Require MFA for Git Commands With AWS CodeCommit
ACM.265 Leveraging short term, rotating credentials via an AWS Role Profile, no git credentials, and git-remote-codecommit
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Git Security | Application Security | Secure Code | AWS Security | MFA
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I explained how to check the version of Python and Pip you get when you run the python command and how to change that if needed.
I showed you how to do that because you might need to update your version of python or pip to use the method of leveraging git with AWS CodeCommit I’m going to show you in this post.
I already showed you how you can create credentials for a user in the AWS console and use those to access your CodeCommit repository with standard git commands. In this post, I’ll show you how to use as a role assumed via an AWS CLI profile.
There are some benefits to this method. For one thing, you can enforce MFA in your AWS policies, and for another you don’t have to manage yet another set of credentials. This method leverages your AWS CLI credentials instead and creates short term credentials that work with AWS CodeCommit.
The other thing is that this method will work with a third-party identity provider and cross-account access to Git repositories. You can’t use git credentials created in the IAM dashboard for a user for cross-account access.
Using the AWS CLI
You can use the AWS CLI with your developer credentials that you already have set up. Add the appropriate permissions to your user or preferably a role and use the AWS-specific git commands listed on this page.
That’s great but you probably don’t want to learn a whole new set of commands right? There’s another option.
Using the AWS CLI with a role and git-remote-codecommit
You can run git commands by assuming an AWS role with short term credentials the way I’ve shown you in other posts throughout this series:
The way it is explained in the AWS documentation seems a exceedingly verbose. It’s really quite simple.
You must have the following installed:
- the AWS CLI
- Python
- Pip
- git-remote-commit — a python tool from AWS that makes this work
You’ll need specific versions of the AWS CLI, python, and pip. When I initially tried to install git-remote-commit it didn’t work so check out this post and make sure you have the most up to date versions from AWS.
Then install git-remote-commit like this:
pip install git-remote-codecommitYou can review the code for git-remote-codecommit here:
Create an AWS Role with CodeCommit permissions and a trust policy that specifies the git user that can assume the role
The role you assume need to have permission to access Code Commit and the repository you are trying to access:
In my case, I’ve been using the web admin user. However, the role I’m using is a cross-account role to access the account where I deploy website. I need to give this user permission to access the repository that I deployed in the Sandbox account.
For simplicity, and only because this is a simple test, not my long term solution, I manually created a test role and assigned code commit permissions to show you how this will work. I am doing this manually because I am going to delete it all after this post as this is not my long term solution. I’m just demonstrating how this works.
Create a role with a custom trust policy.
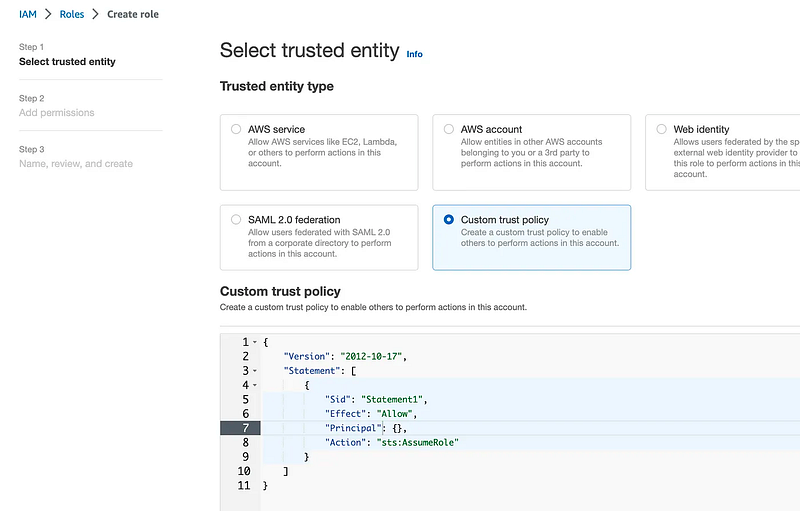
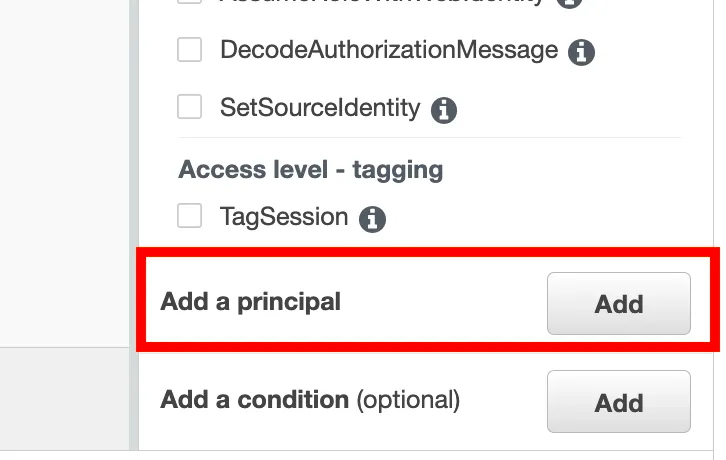
Scroll down. Click Add a principal.
