Prevent Azure Users from Creating Tenants (Maybe)
New button in Microsoft Azure blocks tenant creation across your Azure account. Or does it?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Azure Security | Multicloud Security | Data Breaches
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
While preparing for my next Azure class I was doing some research to make sure my slides were up to date and I noticed new functionality. You can block anyone in your organization from creating a new tenant in your Azure account.
In my classes, I cover what tenants are and when you might want to use one and why you might not. If you don’t create a new tenant for testing you might be introducing security risk. If you do create one when you shouldn’t your introducing complexity, cost, and the possibility that the Global Administrator or security professionals aren’t seeing all the resources in your Azure environment.
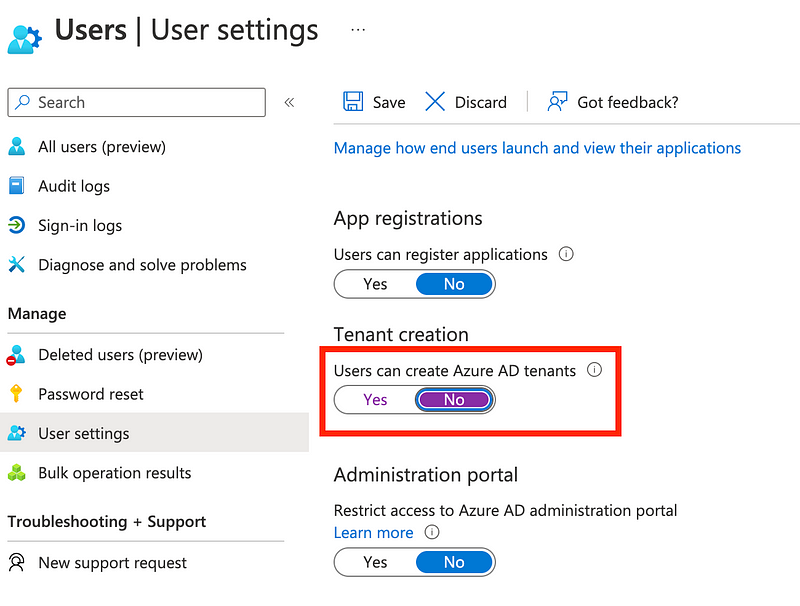
To get to this new screen navigate to to Azure Active Directory:
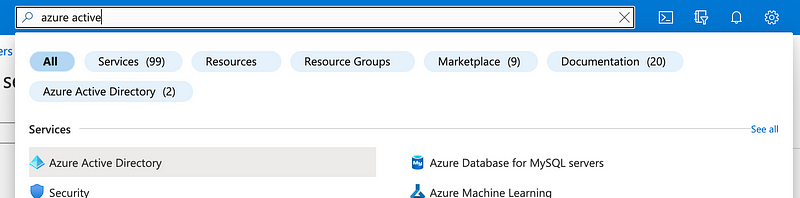
Click Users in the left menu.
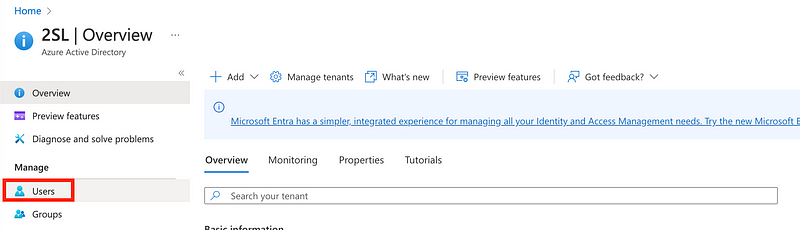
Click on User Settings in the left menu.
