Restricting Access to Invoke Lambda Functions to an IP Range in a Service Control Policy
ACM.312 Applying a policy to an OU to restrict Lambda actions to a specific Public IP address
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Lambda | Container Security | Application Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I explained some of the limitations when trying to create network restrictions to limit who can invoke an AWS Lambda function.
In this post I’ll deploy a Service Control Policy that limits access to invoke functions in the Sandbox Organizational Unit to a specific IP address.
Here’s an example:
First I deploy a policy with the incorrect IP address called RestictInvokeLambdaSandbox.yaml.
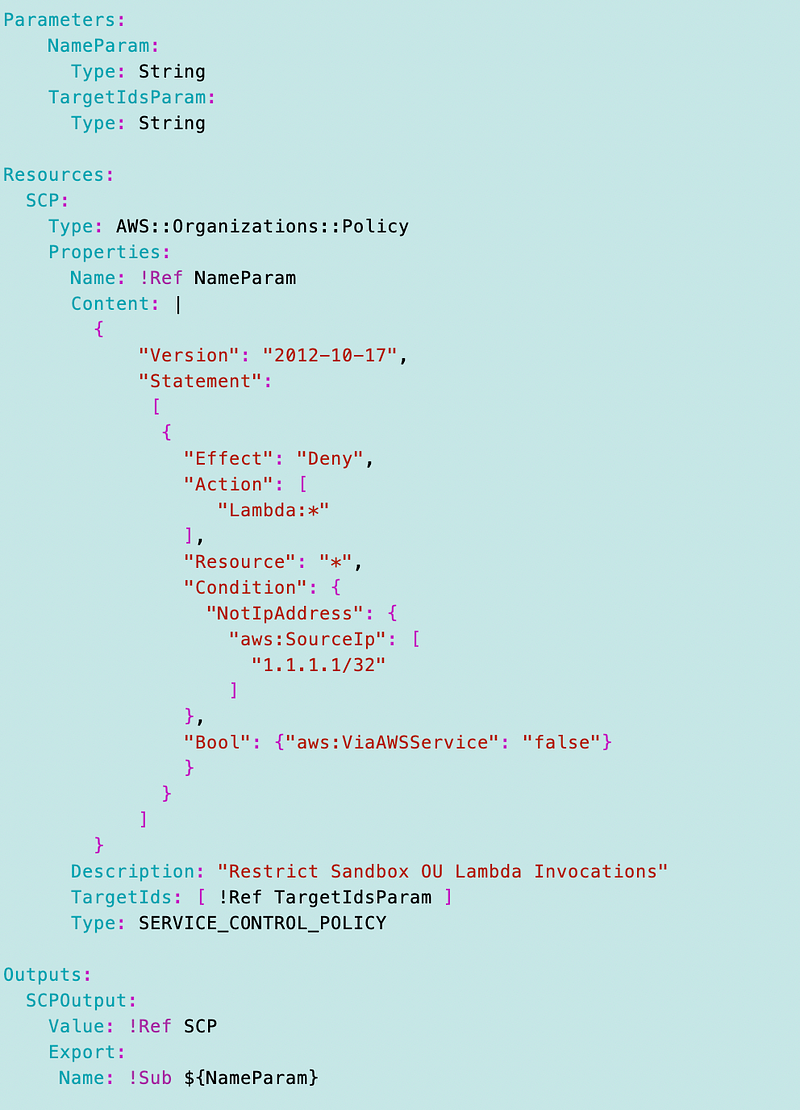
I’m using my common deployment mechanism described in earlier posts.
Next I can run my invoke script from prior posts to see if I can execute the function. No. It fails. Good.
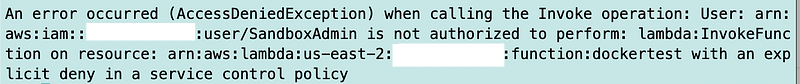
Now change the IP address to my EC2 instance IP address.
Now change the IP address to the correct IP address and it works.
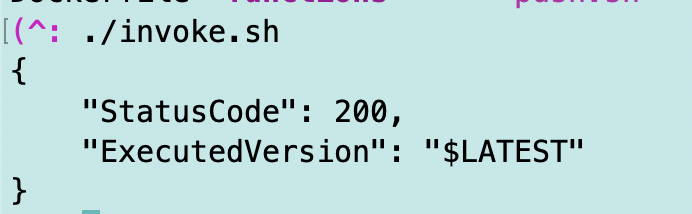
Note that I’ve restricted all Lambda access above. That means I’ve limited console access as well.
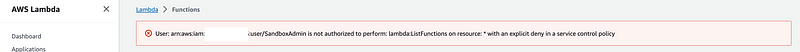
You’ll need to allow all IP addresses for the console actions or limit the policy to the Invoke action if you only want invocation from that specific IP or range.
What if we want to restrict access to a private IP range in a specific AWS account? I’m going to try that out in the next post.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






