MFA is a pain — why bother?
Can we get rid of passwords too and go Passwordless?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Related Stories: Cybersecurity for Executives
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~

It seems impossible to prevent stolen passwords. What’s a system administrator supposed to do when third-party services don’t correctly hash passwords, expose databases to the Internet, and people keep reusing passwords? Fortunately, there are some things you can do to make it harder for attackers to get those credentials or use them. This is the next blog post in my serious of Cybersecurity for Executives.
As explained in my last post, attackers use passwords stolen in one data breach to get into other systems because people reuse credentials and create easy to crack passwords. I explained how stronger passwords help prevent data breaches. Now all you need to do is create a different very long and hard-to-guess password for all 50 different websites you use that require authentication. So that’s just 50 long, complex passwords you need to remember. No problem, right?

Some people have told me tricks over the years like string together four nonsensical words, so the password is lengthy. Use the first letter of every word of the title of a song. For example, “Girls just wanna have fun” would be “Gjwhf” (but that’s not a stellar password because it’s not very long). You could also use the first letter of some other memorable phrase or sentence. You could try to think of a pattern and change a few characters for each password but if someone is really after you and figures out the pattern that could backfire. It’s probably better than password reuse.
Password managers are applications that were developed to help people with password fatigue and to make it easier to leverage best practices. You can store all your passwords in a password manager instead of trying to remember them all. The password manager helps you log into websites and applications. Alternatively, the password manager may be able to generate complex passwords for you. Password managers are better than reusing passwords for sure. The purpose of passwords is secure password management, so in theory, it should be safe to store all your passwords in them.
The thing that makes me cautious when it comes to password managers is that now all your passwords are in one place. An attacker who can get into the password manager has all your passwords. When malware gets onto a computer, it can potentially read the values of secrets in memory or exploit a vulnerability in that application. I explained how hackers find security vulnerabilities previously, and CVEs already exist for some versions of password managers. However, a password manager from a reputable vendor is still better than easy-to-crack and reused passwords. If you are interested in using a password manager, many blog posts and articles compare the different available products.
Some companies will put their most sensitive passwords (only to be used in case of emergency) in a safe that requires two people to access. One of the considerations — where is the safe? Is it accessible to people who might steal it and break into it? Is it in a safety deposit box in a bank that is not available outside of banking hours? Safes are a valid option, but they come with their own set of challenges.
Other people put passwords on phones. Malware can infect phones as well as computers, but at least you aren’t storing them on the system where you log in — or are you? An attacker can break into a phone and steal files just as they would on a computer. Many people use their phones to check email. Click one bad link, and an attacker may have compromised the phone. In one case, a company put part of a password on one person’s phone and the rest on another.
No matter how you look at it — passwords are tricky to protect!
An alternative to passwords involves biometrics — letting people log into systems using their fingerprints, faces, eyes, or handprints. When I used to host servers at a facility in Seattle (The term for this is co-location and preceded the use of public clouds or managed hosting), I would have to put my hand on a scanner that would verify it was me before letting me in. It was so cool and high-tech at the time. Now phones and computers have fingerprint and sometimes face readers to let you get into your devices and applications.
If we use our fingerprint to log in, our face, or our eyes, the attacker can’t steal those, so we’re good, right? Hold on a minute. Think about how a computer validates your fingerprint. You put your finger on the reader, and the reader captures an image or digital replica of your finger. How it that stored? Bits and bytes on a computer or device — just like everything else! An attacker can steal that just like any other type of data.
Let’s say you go to a restaurant and have a drink and someone swipes your fingerprint off of the glass. (Yep, I’ve watched too many of that kind of movies.) Is it possible that the person can now replicate those bits and bytes to trick biometric readers and get into your systems? What if someone steals the bits and bytes representing your fingerprint from some computer system? Can they use it now to log into your accounts? If they can, we have a bigger problem. When an attacker gets your password, you can change it. Security professionals use the term “rotate” for periodic password changes to help prevent attackers from using or cracking them. You can’t rotate your fingerprints. Well, technically maybe you could, but that’s definitely not a preferred option if you ask me.
Here’s another reason why you might want to change your passwords periodically. Sextortion involves an extortionist ask for money in exchange for not telling people what you have done, whatever that may be in the realm of the topic at hand. This problem is happening to adults of all ages and even children. For some of these cases — I can’t help you. Be cautious on the Internet and with people you don’t know and think about what you are doing and how it may be exposed. Sadly, this does happen to innocent people as well who are just looking for love. I also hope depraved people who engage in revenge porn and these types of emails are locked away for many years.