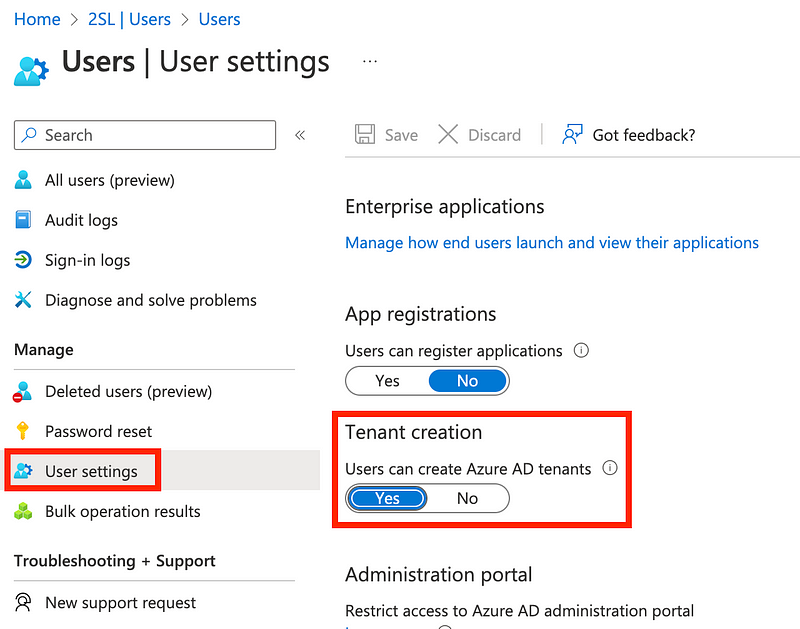
Now before we change that setting, I want to figure out what sort of access a user has by default in my account.
Create a new user with the default User settings (the User role):
Login with the new user in an incognito window (so you don’t have to log out of your administrative user). Navigate to Azure Active Directory and click on Manage tenants.
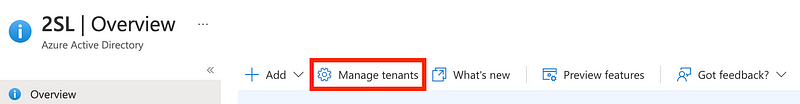
Click Create.
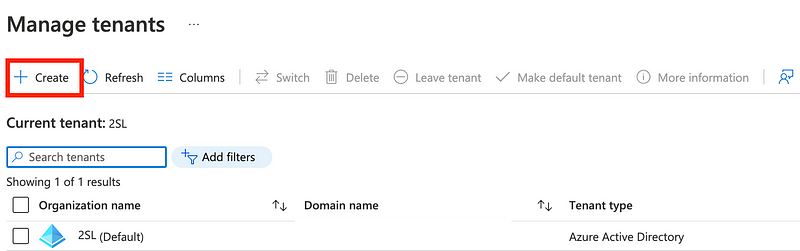
Click Next > Configuration.
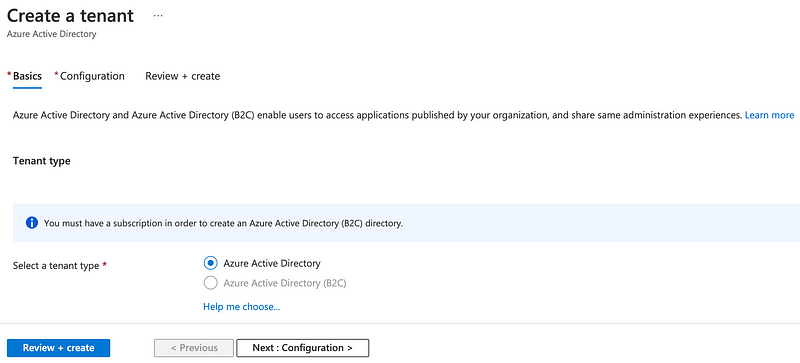
Click out the basic information. Click Next: Review + Create.
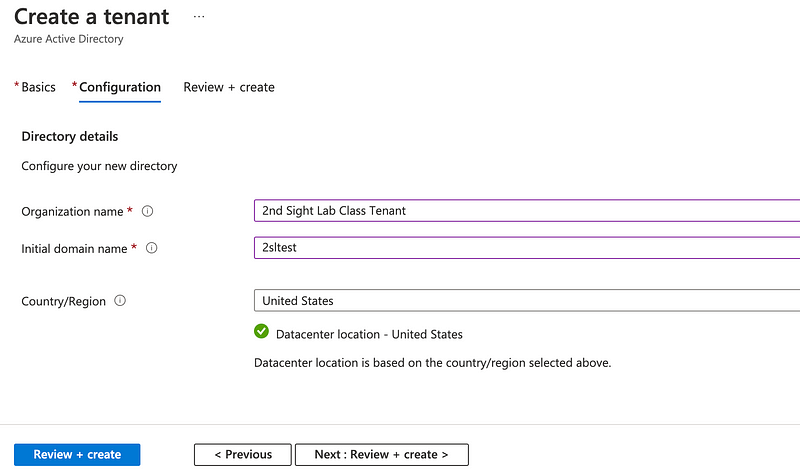
Click Create.
