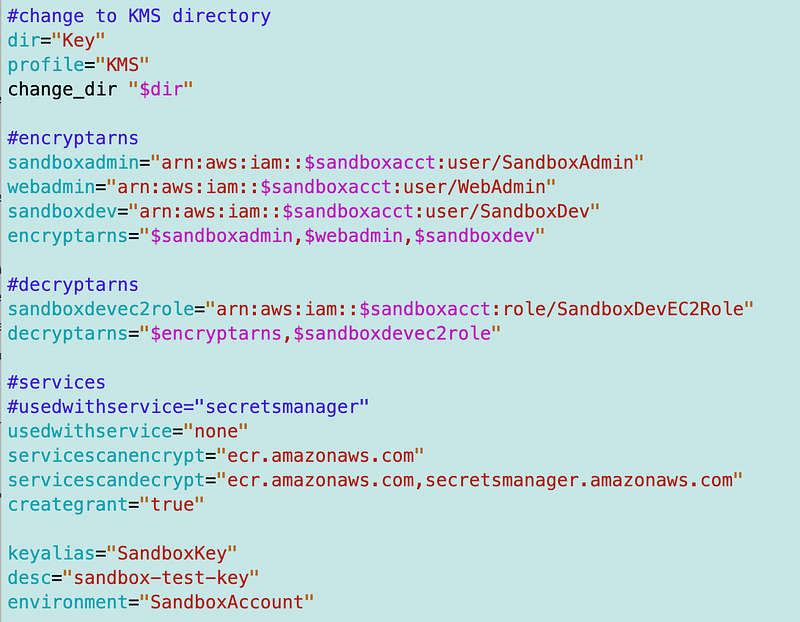
Add permissions to KMS Key Resource Policy
Next I need to allow the SandboxDev user to encrypt and decrypt and the SanboxDevEC2Role to decrypt with the sandbox KMS Key. I edit my automation to add those two roles to the encrypt and decrypt users.
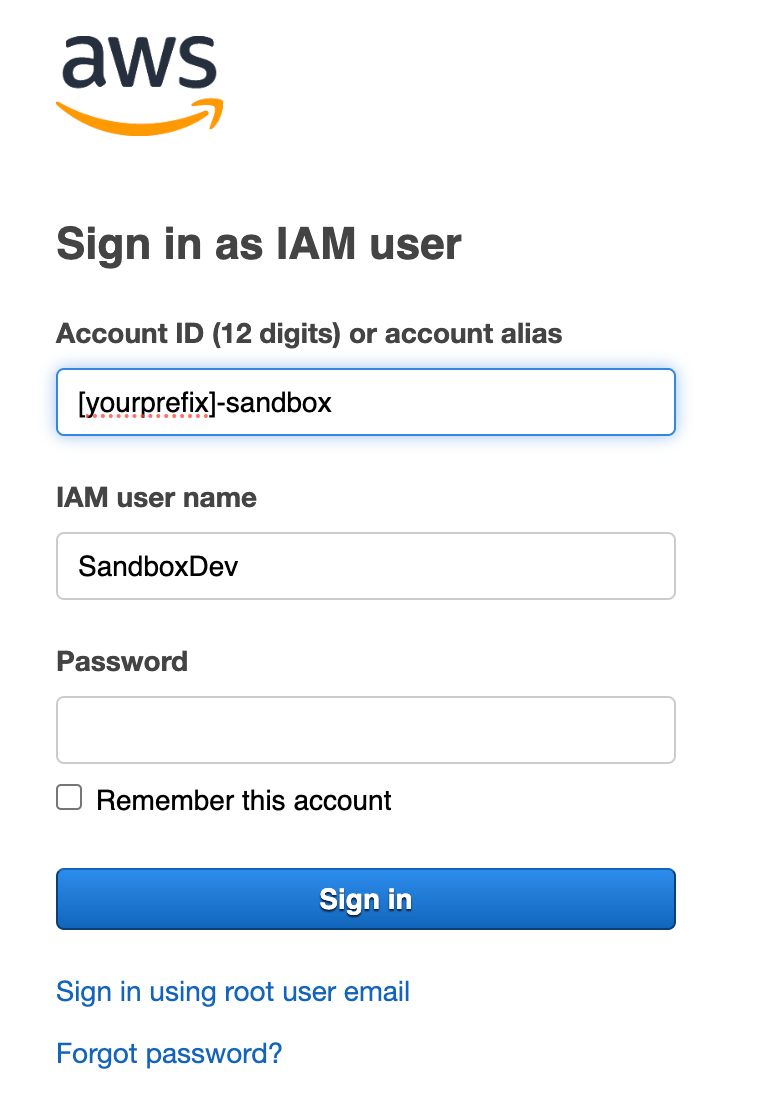
Login as SandboxDev
Log into the AWS Console with the SandboxDev user. If you’ve been following along, you have an account with a prefix specific to your organization and -Dev at the end if you used my deployment scripts.
