Security for Startups
Limited resources and new to security — where do I start?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Related Stories: MFA | Passwords
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
If you have a startup, you may feel intimidated by the thought of trying to secure your business. If you are not familiar with security, what are some of the most important things you can do to reduce the risk of a data breach? Even if you are familiar with cybersecurity, your time is limited and precious. Your organization is small, and you don’t have many resources to implement extensive security controls. Where should you start?
Here are a few things you can do to reduce the risk of a data breach. I rarely ever recommend specific products, but for startups, I do have a few recommendations below. I am not paid by any of these companies to endorse their products. These are not the only products you can use safely and securely. They are a few that I know will be decent choices for a small business with limited budget and resources.
#1. Get a security key
One of the most significant root causes for data breaches involves stolen or lost credentials used to take over accounts. At Google Next 2019, the company’s biggest conference of the year, a presenter talking about new Gmail features claimed that they had never seen a successful account takeover of users who employed a security key.

Security keys are a very effective form of multi-factor authentication (MFA). Different types of MFA exist, and the effectiveness depends in part on the kind of MFA you choose and how you implement it. It also depends on how the system you are logging into implements things on their side, as we learned in the recent Twitter breach. In general, security keys will immensely help limit account takeover as a source of an attack.
Different types of security keys exist, and companies may manufacture them in different countries. Try to understand where vendors create and test security products. Yubico is one of the companies that has been making security keys the longest. Their product, called Yubikeys, are manufactured in the U.S. and Sweden. Use online services that allow you to associate one of these keys with your account so someone cannot log into the account unless they have the key. Some services like Gmail will enable you to associate two keys. You can use one and put the second key in a safe place if you lose or damage your primary key.

If you can’t use a security key on a particular system, at a minimum use another type of multi-factor authentication such as your phone, an authenticator application, or a service that offers push notification. If you’re not familiar with those MFA options I cover them in my book mentioned later in this post.
#2. Set up permissions and access very carefully
A lot of companies give people full access to people helping them create systems and resources. Think about what might happen if you ever have a falling out with that person or the individual decides to leave your company. Will you still have access to the systems you had them set up for you? Will you be able to lock that person out of the accounts if you need to do so? What if malware compromises the person’s systems — what will it be able to access? Before granting access to any resource of any kind, understand the permissions you give and limit to what is required. It will take some additional time but will save you a headache in the long run.
One example would be people who set up Zoom calls without understanding the different options. That resulted in the infamous Zoom bombing attacks. Choosing a unique ID for each meeting and limiting the meeting to the people authorized to attend resolves that problem. Look for ways to restrict access to people and resources that require it.
Another example would be sharing documents using Microsoft Teams or Google Drive. You can limit access to specific people, or to anyone with the link, or open the resource up to the entire Internet. Don’t assume that just because someone doesn’t have the link, they won’t find it. Attackers can see what links people are visiting if they have access to the network traffic. These links may also end up in emails, get forwarded, or saved in logs. Use the more secure option of limiting the document share to specific people that must log in to view the document.
#3. Use the cloud. Carefully.
Using cloud systems can help small businesses leverage some built in security. The cloud providers add redundant storage, logging, and security alerts that would be very expensive for a small business to implement. Many small businesses do not have the staff or knowledge to architect systems securely. A cloud service will help by offloading part of the responsibility.
However, there are still aspects of cloud security you need to manage yourself. It’s all in the documentation. Read that documentation to understand the security controls for any service you use before you put sensitive data in that service. It takes time to read and understand the documentation and security controls. You don’t have to allow every aspect of every cloud service all at once. Take the time to understand and adequately secure each service you use as you add it to your system implementation. Most importantly, take action to prevent any data stored in the cloud from direct exposure to anyone on the Internet. If you cannot implement every security recommendation at once, start with that, and then use an iterative approach to improve your cloud configuration and system architectures.
Assess your vendors and read your contracts. Better yet, hire a lawyer to review contracts. Some cloud providers and online services do not have any better security than you do, and risks of a breach may increase because now you are exposing your data to more people. Read and understand your contracts and assess your vendors to make sure they are handling data appropriately. Understand costs, data privacy, and potential liability associated with your agreement. If the vendor does not manage the information securely, who is liable? What happens in the event of a data breach? How is the data backed up, and who has access to it?
#4. Email for startups
For startup email services, Gmail is a good option. I started my second company, Radical Software, in 1998 and incorporated in 1999. We helped companies build web and e-commerce applications. Back then, spam was rampant for reasons explained in Brian Kreb’s book, Spam Nation. In the years following, I tried several outsourced email solutions and spam-fighting products before landing on a service called Postini, which worked better than all the rest. Google bought that company to help fight spam, and the rest is history. I’ve been on Gmail since, and it works well for small businesses. It not only eliminates most spam but has additional monitoring features that will alert you to security problems.
For example, earlier this year, I received an alert about malware in an email message. Upon further inspection, the threat was benign. In another case, a security researcher shared malware with me that triggered an alert. It seems that Gmail is working pretty well! The only problem I have with it is when it blocks my security research, but I’d rather have that versus unwanted malware in my inbox.