Choose type user.
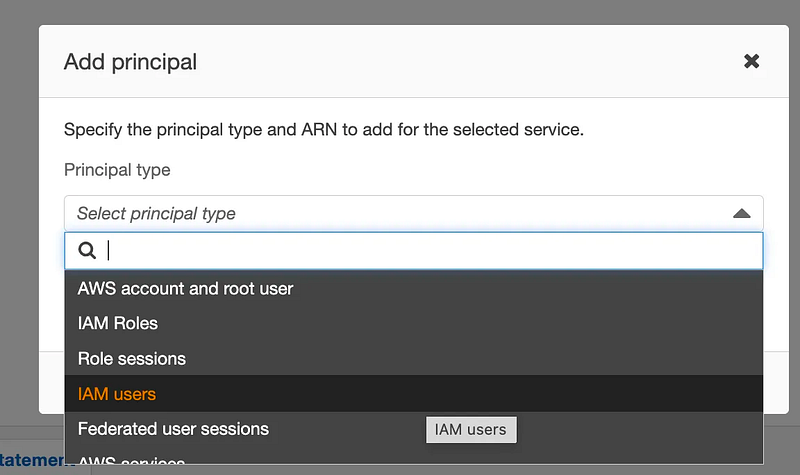
Enter the user ARN, which you can copy off the user profile page or fill in the account number and user name in place of the curly braces below.
Add a condition. Choose MultiFactorAuthPresent.
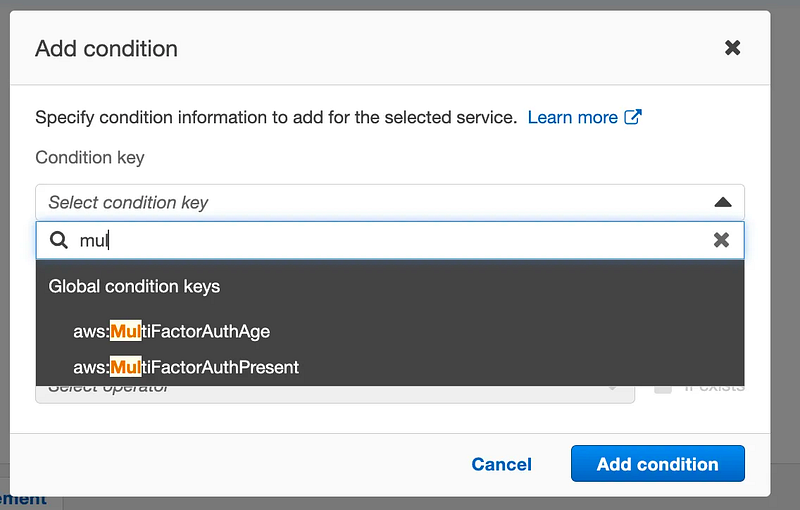
For qualifier, choose all values.
