Storing a GPG / PGP key on a Yubikey
Moving a GPG key to a Yubikey and using it from there to encrypt documents
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Encryption | Cybersecurity
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I wrote about GPG here and how you can use it to protect documents transmitted in email.
I tried this once before but somehow my key got corrupted. I stored my GPG key on a Yubikey. I’m going to try this again.
Compatible keys
The following post is from 2020 so I’m not sure how up to date it is, but the first thing you need is a compatible key.
Check out this post or the documentation for your particular key to see if it is compatible. That post has drop down pictures of the different types of keys as well which is pretty cool.
Now what’s odd in my case is that I think I have three compatible keys, but two of them do not work. I know that I used one of these keys in the past to store a GPG key. I am wondering if the problem is that I used one key and then from there out the other keys don’t work? I’m not sure.
The last time I tried this, I used my Yubikey to store a GPG key on one machine and then use the Yubikey on another machine and it didn’t work. It was at this point I could no longer get into the key with the pin and essentially had to reset it. I’m following the instructions from Yubikey for all of this, and there are some strange results occasionally, but I’m going to try it again and see if it works this time around.
OpenPGP (GPG) pin
It was at this point I learned that my Yubikey had a pin for OpenPGP. Yubikeys are not only for logging into websites.
If you haven’t set a User PIN or an Admin PIN for OpenPGP, the default values are 123456 and 12345678.
To set the admin pin you might try this method:
gpg --card-edit
[the prompt will change to gpg/card]
passwd
[will show you the card number detected.]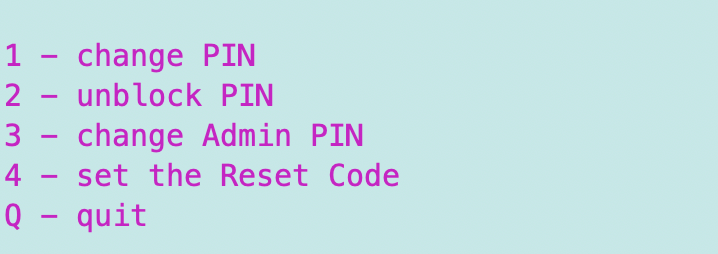
Enter 3.
Enter the default admin pin.
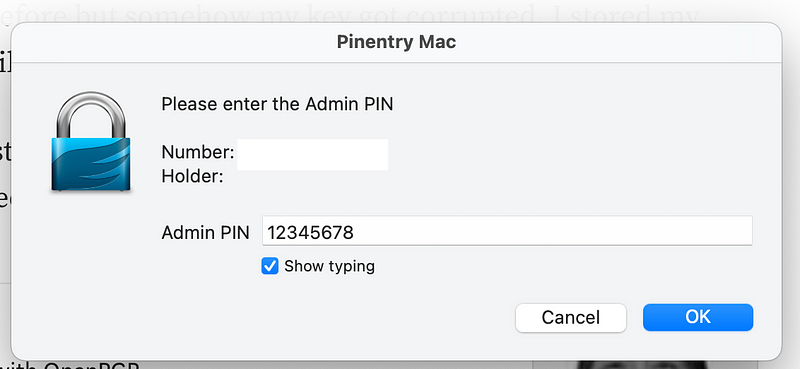
Enter a new pin twice.
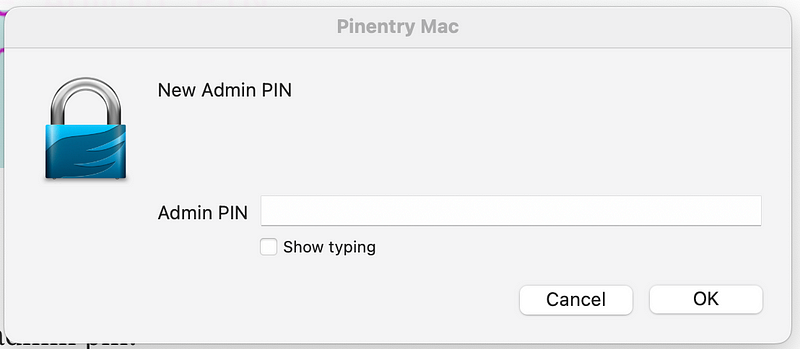
Repeat the process for the non-admin pin.
Here’s where things are really odd. After setting my pin, it was as if it didn’t save. The pin kept reverting to the default pin. I think perhaps the problem was that I was initially setting a pin that was too short, but I’m not sure. I am still not sure how I got it to work, but I have changed the pin now and rebooted and the new pin still works. We’ll have to see if it continues to work.
Here’s some other odd behavior related to passwords.
This whole process seems a bit fragile. For something that stores encryption keys it seems like it would be more robust.
Test your pins
Now, before you do anything else, test those pins and make sure they work!
I think this is the mistake I made last time. If you don’t know your pin you can run out of retries. I may have thought I set the pin when I didn’t or perhaps I didn’t actually reset it. So test your pin.
In my case, I rebooted my machine, and then tried to use the passwd command again. The first few times I tried it, the pins reverted to the defaults, like I just explained.
Hopefully they are now set.
Resetting your Yubikey pins
If you don’t know the pin for a card you can reset it, but you will lose any keys on the card.
One of the ways to reset your pins is to download and install the Yubikey manager software. Personally, I don’t want that installed and running on a machine where I’m activity using my key to access websites. If I need it, I install that on a separate computer and use it there, where I manage my keys. That way that software is not available to make modifications to my keys if something should become compromised on the machine where I’m working.
I wrote about that in relation to using a Yubikey as a second factor for the AWS CLI, which requires you to install Yubikey software, here:
Though I love Yubikeys, I don’t use a Yubikey as a second factor for the AWS CLI. For each security control or tool you need to understand how and where it is most applicable.
Here’s how to manually reset your key if you need to do that (paraphrased from the above article):
Insert the YubiKey into a USB port.
Run the GPG command:
gpg --card-status.
If you receive the response "gpg --card-status"
fails, terminate gpg-agent and gpg-connect-agent processes,
then try again, or you can reboot.
Run
gpg-connect-agent --hex
If PIN retry counter from step 2 is greater than 0, enter the command:
scd apdu 00 20 00 81 08 40 40 40 40 40 40 40 40
Repeat the above command until one of the following occurs:
* YubiKey 4/5 Series device reports "D[0000] 69 83"
* YubiKey NEO device reports "D[0000] 63 C0"
If Admin PIN retry counter is greater than 0, enter the GPG command:
scd apdu 00 20 00 83 08 40 40 40 40 40 40 40 40
Remove and re-insert the YubiKey.
Terminate gpg-agent and gpg-connect-agent processes (or restart).
Run the GPG command:
gpg --card-status
Confirm the PIN Retry counter is as follows:
"3 0 3" on a a YubiKey 4/5 Series device
"3 3 3" on a YubiKey NEO deviceIt also seems like the clear command might do something to reset the card, but I’m not sure. Use at your own risk or do additional research.
Key and file backups
The point in the first article on generating the key externally is valid! If you generate the key directly on the device you can’t back it up. If anything happens to your Yubikey, you won’t have access to your data that you encrypted with that key.
But the good thing about generating the key on the device is that it doesn’t exist on some other device that may become compromised later.
You could also make multiple copies of the data encrypted with different keys. That way if something happens to one device or key, you can use a different device or key to access the data. That is an approach I generally take. I have different computers for different purposes and back things up in multiple places.
Generating a GPG key
I explained how to generate a GPG in this post.
Recently I’ve been reading some articles about weaknesses in GPG. One of the options for generating a GPG key is to use a newer encryption algorithm called ECC (Elgamal). I’m not going to get into that here because it is too much for one post. Be aware that use of ECC requires using appropriate curves. And just to be clear, ECC is better than RSA.
Check out NIST 800–186 for more information.
For now I’m going to generate a key using the mechanism described in my prior post.
To create a backup of your key:
Before sending your key to your Yubikey, create a backup.
Insert the YubiKey into your computer.
Get your GPG key id by running the following command:
gpg --list-keysRun the following command where 1234ABC is your GPG key ID:
gpg --export-secret-key --armor 1234ABC Store that key in a safe place as a backup. In my case, I store the key on a computer I don’t log into on the Internet except to get updates and I work on a separate computer where I use my Yubikey.
