Deploy A TLS Certificate for on AWS Using CloudFormation
ACM.245 Using AWS Certificate Manager to deploy a TLS certificate for a web site or application
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Application Security | AWS Security | DNS | TLS
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post, I explained how to use the AWS CLI to deploy an NS record on the primary domain hosted zone. It wasn’t that simple.
Now we can deploy a TLS certificate using CloudFormation (and I’ll switch the above to CloudFormation later as well.)
TLS is not SSL
Just a note to start that SSL was retired a while back and TLS is the replacement. You should not be using SSL. Unfortunately much of the documentation out there even for TLS references SSL. Know that they are different and you should not be using SSL. You also want to make sure you are using an up to date version of TLS and that your system does not accept downgrading to an insecure version. Check the configuration instructions for your web servers, application servers, and other systems you use with TLS to lock down your configuration appropriately.
One interesting note. I was looking up the spec to show you that there are two different specs for the different technologies and stumbled across this update:
It says Huawei in the top right corner. That’s interesting. I hope people are paying attention to changes in specifications and evaluating them carefully. So many vulnerabilities exist in encryption protocols.
If someone could insert a vulnerability (as they have, including governments around the world) then they may be reading all your data. So it is important that we have top minds working on encryption protocols from whatever country you’re from and everyone is developing a truly secure solution. But I digress.
A Free TLS scanner
You can use this free scanner to check the security of your TLS certificates. Unfortunately this has SSL embedded into the domain name but you can use it to check your certificate configuration.
About AWS Certificate Manager
That certificate deploys a certificate using AWS Certificate Manager.
We are going to create a public certificate for use with a web site, web application, or Application Programming Interface (API).