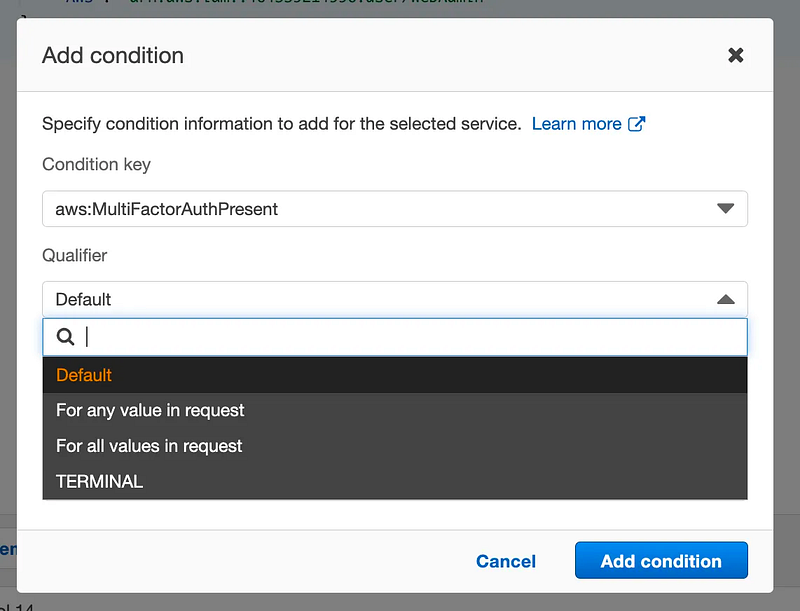
I have no idea what “TERMINAL” means in this list and cannot find any documentation on it.
For Operator enter “Bool”. For value enter “true”. Click Add Condition.
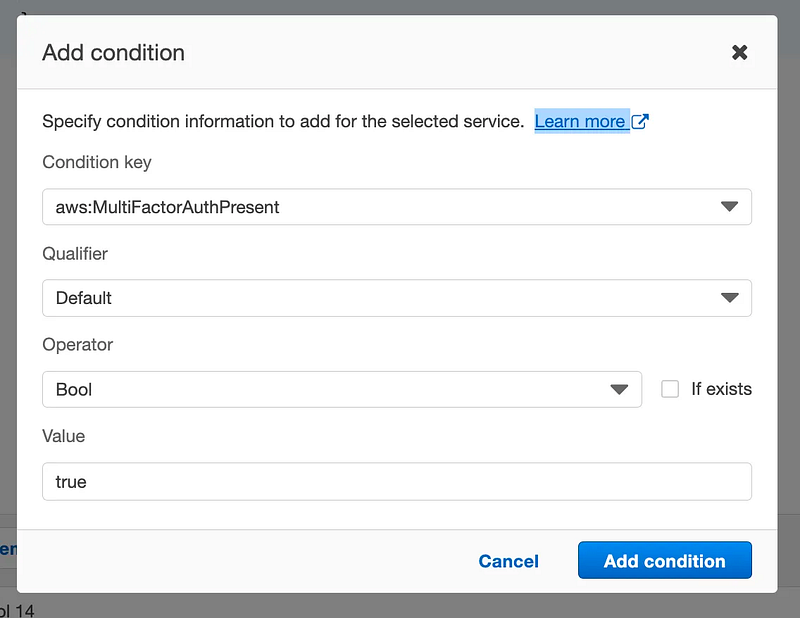
Click Next. Click Create Policy on the top right.
Search for CodeCommit. Click on CodeCommit.
