Programmatic Governance in Azure
Multicloud.6 Using Azure ARM or Bicep templates to govern all the things
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Multi-Cloud Security | Azure Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I could write so many more things about IAM and little details you should know about all three cloud services but I really just want to give you some code. Because the more we can automate consistently, the more time we can save and the more errors we can prevent.
So I wanted to show you how to programmatically create a few things pertaining to governance on Azure.
In this other series I’m working through at the same time, I’ve been creating nearly every single resource with AWS CloudFormation templates.
Although that code is specific to AWS, the concepts are the same in Azure. You can create what are called Azure Resource Manager (ARM) templates in Azure to do the same thing. ARM templates define the resources you want to deploy. Then you execute commands to deploy them.
I particularly like this feature:
Modular files: You can break your templates into smaller, reusable components and link them together at deployment time. You can also nest one template inside another template.
I just wrote about Micro-Templates for AWS (a term I made up).
I particularly do not like this feature:
With deployment scripts, you can add PowerShell or Bash scripts to your templates. The deployment scripts extend your ability to set up resources during deployment. A script can be included in the template, or stored in an external source and referenced in the template. Deployment scripts give you the ability to complete your end-to-end environment setup in a single ARM template.
That feature misses a key point of templates that define your resources and infrastructure. They should not include executable code. The executable code should be used outside the templates to call and manage the templates. The templates themselves should only describe resources. Likely that add-on exists due to features lacking in templates that may exist in the Azure CLI or PowerShell commands.
You can think of the distinction of separating executable code from a description of the resources like the distinction between a control plane and a data plane. Kind of. The control plane controls the deployments. The data plane does its specific job — whatever that application is supposed to do. A template should only deploy the resources defined in it, not go off and do a bunch of other things in a free-form script. At least not if you want to reduce risk in your deployment process.
You can write Azure ARM templates in either JSON or a Microsoft specific language called Bicep. Most developers want to learn things that are universal and span multiple cloud platforms when possible, so I’m not sure why Microsoft uses Bicep instead of YAML. But they did, and it seems like a lot of Microsoft-only developers are using it. Both JSON and YAML can be a bit abstract to grasp when you first start using them. However, both are much more powerful than a language designed to work on only one platform. If you learn JSON it will be applicable in many other scenarios. If you learn Bicep you can only use that on Azure and Microsoft platforms.
For that reason, I’m going to use JSON for my examples. If you’re trying to learn JSON and Azure ARM templates, some of the tips I provided for AWS CloudFormation templates are also applicable to Azure ARM templates.
It helps to understand the sections you can add to a template. Those are defined here:
Example:
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "",
"apiProfile": "",
"parameters": { },
"variables": { },
"functions": [ ],
"resources": [ ],
"outputs": { }
}One of the tips above was to find the list of all possible resources you can create with AWS CloudFormation templates. Here is a list of resources you can create with Azure ARM Templates.
Thinking about governance what, type of resources might we want to create? I can think of a few:
Azure Account - Maybe.
