Deploy a Public and Private Subnet in an AWS VPC
ACM.274 Creating multiple subnets with different route tables
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | Network Security | Cybersecurity
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I fixed an issue with an AWS Prefix List I created earlier.
In this post I need to make a change to my VPC deployment scripts so I can create both a private and a public subnet in a single VPC. I explained what public and private route tables are here for VPCs and Subnets.
I’m going to reuse but modify a lot of the code I wrote in prior posts.
VPC Flow Logs Role
Before I can deploy the VPC, I have to deploy the VPC Flow Logs role in the Sandbox account. Recall that we created our code such that every VPC will have Flow Logs enabled by using our script.
My roles are this folder:
/SecurityMetricsAutomation/IAM/stacks/RoleI create a separate deploy script for the sandbox account to avoid breaking existing code.
deploy_sandbox.shI copy the code for the Flow Logs role from deploy.sh to my deploy_sandbox.sh script.
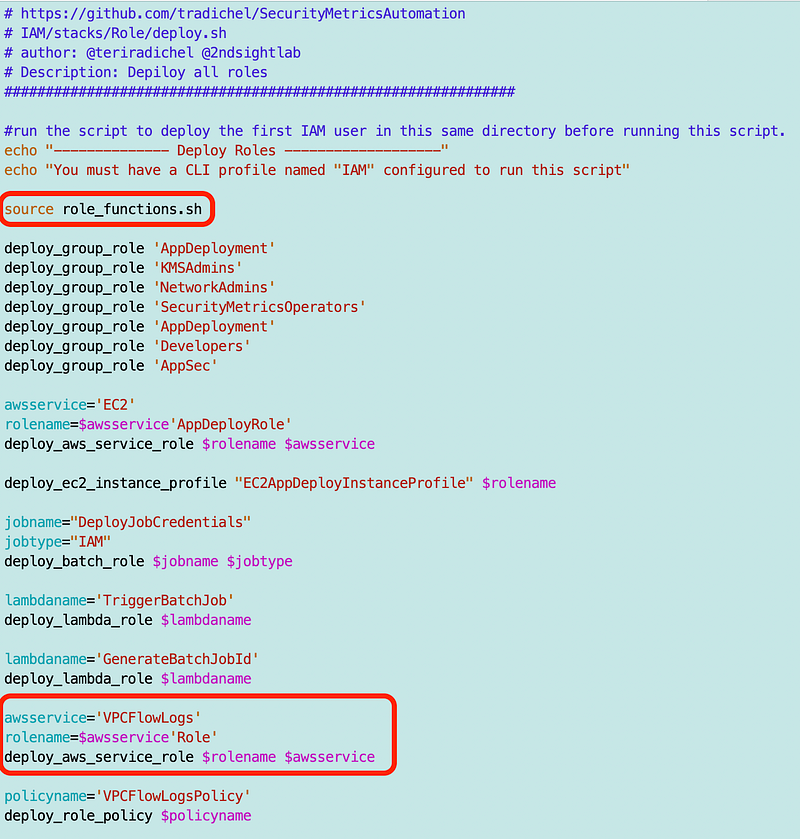
I need a role profile named IAM and can use my SandboxAdmin credentials with that profile so I set that up in my AWS CLI and ideally it is a role assumption that requires MFA.
Existing networking code and deploy script
For network resources, I’m starting with my existing networking code from prior posts which exists in:
SecurityMetricsAutomation/Network/stacksOnce again I create a separate deploy script for sandbox resources.
deploy_sandbox.shAs a starting point I copied my existing deploy.sh script to deploy_sandbox.sh and I’m going to modify the existing code now in the deploy_sandbox.sh to work for this use case.
VPC
First, I’m going to modify the VPC code in my deploy_sandbox.sh script.
One of the things I realized while writing this is that I’m really not specifying whether the VPC is public or private but whether a route table is public or private based on the routes it contains. I modified the vpctype to be rttype instead because that makes more sense. I also changed the comment, the VPC name, and the CIDR block.