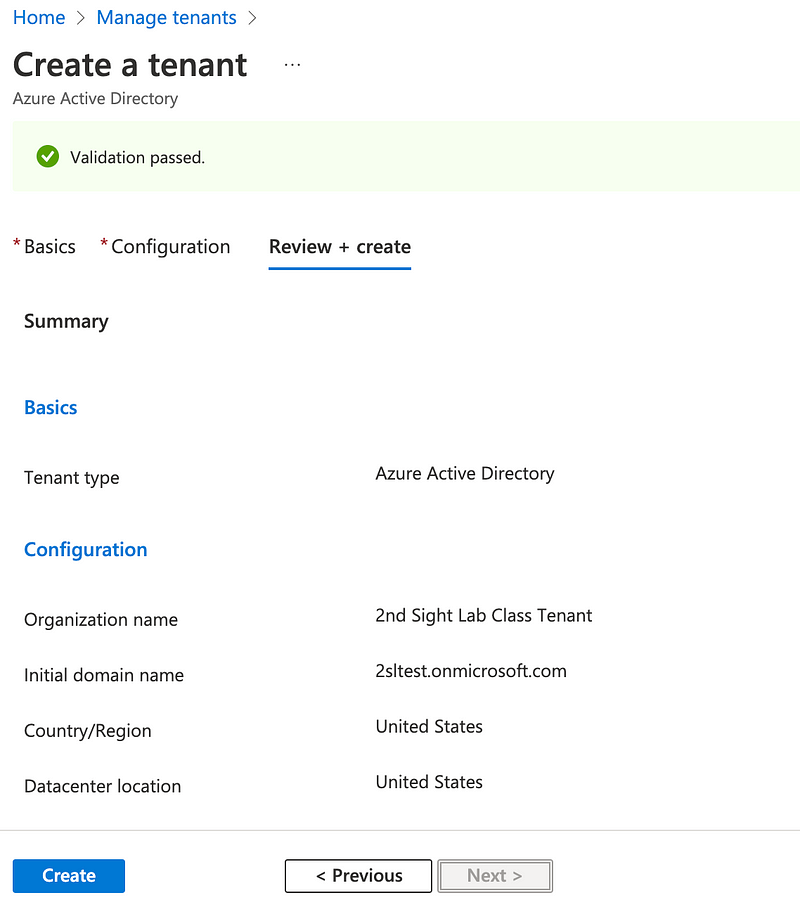
In my trial run, I got a captcha that consistently failed with a useless error message.
“Tenant creation failed. The creator of this fault did not specify a reason.”
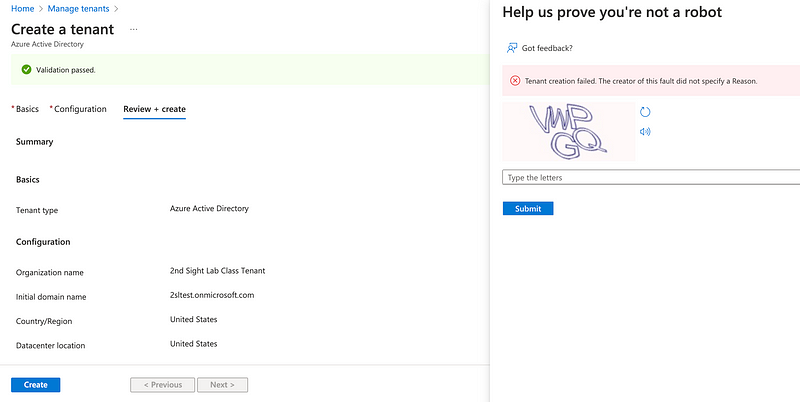
Not helpful at all.