Azure Tenant
Azure Management Group
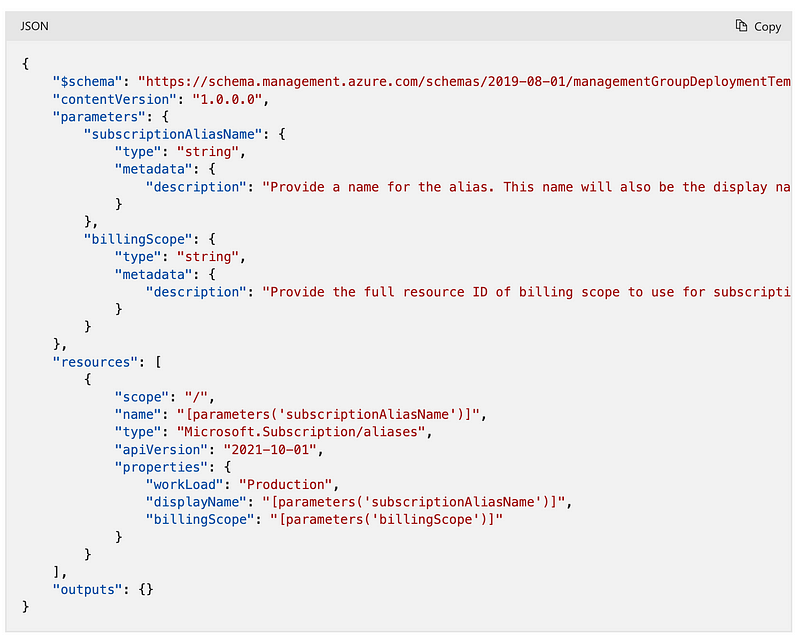
Azure Subscription
Azure Policy
Azure InitiativeThe other thing is, if we want to follow best practices and not use the root user for deployments we need to create a new organizational root user like I did for AWS here.
Those are just a few things to get us started. How many of those things can we create with Azure ARM templates?
Well, first of all, although Microsoft says Azure AD has become Entra ID, pretty much all their documentation says Azure AD still. That’s not confusing at all. There are no entries in the documentation for Entra ID. So if any of my links break in the future, head back to this portal and search for Entra ID wherever I have written Azure AD.
Azure Accounts
Can we create an Azure account with an ARM template? Well, I don’t see a way to do that. But in my case I really only ever have one or maybe two Azure accounts. I might have one for testing new class material but most of the time everything is completed in a single account. I’m curious as to how many people use multiple Azure accounts and why. If you would like to discuss this, come hang out with me at the IANS event in October and we can discuss. These sessions are not only for me to talk but for others to share information. As mentioned, sorry no vendors but vendors can hold their own sessions and showcase their products.
So anyway, I don’t see a way at the time of this writing to programmatically create an account but I am not sure there’s a real need for that either. Unlike AWS you probably won’t be creating a lot of separate accounts.
Azure Tenants
Let’s search for Azure Tenants in the list.
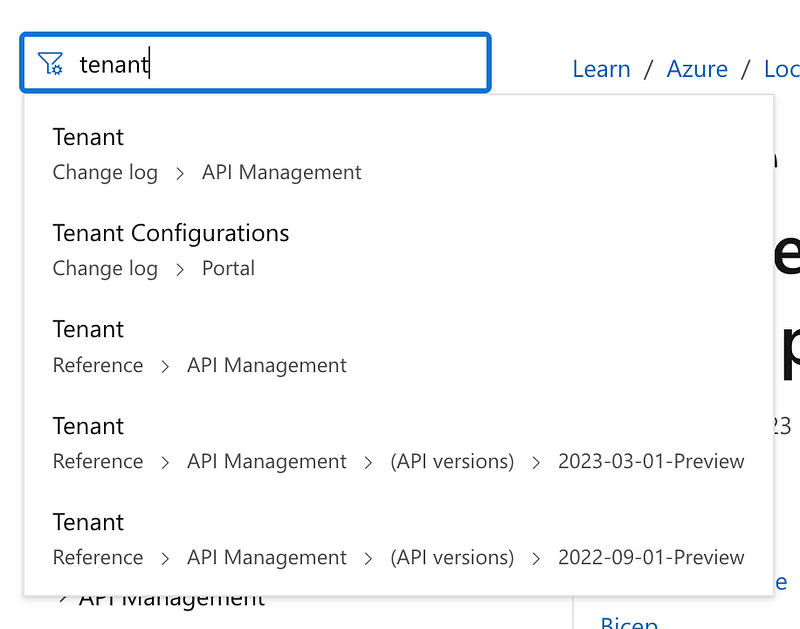
I only see some tenant settings that you can control with an ARM template and a tenant for API management. API Management is Azure’s API Gateway solution. This isn’t referring to an Azure AD (Entra ID) tenant.
https://azure.microsoft.com/en-us/products/api-management
It looks like we cannot programmatically create a tenant. Chances are, you won’t be creating a tenant that frequently. So perhaps you don’t need this so much. But what if disaster strikes and you do for some reason need to recreate your Azure account resources? There are some tenant settings that impact visibility and upon recreation of perhaps duplication of a tenant to create a copy for testing, you’ll want to make sure all those configuration settings match.
