Why You Might Need A Better Password
Assessing the risk of the devices and havoc they might be able to wreak (and why MFA might be easier)
I love being surrounded by people that challenge me on my security-minded assumptions. Especially less technical people who say, “Yeah but why does that matter?” It makes me think harder about whether it does matter, when and why and how to explain things.
Recently when someone told me something for which they created a password and let’s just say the password was not ideal. My understanding is that the system also did not support multi-factor authentication. I presume that device is not connected to anything else on the network. However, employees install an app on their phones and possibly on computers in the organization to manage it remotely.
The person did not disagree with me that the password would be easy to guess but their response was “So what?” Who’s going to care and what can they do if they get access to that?
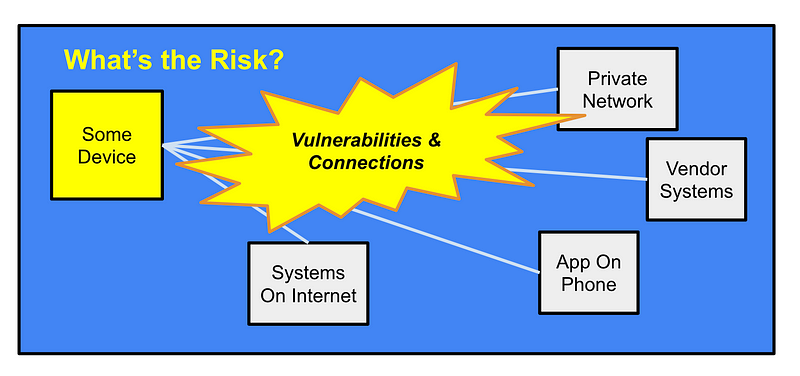
So that got me thinking. Does it really matter? (In other words, what is the risk, which is pretty much the crux of decision making in cybersecurity.)
Whether it matters or not depends on your particular organization and how well that vendor secures their software and network. Basically it boils down to what an attacker, hooligan, or disgruntled former employee can do if they guess your username and password. And, unfortunately, some vendors make those credentials easy to guess.
Here are some questions to ask yourself when trying to assess the risk of an attacker obtaining a password to a system you use.
What can the attacker do with the password?
Perhaps it’s no big deal for that individual system. They might be able to shut off some device remotely. You think, oh well, I’ll just turn it back on. But do you really want that device to randomly be shut off and manipulated and to have to constantly monitor for that problem? What if the device is shut off at a particularly critical moment in time? Yes, maybe it’s not going to cause too much damage but is it an annoyance, waste of time, or complication you can avoid simply by creating a better username and password?
By the way if a vendor creates an obvious username and password for you, they are likely doing that for all their other customers. So now you can probably guess what the password is of all their other customers. You trust yourself and your staff and think they would never do anything bad. But what about everyone else who can figure out what those passwords are across the universe of customers that do business with that vendor?
That problem is why the federal government has mandated that device manufacturers can no longer use a single default password for all devices. It used to be in the past that most devices had a default username and password. It was generally published on the manufacturer’s website so attackers could easily obtain it and scan the Internet for all the devices using those default passwords and break into them.
And, of course, many people never change the default passwords on network equipment. If that’s you, please go change it now.
Attackers then leveraged these devices to commit crimes on their behalf or to monitor the traffic of the users whose devices they compromised to steal credentials and access financial accounts.
This issue recently reared it’s ugly head again as the US government dismantled a botnet infecting many people’s and organization’s home networking equipment (again).
In many cases, attackers are breaking in using malware, not compromised passwords, but compromised passwords just makes it even easier for them to get into systems and devices. Even though your vendor may not be using the same default password for everyone, an easy to guess password is just as bad. Anyone who can figure out the vendor’s patterns for setting passwords can compromise their customer systems.
How attackers crack passwords
When people like me use password crackers on a penetration test, which simulates what attackers do in the real world, we start with a wordlist that might be used in passwords at your organization. For example, I might use the name of your organization, or any words associated with your organization in my list of words and phrases to feed into my password cracker to guess those passwords. Then the password cracker will manipulate those words in various ways like replacing the letter E with 3 or adding an exclamation point or number to the front or end of those words.
How attackers leverage stolen passwords to access multiple systems
In some cases, attackers access passwords that are stolen in a data breach. For example, they got a list of stolen passwords in a breach of one of your vendors and it included the usernames and passwords for all the customers who log into that vendor website.
