Modifying A Role CloudFormation Template to Pass in an ARN to Assume the Role
ACM.30 Allowing an IAM admin to run IAM-related batch jobs
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | Cloud Security Architecture | IAM
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post we created policies for use with a common AWS IAM Role template.
In this post, I’m basically going to show you what not to do in an AWS trust policy in CloudFormation as it introduces some potential security risks. Then I’ll show you a better way to do it in a later post.
I explain the security problems with approach below here.
If you are using this approach in any of your CloudFormation templates for IAM Roles you might want to consider changing it as I have done here:
Initially we created a batch administrator user who was allowed to assume the roles to run our batch jobs. In this post we want to allow the IAM user we created earlier to assume the batch job role that requires IAM permissions.
An AWS CLI profile with EC2 instance metadata credentials
Before we alter our batch job role template, let’s look at what happens when we try to assume the batch job role using the role assigned to an EC2 instance.
Let’s say you wanted to configure an AWS CLI profile to assume the batch job role. Find the ARN for the role we created for this batch job.
Navigate to IAM. Click Roles. Search for “Batch”:
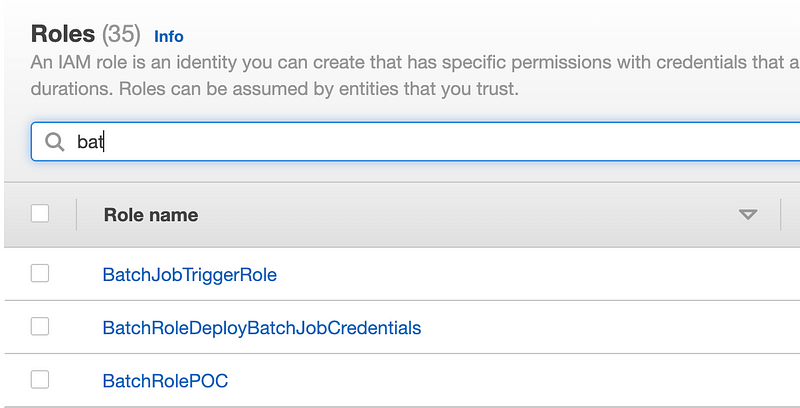
Click on the BatchRoleDeployBatchJobCredentials we created for this batch job we’re using to deploy our batch job administrator credentials.
As shown in a prior post, copy the ARN by clicking the copy icon.
Add the following to your ~/.aws/config file:

Save the file. Hit the escape [esc] key and type:
:wq!In the above configuration we’re creating a CLI profile named “batch” and we’re executing commands with the specified role.
We need some credentials to assume this role and we’re telling the CLI to use the credentials of the EC2 instance on the second line where the credential_source is the Ec2InstanceMetadata.
I explained what EC2 metadata and it’s relationship to permissions granted to your EC2 instance in an earlier post:
I presume you are following my previous instructions to run the scripts on an AWS Instance with an IAM role assigned to it.
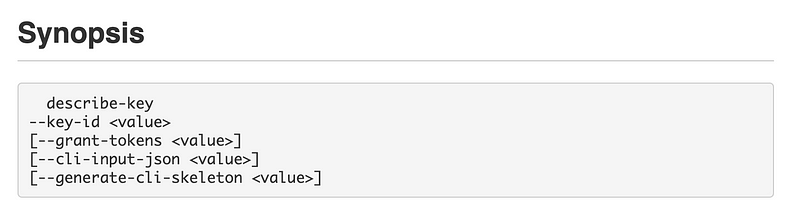
Our batch job role has KMS permissions. Test your CLI profile by running the command to describe the KMS key we created in an earlier post. We allowed this user to perform that action in our key policy. We can find the CLI documentation for that command:
We need to pass in a key id:
You can find the key ID by navigating to KMS and looking for your key ID there, or by looking at the outputs of your CloudFormation template:
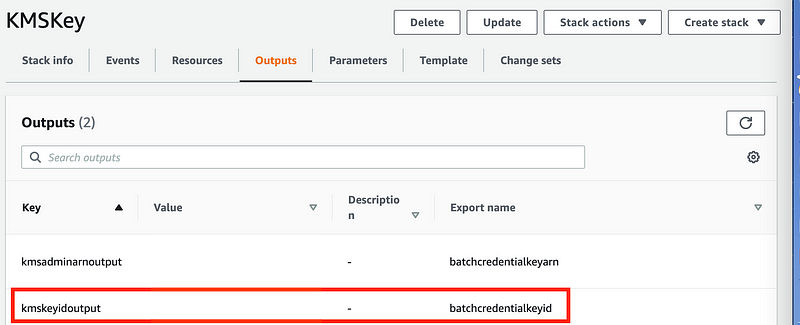
Note that I redacted my key id in the above screenshot but you will see one in the Value column. We’re going to use that id to run our CLI command. Replace [keyid] with your key id in the command below:
aws kms describe-key --key-id [your key id] --profile batchWhat happens next? You will likely get an error if you’ve followed my instructions exactly.