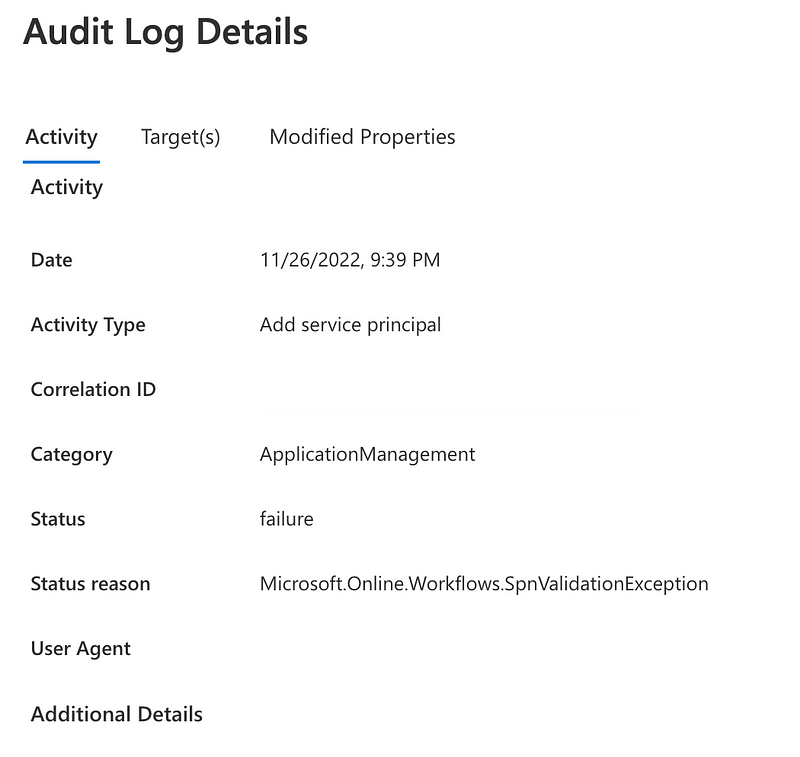
If I head over to Azure Active Directory and look at the Audit Logs, since this action is related to Azure AD, the only error I see is:
Microsoft.Online.Workflows.SpnValidationException
It’s trying to add a service principal. Since I have done absolutely nothing else in this account for a while I presume this is somehow related.
I check the Activity Logs just in case but there’s nothing there as I would expect. I haven’t been in this account for a bit. It asks me if I want to look at Log Analytics. Sure, why not. Well here I get this lovely bunch of errors:
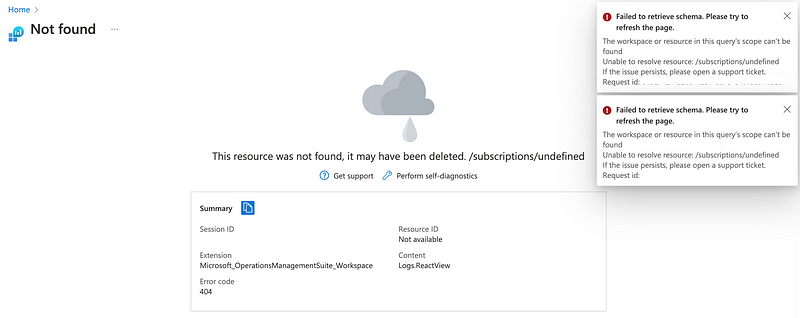
If anyone thought I was picking on AWS in my latest blog series when I pointed out issues — I’m wasn’t. These mystery error messages exist all over cloud providers and software in general.
Better testings leads to better outcomes:
Write thoughtful error messages:
Just to confirm that creating a tenant is possibly let’s do that from the Global Administrator account. Yes.
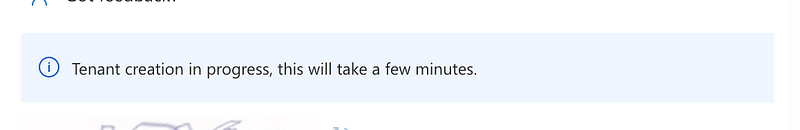
Someone on Twitter made a comment that any user can create a tenant adn will be blocked when toggling this function, but that does not appear to be true. At least not in the moment, in my account, when I took the steps I’m showing you.
