Delegated Administrators for Services Integrated with AWS Organizations
ACM.396 Do you know which accounts are configured as delegated administrators for services in your organization?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | AWS Organizations | IAM
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post, I wrote about enabling and disabling trusted access for all the services that you can use with AWS Organizations that support it.
In this post, you get some purple and gold in my terminal window in support of my alma mater — the UW Washington Husky football team ranked number 4 today. Go Dawgs! No, not those red dogs. I like them too but I’m talking about the purple and gold.

OK back to programming. Sorry. 😆
One of the services I set up trusted access for in that post was the Account Management Service (meaning changing alternative account emails, not the root email for the account, and a few other settings).
Making the orgadmin account a delegated administrator of the Account Management service
I’m going to delegate access to the orgadmin account I created to manage those settings outside the root AWS Organizations Management Account.
Note that I made some adjustments to my code to append the environment name to the account name in this format:
[env]-[account]
So the name of my account is now root-orgadmin. You’ll see how that helps us in future posts.
The problem we have with operating in the root AWS Management Account is that any Service Control Policies we write do not apply to that account. So as much as possible we want to operate outside that account.
How can we do that when we are managing services across the organization? AWS allows you to delegate responsibility for certain actions to other AWS accounts. By doing that the users in what is called the Delegated Administrator account can perform actions normally restricted to the management account.
Delegated Administrator for AWS Organizations
I already wrote about how to do this manually for AWS Organizations when this feature was first announced:
AWS Organizations works a bit differently than the other services that work with it. In this post we’re focused on services other than AWS Organizations to which you can delegate access.
Creating a common functions to register and deregister delegated administrators
I mentioned the page that works with AWS services in the last post and we looked at trusted access in the second to last column. In this post we’ll take a look at delegated administrator access in the last column.
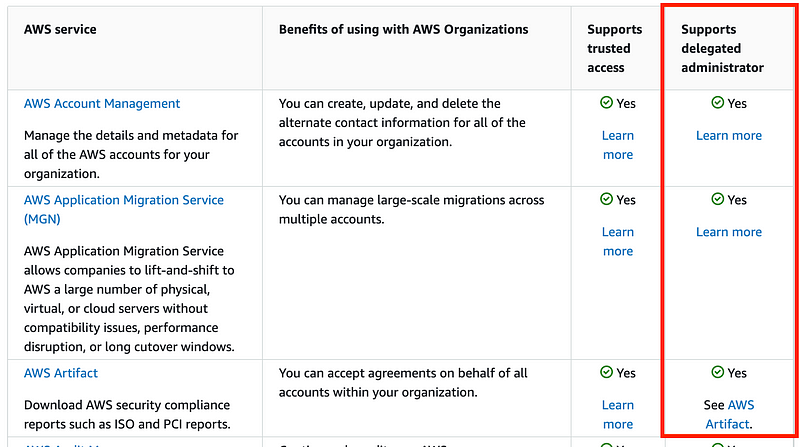
If I take a look at a couple of the links do we have a common mechanism for delegating access?
