Configuring the VPC and VPC Flow Logs for an AWS Site to Site pfSense VPN
ACM.465 Creating a VPC to connect our pfSense to via a VPN and configuring logging to inspect the related network traffic
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Network Security | AWS Security | Cloud Architecture
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I explained why you might want to route your traffic through AWS.
In this post I’m going to set up the VPC and VPC flow logs manually for use in that architecture.
If you want to automate creation of a VPC and Flow Logs and add some governance to ensure they are always set up correctly I wrote about that in other posts:
Create a VPC (AWS Virtual Private Cloud)
Head over to the VPC Dashboard in AWS.
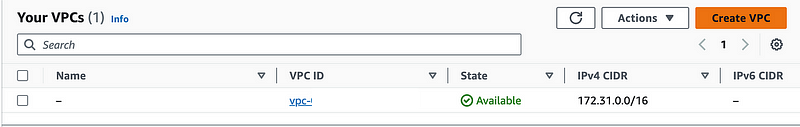
You’ll see a default VPC there but we’re going to create a separate VPC for this process.
Click Create VPC.
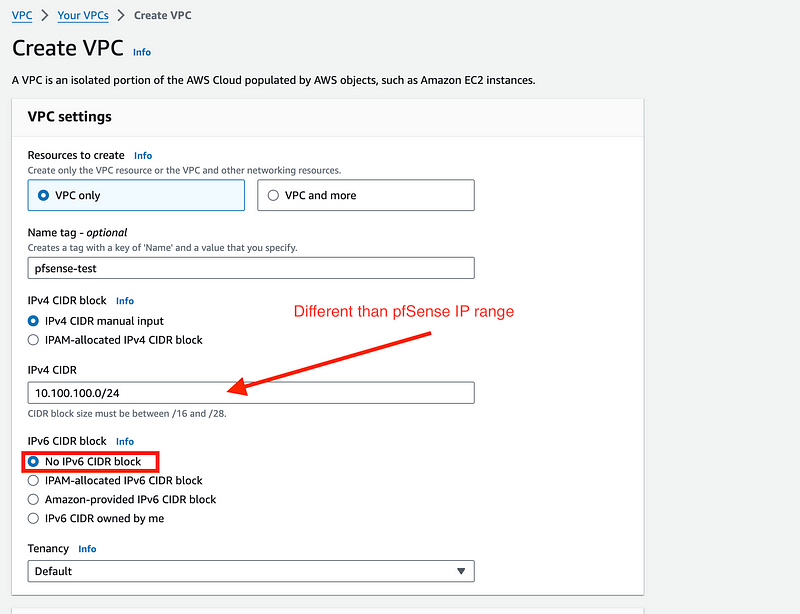
Add the VPC settings:
Click Create VPC.
Inspect the VPC Routes
Why did I create a separate VPC instead of using the default?
Look at the route table for your new VPC:
Click next to your VPC, then click on the route table link. (It might take a minute to show up.)
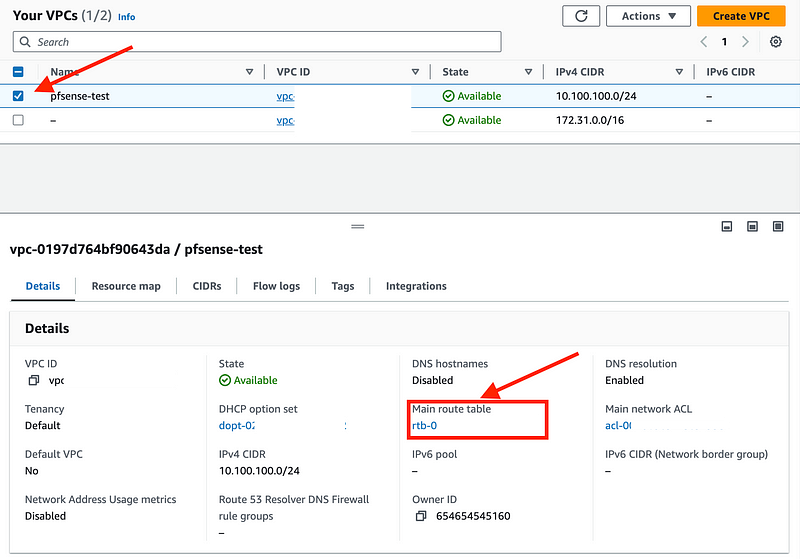
Click on Routes.
This route table only has a local route, meaning anything deployed in this VPC cannot reach (or be attacked by) something on the Internet.
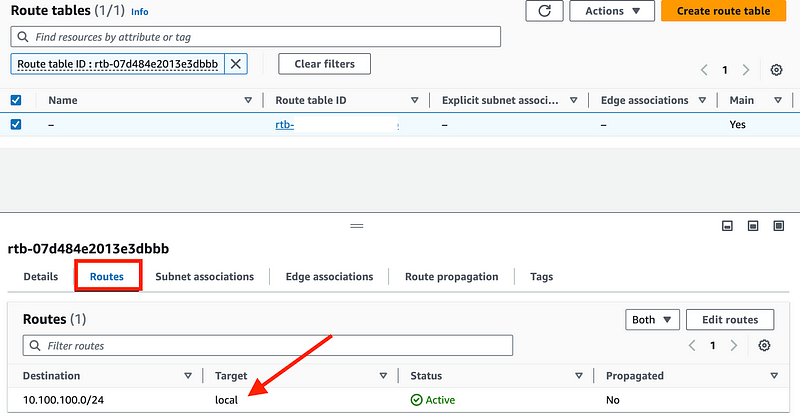
Head back to your list of VPCs and click on the default VPC that was in your account when you created it.
The default VPC in your account has an Internet Gateway route by default. That means traffic can get directly to the Internet. You could remove it but I’d rather just create a new VPC instead and maintain more control over the route tables. Also, when you try to automate you can import that VPC but it may be easier to create a new one. Also some tools look for and use the default VPC and I want to make sure this VPC I’m creating is not used for anything except the purpose for which I am creating it.
Configure VPC Flow Logs for your new VPC
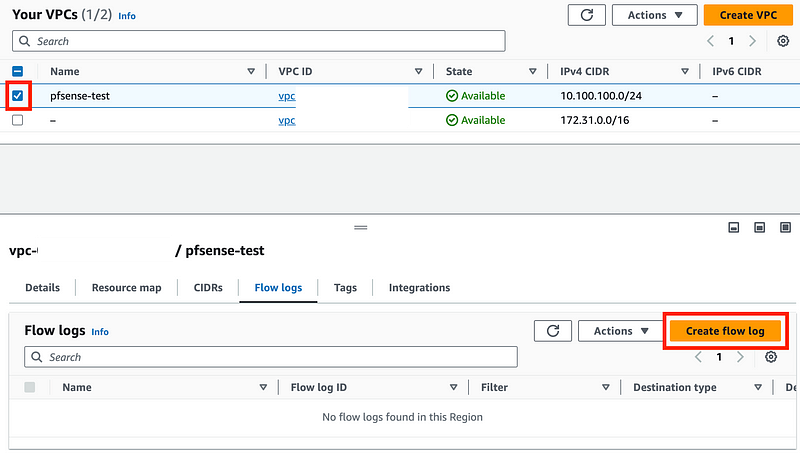
Head back over to the VPC list and click on your new VPC, then Flow Logs.
Because I’m not going to send a lot of traffic to AWS I’m going to go ahead and select a 1 minute interval to see traffic more real time. The traffic will show up either based on a time interval or the amount of data in the logs — see the AWS Flow Logs documentation for details.
Also, we need to create a role for VPC Flow Logs and I’m going to send my logs to CloudWatch, which requires a log group. See the next steps.