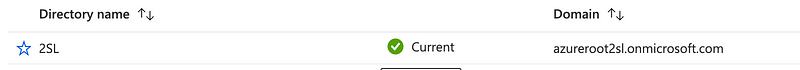
OK after that tenant got created I deleted it. Well, I thought I was going to delete it but I forgot to toggle one of the other “magic buttons” I talk about in class.
You have to give the Global Administrator permission in every tenant to manage Azure Active Directory resources in that tenant. It might seem logical that the Global Administrate would be…well…a global administrator. But not by default. The global admin might not even see all the tenants in an account unless you give it access.
In the Azure Active Directory properties for the new tenant toggle the button at the bottom that allows the global administrator to manage AAD resources and delete the new tenant.
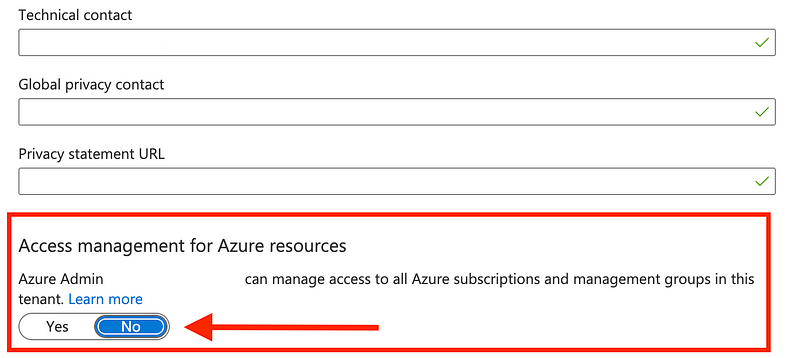
Toggle to yes. Click Save at the top.

Tangent: Why is the save button not at the bottom? One of these days I’m going to write a UI 101 blog post. Steps on a page should flow from start to finish in the same direction not jump all over the place.
Now you can click the link to delete the tenant at the top and proceed with deleting the tenant when it returns you to the prior page.
Verify the tenant got deleted by returning to Azure AD and checking the tenant list. Ah, nice. I get this lovely error.
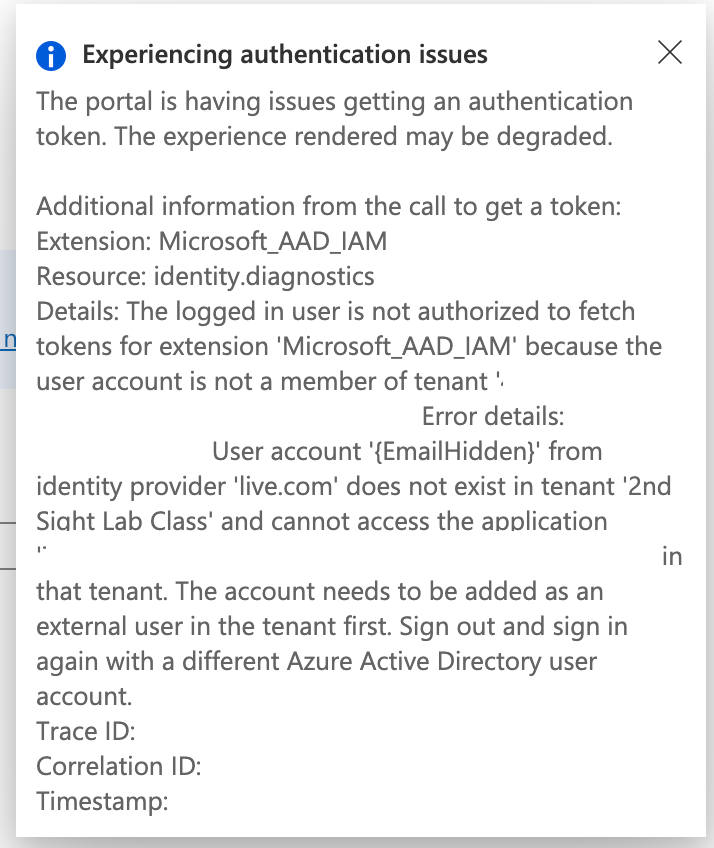
That’s the tenant I just deleted. I can did verify that the tenant no longer exists on the Manage Tenants screen.
Now, finally, back to what I was actually trying to show you.