Yes it looks like we do:
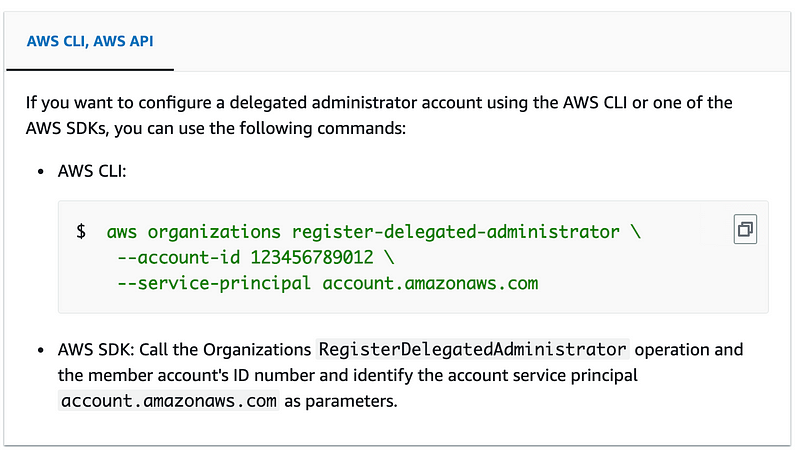
The converse of that, as you might expect, is the following command:
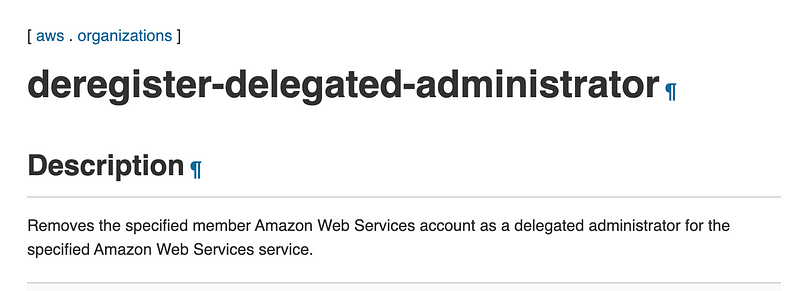
To support this command we can create the following functions:
register_delegated_administrator
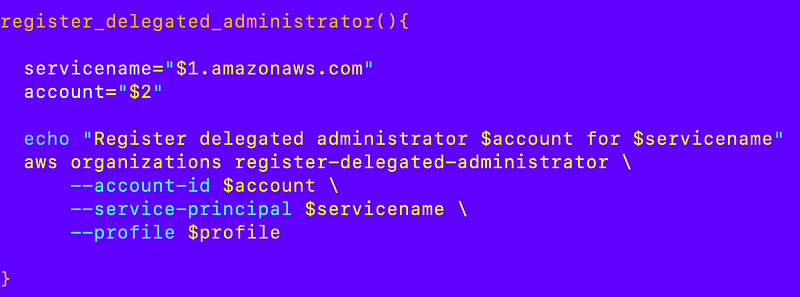
deregister_delegated_administrator
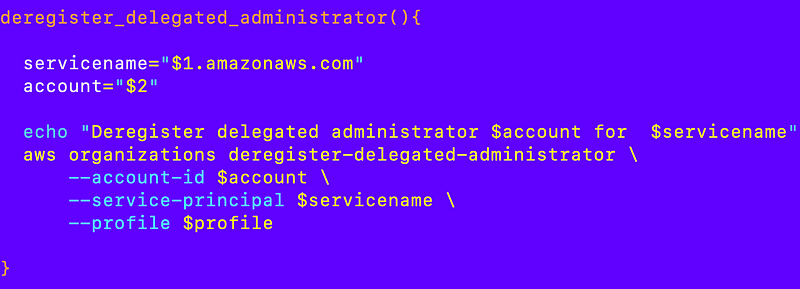
Now I can try this out by registering the org admin account I created as a delegated administrator for the account service when I create it.
