Homomorphic Encryption
When data is truly encrypted in use with Microsoft SEAL
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Multi-Cloud Security | Encryption
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
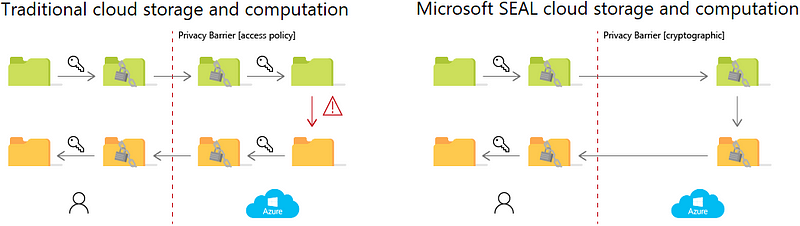
I’ve been seeing cloud providers advertise various enclaves and confidential computing solutions as “encryption in use.” But is it truly encryption in use? I may be splitting hairs here but I would not consider data operated on in an enclave as encrypted in use.
I wrote about enclaves, TPMs, TEEs, and confidential computing in these two posts:
If you want to see the whole process of creating credentials and trying different methods to create, protect, and store them follow along with the related posts in this series:
Encryption in an enclave
When you use an enclave to protect sensitive data, the data remains encrypted, even in memory, until it enters the enclave. At the point it enters the enclave, it is decrypted. That’s where some trusted and verified application code that exists in the enclave can operate on it in its decrypted form. Once the operation is completed, the data is once again encrypted and sent outside the enclave for transfer or storage.
It seems like it would be more correct to say the data is always encrypted, even in memory, unless it is in the enclave, which should be a physically separate piece of hardware so any malware on the rest of the hardware has extremely limited access or mechanisms to get into the enclave and access the data.
Rather than try to break into the enclave itself, I would expect attackers would try to get into the development process to get their own code inside the enclave. I’ve been writing about the problem with development and deployment system security for years. Although companies spend a lot of time making sure their code works and is secure in the development environment, they forget to consider how it may be altered on the way to it’s final destination. Think NotPetya and Solar Winds.
Encryption in use
What would true encryption in use look like? Encryption in use would mean the data is still encrypted while it is being processed. It never gets decrypted.
Consider that you have two values:
1 and 2
You want to add 1 + 2 and get a result.
Your encrypted data is gibberish. This is not actual encryption but it would look something like this:
13ns454673213axcv246q + qe56adv3463345 = ?
How could a computer process encrypted data? It looks like gibberish? The computer first has to translate the encrypted values back to something it can understand and add together to get the result: 3. And then it has to encrypt the result because if anyone can see the result that also is not encrypted in use.
Is there such a thing as encrypted in use? Actually, there is, kind of.
Microsoft has been working on this for a while with the Microsoft Simple Encrypted Arithmetic Library (SEAL).
Caveat:
Homomorphic encryption is not a generic technology: only some computations on encrypted data are possible.
This type of encryption has limited use cases like simple integer arithmetic and it comes with a lot of overhead, so it is not viable for many use cases. The article above states:
Microsoft SEAL homomorphic encryption library allows additions and multiplications on encrypted integers or real numbers. Encrypted comparison, sorting, or regular expressions aren’t often feasible to evaluate on encrypted data using this technology.
There are also a fair amount of caveats in the readme of the Github library.
Semantic Encryption Vulnerabilities
The questions I have when I think about the possibility of homomorphic encryption on a broader scale is, wouldn’t that lead to semantic encryption vulnerabilities?
Semantic encryption flaws result from being able to determine what the encrypted values are based on some property of the encryption that allows you to decipher what the values are without decrypting them.
White papers and research exist in on this topic.
This one looks interesting as it is applicable to TEEs, but I digress.
I remember a particular vendor that offered the ability to encrypt data before sending it to the cloud when everyone was afraid of moving data to the cloud. Some cryptography experts point a semantic encryption flaw due to repetitive characters in a demo the company was displaying at conferences. I can’t remember the name of the company at the moment so unfortunately cannot provide a link but it was a company we used at a financial organization where I worked (post-discovery of that vulnerability — hopefully that was the only one).
Leaving it to the Cryptography Experts
Encryption in use is a very interesting concept, but I’m not sure if it is as viable or possibly even as secure as other options. I’ll leave that assessment up to cryptography experts. But don’t rely on the cryptography experts who developed the product or software when trying to vet a potential solution. Typically cryptographic schemes undergo scrutiny by many sources before deemed secure, hence the phrase:
Don’t roll your own crypto.
When thinking about security solutions, it’s important to not get too tripped up in the terminology or focus on one aspect of the technology that solves a particular problem while introducing another. Rather, understand the solution as a whole, potential attack vectors from all angles, and how it fits into the larger enterprise architecture. I think TEEs or enclaves can be valid way to provide additional protection for sensitive data. I just wouldn’t call them “encryption in use.” However, encryption in use has a long way to go and wouldn’t recommend it until vetted by industry cryptography experts.
On that note, I tried to find out if Bruce Schneier has written about homomorphic encryption. Yes, he has. He wrote about a discovery related to homomorphic encryption by IBM here in 2009:
Visions of a fully homomorphic cryptosystem have been dancing in cryptographers’ heads for thirty years. I never expected to see one. It will be years before a sufficient number of cryptographers examine the algorithm that we can have any confidence that the scheme is secure, but — practicality be damned — this is an amazing piece of work.
So yes, homomorphic encryption is really cool and maybe some day we’ll be able to use and trust it, but for the moment, it has a long way to go.
He noted that Google released a tool for homomorphic encryption here in 2019:
He reiterates that homomorphic encryption is impractical here in 2020:
Update: 6/8/23 — I noticed a post on Homomorphic encryption in the AWS Security blog. I didn’t look through the implementation in detail but is it truly homomorphic encryption, or using an enclave to prevent access to data while unencrypted? Also, encryption that is not very secure will allow you to make inferences about the data — that’s also not homomorphic encryption. It’s a security vulnerability sometimes referred to as a semantic encryption flaw. It means that your encryption will not produce a random histogram when evaluated and it may be possible to decipher what’s in the data through analysis, rather than direct decryption. I haven’t looked at the details in this post, but be aware of the differences when you evaluate a homomophic encryption solution. I leave the analysis of this solution as an excercise for the reader.
Although a TEE or enclave is not truly encryption in use from my perspective, they are still a viable approach to providing better security for your sensitive data. Just make sure you do an analysis of what is entering and leaving the enclave as well as what is in it.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab






