Why It’s Hard To Create Firewall Rules for Google Update Traffic
Same IP addresses for Google Updates and Google Ads?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Google Security | Network Security | Data Breaches
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In my last post on the topic of monitoring your home network and computers for problems I posted about some malicious traffic I noticed on my network and how I inspected my Mac for malware (or should I say, evidence of malware).
Related to that, I was having some problems connecting to Google’s update service. I thought I had allowed the domain through my firewall rules. Where he’s why that’s not going to work.
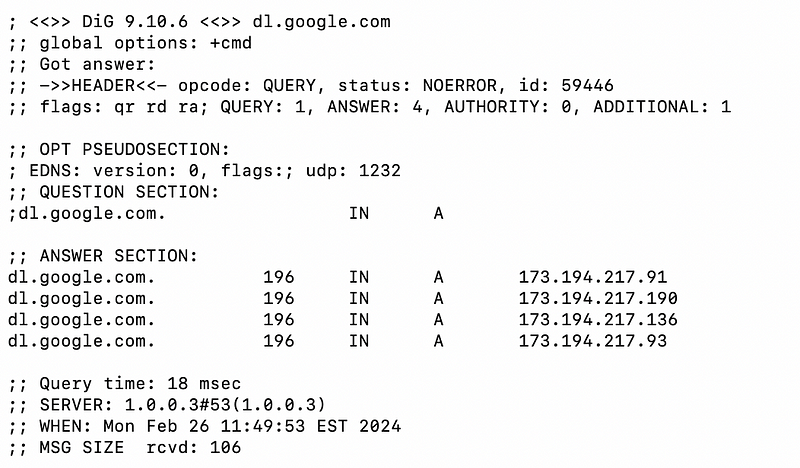
Dig dl.google.com
Dig ads.google.com
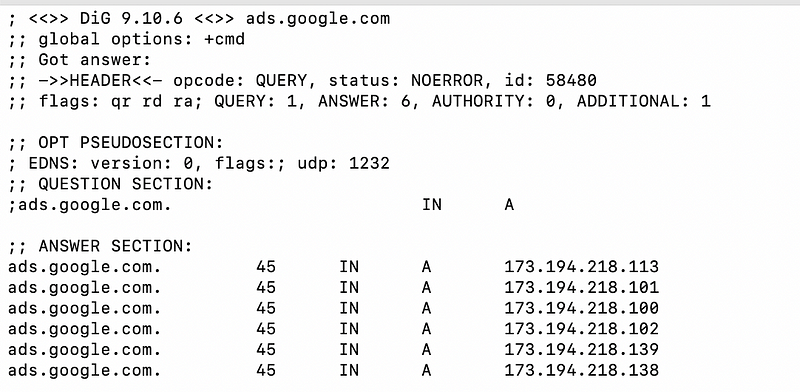
Depending on which Google IP addresses you query at any particular time, you mights see that completely different services resolve to a similar — or in some cases the exact same — IP ranges.
In the above example, the two IP ranges are somewhat different, however, these particular IP addresses are more similar:
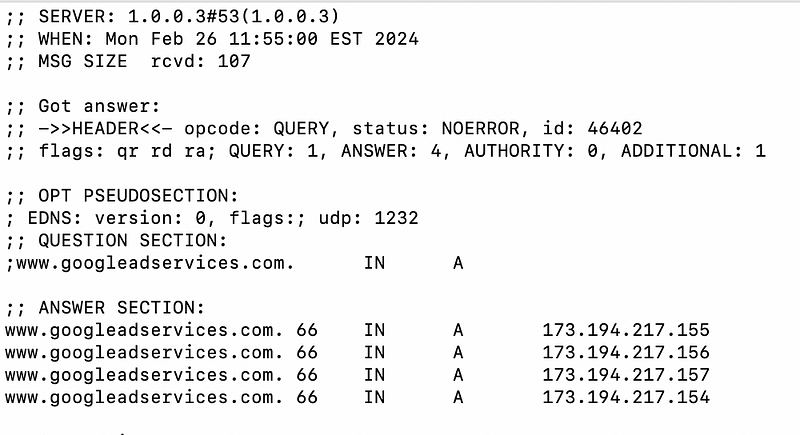
And in fact yesterday, something I cannot reproduce now on a different. machine, the IP addresses for the ad service was resolving to the exact same IP addresses that I needed to get to in order to get a Google update. Hmm?
So what was going on there? Not sure exactly but something to take a look at on your network. Was something compromised or is this Google’s way of saying, if you want to use our browser you have to look at our ads? Because the browser is free and yes, Google does need to make some money. Perhaps they should off an ad-free browsing experience for an additional cost if that was the objective. But now I’m not seeing that same behavior.
It would be great if Google published the IP range from which you should be getting updates for their various services.
If you know something about Kubernetes it’s easy to imagine why this is happening. Google has been known to be excellent on squeezing every last drop out of their computer resources — but sometimes that comes at the cost of security. Although they seem to be superior in some ways at processing large amounts of data due to their ability to scan and process — all the Internet — their optimization focused designs sometimes lack an understanding of how that can cause a security problem.
When Kubernetes came out my team wanted to use it and I looked at the design and said — show me how you are going to segregate the network traffic of different services so lets say, only the billing service can connect to the billing database? You couldn’t. At least not with a single Kubernetes cluster. Because you set up this Kubernetes service to handle all your containers and they all shared the same hardware and you couldn’t distiguish between different nodes via networking. You also couldn’t handle TLS traffic or monitor individual nodes. Now you can through the use of tacked on sidecars.
Security is best when it’s baked into the underlying design, not added after the fact. Kubernetes now has better security options, but what if somehow the servers got miconfigured (if not done intentionally) and the containers for updates were on the same hardware and networks as the servers for ads?
Or, was something compromised. Was I being directed to ad servers for updates due to some malware somewhere in the network or on my system? I don’t really know at this point. But this is something to be aware of and monitor in relation to Google software updates — or any software updates for that matter. Make sure they are coming from the proper network and understand what else is on that network that might send you a malicious update.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
