What to Do About a Recently Discovered SSH Vulnerability
ACM.382 How to protect your SSH connections
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: AWS | EC2 OS Security | AWS Security | Encryption
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I explained why you should check if your AWS CLI is really up to date and how to update it if it’s not.
In this post I’m dealing with a diversion of thought due to the recent discovery of an SSH vulnerability. I want to explain a little bit about what’s at risk and how you can address it.
What happened?
Some security researchers determined that they could read the data transferred over some SSH sessions even though it is supposed to be encrypted. This undermines the whole reason for using SSH in the first place. However, it is only applicable to a certain encryption algorithm.
About encryption algorithms
First, a bit about encryption algorithms. When you “encrypt” something that can mean many different things. It’s generally a bunch of math to take something in a readable form and put it into a scrambled, unreadable form called ciphertext. Only the people that hold the proper “key” or input to a formula can descramble the data and return it to its human readable format called plaintext.
So what’s the formula? Any number of encryption “formulas” or “algorithms” exist to encrypt your data. Some are better than others. Over time certain algorithms are shown to be flawed and new algorithms are developed to overcome weaknesses in older algorithms.
It’s up to you to ensure you are always using the most up to date secure configuration for your encryption algorithms. If you’re not sure which algorithms to use, a lot of people leverage guidance from the National Institute of Standards and Technology (NIST) most commonly just called NIST by security professionals. NIST provides cryptographic standards for different types of encryption algorithms.
If you read my book at the bottom of this post, you already knew that.
Encryption Algorithms for SSH
There are different encryption algorithms that you can use with SSH. One of them is called RSA. That is the particular algorithm that has issues according to this research. If you want to protect yourself against this particular vulnerability you can choose another kind of algorithm that uses a different method for encrypting the data called Elliptic Curve Cryptography (ECC).
When I learned about ECC it was primarily used for encrypting mobile application data because it is lightweight compared to some other forms of encryption, meaning it takes less processing power to encrypt and decrypt the data. But now ECC is more common and recommended for use in most cases.
For example, I wrote about how ECC can be used with GPG here and also referenced NIST for determining the recommended use of ECC.
One of the things I mentioned is that you have to choose the correct “curves” or type of ECC you use. Again, refer to NIST.
So where are you using SSH and how do you fix it?
Well, if you’re using SSH with AWS, you have the option to choose which algorithm you want when you create an SSH key pair.
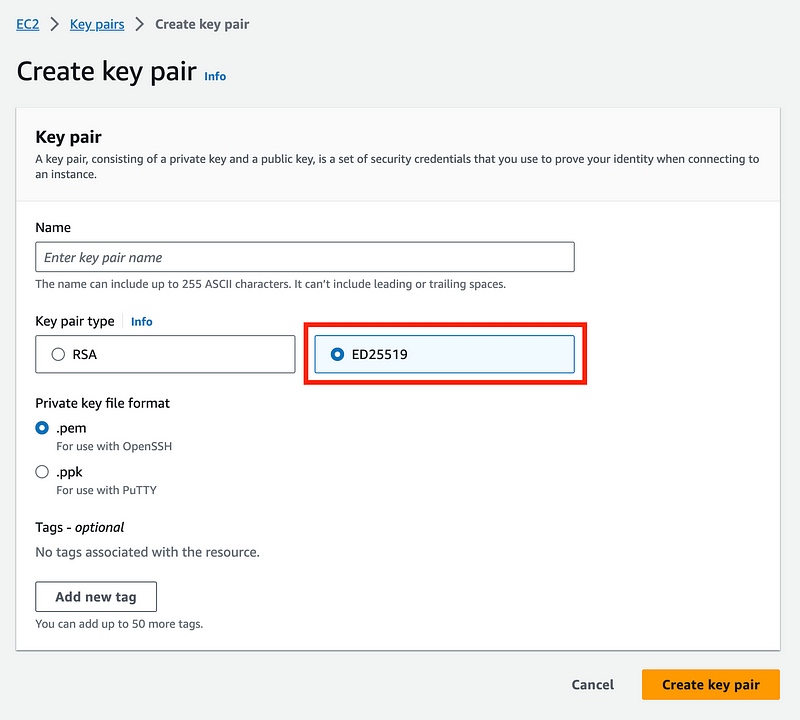
What if you are using SSH keys with GitHub?
