Drift Detection for Multi-Cloud Security
Multicloud.10 How drift detection can help you find non-compliant resources
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Multi-Cloud Security | AWS Security | Azure Security | GCP & Google Security.
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I wrote about Terraform to help you manage the complexity of multi-cloud deployments. I also warned you about some of the security issues you might face if you rely on Terraform that you should assess.
In a prior post I mentioned drift detection. I looked at which cloud providers offered that capability and it seems like only AWS does at this time. I wrote about an option for implementing this on Azure in my post on automated governance in Azure and I’m sure you could implement this yourself on GCP as well.
Drift Detection on AWS
Let’s look at how it works in AWS. I’ve been deploying a lot of resources for my other series here:
I’m going to log into the AWS Sandbox account I created and take a look at my CloudFormation stacks. I selected a stack for a Route table.
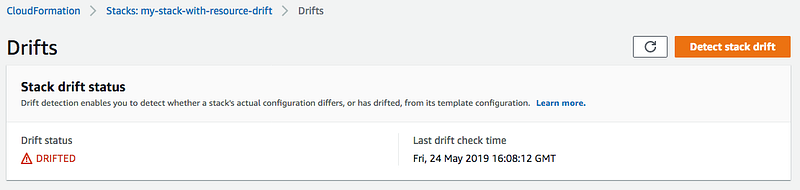
Next I clicked on Stack actions > Detect drift
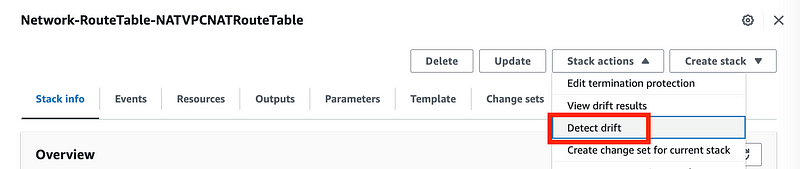
A message appears that drift detection has been initiated.
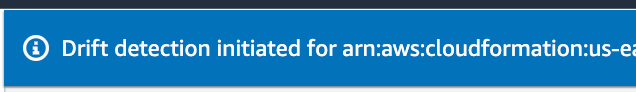
When the process is complete, click Stack actions > View drift results.
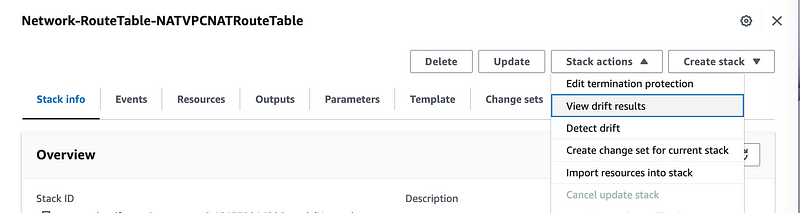
The results show that my resource, a route table, matches the configuration I deployed using CloudFormation.
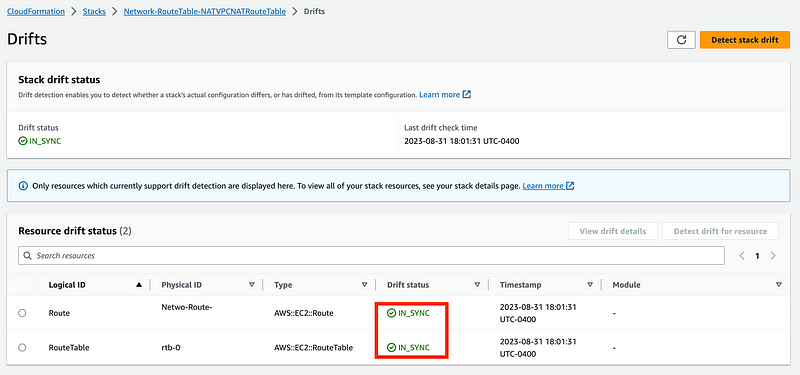
What was that configuration?
