Welcome to AWS Identity Center
ACM.10 Successor to AWS SSO (Single Sign On)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | Cloud Security Architecture | IAM
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I wrote about AWS KMS keys and how they can help secure resources in your account. The great thing about encryption on AWS is that it uses the concept of additional authentication data (AAD) to combine identity and encryption for greater protection using layered security controls.
Well, with each step along the way of writing this series on using AWS Batch to automate security metrics, the next post I thought I was going to write eludes me. I thought I was going to create a KMS key next. In order to create a key policy I needed identities to which I could grant access in the key policy, so first I would need to create some users. But then I had explain why I’m opting not to use the Yubico CLI to obtain MFA tokens (next and already written).
The next step after that would be to create a user. However, I recall there was some reason why I could not use an AWS SSO user assuming a role with an external identity and MFA. I was trying to remember what that was when I realized that AWS SSO has a successor: AWS IAM Identity Center.
This was introduced….yesterday:
AWS SSO vs. IAM
If you’ve followed me on Twitter for any length of time you may have seen that I was not fond of AWS SSO. I tried to get used to it. I tried to like it. I couldn’t. Sorry to whomever designed it but the user interface simply did not work for a security professional and was completely illogical to me. I have submitted feedback comments in the console at moments of frustration but it never changed and I never expected it to…maybe it finally has.
I do use AWS SSO in one account but not in another. At times it simply doesn’t work for my needs so I have to create an AWS IAM user, and I am reminded in those moments why I like AWS IAM so much better. SSO is nice in that it consolidates users across your organization and provides access to multiple accounts, but so many other things are lacking.
So I guess now we’ll go exploring this change instead of jumping into creating a new user in case the changes to AWS SSO justify a change to my potential architecture and design.
Automated creation of users with AWS Identity Center
First question. How can I automate creation of users with AWS Identity Center? Perusing the documentation shows how to create a user manually but not programmatically.
When I log into the AWS console and enable the AWS Identity Center I see all my AWS SSO users, so I presume that the same mechanisms used to create AWS SSO users programmatically will work with AWS Identity Center.
It does look like the previous CloudFormation documentation for AWS SSO has been renamed AWS Identity Center:
Great.
Can I use an AWS Identity Center User with the AWS CLI?
It looks like we can configure the AWS CLI to use an AWS IAM Identity Center User:
However, it looks like these methods require use of a web browser. Not really a fan of that and not going to work with the type of MFA solution I’m considering for batch jobs. This alone has ruled out my use of this type of user for what I’m planning to do.
It also requires exposure of the URL to my SSO login portal in a configuration file. I don’t really like that either. I don’t see any configuration options here for MFA or an external ID. Maybe they exist but are not documented. Perhaps the browser is considered a form of MFA but I’m not sure it is actually an out of band MFA option. I wrote about that in my book. I’ll need to think about that a bit more but for now this option doesn’t meet my current needs.
Multiple Yubikeys
One thing I noticed while look at AWS SSO is that it finally supports multiple Yubikeys. Yay! This is a huge win. I just talked about that missing functionality at the AWS Summit in Atlanta. Now you can have a Yubikey that you use on a daily basis and one stored away in a safe in case you lose or break your primary key. You won’t have to call AWS to resolve the issue if you plan ahead.
Permission Sets
AWS Identity Center carries over the concept of Permissions Sets. Did they fix any of the problems I submitted with those permissions sets? Not completely, if at all. There may be less clicks to get to some of the information which is helpful.
When you click on a User, you can’t see the permissions that user has like you can in IAM. You can’t click over to a policy that applies to that user that you want to modify. You can see what groups they are in. Ok so click on a group. You can’t see what permissions groups have either. Maybe they are still working on that. Fingers crossed.
Alright navigate over to permissions sets. Click on one of those. You can see the permissions in a permission set. Great. Can you see the users who have those permissions? No. Can you see the groups who have those permissions? No. You can see a list of accounts.
Accounts is really where you want to look, the way the UI is currently designed. Don’t even bother looking at users and groups when you are trying to evaluate permissions. Click on accounts.