Ok, the vendor let you know and you changed your username and password so you’re good right? Well, not if you used that username and password in some other system. The attackers will use what is called Open Source Intelligence (OSINT) to find out everything they can about your employees and your organization. They will figure out or guess what other systems you are using where you may have used that same password and try to login using that password.
If you use the same password in multiple places, they might get into a system that was not breached using the username and password from another breach.
The problem with shared usernames and passwords
If you are using a shared password for all your devices that allow you to access systems remotely, you had better have a good handle on all those systems and make sure you can immediately rotate all the passwords when you decide to let someone go or you have someone who goes rogue in your organization. For this reason, it’s always better to create a separate username and password for each user. It also allows you to better track who did what.
The other issue is that, let’s say one employee’s phone is compromised in the scenario at the top of this post. Attackers are using that device to access the system. It’s easier to identify the source of the problem and change that one password without affecting other people who need to operate the device.
Another issue with shared credentials is that you can more easily get locked out if you only have one set of credentials and someone is able to change the password. If you have multiple logins and an attacker gets access to one device and resets the only password you use to get into a system you’re stuck. If you have multiple logins and the system doesn’t allow one person to change another person’s passwords you still have a way to manage the device and access related systems.
Most security frameworks and any compliance regulations for financial-related systems, for example, mandate that you use separate usernames and passwords for each individual that accesses a system for those reasons.
How stolen credentials for a vendor management system allowed attackers to steal a massive amount of credit card numbers in retail stores
Perhaps that system is not incredibly important but access to that system allows the attacker to get access to something else on your network. Consider the Target breach. No, the attackers did not get access to an HVAC system itself as was incorrectly reported by various sources.
They got malware onto the computer of one of Target’s vendors. Then they stole the vendor’s username and passwords and used them to log into the portal that Target used to manage vendors.
Once the attackers logged into that website they found vulnerabilities in that web application (the way I do on penetration tests and report those vulnerabilities to my customers so I find them before the attackers do.)
From there, the attackers attacked other systems in the network until they made their way to the point of sale systems (the systems that process credit cards.)
They used very sneaky methods to send messages on the network and exfiltrate data as I explained in a white paper on that data breach written for SANS Institute.
A fish tank thermometer was used to hack a casino
An attacker got access to a thermometer in a casino and used that to access the high roller database and exfiltrated it through cloud systems according to various reports.
It’s just a fish tank, right? But what else can it access on your network? Are you installing an application to control it? What can that application access? Other applications on your phone?
So what’s the risk?
The question is often not what the passwords and access to the system alone can do — but whether the system that the attackers get into has any vulnerabilities and what else that system can access.
Let’s say you’re not concerned with what the attackers can do with what the system is supposed to do if they get access to the credentials. That’s often not the biggest problem. Beyond that, what it really what it boils down to is this:
Can the attackers leverage access to one vulnerable system to get into or attack others. The vulnerability may be a weak password, or a system flaw that can be accessed and leveraged after logging into the system. The attackers may use it to get into any other connected devices on the same network. They may find a way to spy on any traffic on that same device or network where the application for the device gets installed. The attackers may be able to use that system to attack other systems and interfere with network traffic.
That’s the risk you need to think through when you create a weak password for a device that you connect to over the network. Maybe it matters, maybe it doesn’t.
But the attackers can still break in some other way, right?
Even if you use a strong password there are other ways attackers break into systems, but the way I think about it is to limit the chances you give attackers in as many ways as possible. This is called “limiting the attack surface.” Each attack you take away makes the attacker’s job that much harder.
Want to create a better password that you can remember? Use a longer phrase like a line from a song or a set of random words. You can also use the first letter of a phrase, for example. Avoid the name of your pet, mascot, birthdays, anniversaries, sports teams, seasons, and the word password itself. Random letters and numbers are best but hard to remember.
A password manager can help but those are often still under attack. Unless you understand how to set up a password manager on a private network you might want to consider simply writing critical usernames and passwords in a book that is not easily accessed by other people. Don’t store it in your desk drawer at work, on a sticky note, on your phone, or in a safe with a key hanging on the wall.
All that sounds so complicated right? So here’s how you get around that.
Make sure all your vendors support MFA. Use a Yubikey. Then your passwords don’t matter as much. You still want a reasonably secure password, but you give each person a separate login to any application and they use a Yubikey to login. (They work on phones too.)
That’s really a much better solution. If your vendors don’t support MFA via Yubikeys, consider making it a requirement to implement it as part of your contracts going forward.
Want a more detailed security assessment of your environment? Consider hiring 2nd Sight Lab for a vulnerability scan or penetration test.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