Recall that I deployed the account here:
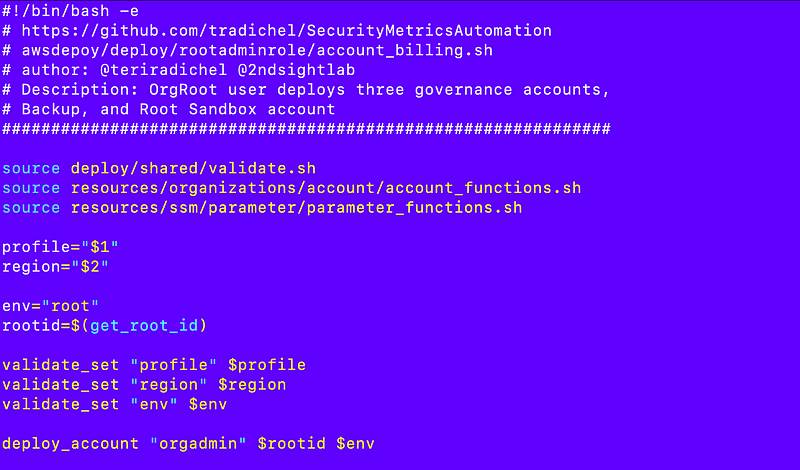
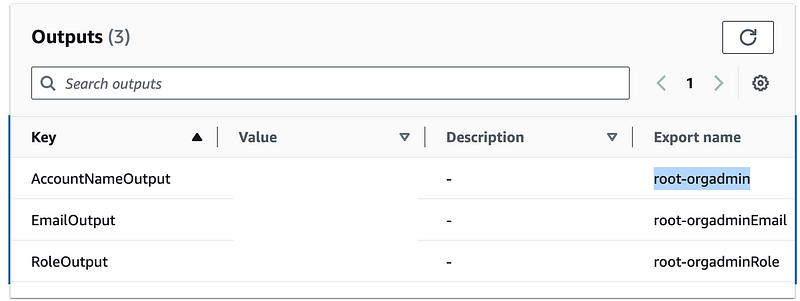
Also recall that I am now making the value of the name parameter (NameParam) the name of the output that returns the ID or ARN, whichever is most appropriate, for a resource in all my CloudFormation templates. In this case my template output with the name of the account returns the account ID as I showed in this post:
The value root-orgadmin was passed into NameParam for my template and because the export name of the output that returns the account ID. It was also assigned as the name of the resource in the template.
So now I can retrieve the account ID using that output with my common function in my shared functions file:
deploy/shared/functions.sh
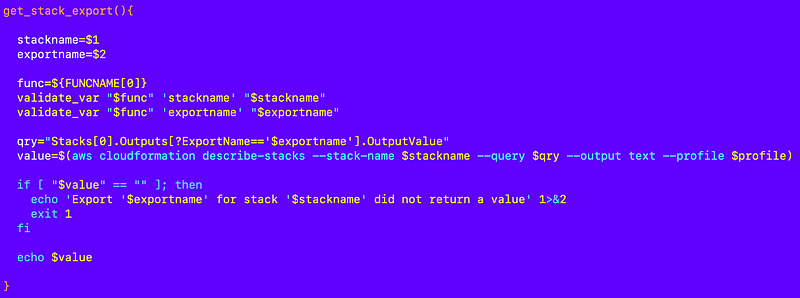
I also have a function in the account_functions.sh file which does not use the organizations stack:
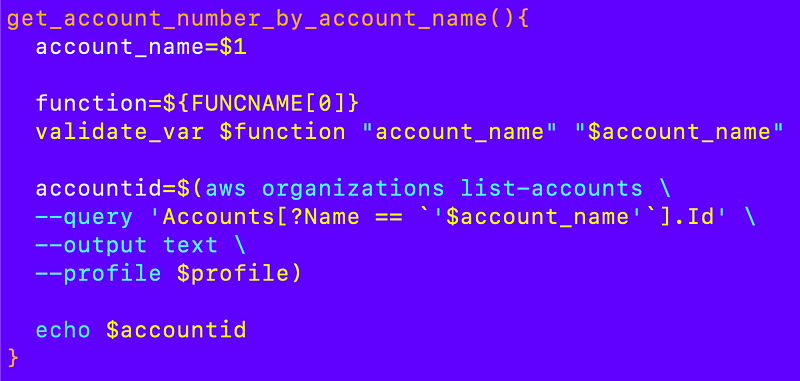
Take your pick but I think I’ll use the latter.
Except it doesn’t work. Here’s why. Closing AWS accounts is a royal pain in the neck as I’ve written about before but the process keeps improving. You can close an account but then it hangs around for 90 days and in the past you couldn’t create the same account or use the same email that was assigned to a suspended account I believe.
Well, AWS fixed that I think in a way? I don’t think it was like this before. Now, apparently, you create a new account with the same name. No wonder I was confused when I deployed a new account and thought I had to change the name but it worked with the same name. It worked so I shrugged and moved on. Ok great. That problem is solved.
So now my function to look up an account by name doesn’t work because it returns the suspended account. I’m getting this error:

Alright I hope I can fix that by querying the status of the account and returning the active account ID instead.
So I query the accounts using this command:
And indeed, there’s s status property.