If I return to the stack I can click on Template and view the code that deployed the stack:
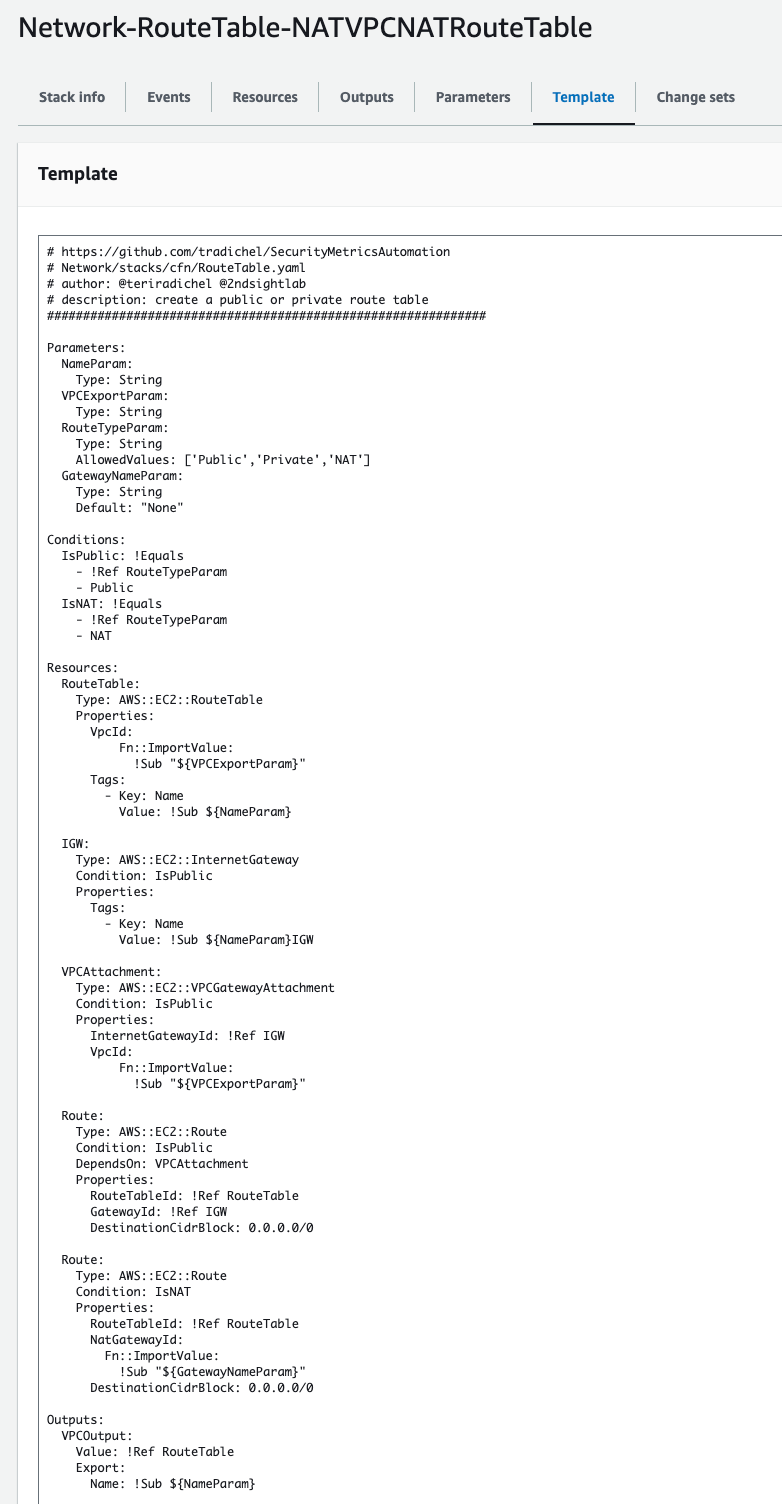
The route deployed depends on the value passed into the Parameter: RouteTypeParam.
Click on Parameters. There you’ll be able to see the parameter values passed into the template.
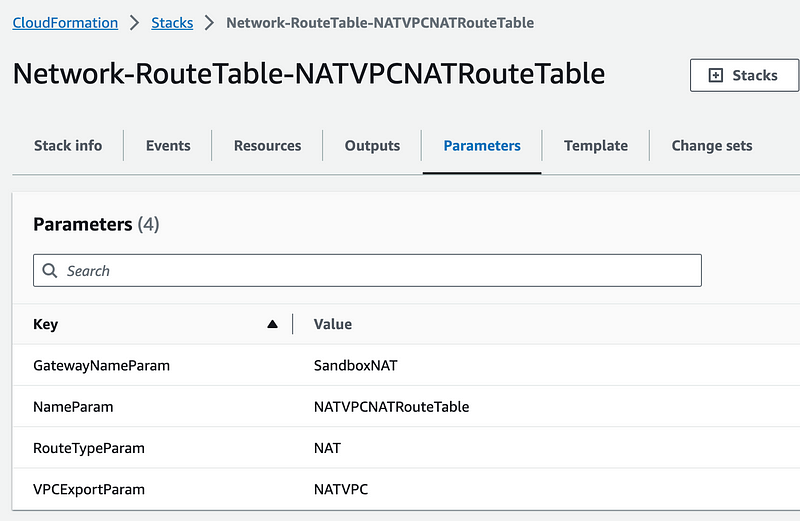
Now let’s say something got deployed which was not in sync with the code originally used to deploy the resource. You would see that the stack had “drifted” from the deployed configuration. At this point you can go back and redeploy the resource to get the configuration back in sync.