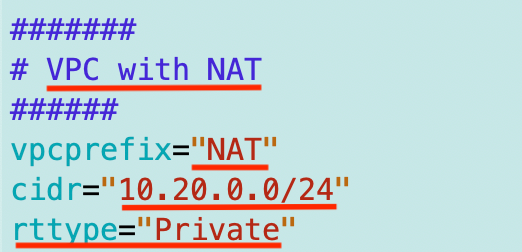
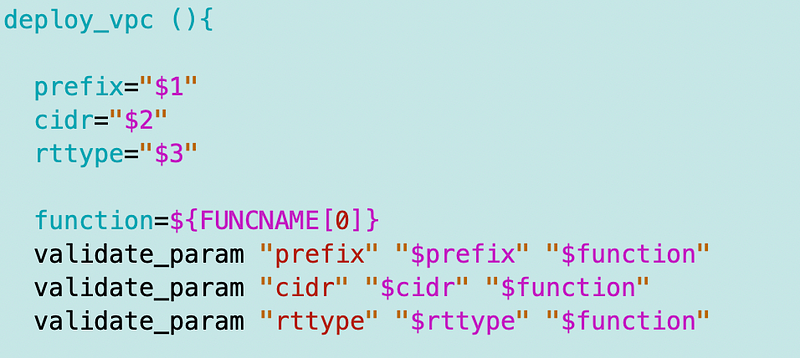
The code then calls the deploy_vpc function and I change every reference in this function to vpctype to rttype.
Route Tables
While I’m in this function I’m going to make another change. I need to have separate route tables for the public and private subnet in the VPC.
I removed the code in the deploy_vpc function and move it to a separate deploy_route_table function.
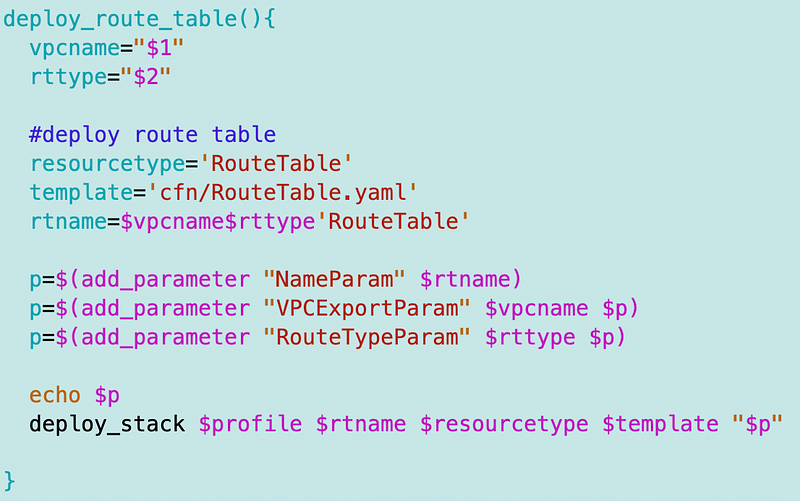
I change the VPC function to call the above in place of the code I removed.
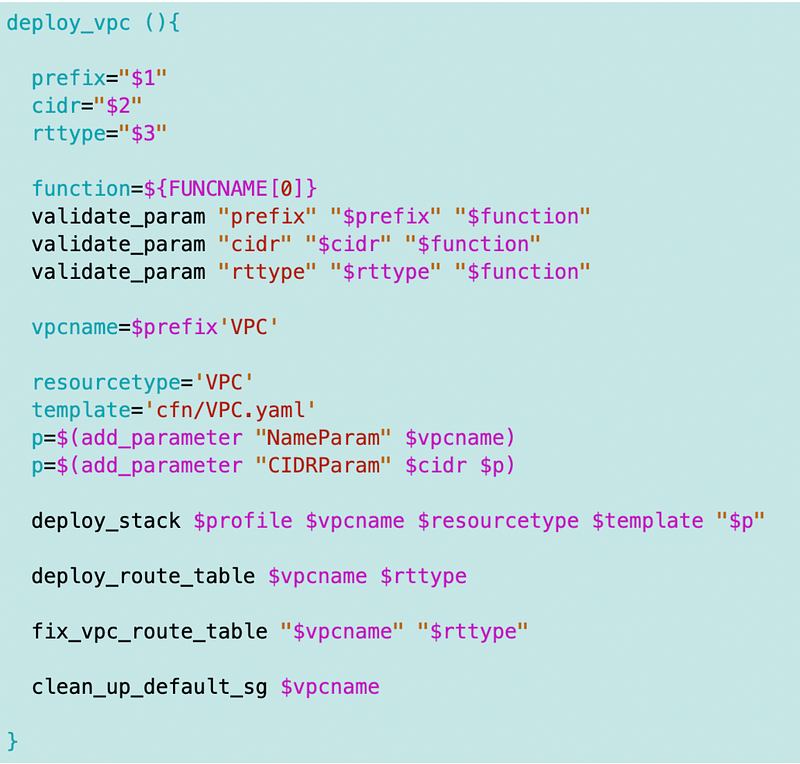
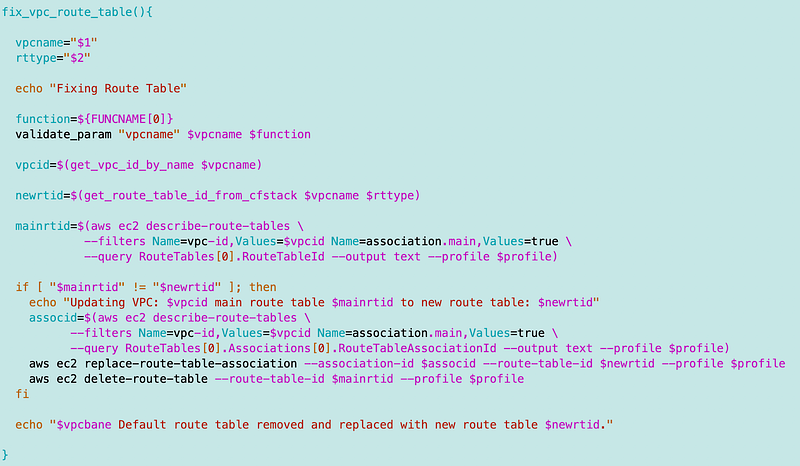
I had to clean up a few things in the fix_vpc_route_table function as well.
Prior to that I added this function:
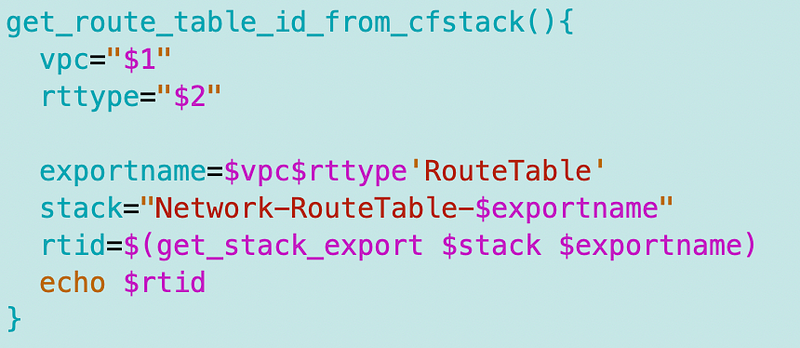
(I’ll show you in the next post how I’m going to make that even more generic to reduce lines of code.)
The updated code to fix the VPC route table to only have the one we deployed with CloudFormation and our specific name:
I add a call in my deploy_sandbox.sh file for a new private route table.
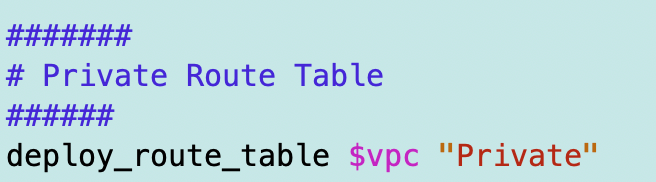
Now the VPC has both a public and a private route table associated with it.
I’ll show you some other route table updates in the subnet section below.
NACLs
Initially I had embedded NACL rules within my subnet function. However, it is possible for two different Subnets to use the same NACL rules. If possible we want to do this in alignment with the DRY Principle I wrote about earlier.