From the GitHub documentation make sure you choose the recommended option.
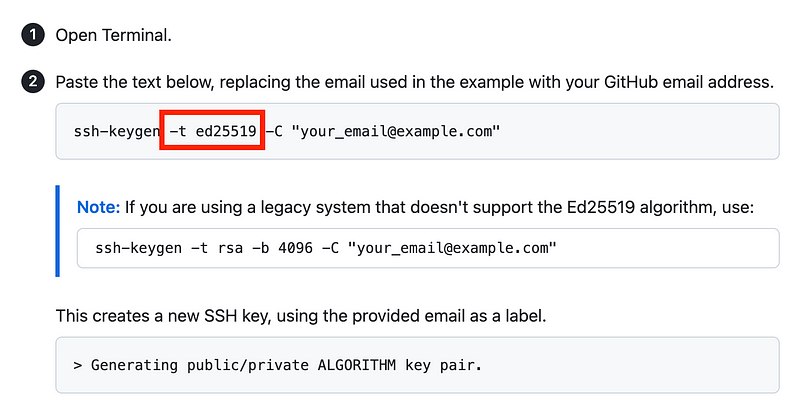
Anywhere else you are generating or using SSH keys likely involves the above step where you choose an algorithm while generating the SSH key. Use that or the latest algorithm recommended by NIST when using SSH keys.
What if I am using a VPN?
Whether or not your SSH traffic is at risk depends on the type of VPN you are using and how it is configured.
- Some VPNs are configured with “split-tunneling” that encrypt some traffic but not other.
- An IPSEC VPN with no split tunneling should be sending all your traffic through a “tunnel” that encrypts all your data including your VPN traffic. This extra layer of protection may help you. IPSEC is yet another protocol to encrypt traffic as it traverses the Internet.
- IPSEC can use different encryption algorithms — like RSA.
IPsec supports a number of authentication keys, including HMAC-SHA1/SHA2, certificate authorities (CAs), RSA, ECDSA, and pre-shared key (PSK). Each key has unique strengths, benefits, and use cases.
- An SSL VPN is likely not tunneling all your traffic as it works at the application layer.
https://www.cloudflare.com/learning/network-layer/ipsec-vs-ssl-vpn/
What if I am using a RDP to connect to remote machines?
RDP is a different, alternative protocol to SSH. RDP solutions have also been subject to vulnerabilities in the past.
https://www.cloudflare.com/learning/access-management/rdp-security-risks/
RDP solutions may be using RSA but this specific vulnerability was reported against SSH. I’ll let the crypto experts sort out and explain the risk and vulnerability.
What if ECC has a vulnerability?
Could ECC have a problem in the future? Yes, and it likely will. In fact it already has. As I mentioned, using the wrong curve or some misconfigured version of the service can cause a problem.
ISACA, another security organization whose conferences I’ve spoken at, describes some of the possible attacks here:
Using ECC is definitely better than RSA but as with all security solutions, your best approach is Defense in Depth as I’ve been demonstrating throughout this blog series and wrote about in my book for executives at the bottom of this post.
Your best bet is to make sure your administrative ports are not exposed to the entire Internet. I’ve explained how to create secure networking on AWS throughout my latest series and written about security for home networks as well.
Preventing the attackers from connecting to your host does not protect the data in transit. The attackers may be able to see it as it traverses the network. However, if they steal credentials in that traffic used to connect to that host, they won’t be able to use them to gain access to your entire network potentially.
Now back to what I was writing about — a container that requires MFA for AWS deployments.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
