Check Your Google Chrome Version
Bonus: Difference between vulnerabilities discovered by security researchers and zero day updates in security announcements
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Cybersecurity | Google Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I’m supposed to be getting ready for an Azure class, but this PSA is too important to wait. Thanks to some trolls I thought it was worth a few minutes to write this up. I blame an outdated version of Chrome that isn’t highlighting typos for any misspellings. j.k.
Whenever I get trolled on something and it seems people are trying a bit too hard it always makes me wonder about their intentions. Often they sound angry instead of simply pointing out a mistake or expressing a different opinion. They usually aren’t following me. They often have very few followers (but not always). That happened to me yesterday. The troll comment also got reposted by a non-cyber bot-looking account which made me extra suspicious. Meanwhile, the tweet was getting likes by credible security researchers.
As a side note, another topic I get trolled hard on is IPv6. If you choose to use it, make sure you understand the details of the protocol, how it is different from IP4v, and how to configure it properly to not expose internal system information. I often wonder what the objectives are of the IPv6 trolls and why they care so much what version of IP I'm running on my *home* network. Why does that matter to anyone else? Consider troll motivations.I’m going to explain how to check your Chrome version because having auto-update on doesn’t always work and in my case, I double checked and one of my systems was not up to date. I’ll also explain how to manually update when auto-updates are not working. First, and explanation of different types of updates and why some are more critical than others.
Different types of vulnerabilities and updates
For my new Twitter “friend,” here’s the difference between this security update and some others. Often security researchers will try to find security problems with Google. They will report them to Google and get paid for them. In theory, the only people that know about that update are the security researcher and Google.
In this case, Google is reporting that someone is actively exploiting a security problem in the wild, for which no update previously existed. That’s known as a Zero Day, meaning a fix for the problem has been available for zero days. Attackers are using it to exploit systems and there’s nothing you can do about it (except possibly network security which I write a lot about on my blog and have more coming!)
In recent announcements, Google stated that attackers were exploiting security vulnerabilities which indicates that the vulnerabilities got discovered when attackers exploited a system — not because a security researcher shared a vulnerability with Google.
Who are these attackers exploiting Google browsers? Well we have a lot going on in the world right now as I have explained before and everyone should be on high alert. It appears that multiple countries may be coordinating on cyber attacks from reports I have read. Whatever the case, it’s a good idea to make sure your systems are always up to date.
I retweeted a news article about a Google update that was being exploited in the wild. The update is coming in a couple of days, but you can get it manually.
Check your Google Chrome Version
I went in and checked my Google Chrome version and suggest you do as well. Here’s where you check on a Mac — Click on Chrome in the top menu and About Google Chrome. Edit: I just checked on my Windows machine. Type “Update Chrome” in the search bar and click the button. On phones you can check your applications for updates. It’s funny that my significant other does that probably more often than I do. Every day he asks me, how many updates do you think I have today?
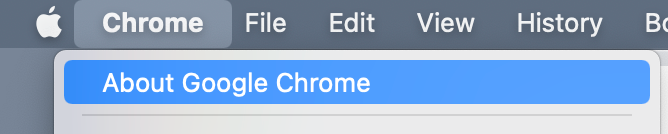
Once again my updates are not working. I was not sure if I was running the latest version because the Google releases page has the latest “beta” version. But I guess everything is in eternal beta at Google.
After I manually updated I got this version: 101.0.4951.41
New: On the same day I updated another Mac and got this version:Version 101.0.4951.54 (Official Build) (x86_64)I searched on that version to find the latest Google stable release version which oddly doesn’t come up when I search for “latest Google version” in Google:
Additionally, when I search on Google Stable Version I get old cached results.
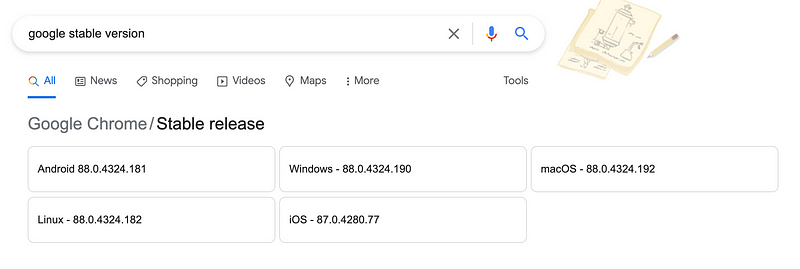
Manually update Google Chrome
Google update wasn’t working for me. I got this error:
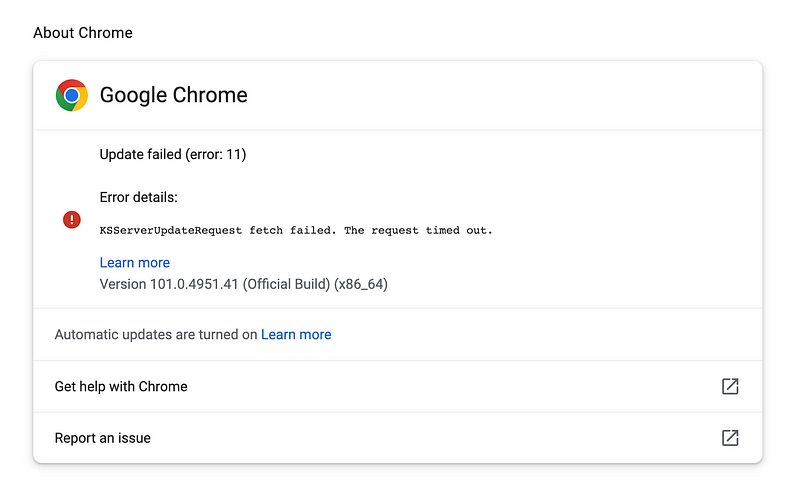
I presume this is my fault because if you read my blogs I’m not the average Internet user. However, I have the network open to the Google update servers. I certainly hope that Google is NOT requiring third-party cookies or inbound network traffic for this to work.
Before you update you might want to switch your DNS servers to this service from CloudFlare which blocks known malicious domain names:
To update manually go to the Google download page, manually download Google Chrome, and reinstall it. Here are some problems you might have:
Can’t download using Google Chrome (especially if it is infected)
Download from an alternate browser such as Safari or a Microsoft browser. The last time I did this I completely deleted Google Chrome from my system and reinstalled.
Make sure you shut down Google chrome.
You can’t install a new version of Google Chrome when you have Google Chrome running. Terminate it and then install the new version.
Replace the existing version.
You want to make sure the old version is removed so you don’t accidentally run it. As I just mentioned, I completely deleted Google Chrome before installing the new version last time. When you install on a Mac choose the option to “replace” instead of keeping both versions around. I haven’t tested on Windows but if you get a similar option do the same there.
That’s it for now — back to work!
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