An error occurred (AccessDenied) when calling the AssumeRole operation: User: arn:aws:sts::xxxxxxxxxx:assumed-role/xxxxxxx/i-xxxxxxxxx is not authorized to perform: sts:AssumeRole on resource: arn:aws:iam::xxxxxxxxxxxxx:role/BatchRoleDeployBatchJobCredentialsThe reason we’re getting this error is because we haven’t allowed the user or role we’ve got configured on our EC2 instance permission to assume the batch job role (BatchRoleDeployBatchjobCredentials).
Catch-22 for creating credentials with a role that requires MFA to assume
Let’s revisit our trust policy to see what we did. Navigate to the IAM dashboard in the AWS Console. Click on Roles and the role we are trying to assume. Click on the “Trust Relationships” tab.
Recall that we Are allowing our BatchJobAdmin to assume our batch job roles but only when MFA is present.
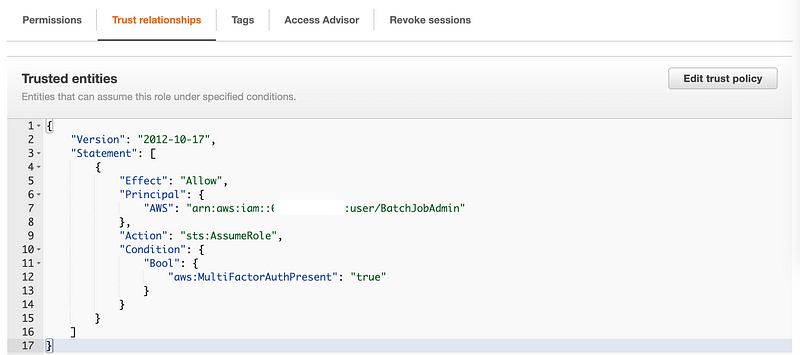
So maybe we should add our batch job credentials to the EC2 instance so we can assume this role. But wait. The credentials for that user is what we are trying to create.
The problem is that we can’t use batch job user to create our credentials because that’s the user for whom we’re trying to create credentials. Or in other words, permissions to deploy credentials can’ t depend on the credentials we are trying to deploy. Our catch 22.
Since I never want to expose the batch job admin credentials to a human, I’m going to have to use a different set of credentials to create them. We’ll use the IAM user to perform this IAM-related task, eventually via a batch job but for now we want to test that we can deploy the credentials.
Modifying our Role Template To Allow Different ARNs to Assume A Role
We have a couple of choices to allow different identities to assume our batch job roles:
- We could alter the batch job role template to pass in the assume role principal when it is deployed.
- We could create a new CloudFormation role template specifically for this job or the IAM administrators.
I started out with option two because I thought it might help prevent misconfigurations of batch jobs but reverted to option one to keep things simpler.
However: We’re not done with this template. The way I initially modify it to make this work has a potential security problem. I’ll explain in upcoming posts and show you how to fix it.
Alter our existing batch job role to make it more flexible. Take a look at the batch_job_role.
Here’s where I need to assign a different ARN, other than the batch job admin.
