Abstraction and MITRE ATT&CK
Leveraging abstraction to come up with primary points of attack
One of my posts on Cybersecurity and The Principle of Abstraction.
Free Content on Jobs in Cybersecurity | Sign up for the Email List
I’m reviewing MITRE ATT&CK as part of the work I’m doing on secure software coding. I’ve heard that the MITRE ATT&CK conference is amazing. I’ve never been but would like to go someday. It looks like they will be broadcasting live from the next conference on March 29 & 30, 2022 so I’ll try to join that. You might want to as well!
MITRE ATT&CK is an amazing resource of all the ways in which attackers try to break into your systems. The myriad of ways they can do this can be quite overwhelming. How do you digest and apply this information? As I’m reading through the different methods of attack I imagine someone’s head exploding as they try to write security policies. What is a person to do with all this data??
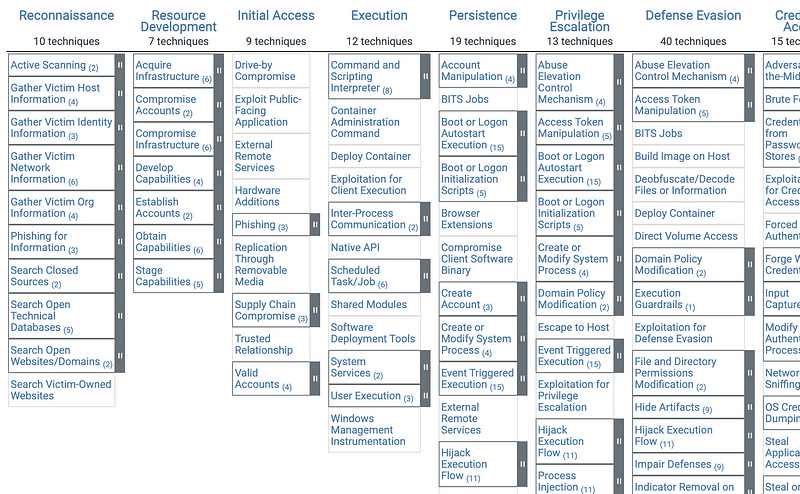
Many books and articles cover the topic of applying this framework in your organization so I will refer you to them for an in-depth discussion. I haven’t read them all, but it’s on my to-do list to explore those further. I have my own opinions and approaches. I’ve talked to customers about the application of MITRE ATT&CK on IANS research calls about my perspective. I’ll share some of that here.
As I’m going through the list in detail to determine what details I want to put into my book this thought came to mind. I’m writing kind of free-form here so I’m not sure if it will lead or if I will include it in the book, but I wanted to write it down while it’s on my mind.
The key point which applies to a lot of security issues is this:
When dealing with an overwhelming amount of data, abstract it into higher-level categories. See if you can deal with categories of items as a whole instead of individually.
I’ve been thinking a lot about abstraction and its application in security for some time and used it throughout my career to reduce risks. In the book, I’ve written about abstraction to reduce code and the chances of a bug that leads to a security vulnerability. Reduce the number of lines of code, potential bugs, and things you need to maintain. I have ideas for other books on different aspects of security that will also leverage the principle of abstraction.
When looking at MITRE ATT&CK here’s how I would apply abstraction. First of all, look at the category of reconnaissance. What’s the key point here?
Don’t expose your data unnecessarily.
The details are great because it goes into depth and shows many ways data may be exposed. It can get people thinking as they create new processes and applications. It will help explain to people that may be vished that they should be careful what information they share. I explain to software programmers how their error handling might expose data unnecessarily.
But after listing how attackers may try to obtain useful information and get at data, they may come up with a new method tomorrow that’s not on that list. When people are thinking about how to secure systems, rather than thinking about the tactics attackers will use to get at your data, think about how you may be exposing data unnecessarily.
Let’s add this to our abstracted list:
- Unnecessarily exposed information
Developing attacks
Some of the details of MITRE ATT&CK go into how attackers set up their infrastructure and develop an attack. This information is useful for those who are investigating attackers and trying to hunt them down. For the most part, these are things attackers do before an attack and most of these things don’t directly affect the average business or organization.
However, there are a few concerns on this list. An attacker might try to use your resources to carry out their attack. They might trick people to add their resources to your network or physical location. Let’s add these two items to our list of abstractions that we need to worry about when considering what to do about cyber attacks:
- Tricking People
- Vulnerabilities
Initial Access
How the attackers initially access and compromise systems and networks is of primary concern. If you can stop the initial attack vector, then you can stop right here and you don’t have to worry about the rest. As we all know, that’s really hard to do, and you will have to worry about all the rest but to me, this is the very most important category in all of MITRE ATT&CK. Stop them before they get a foot in the door.
So what type of categories of problems do we have in this list? Once again we have the following two items:
- Tricking people
- Vulnerabilities
We also have the category of stolen credentials. Stolen credentials may be obtained through….tricking people and vulnerabilities. However, they may also be obtained through other methods such as a third-party site getting compromised.
- Stolen credentials
There’s another category in this list which is all-too-common in cloud environments. Misconfigurations that lead to data exposure or system compromise. When an S3 bucket full of user names and passwords gets incorrectly exposed to the Internet, attackers can use them in subsequent attacks. The misconfiguration may also allow attackers to obtain access to systems. Let’s add that to our list. In this case, I’m going to call it system configurations to differentiate it from network layer problems.