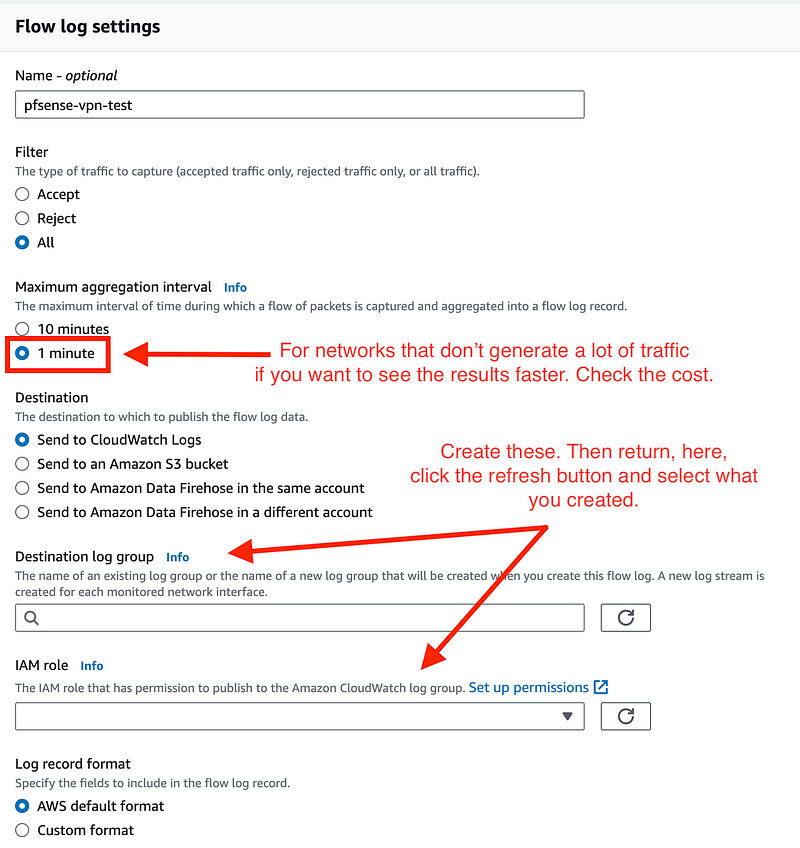
I like to open a new window so I don’t lose what I was doing.
Click on the AWS window and choose open in a new tab.
Create a CloudWatch Log Group
CloudWatch is the service where you can store AWS logs of almost any kind.
Although AWS doesn’t specifically have a SIEM solution, this is a log repository where you can store all your logs and create any sort of automation you want based on those logs. I wrote about how to do that in a white paper for SANS nearly a decade ago now in a white paper entitled Balancing Security and Event Driven Automation.
Larger companies and organizations may want to explore Security Data Lake:
Some companies opt to store logs in S3 to save money but then you have to have the tools to query the data the way you need and to keep those buckets secure.
CloudWatch will work well for this small test and it works well for most of the things I do. You can check out the pricing here:
Head over to the CloudWatch dashboard.
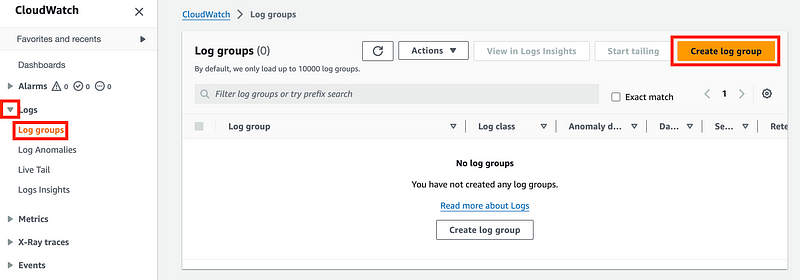
Expand Logs. Click on Log groups. Click Create log group.