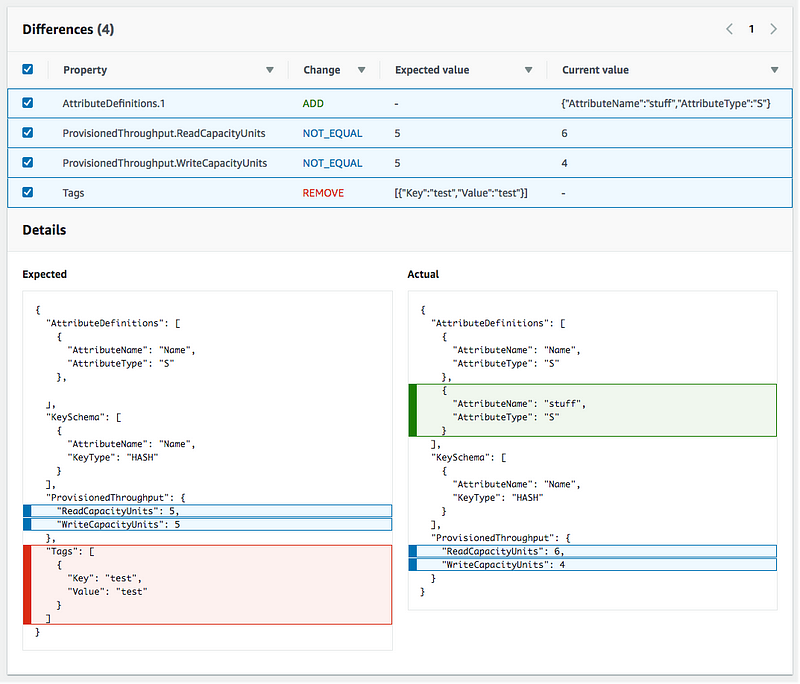
As shown in this documentation you can also compare the differences:
You can also perform drift detection with the AWS CLI and create a report or auto-remediations if you want. I’ll probably cover that more in my other series.
Drift Detection on Azure and GCP
You can’t easily perform drift detection on Azure or GCP. It’s not built in, though as I mentioned people are requesting it for Azure and have proposed some implementations. You could implement it yourself.
Keep a log of commands executed to carry out deployments.
Keep a copy of the template used for each deployment.
Keep a copy of the parameters passed into the template.
Run a query in production to pull the current configuration.
Compare all the values used in the deployment to what exists in production.
Report on whether or not the values match.Obviously the more variations in the way things are deployed, the more code you will need to write. If you don’t use templates, how do you know if the libraries change and are producing different results compared to the original deployment? It can be done but is not a simple task. It will be easier if you can compare a template to a production query in a fairly straightforward way. In other words, you get back a query from production that closely aligns with the template used to deploy your resources as shown in the code diff above.
Terraform Drift Detection
If you are using Terraform for multi-cloud deployments you have a consistent way to detect drift.
An important part of tracking and detecting drift is the terraform state file. I mentioned the state file in my last post. Some people were not happy that Terraform does not yet allow customers to encrypt the state file. What is in the state file?
According to the documentation above:

Does this file contain sensitive data? Take Terraform for a spin and judge for yourself. You will want to try to avoid that by using an appropriate secrets management system. Terraform provides one called Vault. AWS, Azure, and GCP have services to manage encrypted secrets and retrieve them at application runtime.
Here’s a scenario where someone is having a challenge with the Terraform state file and the answer recommends potential solutions.
As an aside I showed how to create a secret in AWS CloudFormation without exposing it to a user here:
Later AWS came out with a mechanism to create an RDS database without exposing the password in a similar manner.
Hopefully Terraform supports that. I haven’t tested it.
The fact that Terraform can help you implement drift detection is great. The problem is that Terraform templates are likely not a one to one mapping of what the native cloud templates look like and may not map directly to queried output. You’ll want to verify the drift detection works properly if you are depending on it.
One thing that concerns me in the above implementation is that the state file mentions caching. If the data is cached and drift detection only looks at the cache, not the actual cloud environment, something might be missed. Also, caches can be poisoned. If you are going to rely on Hashicorp drift detection, you’ll want to evaluate that threat vector carefully.
If the drift detection works properly and is reliable — this is a feature that could save you a lot of time and quickly spot rogue deployments outside of your defined, secure, deployment process.
Here are a few other posts on Drift Detection that may interest you:
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