But there’s one related email campaign going around I can help you with, and it has to do with fake emails. I got one, and it threatened to expose some nasty secret. Well, I knew it was false on multiple levels. One reason — it was an old password I haven’t used in years. Regularly changing your password can help you spot a fraudulent email like this. What if you are using a fingerprint? You’ll never really know if they are lying or telling the truth, in addition to not being able to change it to keep them out.
Systems storing biometric data could do things to ensure it is adequately protected using the methods explained in my last blog post. Instead of storing the actual fingerprint data, a hash of the data with a salt might help. I do think biometrics as a second factor is a decent option because you can combine the storage of that data with something device-specific as a salt. The issue remains that if the fingerprint is ever in plaintext at some point in the system as the system is converting it to a hash, malware might be able to access it. Just like with password managers, attackers can steal biometric identifiers while unencrypted in memory.
As a final note on biometrics, be aware that the Chinese government is making use of facial recognition to track and monitor citizens. Nation-state attackers who have your biometric data and licit or illicit access to foreign systems might be able to track people in other countries as well. I’m not a fan of facial recognition systems on many levels. I hope companies like Delta Airlines, who are starting to use facial recognition, do not force people to use it. Not only could a picture easily be swiped that can fool some systems, but 3-D printer models have tricked these systems, and they make mistakes. It is also interesting that the iPhone was one of the first phones to offer facial recognition. It was popular in China, and Apple was using parts from China before the US tariffs that exist at the time of this writing. More on supply chain issues later.
What can we do to make it harder for attackers to steal and use our passwords? How can we ever protect ourselves if we want to use a pin or facial recognition? There’s one other thing that I know of that can help — MFA, which stands for multi-factor authentication. Sometimes it’s called 2FA for two-factor authentication. With MFA even if an attacker gets your password, fingerprint, or pin, they can’t log in because MFA requires a second piece of information. Let’s look at this in a bit more detail because it’s not quite that simple. MFA implementations can be secure or flawed, just like anything else.
You may be familiar with MFA if you have enabled it on your email account or bank account. (Highly recommended!) If you enable this feature, when you log in a number is sent to your phone. You then enter that number into the web application, and it lets you into your account. How does this help? Even if the attacker obtains your password, it’s unlikely he or she also compromised your phone unless you are dealing with an advanced and persistent attacker.
When you attempt to log in, the system sends the password to this alternate location on a separate device and even better if it’s on a different network. Sending the information on a separate channel is known as “out-of-band.” Using a separate channel helps in scenarios where an attacker is listening to your primary form of communication or has control over your device. For example, during data breach investigations, best practice is to use an out-of-band channel like cell phones, in case the attacker has compromised your corporate network phones.
It is essential to understand this last point because some MFA implementations will send the second factor to the same device on the same network. An attacker that can listen on the network may be able to capture all the elements required to log into the system that requires MFA. Additionally, malware on your laptop that has stolen your password can log in to the remote system and get the second factor if sent to that same device. Attackers on your network can try to divert these second-factor messages on your local network to their own devices.
Two factors used on the same machine is like someone emailing a user name and password in two different messages. That’s not going to help if an attacker is reading all your emails! Sending the username via email and the password via a text message over separate networks is better. Now the attacker has to obtain access to both to steal the credentials. You can also encrypt the data using GPG, but that’s a topic for another day.
MFA traditionally involves at least two factors: something you have (a cell phone) and something you know (a password). The point about the something you know is that no one has it but you, and no one can steal it out of some system. It only exists in your brain. That’s the idea anyway. Unfortunately, we’ve gotten to the point where our brains can’t hold all the passwords we’re supposed to remember. We’ll look at a passwordless solution from Microsoft in a minute where the simplest version is two things you have — your laptop and your fingerprint, for example. Its better than a password alone but not the best. A robust MFA implementation will involve two completely separate factors from two completely different channels.
As with anything in security, we make choices based on the risk of loss and potential cost if that loss occurs. Although ideal, different channels might not be possible in every circumstance, but whenever possible, try to obtain this level of separation. For example, you log into your bank on your home WiFi network. You then receive a code from your bank over a cellular network via a text or an application, Google Authenticator.