- System misconfigurations
Another category that we’ve already covered is also listed here. Unnecessarily exposed information. Here, the unnecessarily exposed information is the fact that an organization uses remote access services such as SSH or RDP. I wrote about those services in my book on cybersecurity fundamentals and why exposing them is a problem. The fact that those are exposed allows an attacker to try to break into them and use them either by brute force or vulnerabilities. Brute force attacks can lead to stolen credentials so I’m not going to list that as a separate category.
For my purposes, I’d categorize the exposure of RDP and SSH as a network security problem. Some people don’t consider exposure of RDP or SSH to anyone on the Internet to be a security problem. I worked at a large company where we reported a list of SSH ports open directly to the Internet but they did not take action to resolve it. After demonstrating all the ways in which attackers have exploited, brute-forced, or exploited SSH and RDP in attacks, perhaps they will likely agree that exposing the ports is less secure than maintaining those services within a private network. So let’s call it a weakness.
- Network security weakness
Supply chain attacks through vendor systems was another topic I covered in my book. It’s almost spooky how close the Solar Winds attack aligned with my warning in that book. I have a lot more to say about supply chain attacks but for now, make sure you understand this attack vector. I’m going to call it out separately because it requires a different type of approach to managing third-party systems and components on your network versus those you build and manage in-house.
- Lack of supply chain management
Tactics After Initial Access
I would consider almost all the remaining categories to be tactics that attackers use after they obtain initial access. Those tactics are incredibly important for security defenders who are monitoring networks and trying to spot attackers that have entered their networks or obtained a foothold on systems. Many reports such as the Verizon Data Breach Investigations Report explain how attackers persist in networks for months after the initial attack. In the recent Solar Winds breach, the malware did not start taking action until two weeks after it got access to systems.
I’ll add lack of monitoring to our list. Every organization needs a security team that does a deep dive on these tactics and methods of maintaining persistence, moving laterally within a network, or performing other actions to carry out an ongoing attack. Once the people monitoring systems discover a security problem they need to deal with it appropriately. That’s why companies need an incident response team or a vendor that provides this service to them.
- Lack of security monitoring & incident response
There’s one category listed separately here that I’ve already added to my abstracted list. Credential Access explains all the different ways attackers may try to obtain and steal credentials. Credentials often provide the means by which an attacker initially accesses a network. I already mentioned brute-force attacks and other ways credentials may be stolen or compromised.
Although there are many ways for attackers to steal credentials, there is one primary way to stop them from using them. Multi-factor authentication or MFA. However, MFA alone cannot save you if it is not configured and used securely. I covered that topic in my first security book. MFA is the primary means used to defend against stolen credentials so I’m going to change my abstracted item in my list from stolen credentials to the following:
Stolen credentials becomes…
- Lack of Secure MFA
Alright, so now we have a shorter list to work with. What did we end up with? I’m going to change “Tricking People” to the following “Lack of Understanding Cybersecurity Attack Vectors” to align with the other items on the list. We want a list of problems we can fix.
- Unnecessary Information Exposure
- Lack of Secure MFA
- Lack of Understanding of Cybersecurity Attack Vectors
- Vulnerabilities
- System Misconfigurations
- Network Security Weaknesses
- Lack of Supply Chain Management
- Lack of Security Monitoring & Incident Response
This is my abstraction of MITRE ATT&CK. Yours may be different. This list provides an actionable list of high-level security problems you will need to address to stop cybersecurity attacks. As I explained in my first book on cybersecurity fundamentals, an inventory of systems does not stop a cyber attack. It is a subtask of an action that does — fixing all the vulnerabilities and misconfigurations that exist on your network.
All of these actionable security items and how to measure them (to some degree) were covered in my book. I also included other questions executives should be asking about their cybersecurity defenses for a holistic, high-level approach to cybersecurity. To ensure you have properly implemented these defenses, you will need things like security assessments, audits, and penetration tests to confirm these security gaps do not exist. You will need governance to ensure that you prevent problems from entering your environment in the first place and an exception-handling process to deal with security problems you know exist but have been, hopefully temporarily, approved.
An organization can assign the items in my abstracted MITRE ATT&CK list to different teams. Those teams will need to do a much deeper dive to ensure you have addressed all these issues appropriately. As I explain in my first book many security controls have a lot of caveats, “it depends”, and nuances that these teams will need to consider when resolving those problems. Many companies who have been breached employed MFA. Why? Sometimes the way MFA is used is not as strong as it could be as I explained in my book. Sometimes the MFA mechanism itself has a vulnerability.
Your security experts within your organization will analyze and address the items in my list in more detail by leveraging tools like MITRE ATT&CK. But from a high-level perspective as an organization and at the highest executive level, these are the key categories you’ll need to address to stop data breaches. As you delve into each category, you can break them down further and divide up the responsibility. For example, vulnerabilities may exist in hardware or software. You may have internal or external systems that contain vulnerabilities. Who in your organization is responsible for those different aspects of vulnerability management?
Within your own organization, your developers are responsible for writing code that may have vulnerabilities in it. That’s the topic of a book on secure programming I’m writing at the moment. Within the realm of software programming, we can take this same approach. We can abstract software problems into larger categories and manage them more effectively.
Consider how your organization addresses each of the categories I’ve listed in this post and how thoroughly you address the problem. If you’re not sure what these categories entail, check out my first security book that dives into it and stay tuned for other books on the way that aim to provide even more details on strategic approaches to reduce security problems in your organization.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