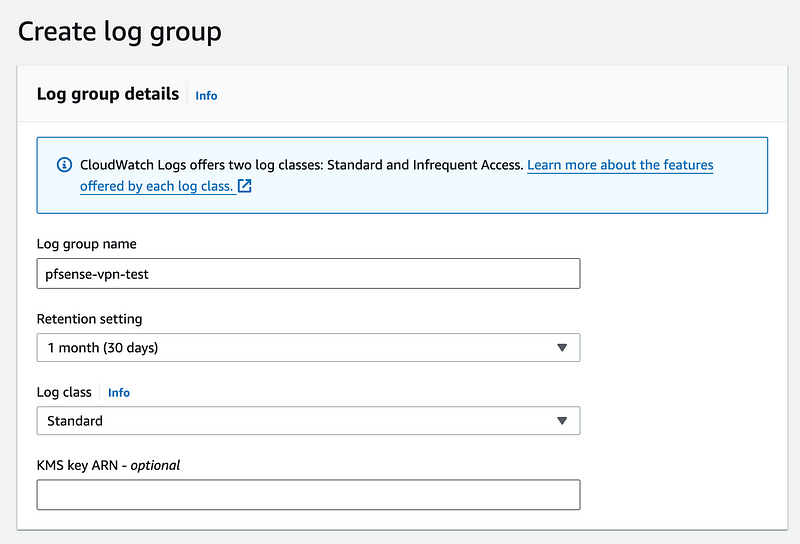
For my long term solution I’d want to create a KMS key but this is a short test. I’m also going to set the retention setting for the logs to 30 days. As logs accumulate you will pay for storage so you have to balance how long you may need them for a security incident versus the cost of retaining those logs.
More on KMS Keys to encrypt your data here:
Click Create.

Create an AWS IAM Role
Right click on the AWS Logo again and right click to open a new tab.
Head over to the AWS IAM dashboard.
Click on Roles and Create Role.
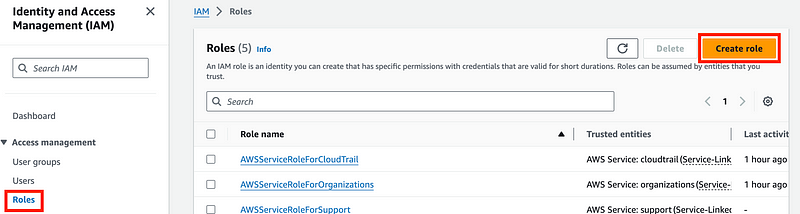
I’m going to create the role described in this documentation — and I don’t see a good way to do that other than to create it manually. This used to be easier and I don’t know why AWS changed it.
Choose Custom trust policy. Copy and paste the role trust policy from the documentation. We could add some additional restrictions here using conditions to limit this role further which I wish AWS would add to their documentation. I also wish they would limit the documentation for this to one page as there are multiple sources with this same information. But for now I have this:
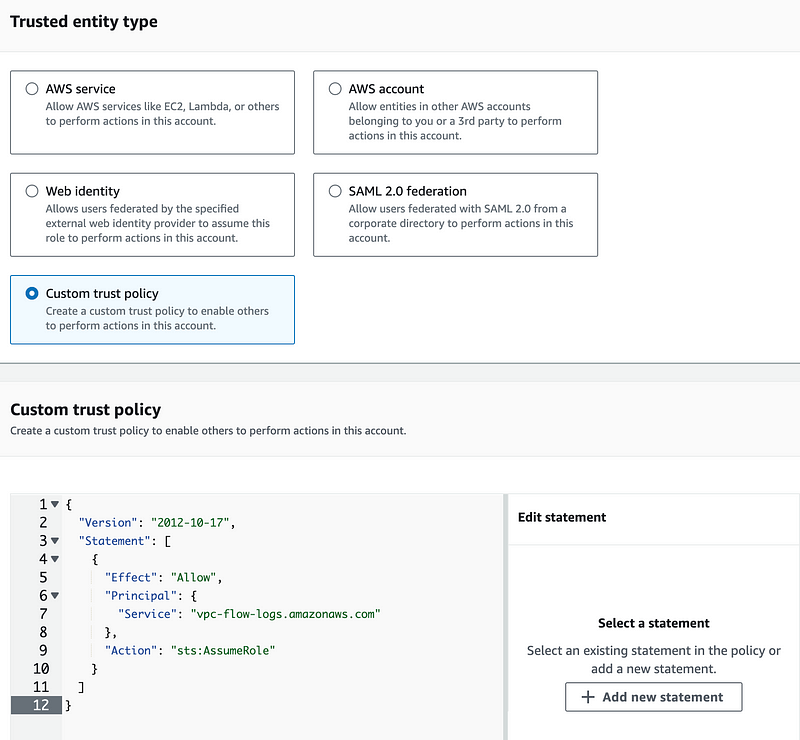
Click Next.
