Does Your VPN Have a DNS Leak?
ACM.474 Why it matters and how to check
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Network Security | DNS Security | Cloud Architecture
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I explained why some so-called VPN-less solutions are not really VPN replacements, but they still have some merit.
While I was setting up my VPN I ran across some interesting posts talking about DNS Leaks.
Now first you have to understand there are different types of VPNs. IPsec VPNs encapsulate and encrypt entire packets and send them thorugh a tunnel as I explained in my original post in this sub-series.
Not all VPNs work the same. An SSL VPN doesn’t encapsulate all your traffic the same way.
While testing, I showed how I changed my routes and phase 2 configuration and used a NAT to send everything to AWS
When I set up my IPSEC VPN to work with a NAT in AWS I showed how I was reviewing the logs and could see that my traffic was getting sent to the IPSec interface over to AWS.
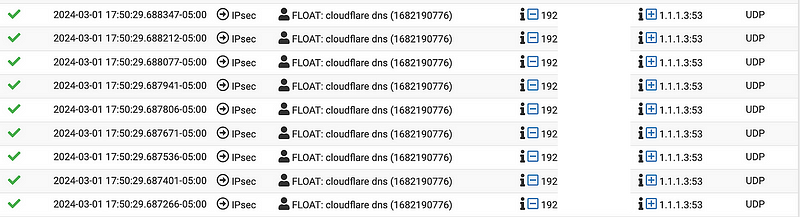
You can look at the VPC Flow Logs and find the corresponding traffic flowing through the Transit Gateway and hitting your NAT IP address in your NAT VPC Flow logs.
You can also review your traffic in your pfSense firewall logs to make sure none of those requests are reaching your WAN interface. You’ll need to understand if your systems are using DNS over HTTPS to understand which ports and protocols to inspect.
In my case, I restrict DNS requests to specific DNS servers and I attempt to limit DNS over HTTPS requests. In that case, you can inpsect the traffic as follows:
Firewall > Rules
Filter on allowed traffic to port 53.
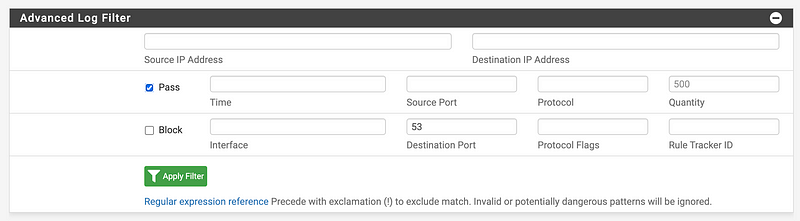
Look for anything unusual.
You can also perform a packet capture.
Diagnostics > Packet capture.
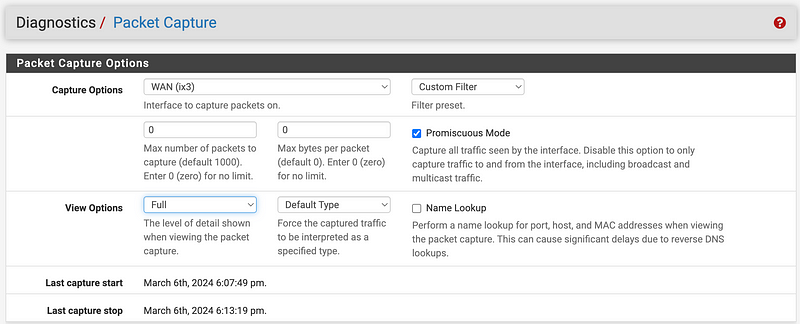
You can select the WAN interface or another interface for which you want to inspect DNS traffic. You can view the full packet or partial.
Presuming you are not using DNS over HTTPS you could use these entries and click start:
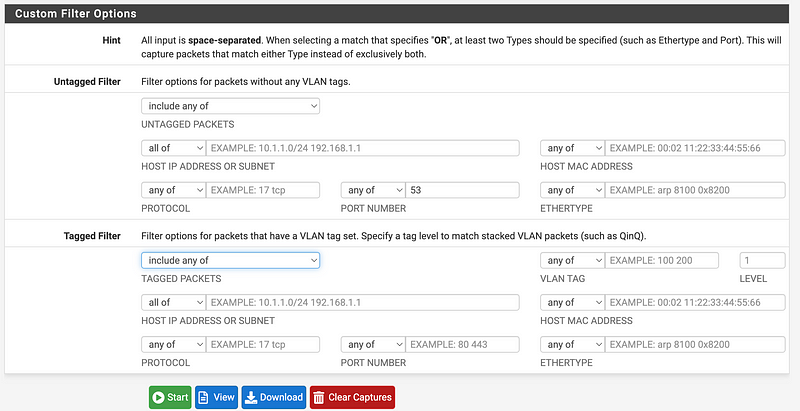
You can also take a look at the IP addresses in a pfSense packet capture as I explained here to make sure you don’t see any DNS traffic from your desired IP range hitting incorrect IP addresses.