I moved the code that creates a NACL to a separate function:
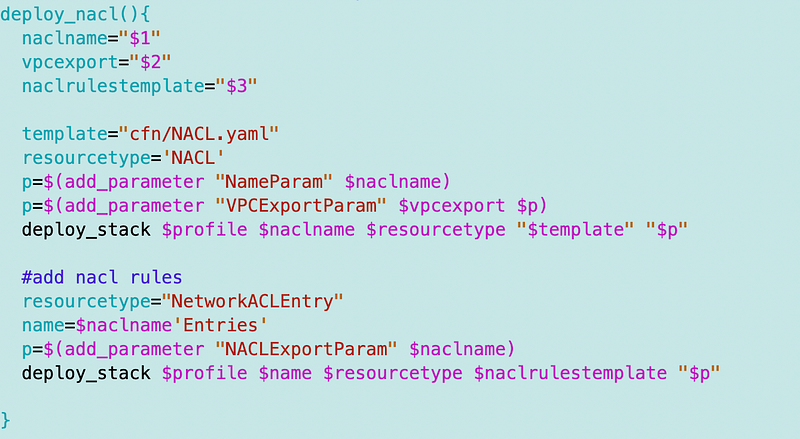
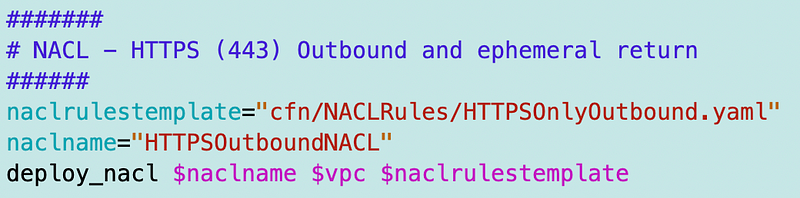
I used that to create a single NACL to use with both my subnets:
GetAZs
Along the way I created a function to get availability zones by index. I wrote about why here and it has the new function, along with another error I got while revising my subnet code.
Subnets
My subnets now need to take inputs for an availability zone, a route table, a NACL among other things. I revised the subnet function to deploy a single subnet instead of multiple and made the necessary revisions:
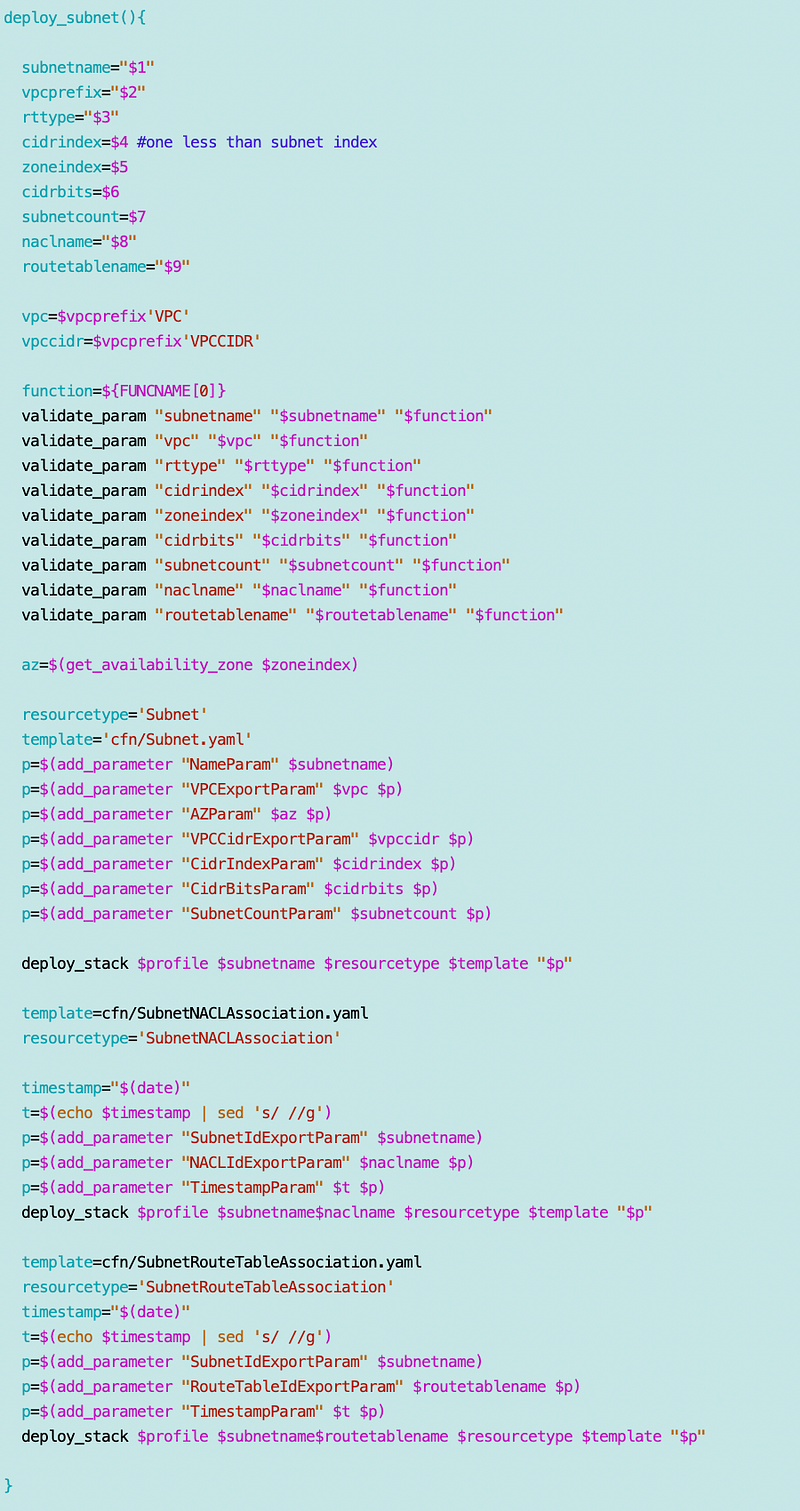
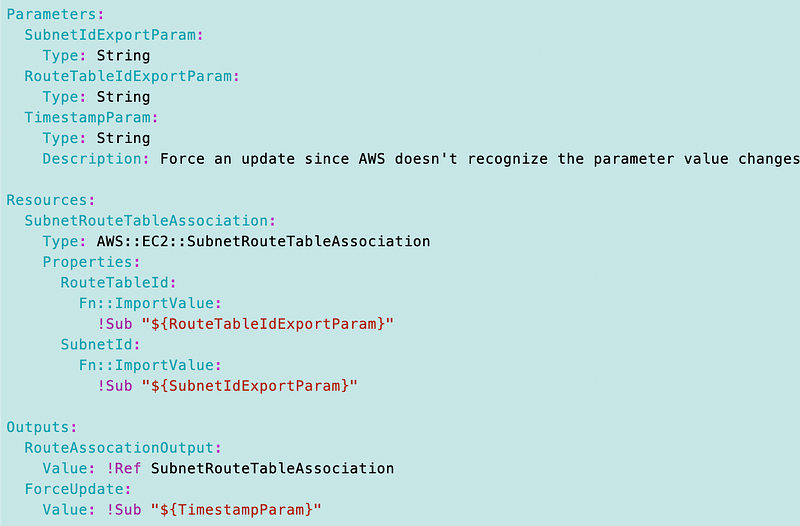
To associate the route table to the route table I had to pass in the name and add code similar to what I have for associating the NACL to the subnet. The resource we will use is a SubnetRouteTableAssociation.
Here’s the CloudFormation template:
I also took the code that creates multiple of the same subnets across AZs and put it into a separate function — which still needs additional revisions for the AZs. I need to look up the AZ by index using my new function and pass it in…I’ll have to get to that later.