MFA is not perfect, but it helps prevent numerous types of attacks. If an attacker got your password from a dump on Pastebin, they wouldn’t be able to log in without your second factor. Any attack where an attacker got your password alone and tried to use it on a login screen would fail.
MFA can prevent an attack that has been in the news lately known as password spraying. Many systems implement something called rate limiting which will lock a user out after a specific number of guesses, either permanently or for a set time. To get around this, attackers will send the same password to many different systems at once, one time, instead of sending many different guesses to the same computer at the same time. By only guessing once on any particular machine and spreading out the attacks over more extended periods of times, an attacker won’t hit the rate limit and get blocked out. With this attack, MFA should still prevent the attackers from accessing the systems when they attempt to log in — unless of course, a flaw exists in your MFA implementation.
Attackers may have used a password spraying attack in the Citrix breach, and it appears this sophisticated group is targeting many other organizations. Forbes writes:
According to security firm Resecurity, the attacks were perpetrated by Iranian-linked group known as IRIDIUM, which has hit more than 200 government agencies, oil and gas firms, and technology companies.
During this breach which went undiscovered for five months, the company was using some form of 2FA, but the attackers were able to bypass it. How could this happen? We don’t know all the details about this breach but let’s look at some potential MFA and 2FA implementation deficiencies or flaws.
One of the struggles with MFA implementations is the fact that people get annoyed when they have to enter the second factor over and over again. Some MFA implementations involve a session with a configurable timeout. I explained what sessions are in my prior post. The person logging in has to only enter the second factor once for the duration, which will have a default timeout — maybe 60 minutes, 8 or 24 hours. When a user checks the box to “keep me signed in,” Microsoft Azure AD creates a persistent token. In this case, the user has effectively turned off MFA for 180 days.
Implementation of some enterprise solutions only requires MFA when someone is on an untrusted network or device. I talked all about trust in a prior blog post, so I’ll refer you to that now. Trust is overrated. I remember one company that I worked at that spent a lot of time and energy implementing MFA. After they set it up, I used MFA once and never had to enter it again before I left the company probably over a year later. That is not going to protect you from any of the attacks about which I’ve been writing.
Another type of attack involves tricking a user into entering an MFA token into a fake, lookalike website. A “researcher” (I use that term loosely) developed a tool with lookalike sites for widely used large companies like Amazon. If you enter your pin into a fake website, the attacker can grab it. Users should be trained to be aware this is happening and to be careful to check they are on the correct domain, and using it is an HTTPS link.
Google has a solution to that problem that might be a bit easier for most users. Instead of entering a pin, you can install the gmail application on your phone. When you log into your computer, you will receive a pop up on your phone asking if you are trying to log in and you click yes. No number to enter. A company called DUO, purchased by Cisco, has been doing something similar for a while. This option is known as a push notification. It’s a user-friendly option compared to other solutions I’ve used and possibly more secure. It uses two factors on two different networks. If someone is trying to log into your account, you’ll get notified on your phone. If you didn’t initiate that login, you know someone is trying to get into your account.
Another way an attacker can get access to MFA protected systems is called a SIM Swap attack or SIM Jacking. In this scenario, attackers convince the phone company to switch your phone number over to their own SIM card. Trying to trick someone into doing something so you can get into systems or buildings is called social engineering. Once the attacker has your phone number, they can get into your MFA protected systems if they also have your passwords. Sim Jacking has been happening in the US more frequently this year, primarily to steal cryptocurrency. Hopefully, the phone companies are taking action to train staff who work on the phone and in stores to be vigilant. AT&T is in currently fighting a lawsuit involving SIM Swapping that resulted in stolen cryptocurrency.
To avoid the SIM Swapping attacks, you can use a device other than your phone for the second factor on some systems. Google offers a Titan security key for this purpose though some have complained about the fact a Chinese company manufactures the device. Researchers later exposed a Bluetooth flaw, and Google replaced some of the keys. Some systems, including Google, integrate with another product called a YubiKey which serves a similar purpose. To log into a site on your computer, you’ll need to plug in the hardware device first.
Hardware devices come with their own set of challenges. What happens when the device is lost? How will you securely distribute a device to remote users and authorize them on the network? You’ll want to make sure only the owner of the account can access the information required to register a new device. I have seen a couple of things I do not recommend. Sometimes registration is performed via a QR code. Don’t distribute these via a screen share. Only the owner of the account should have access to the QR code used for MFA!