Toggle the button for Users can create Azure AD tenants to No. Click Save.
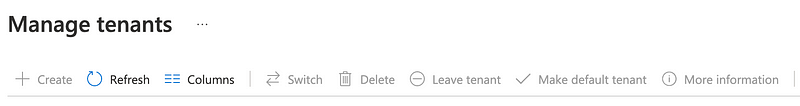
Now return to the Manage tenants screen. The Create button is greyed out.
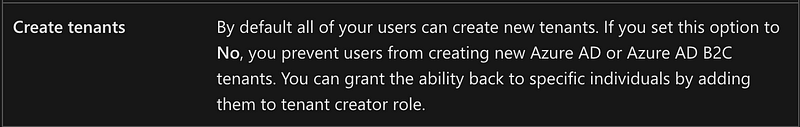
Note that you can still override this setting and grant users the ability to create new tenant to specific individuals by assigning them the tenant creator role.
Let’s give the admin user the Create tenants role.
Head over to Active Directory. Click on Users. Click on Azure role assignments in the left menu so we can see what roles the Global Administrator already has.
Well I get an error because there are no subscriptions. I deleted them all a while back. I would think that some role assignments would still show up here because I’m doing things.
Tangent: Oddly I click on another tab I had open and the tenant I had open still showed up even though it was supposedly deleted and I got more authentication errors. I switched back to my default tenant on the top right of the Azure portal and the deleted tenant disappeared from the list, as it should.
I added in a new test subscription in my default tenant. After doing that, I can once again see the the global user administration option. Seems like a bug. Click on the second role to see if the ability to create a tenant exists in that role.
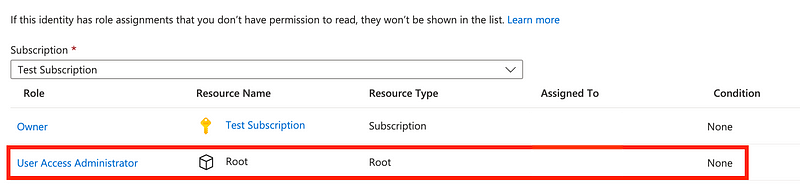
Search on write to find actions that can create resources. There’s no action that allows creation of a tenant.
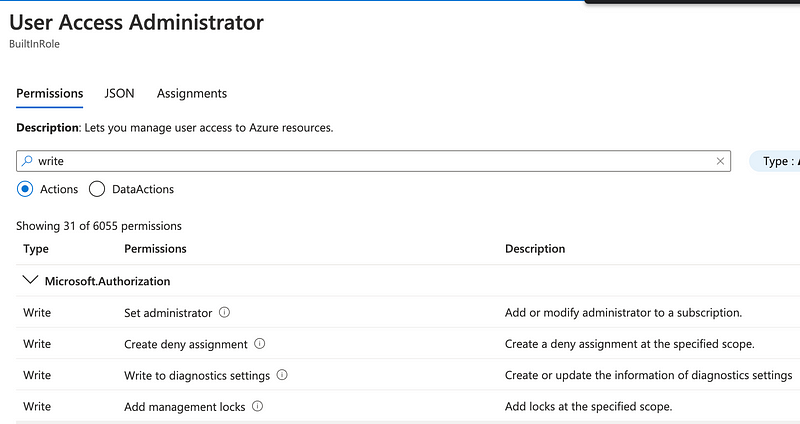
Alright, go back and click on our new Test subscription.
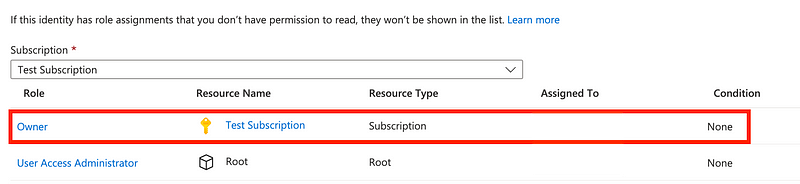
Another tangent. I went back to the alternate tab open in my browser inadvertently and navigated to user role assignment for my global administrator.
Once again there are no subscriptions to select. Even after refresh.
