Import The Default Route Table for a VPC Into CloudFormation
ACM.425 Using CreateChangeSet to import existing resources into your CloudFormation stacks
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | Network Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Part of my series on Automating Cybersecurity Metrics. IAM. Deploying a Static Website. The Code.
Free Content on Jobs in Cybersecurity | Sign up for the Email List
In the last post, I briefly explored a feature announced at the latest AWS re:Invent conference but I’m not sure it’s working or even if and when it does, if it will meet my needs for what I’m going to do in this post.
When you create a VPC it, by default, has a route table and a security group. I wish it did not. I wish you could add those yourself with CloudFormation in a separate template after the VPC creation.
But perhaps we can import them.
I showed how to import an existing Organization into CloudFormation in this post.
Perhaps we can use similar code for the objective in this post.
What I did was to take my prior code for an AWS Organization and convert it to a reusable function.
I replace any hard coded variable values for my organization with passed in parameters.
I created this common resource import function in:
/deploy/shared/functions.sh
Here’s what it looks like:
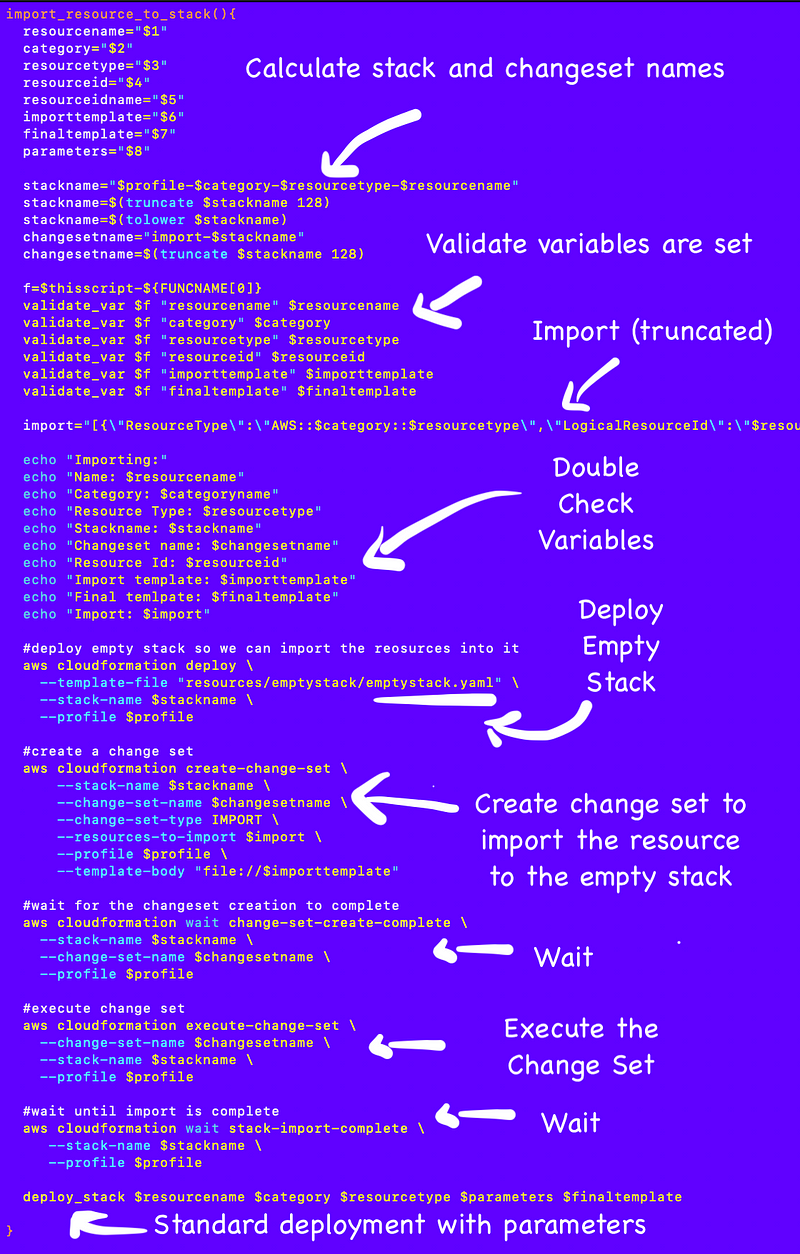
I explained all of the above in more detail in my prior Organization import post. Read that post if you’re not familiar with the above code.
This just shows you how I took that code and turned it into a reusable function in my shared functions file.