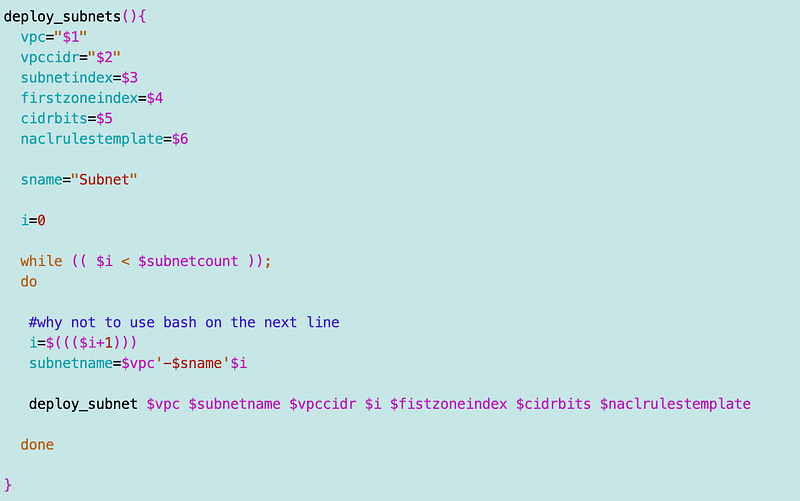
Then I added calls for the two subnets to my deploy script:
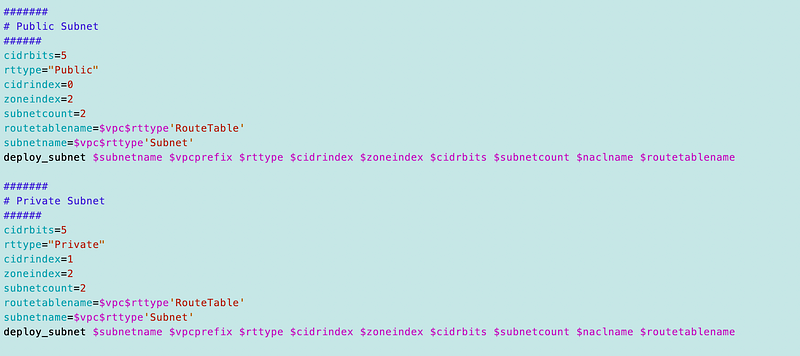
Validate No CloudFormation Stack Errors Exist
Check to see that no CloudFormation stack errors exist.
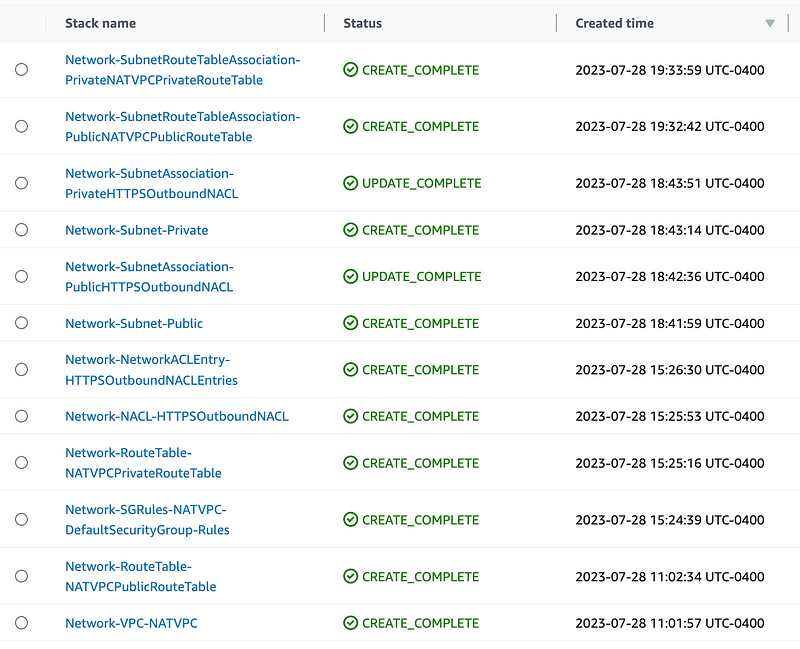
Review Resources in the AWS Console
All these items can be found on the VPC Dashboard.
One of the most critical things to check in this case is that the route tables are correct, and initially mine were not. I had two route tables:
However, both subnets had a route table with an Internet Gateway. In other words, my private subnet was not actually private. The default public VPC route table got associated with my subnet.
Also check that both the subnets have the correct NACL and NACL rules, not the default rules open to every port, protocol and IP address.
Validate networking by deploying compute resources and testing
The next test will be to actually deploy compute resources in our network and validate they work correctly. We will need some other changes to support what I am planning to do with this NAT VPC to reach GitHub from a private network and a VPC Endpoint for AWS CodeCommit.
I’ll check in the code after I’m done testing the static website deployment.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