Additionally, in systems that require a seed or private key (this also applies to software-based solutions), those secrets should never be accessible or known by anyone except the owner of the account. They can be generated in an automated fashion. If your system administrators or anyone else can see or get those values — your system design is flawed. Non-repudiation is not possible, and user communications are at risk of compromise.
Microsoft is pitching a “passwordless” login option for operating systems and online accounts, with biometrics as one of the alternatives and a four-digit pin code as the other. They store a unique number in part of your computer called a TPM (Trusted Platform Module) that is designed to protect secrets in a tamper-proof hardware component. If it lives up to its claim, it is impossible to extract the contents, so an attacker cannot steal your four-digit pin. I presume a hardware device captures the information and it goes straight to the TPM and is never in memory for this claim to be accurate. This claim also assumes your computer hardware includes a TPM from a reliable manufacturer and the ability to store the information in it. More thoughts on supply chain issues arise that I’ll save for a later post.
The idea of getting rid of passwords because people reuse them is intriguing logic, and it sounds appealing. Just make sure, as with all new technology, that you evaluate it carefully before rolling it out to your entire organization. If you look at the first diagram on this page shows a user logging into a laptop, note the number “1” in the photo. I only see one factor in this diagram.
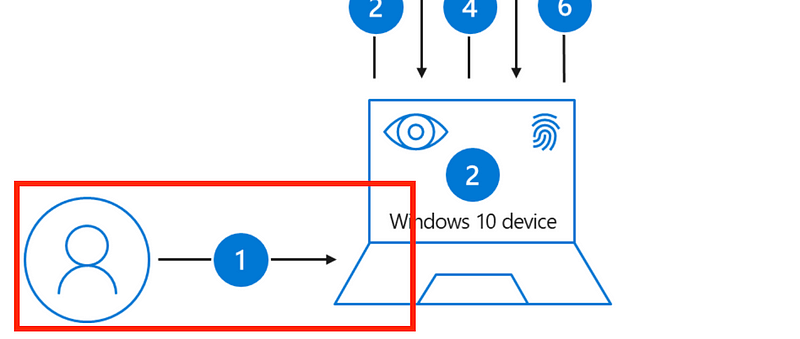
The end-user interacts once with the computer on a single channel. A user only has to know or have one thing (called a factor in MFA lingo) to get onto that machine. In a large corporate environment or at a coffee shop, anyone can walk over to my device if I step away. All they need to get in is my four-digit pin. A four-digit pin is short, and each character only requires guessing one of 10 characters. That’s a pretty easy to crack password even if an attacker cannot extract it from a TPM.
Using the second option with Microsoft Authenticator, Microsoft recommends that you back up your credentials to the cloud. I’m not sure how organizations will feel about Microsoft Azure AD credentials being backed up to Apple’s iCloud, but for some this might be an issue. At least this solution is using multiple out-of-band factors.
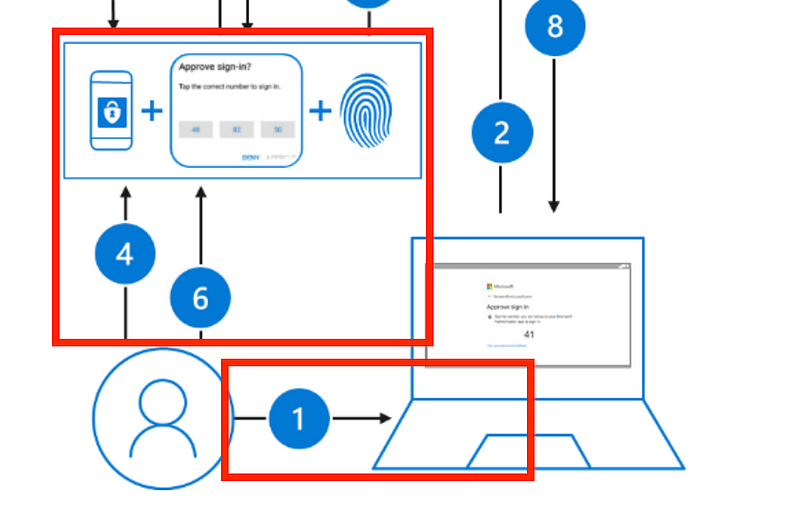
In the last option, the user will use a FIDO2 security key. FIDO standards for Fast IDentity Online and is a set of standards from the FIDO Alliance designed to help companies implement secure authentication solutions. The official definition is as follows:
Based on free and open standards from the FIDO Alliance, FIDO Authentication enables password-only logins to be replaced with secure and fast login experiences across websites and apps
If you take a look at this option, the user has to have two factors — the authentication device, such as a Yubikey and a fingerprint. Only one channel exists in this scenario, but it’s still a pretty good option, depending on the details of the implementation. Following the FIDO standards, the secrets required to identify a user are in a trusted enclave on the YubiKey device and not accessible to system administrators at Microsoft or on your corporate network. If you have a secure mechanism for distributing these keys, it’s difficult for someone to steal the user credentials or impersonate that person.