Here’s one that you will definitely want to know about. As Global Admin in your Azure account, you may or may not be seeing all your subscriptions and resources. You need to elevate your privileges to do so. I find it odd that you do not see everything by default but that’s the way it works.
You can programmatically change this setting, but it is not something you can currently control with an ARM template.
That means there’s no way to check to see if a configuration no longer matches a template that defines how the item should be configured. It also means that you’ll need some other way to track and manage what these configurations should be and ensure they are re-deployed properly in the event that you do need to redeploy a tenant in your account.
To deploy a tenant with a command line script you can use the following Azure CLI command or the related PowerShell command and add whatever other commands you need when the configuration of your tenant needs to be altered. As I’ve done in my AWS Scripts, you’ll need to make sure the script works for create or update. On deletion you may have to reverse some of the commands due to dependencies.
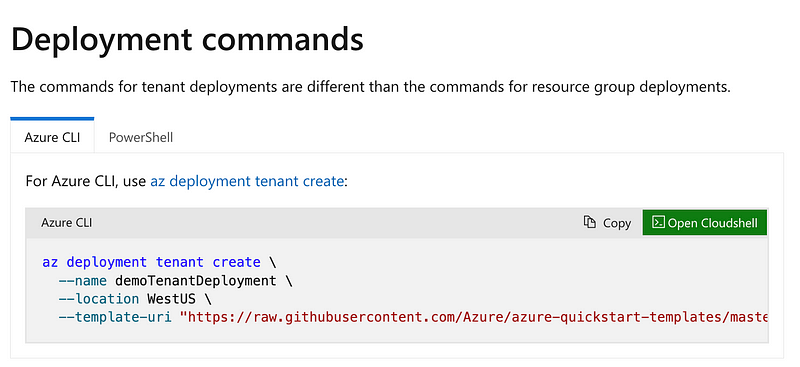
This is where scripts come into templates, but would rather keep the two separate for the reasons I mentioned above.
Azure Management Group
Now lets see if we can use an ARM template to deploy a management group. Seems that we are in luck.
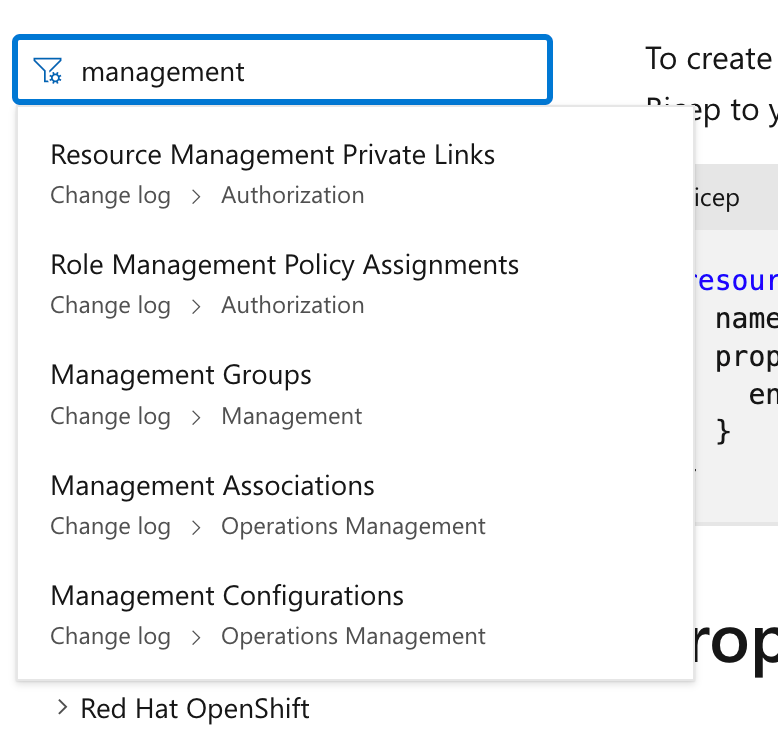
The document is a bit confusing here because it links me to change logs but if you scroll to the bottom there’s a link to the management group page.
Click on the Middle Button at the top for an ARM template. Apparently ARM refers to JSON otherwise it’s a Bicep template. You can also find the code for Terraform here. I’ll write more about Terraform later but I wonder while reading this if this page will be affected by recent Terraform license changes.
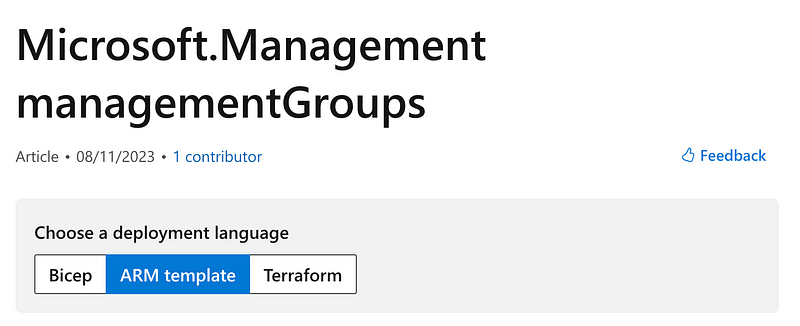
The format for a Management Group template looks like this:
{
"type": "Microsoft.Management/managementGroups",
"apiVersion": "2021-04-01",
"name": "string",
"scope": "/",
"properties": {
"details": {
"parent": {
"id": "string"
}
},
"displayName": "string"
}
}The name can be anything within the naming convention standards. The value for the parent id…is not entirely clear at first glance. Again, the AWS documentation wins here. Though some people don’t like that you have to click a link to drill into AWS properties I find this layout confusing. Maybe I’m just not used to it. The id is a child of parent which is a child of details which is a child of properties.
Click on the link next to properties to see the dtails.
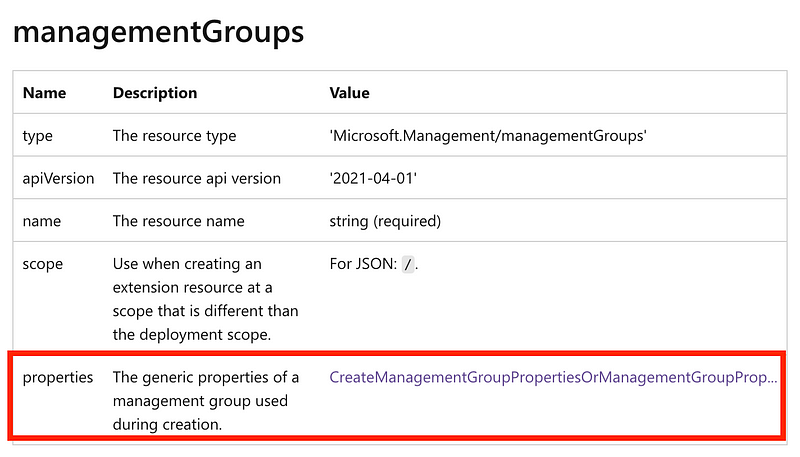
Click on the link next to details.
