Refactoring Existing Code to Use IAM Naming Conventions: Part 3
ACM.44 Ensure group names and policy names are consistent
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: IAM | AWS Security | Application Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In my last post I explained how to create a reusable template and functions to create IAM users.
We can use that same idea to create a reusable function to deploy a group since the only thing I really need to vary in my group template is the name.
I can start with a function to deploy a group.
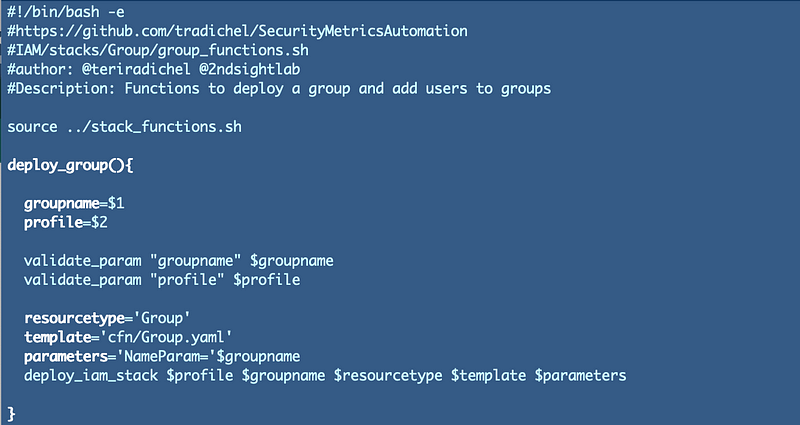
I can also create a similar function for my group policies with the name of the policy template file matching the name of the policy:
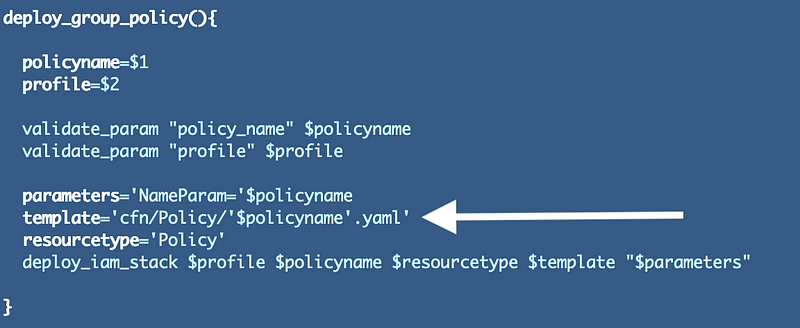
I have the three policy templates in the Policy subdirectory of my Groups/cfn folder:

Here’s the nifty thing. If I always name my CloudFormation policy templates consistently I can easily deploy the policy and the group with a couple extra lines of code. I can calculate the group policy template file name using the group name and deploy it from within the create_group function:

So if my group name is IAMAdmins, then my policy file name will be IAMAdminsGroupPolicy.yaml. I’m not creating a generic policy file because policies are one of the most critical aspects of CloudSecurity and likely each of these will be unique. I add Group to every policy name so I know the policy is associated with a group when looking it up in my list of policies in the AWS console or in the list of CloudFormation stacks.
I decided to keep my group policies in my group folder and this code will prevent group policies from being applied to some other resource — if this is the only code we use to deploy groups and policies. That is another example of how a fully automated environment can help.
Now my deployment script is pretty simple:
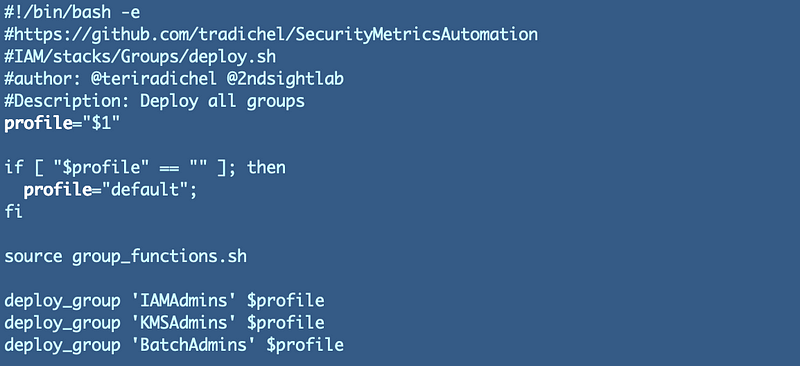
Now I can add new groups very quickly and when I want to find them in the CloudFormation console I can simply search on ‘IAM-Group’.
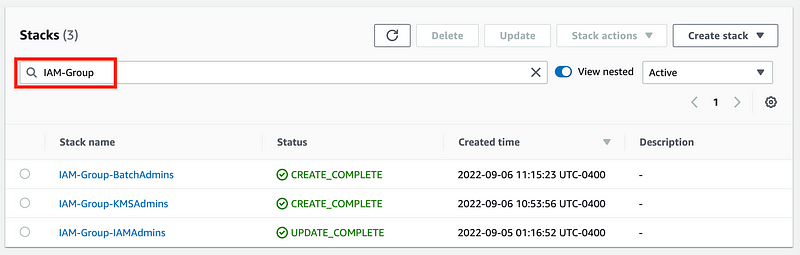
I can easily find policies for groups:
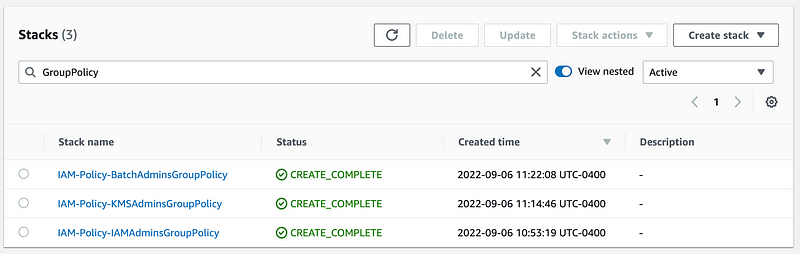
I can find all my IAM administrator templates (though the username would probably match an actual user in a production environment).
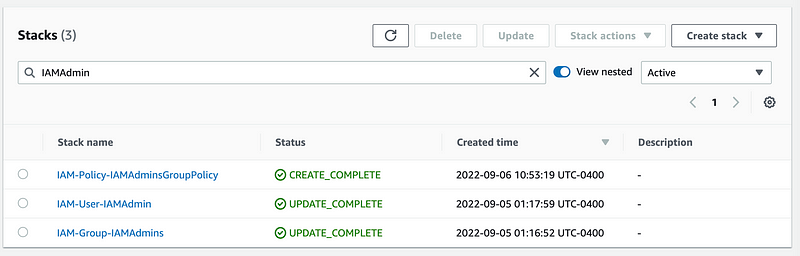
Next I can create a generic function to add a user to a group:

In order to test multiple users I’ve added one more user called IAMAdmin2 so I can test adding multiple users to a group. Refer to this post where I add users with similar common functions.
I just added one line to IAM/stacks/Users/deploy.sh:
deploy_user "IAMAdmin2" $profileNow I can test adding two users to a group in my deploy script:
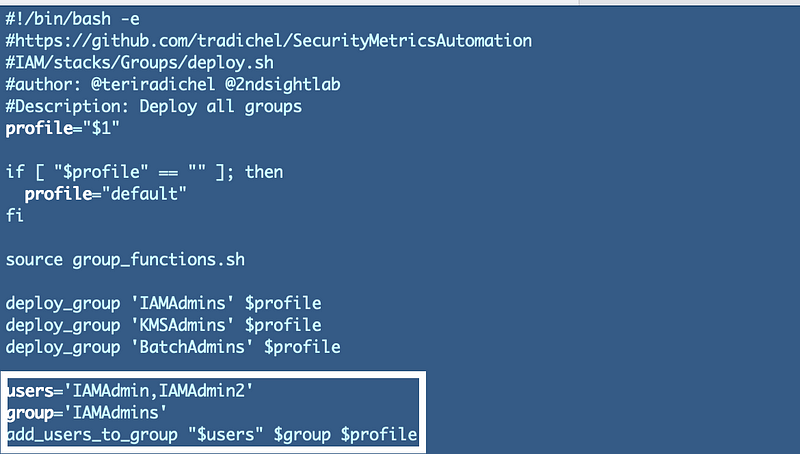
Check to see that your group has the associated users after creating this stack:
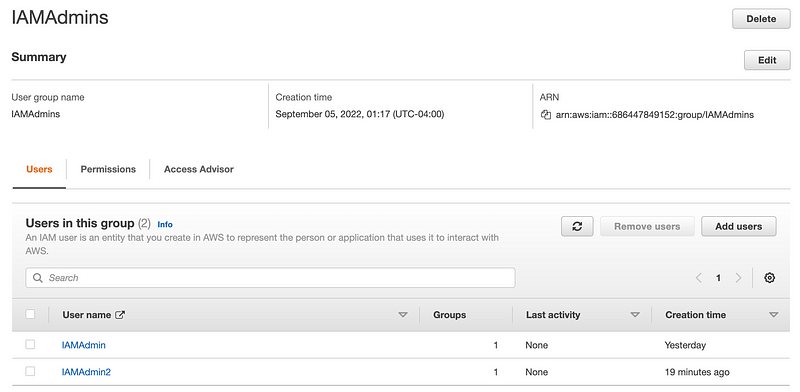
A few caveats about the above deployment script:
Cost
CloudFormation documentation specifies the following for costs:
AWS CloudFormation offers an easy and consistent way to model, provision, and manage a collection of related AWS and third-party resources by treating infrastructure as code. You only pay for what you use, with no minimum fees and no required upfront commitments. When using registry extensions with CloudFormation, you incur charges per handler operation. Handler operations are: CREATE, UPDATE, DELETE, READ, or LIST actions on a resource type and CREATE, UPDATE or DELETE actions for a Hook type. For more information about handler operations and resource providers, please visit the CloudFormation documentation.
This is not exactly clear. What does “When using registry extensions” mean? Well first we can check to see what the CloudForamtion registry is…
The CloudFormation registry lets you manage extensions, both public and private
Are we using an extension here? Is CloudFormation free if we don’t use an extension?
Here’s another item for the #AWSWishList ~ make this documentation clearer.
I don’t believe I’m using extensions and CloudFormation used to be free. The easiest way for me to answer this question is to look at my billing dashboard to see if I’ve been charged anything for CloudFormation in this account. I can confirm that for what I’m doing so far in this repository I am not getting charged any CloudFormation fees. I’ve been using this account and CloudFormation in it for quite some time. In the past, CloudFormation was free, I was just checking to see if that changed.
If you are making use of some kind of extension in addition to what I’m doing here, you might not want to re-run all the stacks just to update one of them. I’m not sure if you would get charged for the execution if there are no updates. The documentation doesn’t say. In the past I’ve had issues with unclear AWS documentation that ended up costing a lot more than initial estimates in a spreadsheet. Hopefully the AWS Calculator would give you more accurate estimates, but it’s still always a good idea to do a proof of concept (POC) and look at your bill before rolling out anything at scale.
If I had pricing concerns and I discovered that I was charged for a call to a stack even when no updates were required, I would create a way to only deploy the specific resources I wanted to change.
Changes in parallel to CloudFormation templates and code
Same as with pricing, you may want to separate out each resource to have its own deployment script when you have a number of things in a repository being updated and you don’t want to deploy unfinished changes. I’m just setting up this repository for testing purposes and the only person in it right now is me. If you had a development team making a number of changes at once you’d likely want to beak up the deployment script.
A change to the validation function
Note that I changed the validation function in stack_functions.sh slightly to pass in the function name.

That way when I report an error I can pass back the function name that had the missing parameter value:

It’s always a good idea to make your error messages as specific as possible to help people quickly pinpoint the source of an error.
Next I added this line to my functions to get the current function name:
function=${FUNCNAME[0]}Then I pass the function name into the validate_param function.

Passing parameter values to a comma separated list parameter
One other thing that you should know is that when passing comma separated lists to CloudFormation stacks you need to make sure there is no space in the list or you will get an error.
So instead of this:
"IAMAdminUser, IAMAdminUser2"Pass in this:
"IAMAdminUser,IAMAdminUser2"Caveats Adding and Removing Users From Groups
I didn’t test removing the IAMAdmin2 user from the group here but I presume removing and redeploying would update the group. What happens if someone removes a user from the group outside the CloudFormation template? I presume redeploying will re-add the user to the group.
What if someone manually adds a user to the group. Is it affected by this stack that adds specific users to the group?
What if we want to output all the users added to the group and use that? Then we have to ensure that the only way the group can be updated is through this automation stack.
On to IAM Roles…
Alright! Now we can very easily create new users, groups, and group policies. We have one more resource to see if we can refactor — IAM Roles. Follow me or sign up for the email list to get that next post.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