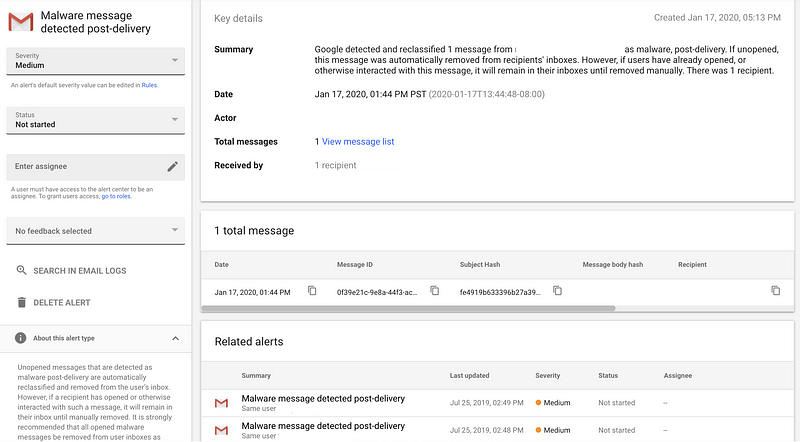
I tend to only check email in a browser and forgo a client like Microsoft Outlook. In the example above, if I downloaded the mail to my local machine, Google would not be able to remove the infected message. Be careful when you open emails. I open risky links and documents on a cloud computer or separate device from the one on which I do my banking or pentesting. I also have separate emails for different purposes. Check the options for storage and backups if you need to keep your emails for a certain length of time due to industry regulations or legal holds.
The video link I posted above goes into more detail on Gmail security features. As with any product, read and understand the security settings. Understand the logs available to you, and turn on alerts for suspicious or high-risk activities.
#4. Choosing a cloud provider to host applications you build
When it comes to choosing a cloud provider, you certainly can use AWS, Azure, or Google Cloud successfully. However, there are some things you should consider when selecting your cloud provider. At the time of this writing, these are some considerations, but be aware that the cloud changes often! Check with the cloud providers for the most up-to-date information if you read this a year from now.
AWS allows you to use almost any available security feature or automation capability for a low or no fee when starting. Nearly every security service has a free tier, with a few exceptions. AWS offers the ability to create robust networking, which may not concern you now but might when you are trying to become SOC 2 compliant, acquire investors, or monitor your network traffic for cyberattacks later. You can automate just about everything at no additional cost. If you do that, you will be able to create solid security policies free from human error. Automation of user and account creation, fine-grained security policies, and solid networking rules are reasons I use AWS to set up my pentesting and much of my class infrastructure.
On Azure, you have to commit to an enterprise license to get certain security features. For example, if you want to create custom IAM policies, you need an enterprise license. MFA is not free. If you’re going to use that Yubikey that I mentioned above for multiple users, you’ll need to pay extra. Automating user creation also requires an upgraded license. For some services, you’ll need to sift through several licensing options to find the one that offers all the security you need at a price you can afford. Azure works fine for a lot of use cases, and a lot of enterprises like it. Azure has good security, but for a startup business, the licensing model is not ideal. Additionally, different service tiers in Azure, such as free accounts will not receive the same level of performance as higher tiers. That can affect small startups as they get off the ground on a low budget.
Google Cloud Platform (GCP) is very user-friendly. I like to say it’s developer-friendly. One of the problems with this ease of use is that many of the “easy buttons” come with insecure defaults. If you are hosting sensitive data, you’ll need to be extra careful to ensure you do not choose default options that leave administrative services open to attack or give a serverless function very high privileges in your account. Some traditional security constructs are challenging to implement. When I started teaching my cloud security class, Google had fewer security features overall than the other two cloud providers, but they are very quickly moving towards feature parity. They were the first cloud to have encryption by default.
#5. Learn basic cybersecurity
Learn more about cybersecurity before you implement your systems, if possible, and definitely before you have to deal with a data breach. I faced a data breach many years ago, and it is one of the factors that propelled me to focus on security. I struggled with how to resolve the issues because my hosting provider was not very helpful. Eventually, I fixed the problem. At the time, the challenge was that I didn’t know anyone who worked in cybersecurity, and limited resources on cybersecurity existed. The classes I found cost thousands of dollars. You can now learn fundamental cybersecurity in many different ways at different price points. My book on Cybersecurity for Executives in the Age of Cloud is one of those options. It’s a very cost-effective choice for executives and those new to cybersecurity working at startups.
As part of cybersecurity basics, understand how to view and decipher high-level network logs. That is one of the most powerful things you can do to understand if your accounts and systems are compromised. Learn how to create appropriate firewall rules. These steps will not stop every advanced attack, but a well-architected network can resolve many of the very remedial problems that cause security breaches. I explain networking basics in my book and have a full day on cloud networking in my cloud security class designed for organizations moving to the cloud. I discovered my first breach with the help of network analysis even though I knew very little about cybersecurity.
#6. Get a security assessment or penetration test
One of the things you can do to see what security gaps exist in your environment is to get a security assessment or penetration test. Have a trusted security professional review your systems to help you find security problems. A security assessment or penetration test from a qualified professional will list the findings and provide resources to help you reproduce and fix the issues. That is one of the fastest ways to get an overview of your security. You will learn a lot in the process if the report explains the findings in a way that you can understand and use to reduce cybersecurity risk.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2020
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