Once I get that running I use the dig command to look up my IP addresses for my website:
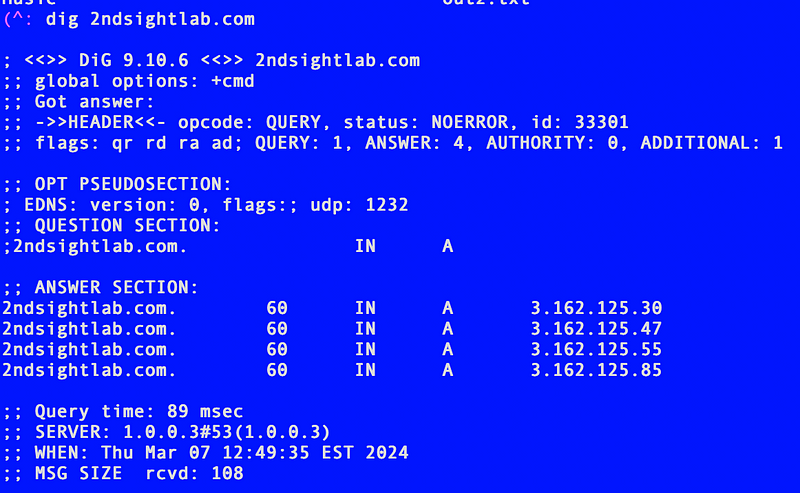
I search the packet capture for 2ndsightlab.com and I’m not seeing it. That’s good. That hopefully means that request went through the VPN and did not traverse the WAN since I’m capturing WAN logs.
I also read about this site called DNS leak test while perusing various VPN content.
I’m not sure who runs this site exactly but here’s what it does.
First, when you visit the page it shows you the IP address the Internet sees (redacted below):
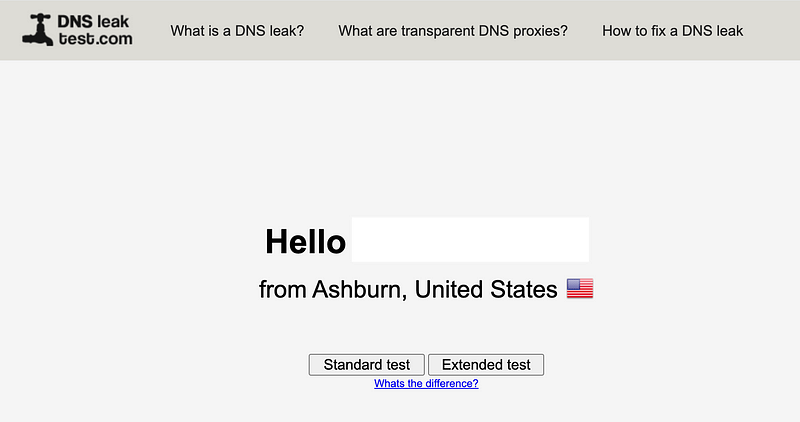
Here it shows me the AWS IP address I’m using which is good. I wrote about how that can prevent people from seeing your home Internet address as you surf the web.
You can perform the extended or standard test.
In my case I want all my DNS requests to go specific DNS servers. What’s correct is that my requests are going to CloudFlare. However, presumably CloudFlare runs it’s own services in front of it’s DNS servers so I’m seeing some other CloudFlare IP addresses, not the DNS servers I have configured. I hope that is correct.
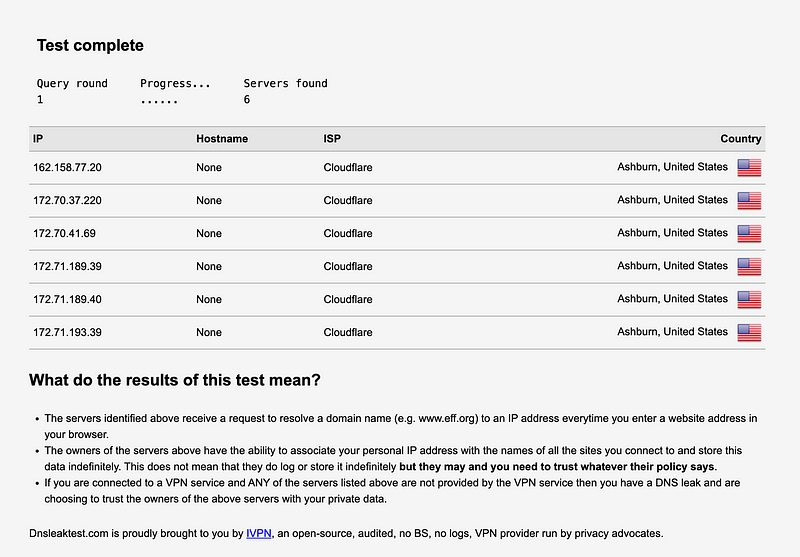
Now some people might be concerned that CloudFlare can see, log, and track their DNS requests.
If you were using a client VPN and that client VPN service provides you DNS servers, you wouldn’t want to see any other DNS servers besides those your VPN provider gave you to configure in your systems. In my case, I don’t want to see any DNS servers other than those I have configured which is CloudFlare at the moment.
What I could do is try to use AWS for DNS instead. I’m not sure if you can use AWS DNS servers from your home network (haven’t tried) but you could set up a DNS server in AWS on a private network using Route 53.
https://docs.aws.amazon.com/route53
That way my DNS requests should never leak to the Internet if we can configure private DNS servers. Then perhaps this service wouldn’t see anything at all — something to test later. It also would be less outbound traffic through our NAT.
On a related note, I wrote about DNS certificate transparency logs here:
In general, it’s a good idea to monitor all your traffic to make sure it’s routing to the place you think it is and not leaking to some other subnet, network, or host where you don’t want it to end up.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