Sadly, AWS does not offer a managed policy for Flow Logs:
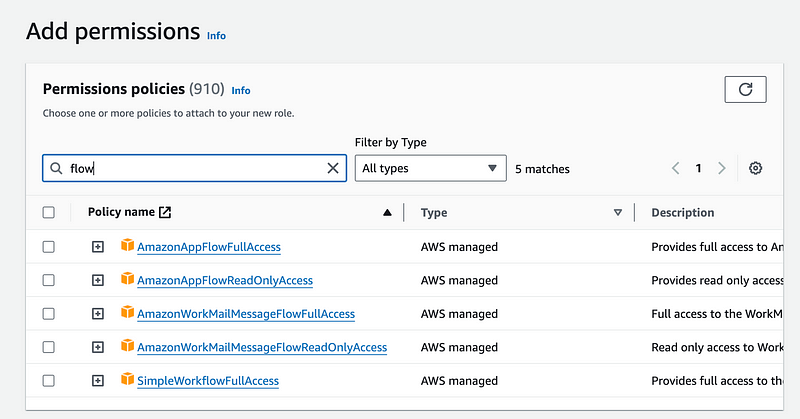
So we’ll need to create a new policy. Once again, I right click on the AWS logo and choose to open the link in a new tab.
Head over to the IAM dashboard.
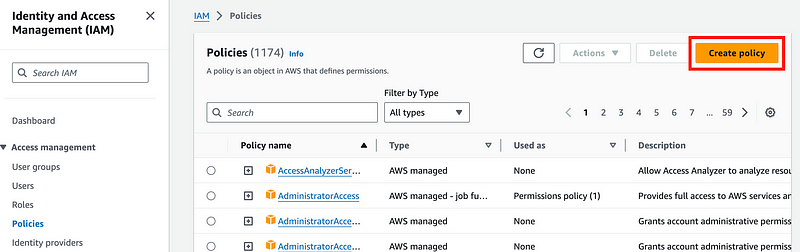
Click Policies and Create Policy.
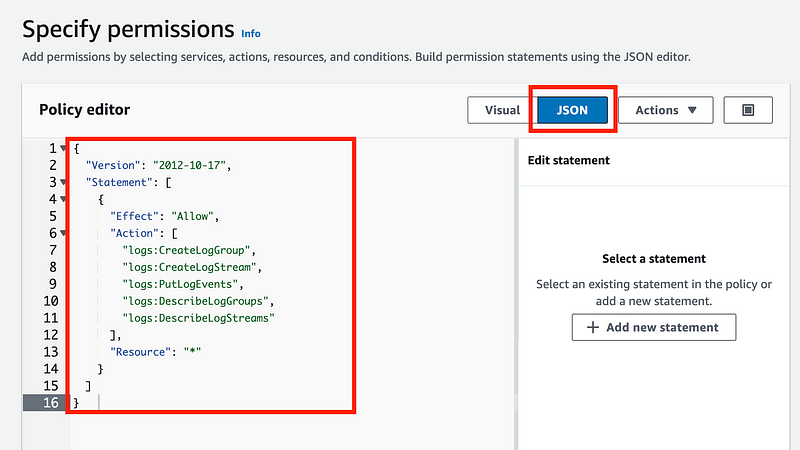
Click JSON. Copy and paste the policy from the documentation.
Note that this policy could be better. It could restrict this role to operate only on the Flow Logs group and only in this specific account and so on as I’ve mentioned in other posts on IAM.
Click Next:
Give your policy a name.
