Getting the Role Name That Deployed a Resource
ACM.360 Adding the role name that deployed a resource to the CloudFormation stack name instead of the profile for better attribution
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: AWS Security | Secure Code | Cybersecurity
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In my next few posts I’m doing some cleanup and fixes as I migrate code to this new format and create my environment deployment code.
I’m starting with something that has been bugging me for a while.
Recall that I have a common function and that initially I was passing in a profile as the first parameter.
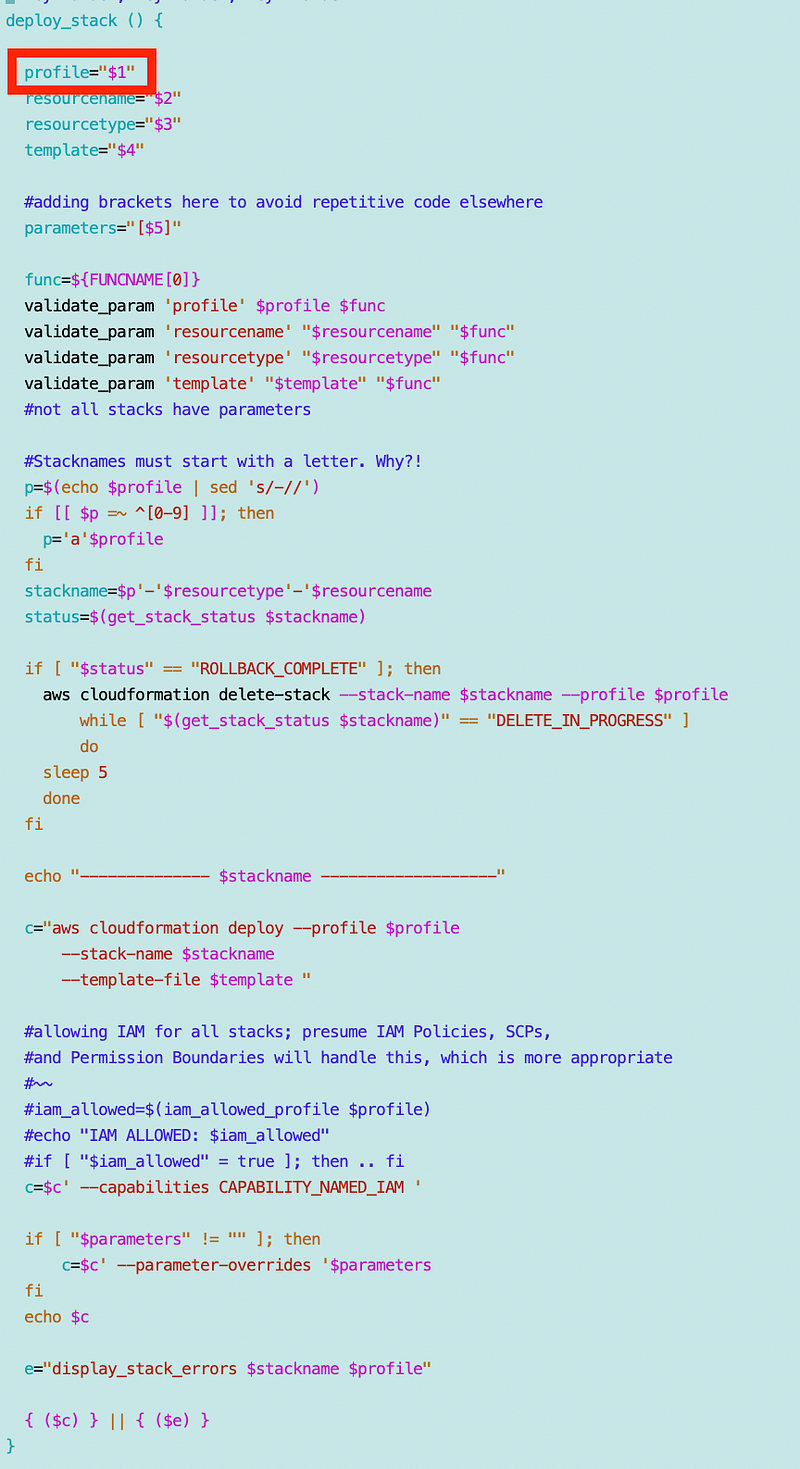
I am using the profile in the stack name but I started to think that is really not appropriate. Someone can name the profile anything and use a different role. What I really need to use in the stack name is the role name which I can get with the following call:
aws sts get-caller-identity --profile SandboxAdmin --output text --query Arn | cut -d '/' -f2So my template changes as follows, and I’m taking out a few comments and removing some error checking. All roles will be all lowercase starting with a letter and no special characters. They can’t start with a number because for some unknown reason, CloudFormation stack names can’t start with a number.
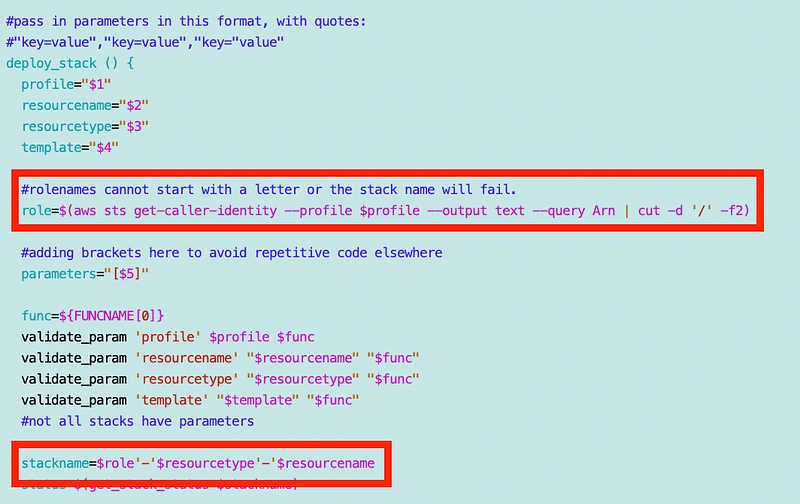
One simple change for more accurate stack names using our naming convention.
Note that I can also remove the profile parameter and the default profile can be used now. I can alter my CLI calls to use the default profile if the profile is not set before calling the function.
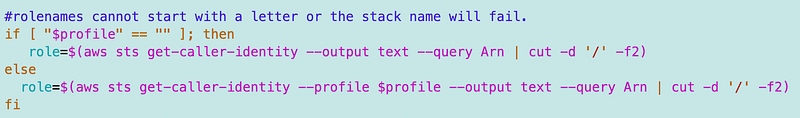
If I restrict all my CloudFormation deployments to roles this should work. I think it would also work with users but I didn’t test that. In my case, I want to force all CloudFormation deployments to use roles.
Because the above would require a lot of if-then statements, and becuase I don’t want to allow users to deploy without a role, I’m going to throw an error if a profile was not set prior to calling this function.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