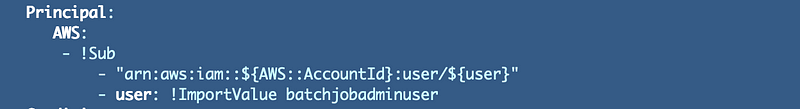
I’m going to replace this with a parameter to pass in an ARN and assign this ARN to the passed in parameter:

I’ll also need to edit the deploy.sh script in the batch_job_role folder to pass in an argument that will be used for the assume role parameter:
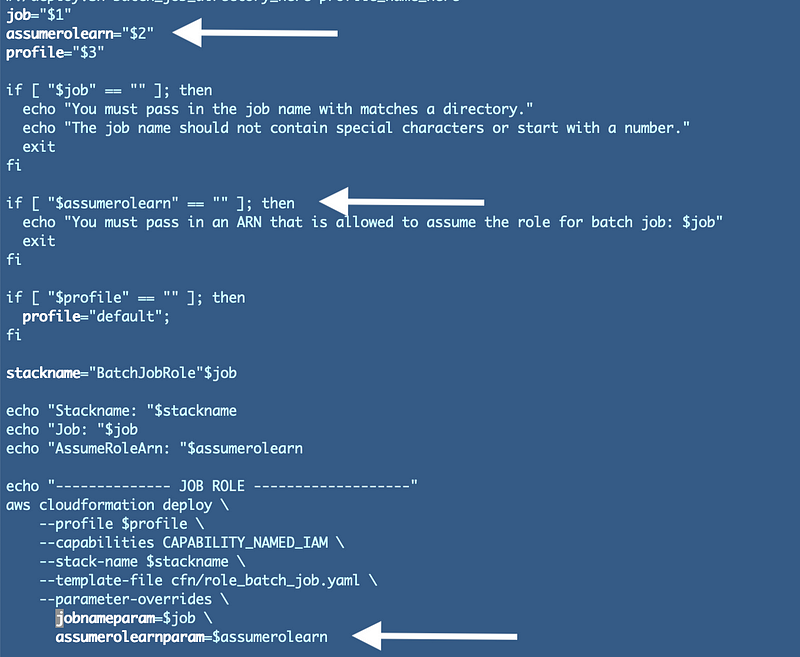
I’ll also need to pass in the role to assume from the deploy.sh script in the job folder:
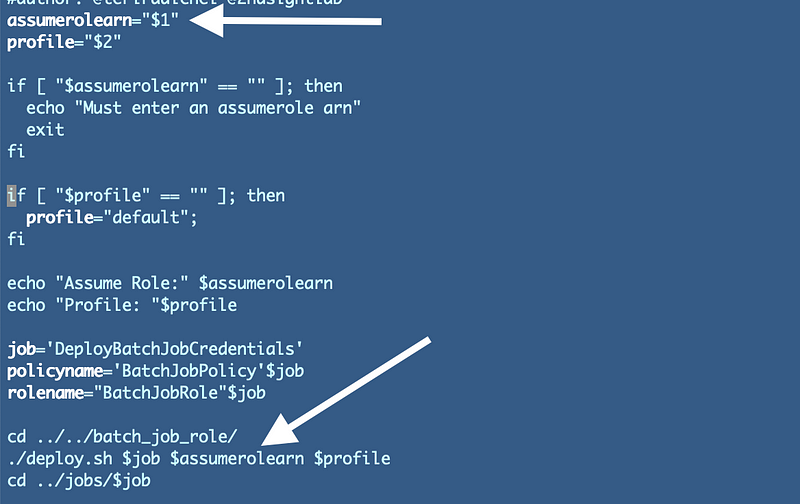
Navigate to your batch job folder:
jobs/DeployBatchJobCredentials/Re-deploy your batch job role and pass in the ARN for the IAM user we created in an earlier post:
deploy.sh [assume-role-arn-here]If you get this error you need first delete the policy stack because it is using the credentials from the role stack. Then run deploy.sh again.
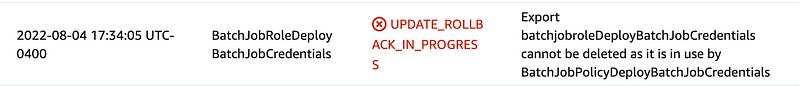
If you have issues where the output names are lacking job names, make sure the script is correctly passing in the job name, not an empty string. If you’re just using my final scripts from GitHub when they are available you shouldn’t have that issue.
Return to the batch job role in the IAM console and verify the policy under the Trust Relationships tab has changed as expected.
Always verify your code worked. When I first tested this code, I got no errors but when I checked the role trust policy it was incorrect. I forgot one change and so the template never updated the role even though the template indicated a successful deployment.
Give the IAM administrator permission to assume the role
For the purposes of this framework, I’m going to simulate an environment where the team that deploys software is not the same team that deploys KMS keys. I’m already created a separate IAM administrator.
Re-deploy the batch job role and pass in the IAM user ARN so it can assume the role, with MFA.
Create a role profile for the IAM user that requires MFA
Follow the steps in the previous blog post where I explained how to set up an IAM profile that requires MFA. Create an iam and an iamuser profile respective to the kms and kmsuser profiles in the post below. Use the batch job role in the configuration instead of the KMS Administrator role in the post.
Test the MFA Profile
Now run the KMS describe key command again but include the new profile you’ve configured. Now it should work.
Now we should be able to use our iam CLI Profile with the batch job role to create credentials for our batch job user.
Remember: We’re not done with this template. The way I initially modify it to make this work has a potential security problem. I’ll explain in upcoming posts and show you how to fix it.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