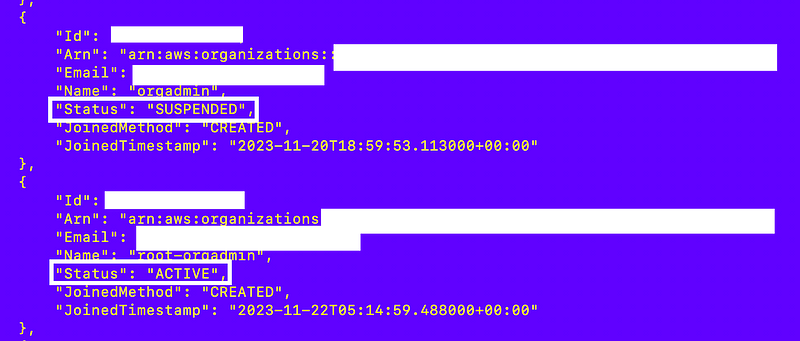
So let’s add that filter on Status equals Active. I always find the query syntax for the AWS CLI mysterious. There’s no example of concatenating two different filters here on the example page:
Found the answer here and am trying to tattoo this into my brain so I can remember it in the future.
Put the two criteria in (parentheses) and concatenate with &&:
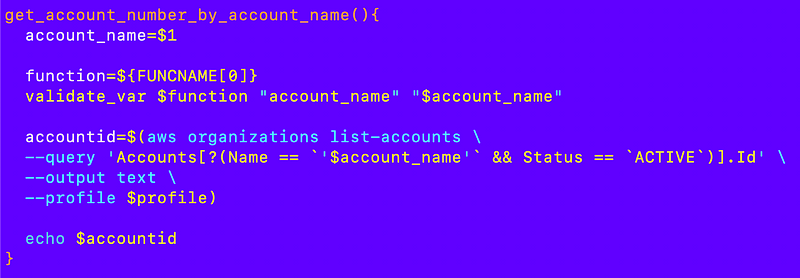
Now my function works.
Review your delegated administrators
So where can I see this in the console? Head over to the Organizations dashboard and click on services. I can see that AWS Account Management is enabled. (I did that in the last post.) But I don’t see the delegated administrator here. Click on the service.
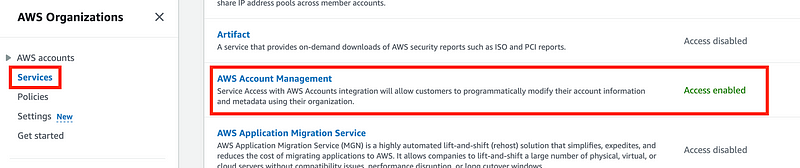
Hmm. No delegated administrator here:
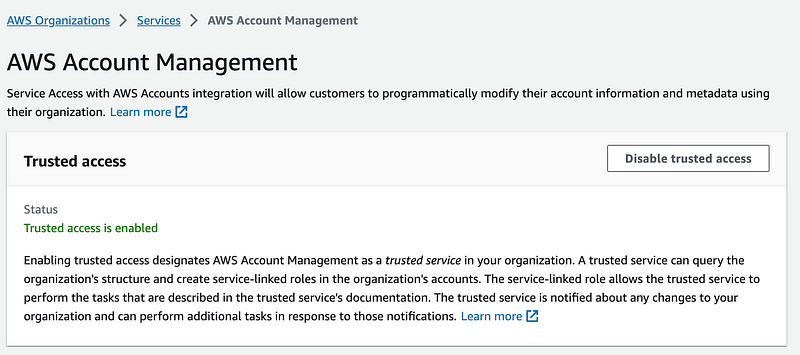
Let’s go look at the account. I clicked on every tab. No sign of delegated administrator access here either.