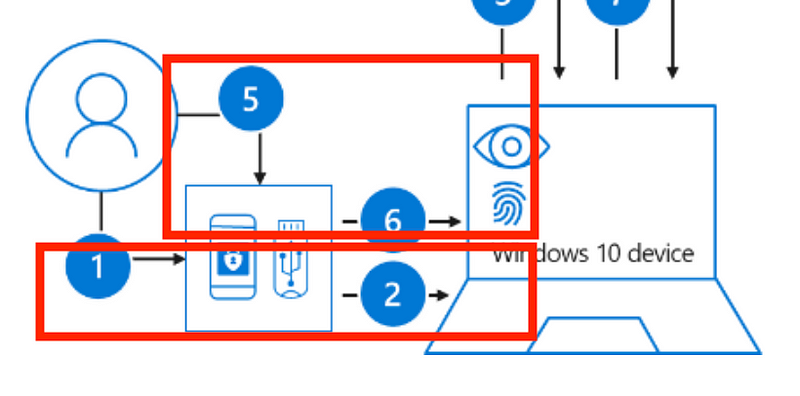
Now let’s think about access to remote computers for a minute. As you can see, the user in the images above is inputting information directly into his or her device. This information is supposed to go directly to a TPM or is biometric in nature. On a laptop configured to use passwordless, Microsoft says the two factors to log in are the biometric or the pin and the device itself. Using the machine you are logging into as a factor to access that machine seems a bit like an oxymoron to me. Using something on that device as a factor for website authentication and device-specific information as part of a hash does make sense. It then requires the user to have that device to log in to something else.
How does passwordless work when accessing remote computers? Here’s where it gets more complicated. As a system administrator at a large company, it is ideal for each person to have a single set of credentials representing their identity for tracking and management. Separate credentials for local and remote access potentially doubles the number of credentials IT departments need to track and monitor. When setting up remote access in a passwordless environment, how can the physical device be one of the factors? The person logging in from a remote location is not sitting at the machine they are logging into and can’t put their biometrics directly into that piece of hardware? Will the biometrics be stored in memory and passed over to the remote hardware? Will the biometric hash be passed around the network?
It appears this was still a work in progress at the time passwordless was released based on some discussions I have read. The solution seems to involve PKI (Public Key Infrastructure) at the time of this writing. I’m not going to attempt to explain it here in layman’s terms, but PKI implementation is complex. Microsoft calls it a Key Storage Provider (KSP). I find the AWS documentation on KSPs easier to understand. At any rate, it seems like certificates are used in place of biometrics once the user authenticates, but I’m still testing this out. Check back later for updates or take my cloud security class to learn more because I’ll be updating that with the results of my research.
I have performed technical due diligence on authentication systems for mergers and acquisitions (M & A). There are a lot of considerations involved in making sure credentials cannot be compromised and will deliver non-repudiation in the case of a security incident. One of your best bets will be to consider using industry-backed standards when choosing solutions. Make sure you think through the potential attacks on any system — otherwise known as Threat Modeling. Test out new solutions in your environment on a small scale before rolling them out to your entire organization. Don’t forget about cloud environments, remote workers, and devices like printers and IOT devices that may require authentication.
Some other hardware and device authentication mechanisms exist to ensure only your approved devices are on your corporate network. I’m not going to dive into those here. If you want to know more read about Public Key Infrastructure (PKI) and 802.1x, to name a few of those options. My biggest recommendation is still to use the concept of segregation to limit what is exposed by a single set of credentials, as I explained in my last post. Lock down your network to limit which devices can access sensitive data. Logging and monitoring failed access attempts will help spot abuse. But on top of that, MFA and changing passwords frequently can help. Keep an eye on the passwordless option and choose the option that provides the right level of security that aligns with risk and the cost of data loss.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2019
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