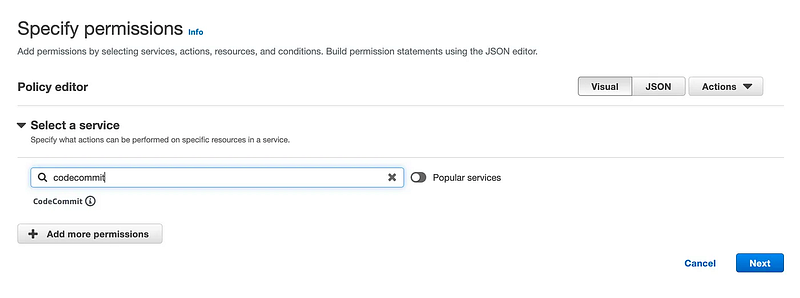
I selected all read and list permissions and the following two write permissions:
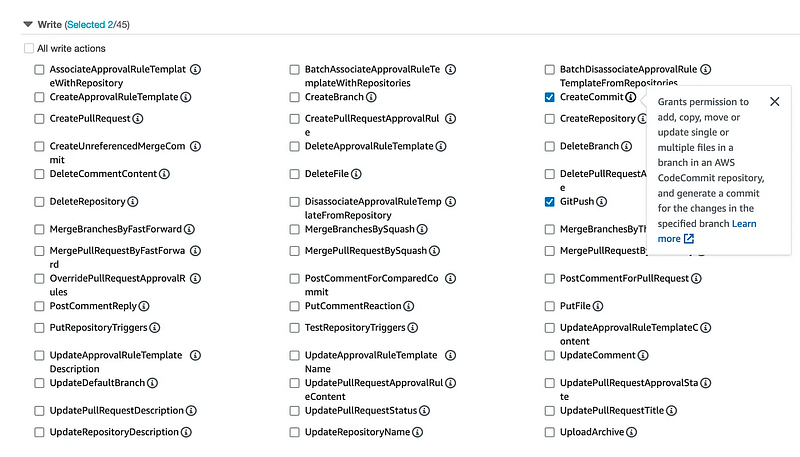
You can specify which repositories a role can act on:
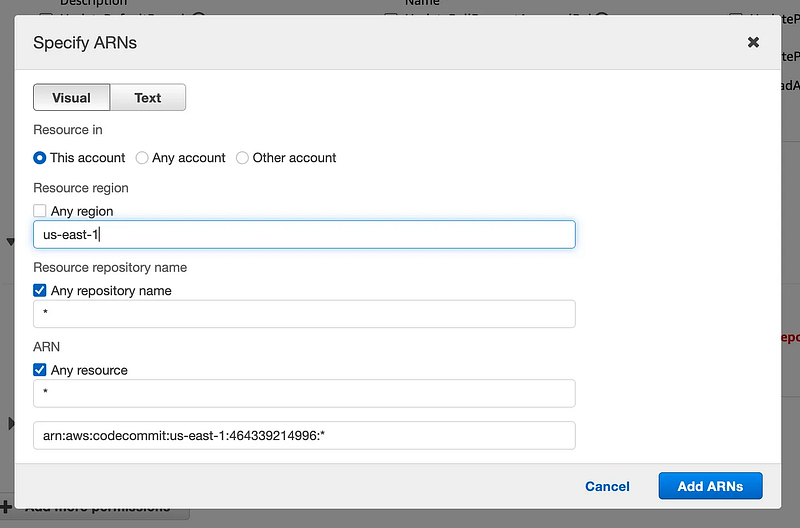
Remember that I added the environment as a prefix to the repository name, so I could limit access like this:
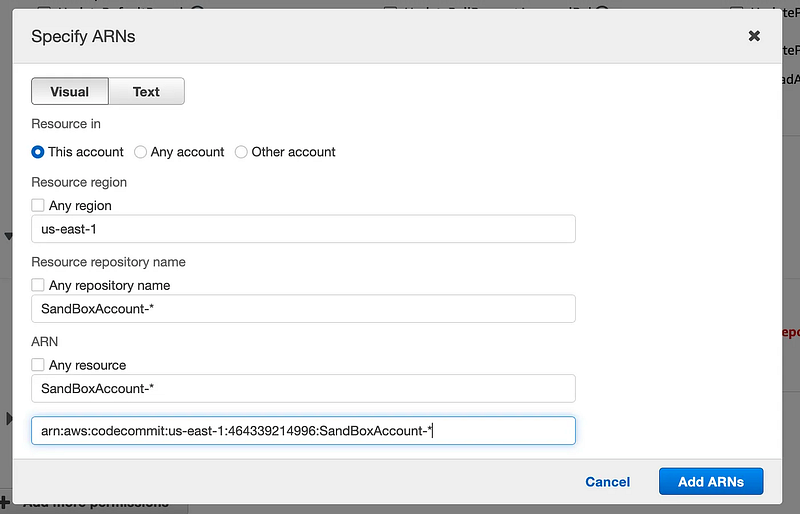
I could also give users access to only their own repository by adding the username as a prefix.