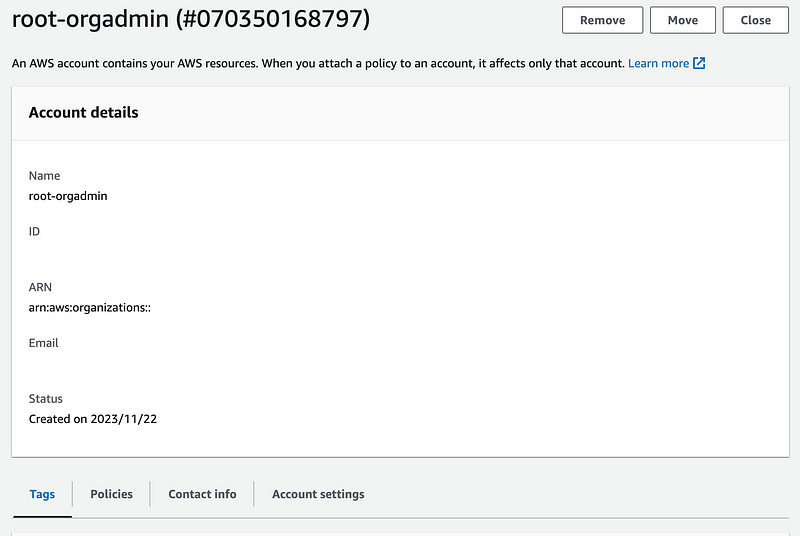
Click on settings. No delegated administrators listed here.
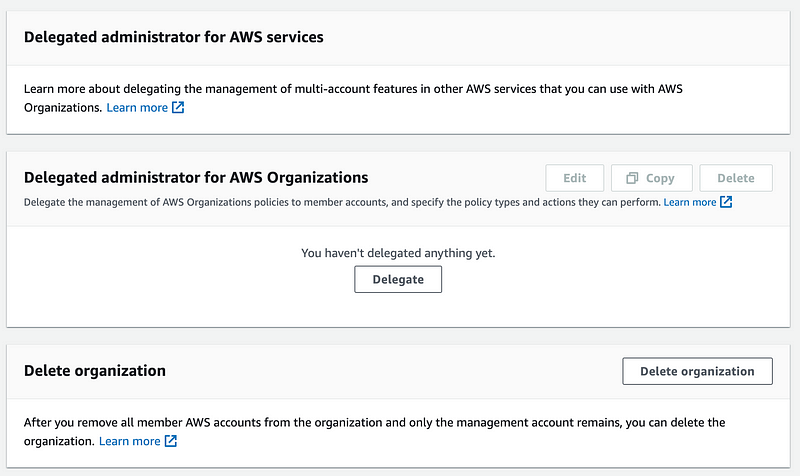
The link to Policies in the left menu is not related.
So if you’re looking for which accounts have been added as delegated administrators for AWS services it is not in the AWS Console at this time on the AWS Dashboard (that I can see.) Maybe it will be added soon. AWS:Reinvent is next week so we’ll see what new features await us!
You can list delegated administrator accounts for your organization using this command:
Using that command I can see that I have one delegated administrator account configured for a service in my AWS Organization:
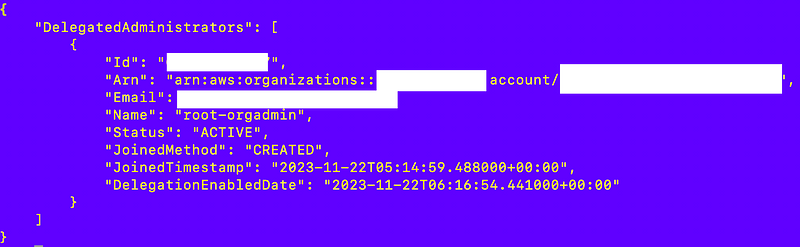
AWS just announced a new dashboard for resources across accounts I need to check out. Maybe you can see delegated administrators there. I’m not going to look at that right at this moment as I’m on a mission to finish a few other things. So many things to do, so little time!
Update: I just realized that there’s a limit on the number of delegated administrators for some accounts — like one. I created a delegated administrator for a service, deleted an account, and then I couldn’t delegate administration to a new account. I think that’s a bug but anyway, I’m going to delegate access to the acount service to my billing acocunt and access to AWS organizations policies to my governance account in a future post.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