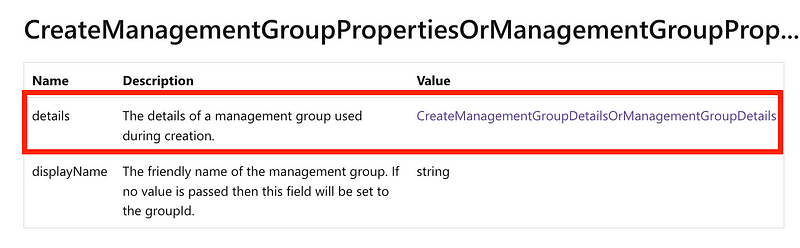
Click on the link next to parent.
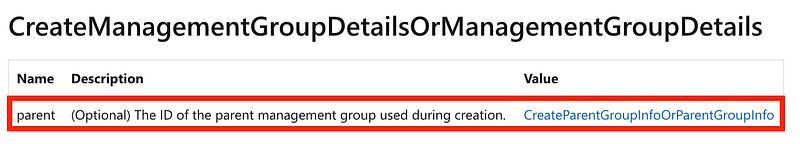
That should take you to id but it’s right under the above on the screen so clicking that link does nothing for me. Here’s the description for ID. The id of the parent refers to another management group and it is optional. You can nest management groups within other management groups to create the hierarchy you want as I described in the last post.
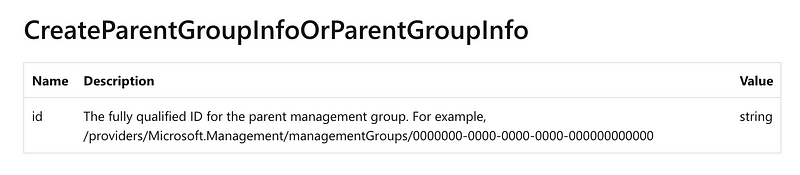
Subscriptions
Next we want to create subscriptions so we can add resources to those subscriptions. There are a number of options for subscriptions, but we’ll go with the one under Management since Management Groups were also under that category.
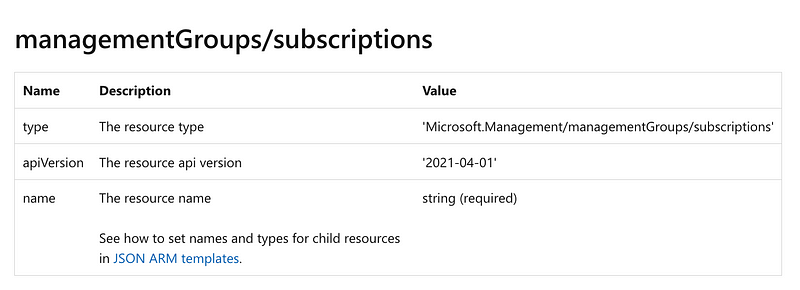
That takes me to a change log so I have to click the link to get to the resource.
Well this is not what we want. This only has a name. If you look under remarks, this resource type is used for moving subscriptions into management groups, not creating them.
None of the search results seem to make sense to me. But if you just scroll down the list there’s a resource for subscriptions:
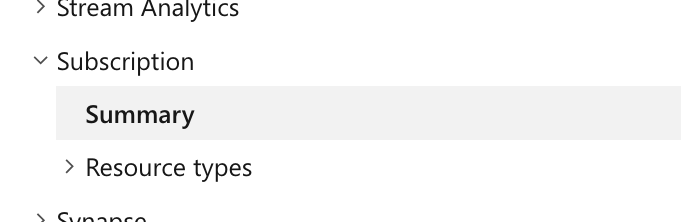
If you take a look at that, it has something about EA an EA DevTest agreements in the description. This is where all the Microsoft licensing options come into play.