As you can probably tell this method of creating policies is both more complicated and much more flexible than the GitHub limited checkboxes for defining permissions I showed you in an earlier post.
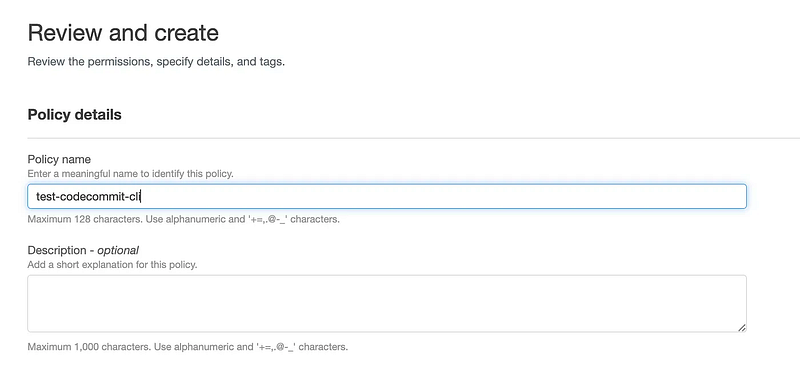
Give your policy a name and click Create Policy.
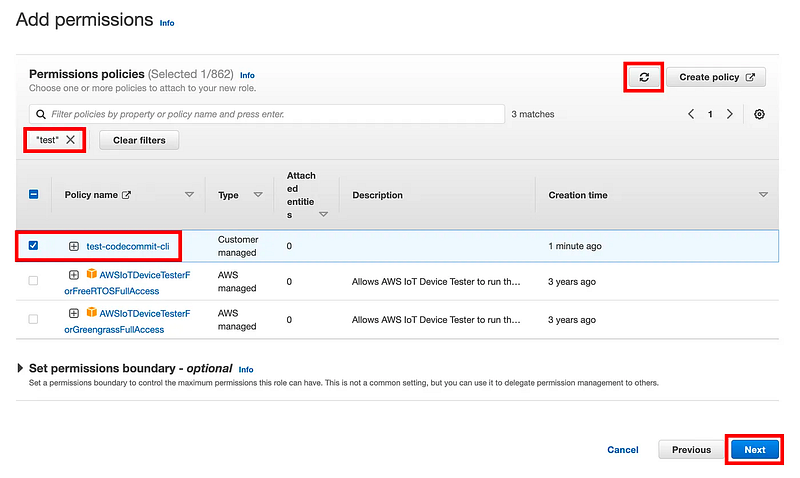
Back on the page where you were creating the new role, click the refresh button. Search for the name of your policy. Check the box next to it. Click Next.
Name your role and click Create Role.
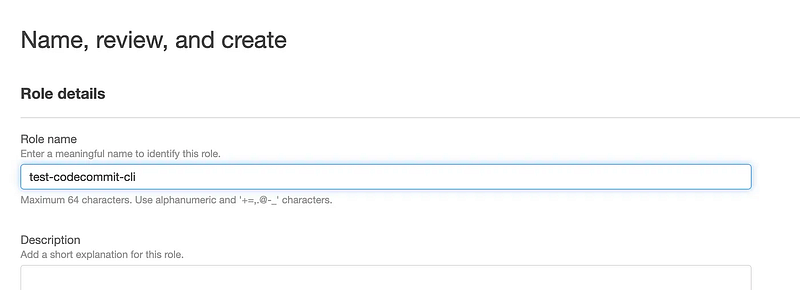
An AWS CLI profile that can assume the role
Configure an AWS role profile as I’ve shown you how to do already for short term credentials, but will provide specific instructions in this post:
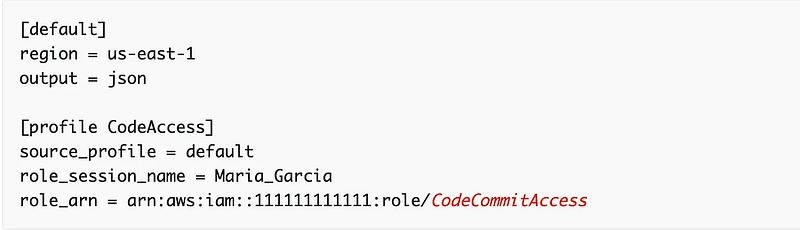
In my case I have credentials associated with this CLI profile: WebAdmin. So I’m going to replace “default” in the profile above with WebAdmin.