What’s nice here is that the view is aligned with the OUs available in AWS Control Tower and AWS Organizations. I still contend that AWS Control Tower and Organizations need to merge. Maybe that’s all going into this new AWS Identity Center, and billing tags or categories will be separated from OUs as the boundaries for those two things don’t always align.
When you click on an account, you can see a list of the permission sets (what users can do) and who in that account is assigned to each permission set. It’s better than nothing but it doesn’t give you a global view of the permissions a user or group has across the entire organization.
This is the question I want to answer at a glance:
What permissions does Bob have across my entire AWS organization? Which accounts can he access and what can he do in each account?You’ll probably need to write programmatic queries to answer questions like that for the moment. Hopefully more improvements are on the way.
I’d also like to be able to drill down from a user or group into their assigned permissions and modify them like you can with AWS IAM.
Do Not Delete Me
Whenever I see the things named “Do Not Delete Me” created by AWS SSO and Control Tower it feels like a disaster waiting to happen.
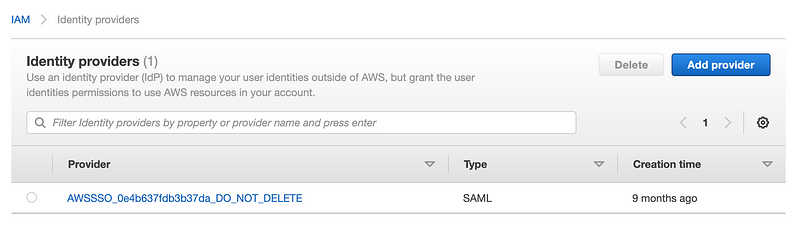
Perhaps these things should just be read only by default and you have to go to the console of the appropriate service to enable deletion. There, you get an explanation and a warning of why should not delete the related items.
No Access Advisor
AWS SSO lacks one of the most useful troubleshooting and policy building features in AWS IAM. The Access Advisor. Click on any user and see what policies and services they have accessed recently within their assigned permissions. This helps you remove things you don’t want or need in IAM policies.
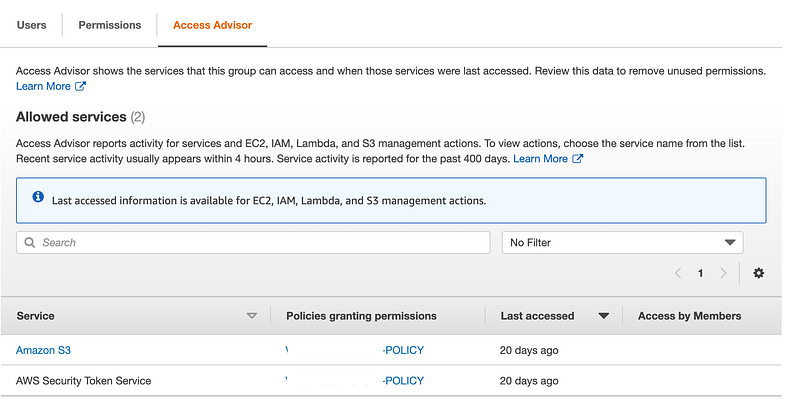
Unfortunately it has some limitations when using cross-account roles. Since the role is in another account the access advisor can’t see what the user did in the other account or report on it at this time. The new identity service doesn’t fix that problem or even include the Access Advisor. I hope it gets added.
Policy Creation Features and Reports
Some of the policy creation features and reports in AWS IAM were also missing in AWS SSO last time I checked. I hope all those things get consolidated into this new AWS Identity Center. That would be great.
Applications
It looks like Application permissions are added in AWS Identity Center similar to how this is set up in Azure. Was that there before? I don’t recall, even though I wrote a whole class on AWS SSO and Control Tower. I had to step away and do a full Azure course so sometimes things drop off and I have to revisit my notes. Basically you can grant users access via SAML to applications within your organization.