To import the key on your YubiKey:
Run the following where 1234ABC is your key id.
gpg --edit-key 1234ABC
keytocard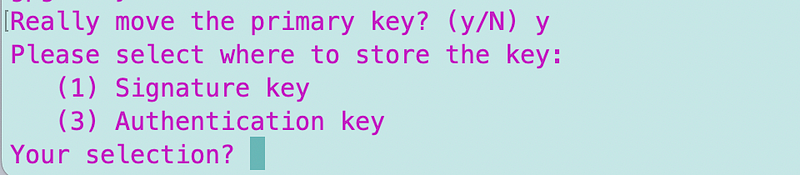
Enter y
Enter 1 to move the signature subkey to the YubiKey.
Enter the commands:
key 1
keytocardSelect 2 to move the encryption subkey to the YubiKey.
Enter the commands:
key 1
key 2
keytocardSelect 3 to move the authentication subkey to the YubiKey.
Enter the command:
quit
yNote that if you’re not using your GPG key for authentication the step to move the authentication key will not be necessary and will fail. You can see the [A] attribute associated with your GPG key if you are using authentication. Otherwise you might only see [E] for encryption and [SC] for signing and certification.
Note that you also may need to change the attributes of your card to allow the type of encryption and key size you want. See the commands below.
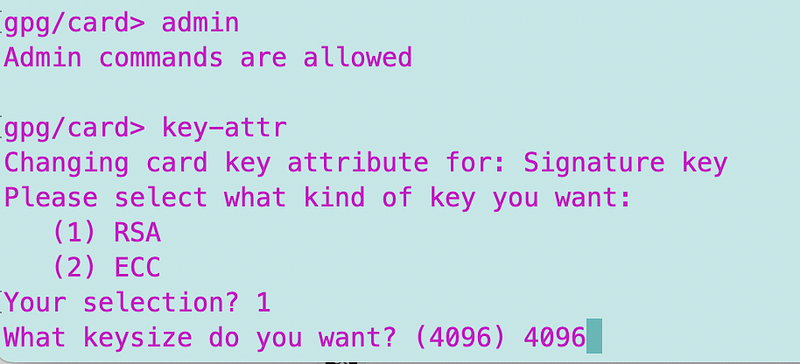
Verify the key is on your card
Now when you run the following command:
gpg --card-editYou should see your key at the bottom of the information about the card.
If you run the following command:
gpg --list-secret-keysyou will see the card serial number associated with your private key.
Still testing…
Now you can try to encrypt a document with your private key. Initially when I went to encrypt the document, it said my pin was incorrect yet again. I used the admin pin to login and reset the pin for the device. Then encryption worked.
Once I encrypt a document, I no longer have to enter the pin.
If I remove the key, I get this message:
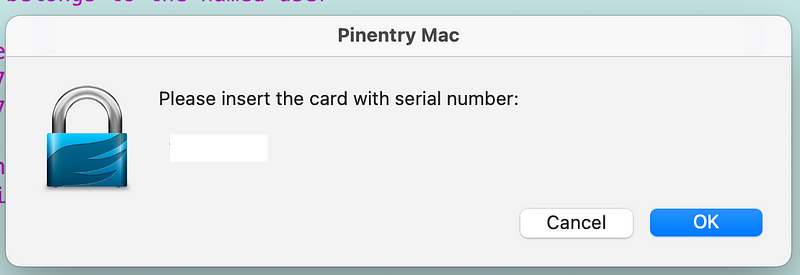
I’m still testing this out but it seems to work so far. My private key should be more protected presuming it’s not still stored on my laptop somewhere or hanging out in memory accessible to an attacker after running commands.
One thing you can do to prevent access to the commands I’ve been running here would be to unplug your yubikey when not in use. I didn’t have to click any buttons to run these commands after entering the pin the first time.
When I use the Yubikey to encrypt a document, I find it odd that I have to put in the pin rather than push the buttons on the Yubikey. In any case, it seems a bit safer than having the key on my laptop where anyone that gets access to the machine while I’m logged in can use it.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