I created an import template that looks like this with a placeholder for the VPC ID:
/resources/ec2/routetable/routetableimport.yaml

I created a function to update the default route table in:
/resources/ec2/vpc/vpc_functions.sh
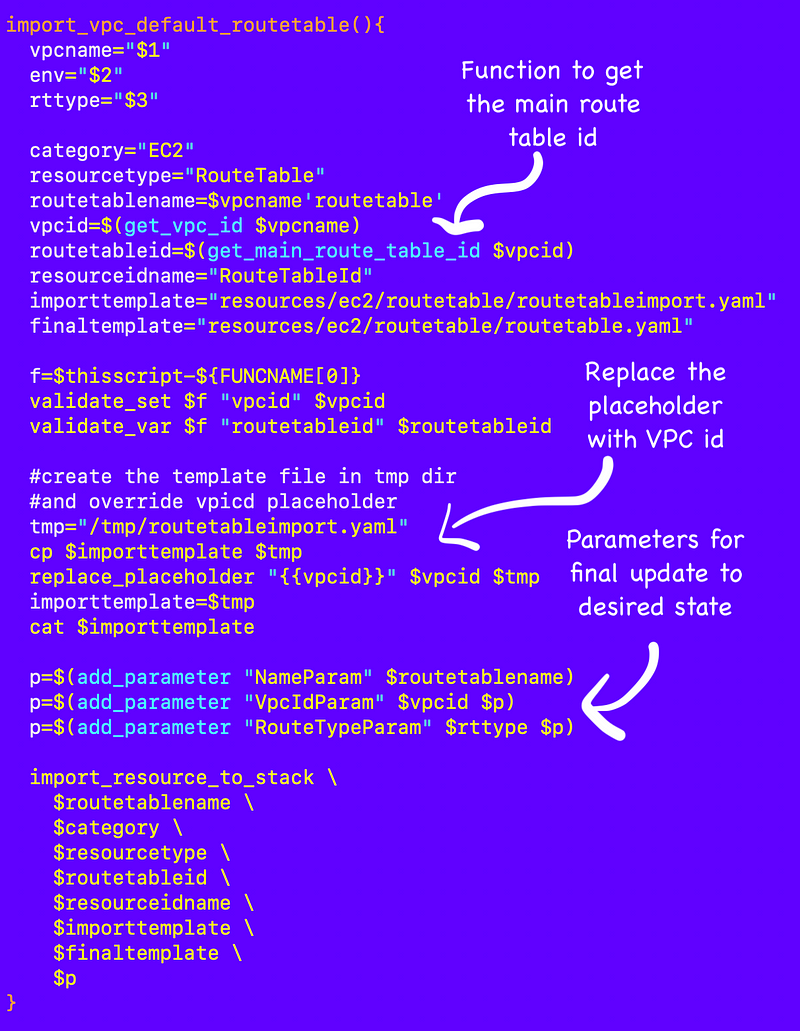
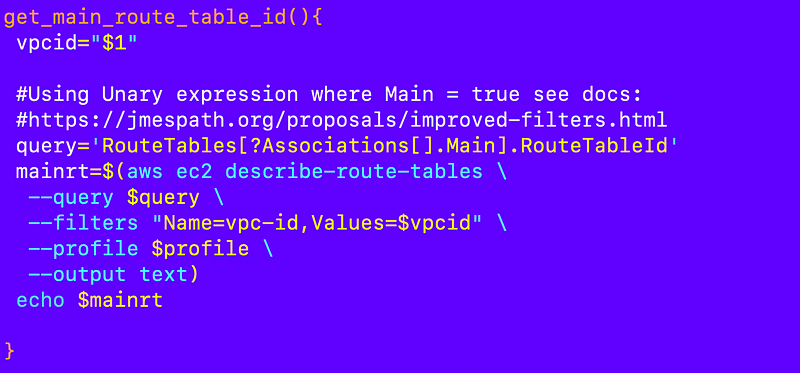
Here’s the new function to get the main route table id:
I call the new import function after I create my VPC.
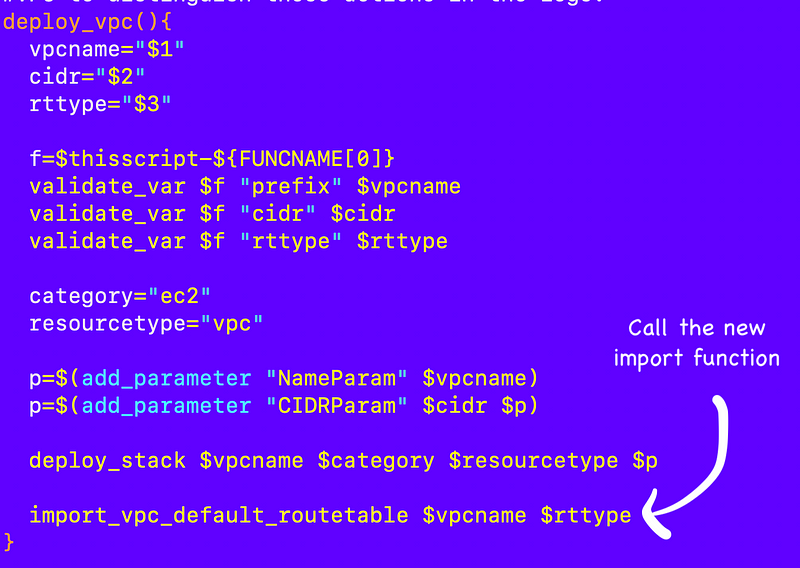
I probably will have to fix some issues with this code later like skipping things that already exist or deleting them first if I run the code a second time.
I already figured out that you cannot delete the route table after you create them because the VPC requires a default route table. If you try to run the stack over the top of itself things get into a wonky state. I’ll need to make sure that I check for existing resources and not try to re-import. I also need to change the detail policy to retain, I think.
Still working out a few things with the final install but the initial import works fine. Just need to troubleshoot some details.
You can do something similar to the above for the default security group as well. Of course I’m leveraging all the common code from my prior posts I wrote about here:
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab