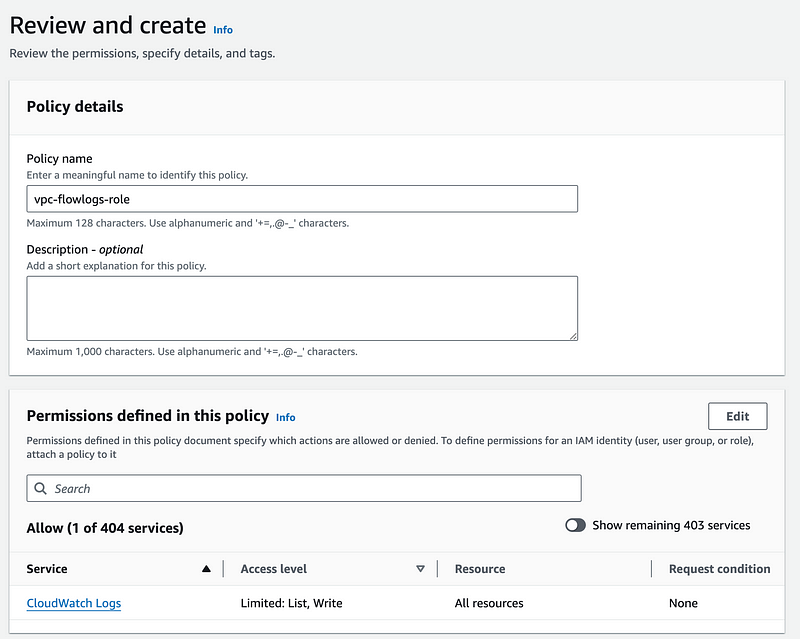
Create the policy.
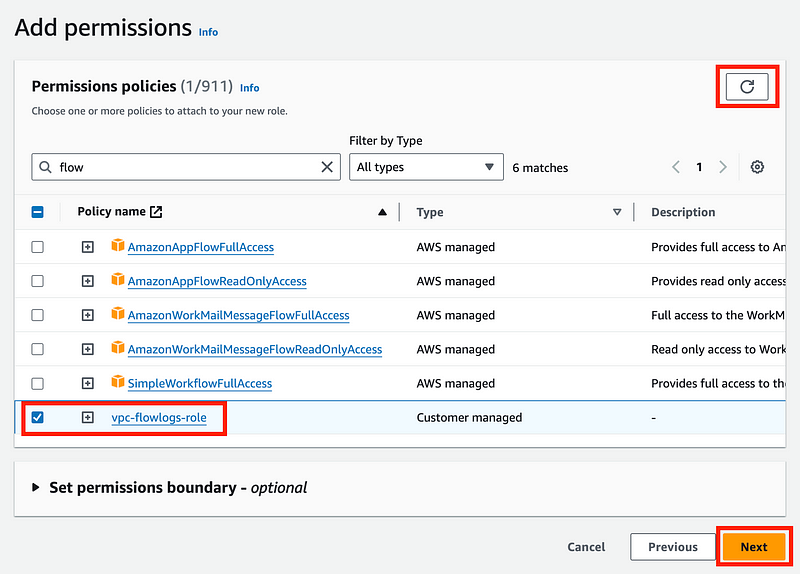
Return to the tab where we were creating the role.
Click the refresh button.
Select the role you just created and click Next.
Give your role a name.
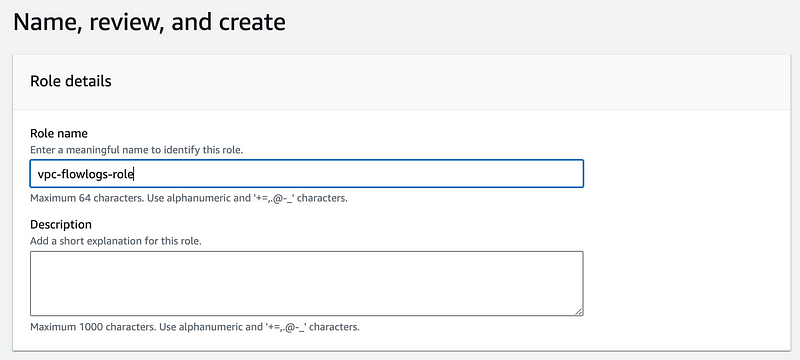
Choose Create Role.
Also be aware of who else can modify your logs and create policies that govern your logs appropriately.
Complete the VPC Flow Logs Configuration
Click the two refresh buttons and the items you just created will appear in the list when you click the text boxes for your log group and IAM role. You can now select them.
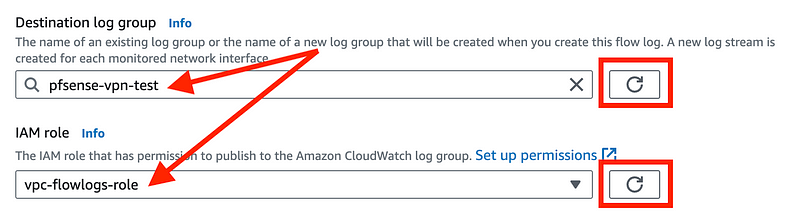
Click Create Flow Log.

Head back over to your VPC. Click on it. Click on Flow logs. Verify that you see your new flow logs entry.
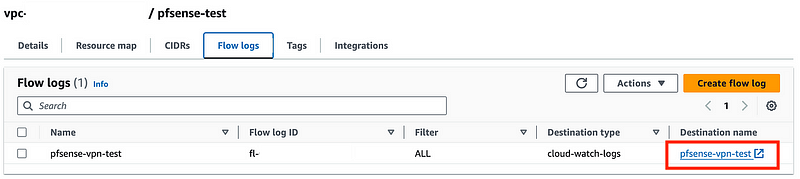
You can click on the flow log link on the right to see the log group where your logs will end up. Right now it’s empty because there’s no traffic flowing in our VPC.
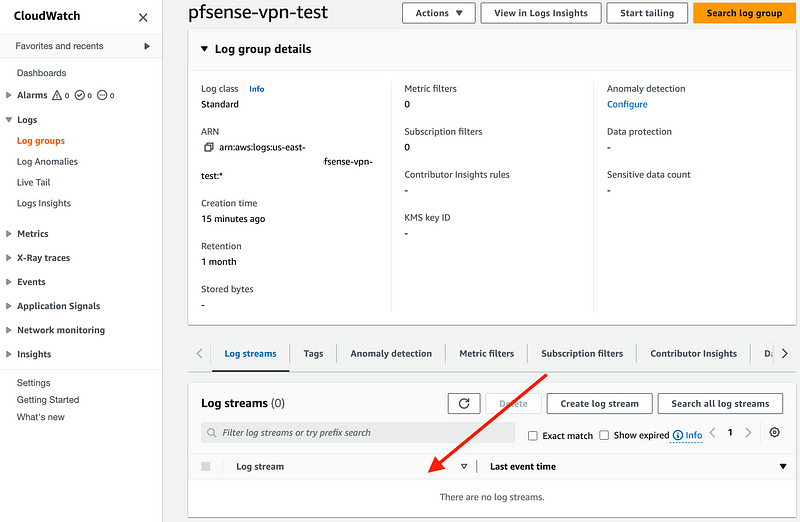
If you follow along in this mini-series on sending traffic from a pfSense through AWS to the Internet, you’re going to end up with the following logs in this log group:
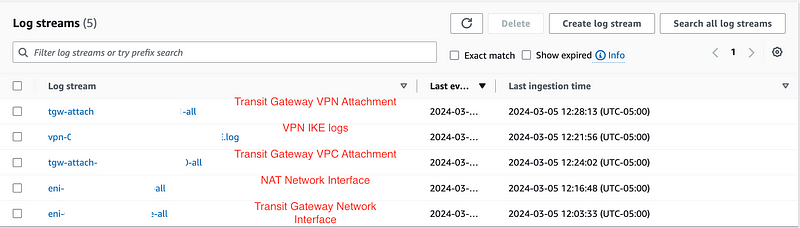
The logs will have different formats.
- The ENIs will have VPC Flow Logs.
- The Transit Gateway logs show traffic flowing through the gateway.
- The VPN logs show the IKE connection information.
I’ll show you those logs in a separate post.
Now we have a VPC and Flow Logs set up to send traffic logs to CloudWatch. Next I’m going to create my subnets.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab





