Unique AWS Policy Templates for a Common Role Template
ACM.29: Creating a unique policy for batch jobs whose roles are created with a common CloudFormation template.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: IAM | AWS Security | Application Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post we created an AWS CLI profile that works with a role trust policy that requires MFA.
In this post we’re going to add a policy for a role created with a common role template. As explained earlier, we can use the same role CloudFormation template to deploy different roles or our batch jobs.
Although we use the same CloudFormation template for batch job role deployments, we can associate a unique policy with each role. If an organization wanted to they could have a team that deploys the role and each team creating a specific batch job could create their own policy.
As also discussed earlier, an organization may want to put boundaries on those capabilities. But the teams building the applications will understand what it needs to do better than anyone else, if they are building a well-architected system. Each team should be able to create it’s own zero-trust policy for a batch job.
I moved the IAM code to a central IAM directory earlier, but I am going to keep the IAM policy associated with a batch job in the batch job folder itself. If you have different teams deploying batch jobs you would want to make sure each team can only change the policies for its own batch jobs. You could do that by assigning each team a separate source code repository for their work in a larger organization.
Create an IAM policy for a batch job role
We’ve been thinking about creating a batch job that will deploy the credentials for our batch job administrators. We determined that this role will need to be assumed by our IAM administrator since that is the user that has permissions to take IAM actions in our account. Creating a developer access key is an IAM action.
Since this job will require the IAM administrator to assume the role to run it, I’m going to create a subdirectory in my jobs folder called iam and move the job there:
/jobs/iam/DeployBatchJobCredentialsWhen I create jobs that are executed by a role assumed by our batch job administrators I will move them into a folder called “batch”. That will help me remember what jobs et run by which roles.
I will need to alter my test script that creates the role and make sure it still works.

I tested and verified that this script still works.
Now we need to add a policy to the role to allow it to create the credentials and deploy them to Secrets Manager, encrypted with a KMS key.
Here are the permissions we will need to give our role:
- Run CloudFormation Script to create AWS Secret Key and Access Key for our IAM user
- Run CloudFormation Script to create Secrets Manager Secret
- Assign the Encryption Key in our CloudFormation script to the Secret Manager Secret and store the secret
One way to do this would be to give the batch job role all permissions for KMS, Secrets Manager, and CloudFormation. We can verify our code functions. Then we can review the actions the role took and refine our policy based on that.
The other way would be to give the role no permissions and then test and add permissions based on the errors we get.
I tried the latter approach first but unfortunately the error messages you get from AWS when you get permissions and access errors are not always clear. It is very time-consuming to try to use that approach. That would be my preferred approach but due to the roadblocks I hit we’re going to use the first option.
For now, to get this working we are going to add all permissions for the services we think we need. Then I’ll explain how to create a zero-trust role in an upcoming post.
We’ll want to use a consistent name for batch job CloudFormation policy templates so we can write a standard deployment mechanism for batch jobs in the future. For now we’ll name this policy file:
policy_batch_job.yamlAssociate the policy with the batch job role
If we check the CloudFormation documentation for IAM Policy, we see that we can pass in a list of Roles.
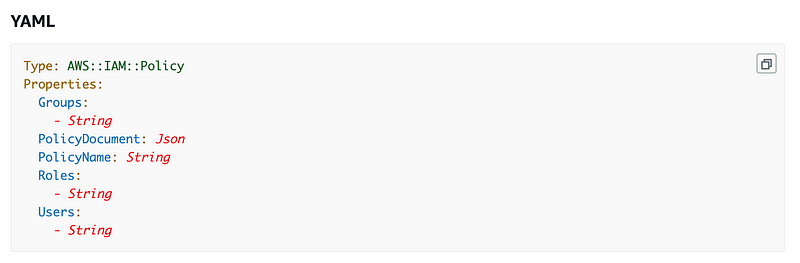
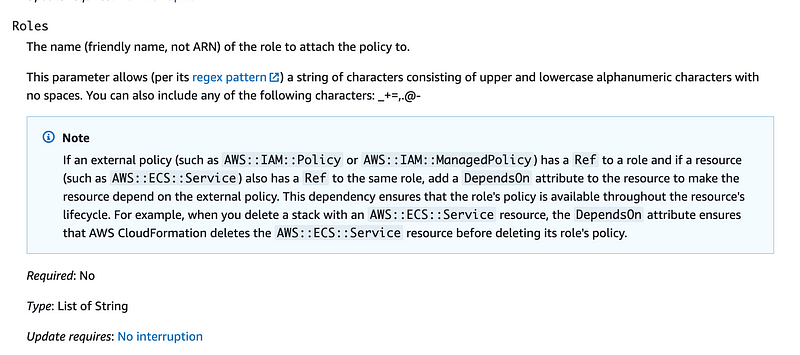
When we scroll down to see what values we can insert for a role, the documentation says we should use a role name:
The output for the role ARN we need is:
batchjobroleDeployBatchJobCredentialsIf you ran the prior CloudFormation templates you should see this output for your corresponding CloudFormation stack.
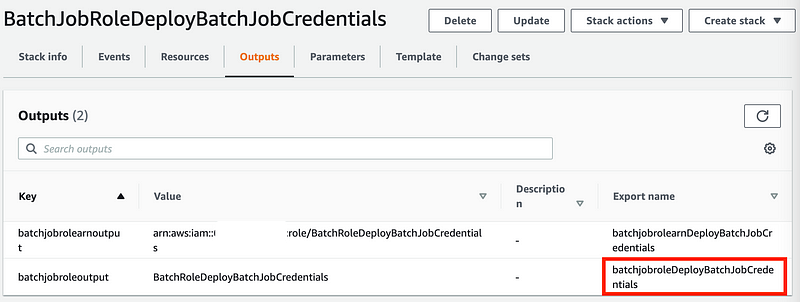
We can use this output with ImportValue to assign the ARN to the Roles element of our policy.

For testing purposes, we know that this role will need CloudFormation, SecretsManager, IAM, and KMS. For now we will grant full permission to those services and then review the logs after executing out commands to see what actions are required.
Note that I would *NEVER USE THIS IN A PRODUCTION ENVIRONMENT*.
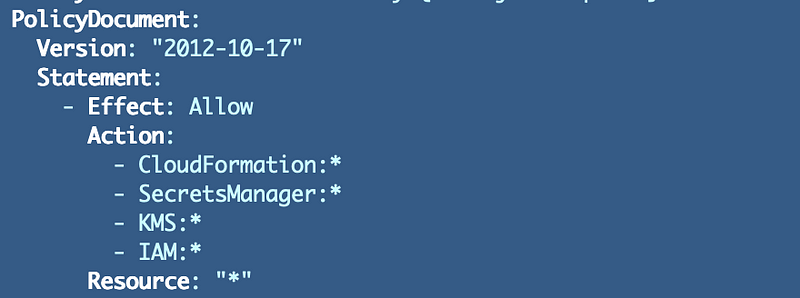
I’d probably want a PermissionBoundary on this in a development environment for all but those who are responsible for implementing IAM Policies.
We’ll have the deployment pass in the batch job name.

We’ll use that parameter in the policy name so the policy name and batch job name match.

Add the code to our deploy.sh script for our batch job to deploy the resource:
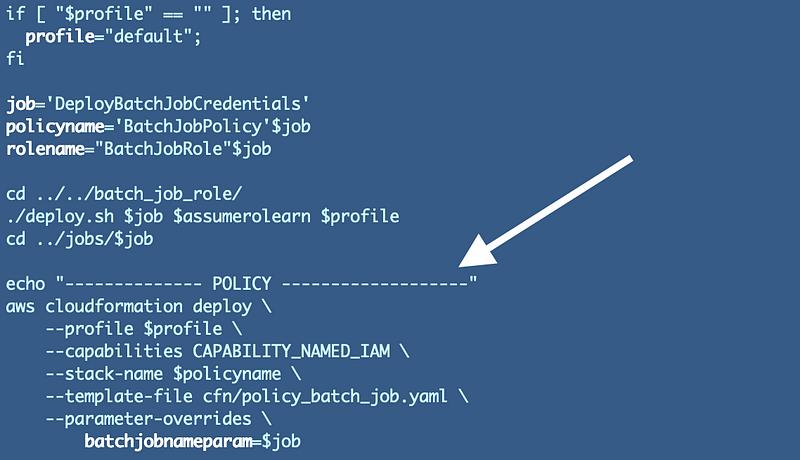
Deploy the policy using the deploy.sh script in the Batch Job directory:
jobs/iam/DeployBatchJobCredentials/deploy.shFor each new batch job you can create a separate policy as demonstrated above, but use the existing role template. This helps reduce potential errors. It also allows you to to have a separate team maintain the role template if you need to do that than the team that creates the policies and permissions for each batch job.
NOTE: This template has a potential security problem which I address in the next post. Can you spot it?
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