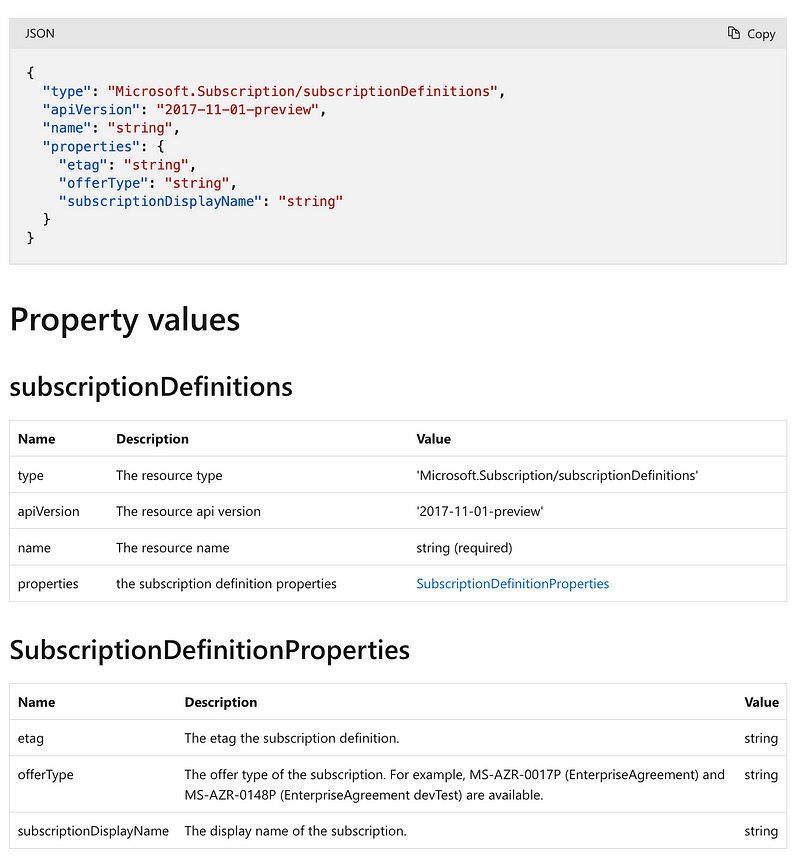
Well I don’t think that’s what we are after. Upon searching further it appears that you can create subscriptions with the REST API if you have one of the following types of agreements only:
- Enterprise Agreement (EA)
- Microsoft Customer Agreement (MCA)
- Microsoft Partner Agreement (MPA)
Here’s where Microsoft licensing complexity comes into play again as I’ve mentioned in prior posts. On AWS I was able to easily create my account structure using CloudFormation. The same is not true on Azure with Azure ARM Templates. Maybe it will be in the future. For now, we need one of the above agreements. For each different type of agreement you must create the subscription in a different way. Here are what the different requests look like for each type of subscription:
Enterprise Agreement (EA)
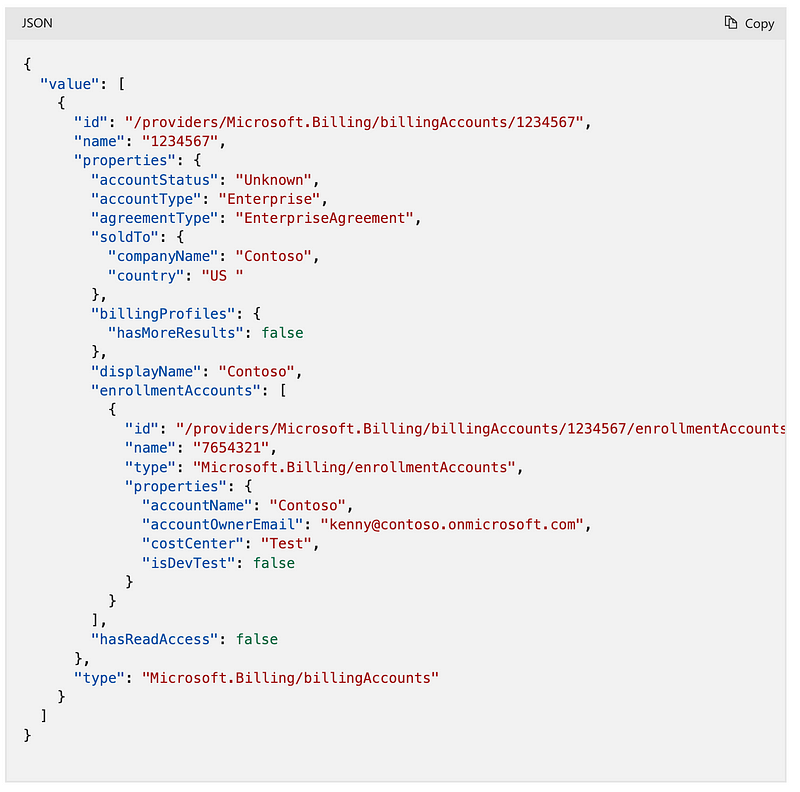
Microsoft Customer Agreement (MCA):
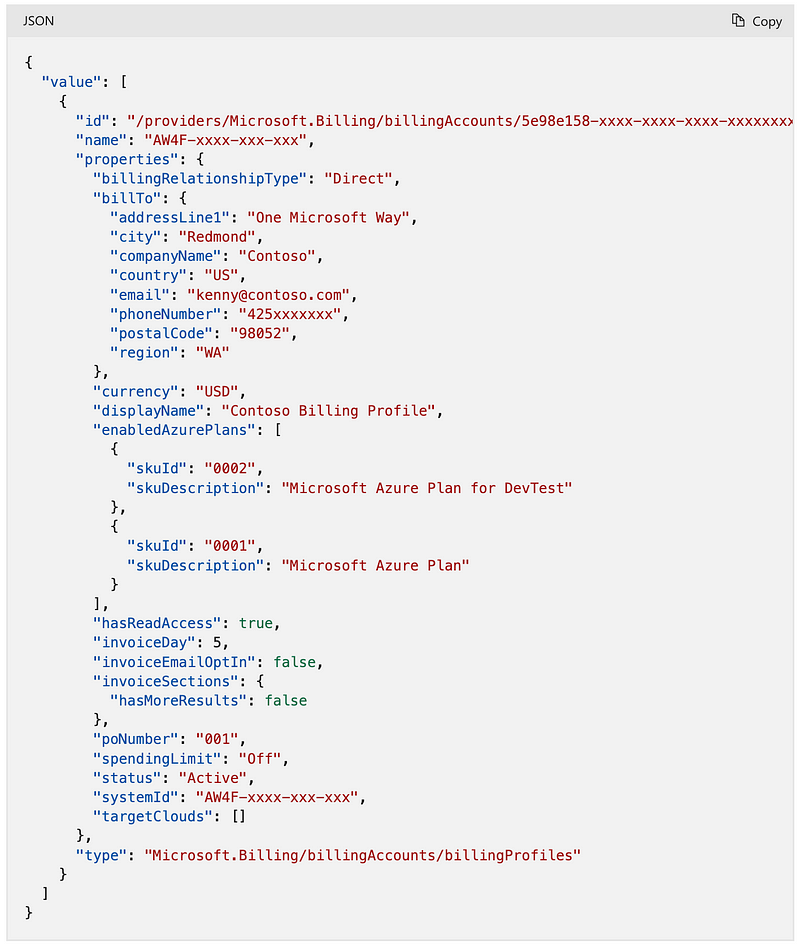
Microsoft Partner Agreement (MPA):
How much does a Microsoft Customer Agreement cost anyway? Well, according to the FAQ, you can call an API to figure that out but you’ll have to bear in mind all of the exchange rate issues noted on this page:
When it first came out it was $100 per month and required a 12-month commitment, but I don’t know what it is now.
Azure Policy
Can we create an Azure Policy with an ARM template? Yes.