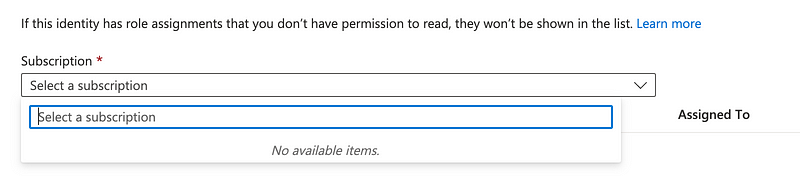
Well, the other tab seems to be working and I can select the subscription over there.
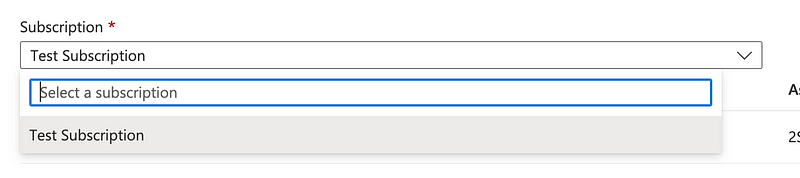
By the way, security teams should be aware of this message:
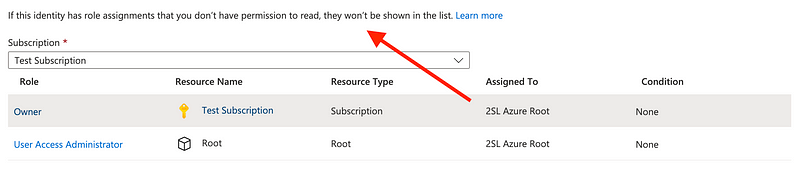
If you are performing an audit are you really seeing all the roles and permissions people have? These are the only two I see for the global administrator.
Click on the Owner role and search on write again. I don’t know how this search box is supposed to work, because if I search on “tenant” I get a bunch of things unrelated to tenants. That also seems like a bug.
But if I search on “write” that seems to bring up things that create resources. Then I just do a CRTL+F and search for tenant. Maybe I’m not doing it the “Azure Way” but I find that as owner of a subscription you can create tenants under the permissions for Microsoft.ADHybridHealthService. Does this mean my user now has permission to create a tenant? Let’s test it out.
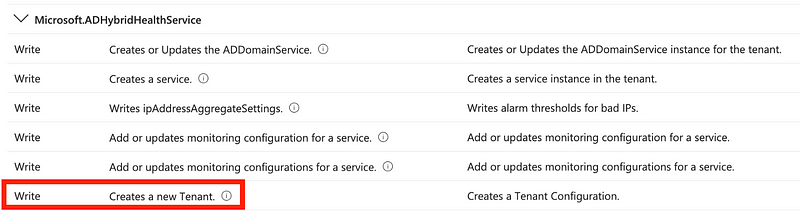
When I return to Manage tenants the + Create option is available again. It appears that I can create a tenant once again simply by making the global administrator the owner of a subscription. Let’s see if it actually works.
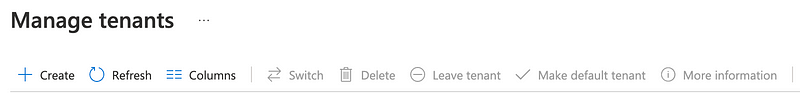
Why yes. Yes, I can. The toggling off of creating a tenant does not stop someone who is the owner of a subscription from creating a new tenant, apparently. Or at least the global administrator.
It does stop the global administrator for creating a new tenant unless explicitly granted that permission. Now, it seems like the global administrator can simply toggle on that button, so that seems like it was kind of a pointless exercise. I’m sure there’s a reason the toggle exists beyond that.
Azure role assignments vs. Assigned roles
I showed you what I see when I click on “Azure Role Assignments in the left menu.” Now if I click on “Assigned Roles” I see something completely different:
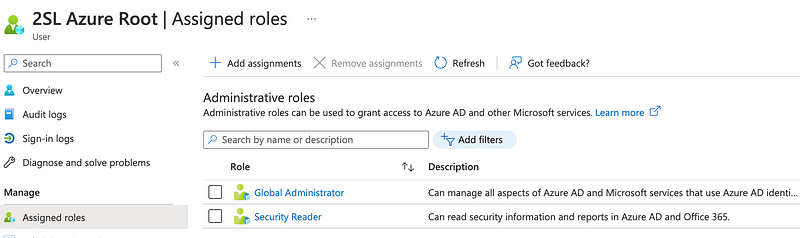
What’s the difference?