I added those credentials originally by running this command:
aws configure --profile WebAdmin#enter your aws access key and secret key when promptedMy new profile will set the source_profile to WebAdmin.
The ARN will be the ARN for the role we just created above.
The session name will be the name of the user assuming the role.
Now for my initial test I’m going to leave off the MFA ARN.
arn="your arn here"
source_profile="WebAdmin"
session_name="WebAdmin"
region="region where repository is located"aws configure set source_profile $source_profile --profile gittest
aws configure set role_session_name $session_name --profile gittest
aws configure set role_arn $arn --profile gittest
aws configure set region $region --profile gittestNow you can attempt to run git commands. The format of the command is as follows:
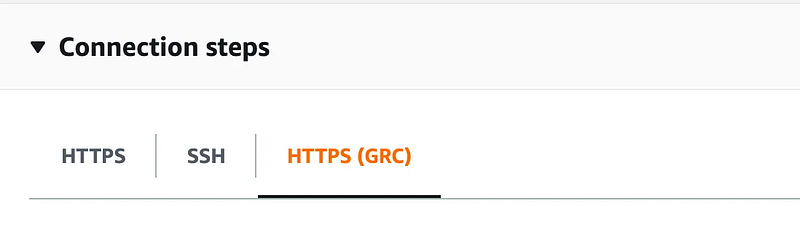
git clone codecommit://profile@RepositoryNameYou can get the clone URL off the CodeCommit dashboard for your repository under the HTTPS (GRC) tab:
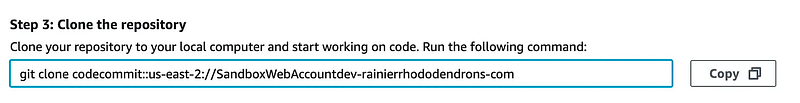
Scroll down to step 3:
Note, however, that I am not using the default profile. If I try to run that command I get this error:
The following profile does not have credentials configured: default. You must configure the access key and secret key for the profile. For more information, see Configure an AWS CLI Profile in the AWS CLI User Guide.

I need to add my profile name into the command like this:
git clone codecommit::us-east-2://gittest@SandboxWebAccountdev-rainierrhododendrons-comAs expected, that doesn’t work but the error messages doesn’t tell us exactly why:
botocore.exceptions.ClientError: An error occurred (AccessDenied) when calling the AssumeRole operation: User: arn:aws:iam::xxxxxx:user/WebAdmin is not authorized to perform: sts:AssumeRole on resource: arn:aws:iam::xxxxxx:role/test-codecommit-cli
Add the MFA ARN to the configuration.
aws configure set mfa_serial [your mfa arn] --profile gittestRemember you can get your MFA ARN from your user security information on the IAM dashboard, and I am using a virtual MFA device for command line operations.
Run the command again. Enter MFA credentials when prompted.
And…it works.
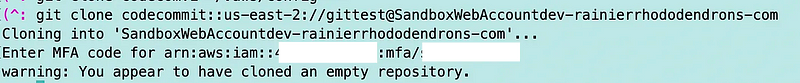
So as you can see if we use this option for credentials, we can enforce MFA.
The one caveat is that I have not reverse engineered git-remote-codecommit. Somehow that software is translating the role temporary credentials to git credentials. It may be somehow possible to bypass the AWS side of things but hopefully not. It seems like the user would have to authenticate to AWS and the connection to AWS CodeCommit is behind the scenes within AWS that the user does not have access to — but I have not looked into that.
It seems like, with this option, you can enforce MFA.
Now onto the rest of my proposed deployment solution to see if I can make it work as I envision.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