Add MFA devices
Add a Hardware MFA device to the SandboxDev User.
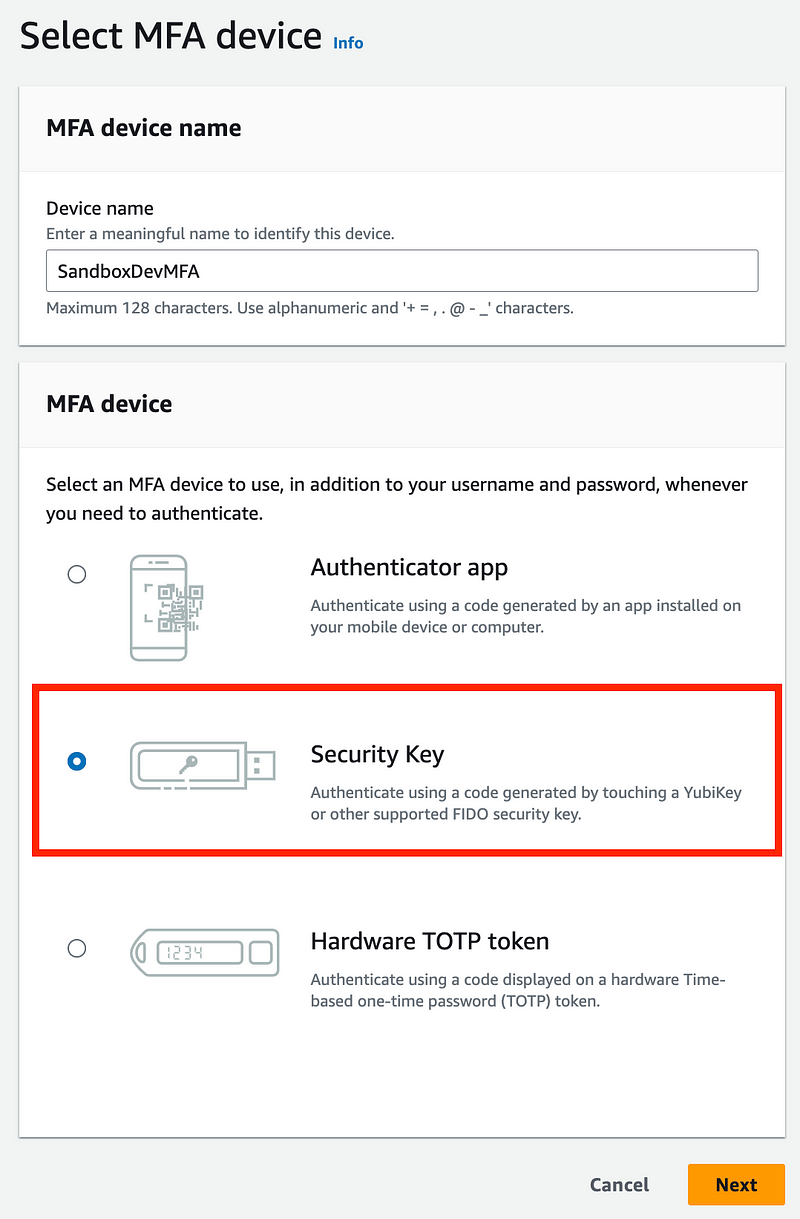
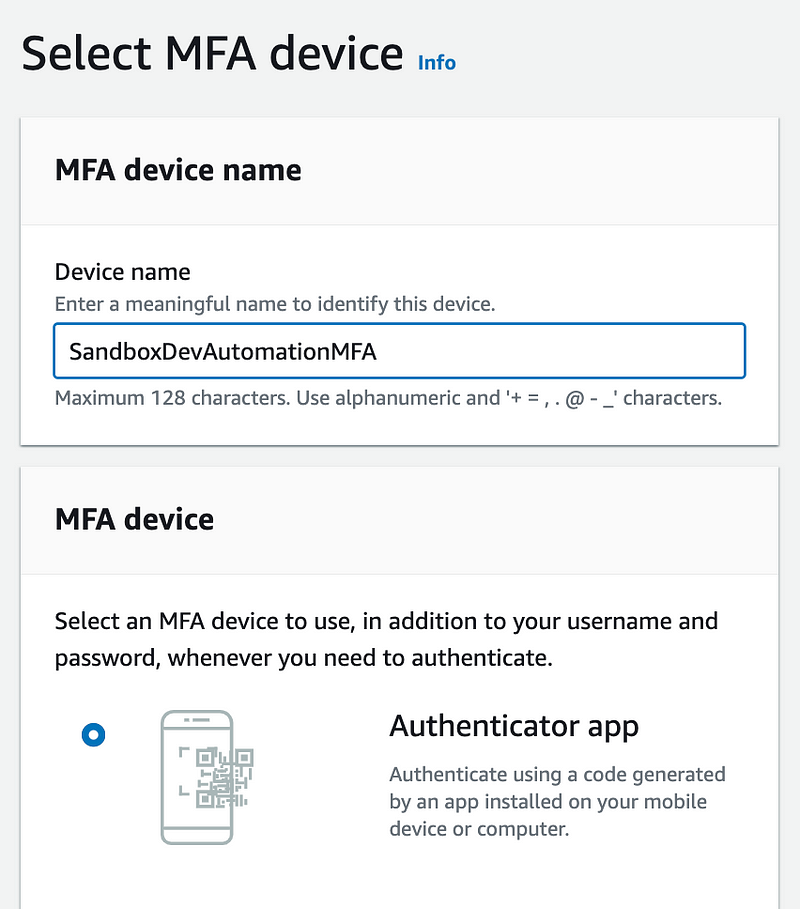
Add a Virtual MFA device to the SandboxDevAutomation User.
I explain why I do not use a Yubikey to generate MFA codes here:
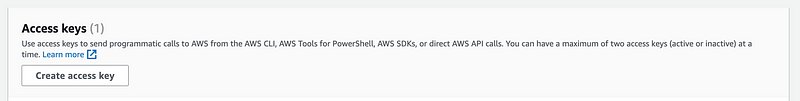
Create automation credentials
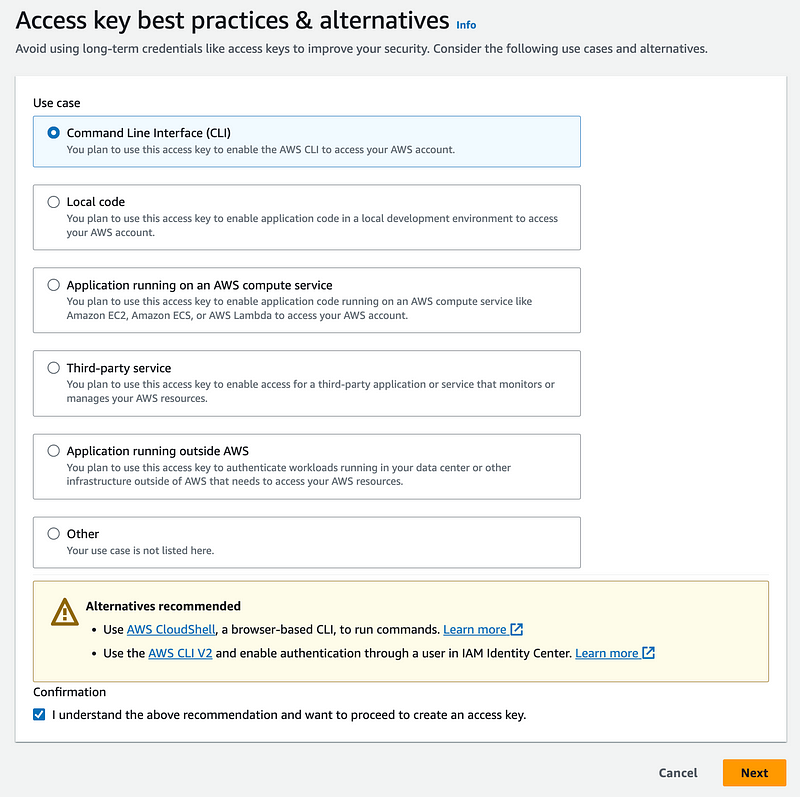
Create an Access key for the SandboxDevAutomation user.
I have explained before that I disagree with the verbiage on this page. The CLI in the browser has a much larger attack surface and it depends how you are using the keys.
Store the credentials in the SandboxDevAutomationSecret
Head to the Secrets Manager dashboard.
Click on the SandboxDevAutomationSecret.