- Azure role assignments are managed by Azure. You can’t add a new role there.
- Assigned roles are roles that you manage yourself.
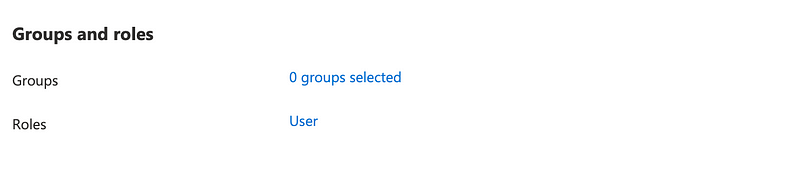
If you return to the user we created earlier that user has no Active Directory roles:
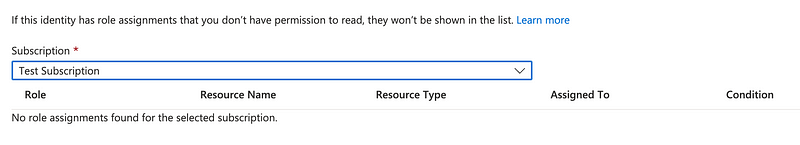
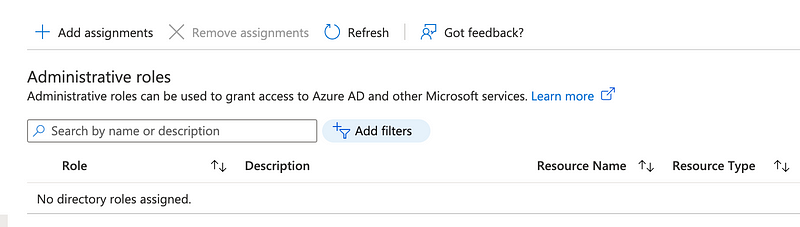
The user also has no assigned roles since we haven’t given the user access to an subscriptions. Let’s add a role. Click on “Assigned roles” and “+ Add assignments.”
This list seems to work a bit better. When you search on Tenant you get Tenant-related functions.
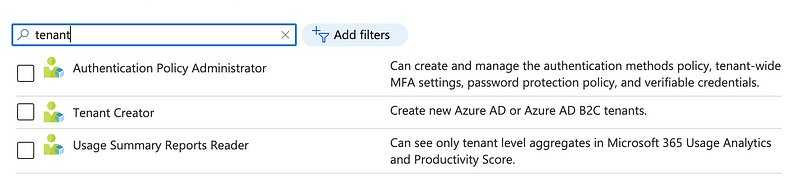
Add the Tenant Creator role. I had to refresh the screen to get it to show up in the list:
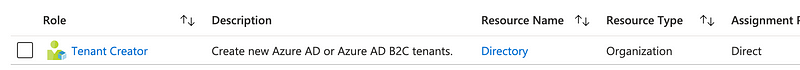
Now head back over to our incognito browser screen where we’re logged in as a new user. My new user can create a new tenant.
Strange behavior for this create tenant button
I’m going to be honest right now. Azure has a nice UI. Personally, I think some parts of it are more coherent than AWS like the consistency around resource networking and IAM restrictions. Windows Defender for Cloud looks nice and is well organized. I like being able to drill down into resources.
But all these magic toggle buttons and weird one-off permissions rules simply make it very confusing to actually secure and audit an Azure account. There’s also a magic button you have to toggle to make sure that, as global administrator in an Azure account, you’re actually seeing all the subscriptions in the account. That is simply odd to me.
I don’t see how this limitation on creating tenants is that useful since any owner of any subscription is not affected by it — at least if you take the steps I took above in an account configuration like mine.
Additionally, the user that is affected by it has the power to change the settings so that seems to make them kind of pointless. I’ll have to keep digging around because maybe I’m missing something.
Or maybe this is a bug and by the time you read this in a few weeks it might be fixed. I don’t know.
I really thought this was going to be a quick, short, post on a new Azure feature. As often is the case with cloud platforms, it wasn’t.
More on Azure to follow as I update my Azure class.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