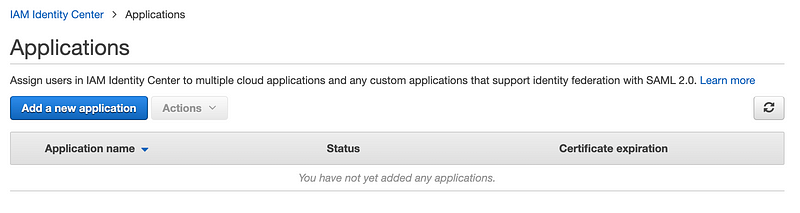
Choose your identity source
One of the first things you’ll see when you enable AWS Identity Center is this checklist:
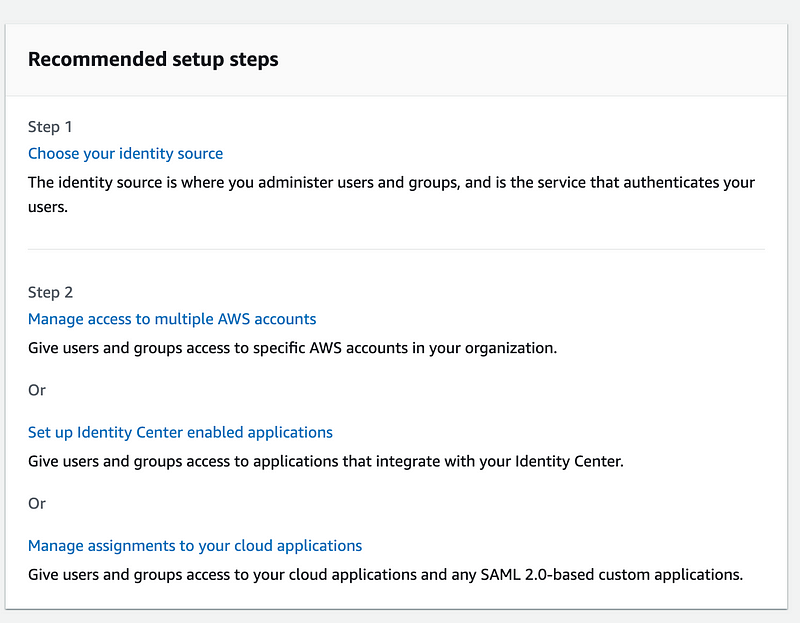
This is not new and something I’ve been meaning to test out. I wanted to add connection to an external identity provider to my class and already have that partially set up. So many ideas….so little time….
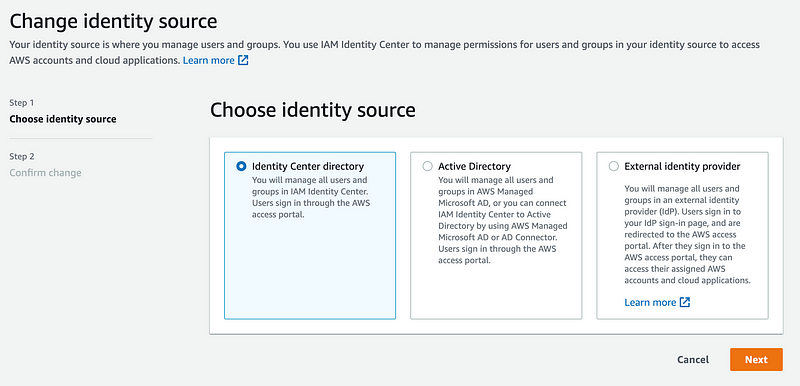
My idea was to see how hard it would be to use an external IDP for all my “clouds” but I ran into some issues with Azure. It took 4 weeks for them to admit there was a bug and by the time they had it fixed for me to test my Azure class was over and I had to complete some penetration tests. So…that idea is still on the back burner. I imagine connecting with AWS will be much easier but I haven’t tried it yet.
Automated Provisioning with a third-party IdP
You can use SCIM for automated provisioning with a third-party IdP.
That looks interesting, however since I’ve already determined that an AWS SSO user doesn’t seem like it will work out too well for the batch job idea I’m working on, I’ll tuck this information away for later use. Back to our batch jobs, and I’ll just use IAM and CloudFormation to create a user for my current needs. I’m sure someone at AWS with access to change internal systems could design a solution for what I’m trying to do better than the one I’m attempting to implement, but I have to work with what is available to me.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