Microsoft also has a number of built-in policies. As I mentioned earlier for cloud provider managed policies, you might want to make a copy of them and manage them yourself in your own source control system.
Initiatives
A number of regulatory compliance initiatives also exist in Azure.
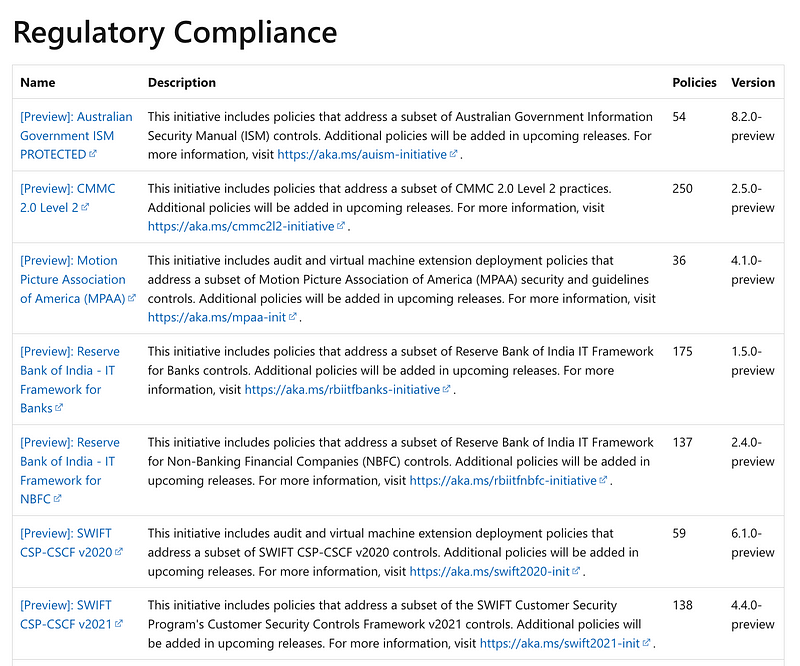
Scroll down on this page.
Should you use them? If you are not using anything, then use them. If you do not have the resources to keep your policies up to date with compliance changes then you may opt to rely on Microsoft to manage these policies and apply them to your account.
However, what if you are out of compliance because of a change to the policy or the compliance regulations and the policy applied to your account leaves a gap. Who is liable in that case? Is Microsoft liable for not keeping the policy aligned with regulations, or is that still your responsibility? I don’t know. Don’t ask Microsoft. Ask a lawyer if that concerns you. It will be based on your contract as I explained in this post.
Can you deploy them with ARM templates? It appears that you assign the initiative ID in the policy assignment resource used above. Here’s a blog post by someone else on how to do that.
I know this feeling:
It took me some trial and error to figure out that nuance as error messages just tell you about some JSON parsing or referencing issues without any hints about processing parameter values.
Anyway, it seems to be possible to configure an existing initiative. I don’t see a way to create your own using an ARM template.
Drift Detection
Does Azure have drift detection for resources deployed with ARM templates to Azure Cloud like AWS does? I am not seeing it. I see data drift detection and something for on-premises deployments via Azure Stack Hub.
Apparently someone wrote a tool for this but I am not recommending it as I haven’t tried it. I’m just pointing out it seems to be possible and you could evaluate this tool or use a similar method to create your own tool. Not as easy as in AWS, but possible.
It appears that someone has requested this functionality.
If you want to see how drift detection works in AWS I wrote about it here with more posts on the way.
Pros and Cons
As you can see there are pros and cons to each cloud provider and there’s no universal magic code you can write to handle them all. I’ll write about a tool called Terraform later but to use Terraform it’s going to have to still know what’s going on under the hood and every cloud platform is different. Terraform also adds its own layer of complexity so you’ll have to decide if it’s worth it for your organization. More on that topic in a future post — and feel free to come and add your input or ask questions in Atlanta in October — sign up using the link above.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