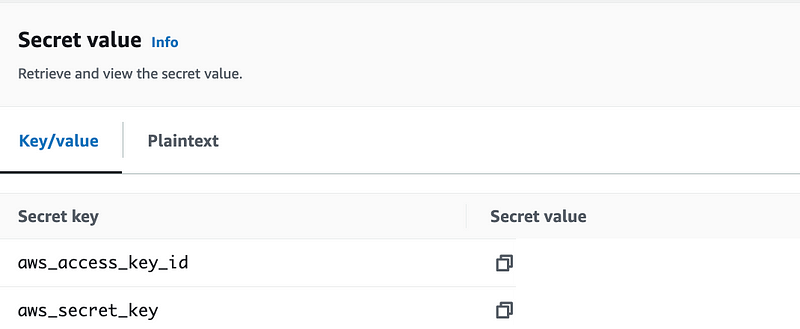
Store the secret key id and secret access key.
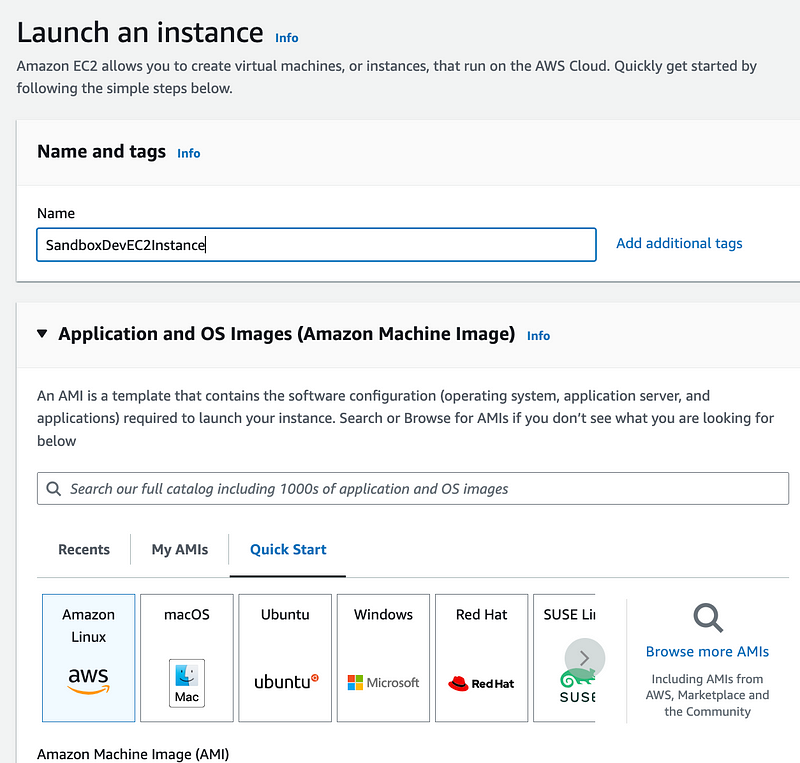
Test Launching an EC2 Instance with the SandboxDev role
Head over the EC2 dashboard and test launching an EC2 Instance. Recall that the Instance name needs to match what we specified in the policy above.
If you need to decode any error messages I explained how to do that here:
Choose the existing networking created for EC2 instances from prior posts.
Choose the role we created under Advanced details.
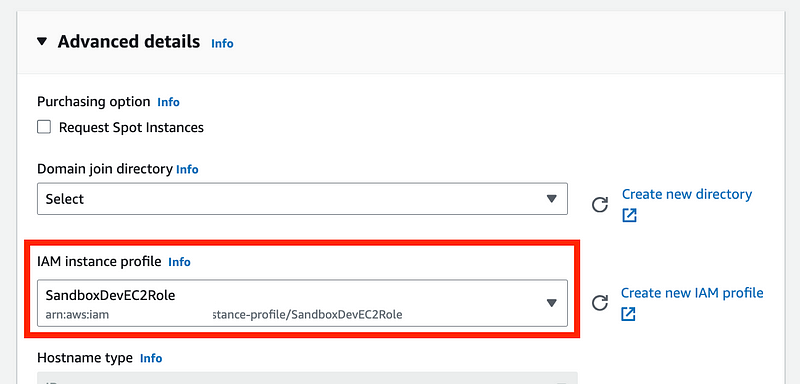
One note that took me a bit to resolve. The message when your user does not have permission to pass the IAM role to the EC2 instance is a bit ambiguous.
Getting the resources setup took some time because I realized I had to revise my approach. I didn’t automate any of this but I will in the future. For now I just want to make sure it works. I can also figure out what permissions each policy requires.
I will test the initialization script in the next post.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