One of the best features of ACM is that your certificates will automatically renew before they expire! Some of the most time-consuming troubleshooting I’ve seen when apps are randomly failing come down to DNS — or failed certificates. Once a member of my team was pulled of a critical project for a day to troubleshoot a failing UI. It was an expired SSL certificate. I heard a story about a travel site that lost $40M in a day while the team performed troubleshooting which turned out to be — and expired certificate.
In all cases it boggled my mind why there was not some sort of alert to the problem in advance. But now you can just automate that away. Do it!
In addition ACM integrates nicely with a bunch of other services:
How much does it cost? Nada. Nothing. Zip. Zilch!
Public SSL/TLS certificates provisioned through AWS Certificate Manager are free.
Why would you not use this service? There are some potential reasons but for most companies it is a no-brainer.
I’m specifically talking about public certificates. Private certificates do have fees associated with them:
Deploying a Public TLS Certificate on AWS
Recall that we used an application name in our other templates for this website so we can find all the resources associated with it. We’ll want to use this in our TLS Certificate template as well.
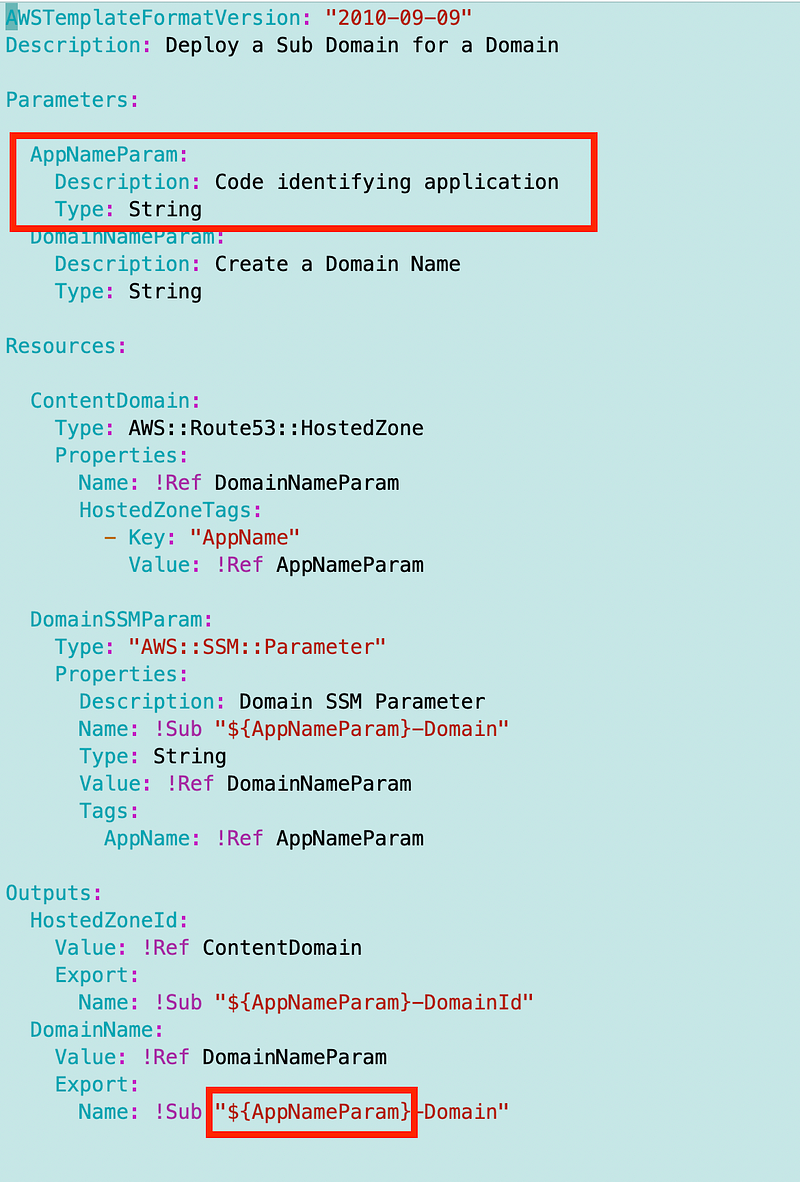
Here’s the documentation for deploying a certificate using AWS CloudFormation.
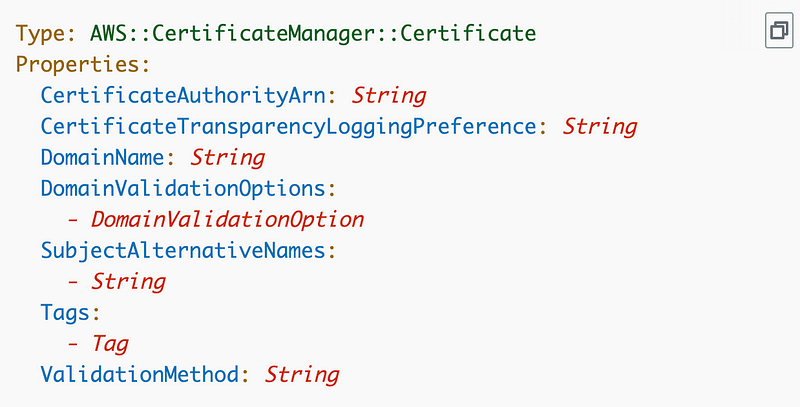
CertificateAuthorityArn — N/A (for private certificates)
CertificateTransparencyLoggingPrference — not now — I’ll write a separate post on that.
DomainName: Get the from the stack where we deployed the hosted zone.
DomainNameValidationOptions: We deploy this in a second step. Hold that thought.
SubjectAlternativeNames: N/A for our subdomain. If we deploy a primary domain like rainierrhododendrons.com then we can use the same certificate for www.rainierrhododendrons.com. But those will be production domains in a separate account with a separate S3 bucket. So no Subject Alternative Name here.
Tags: Optional.
ValidationMethod: Always use DNS. Email is not a secure form of validation. If you do not specify a validation method, email is the default. Creating a common template such as we are doing in this post that forces the use of DNS will help your security compliance efforts.
Note that I am only adding the DomainNameValidation if a hosted zone ID is passed in as a parameter. That’s because we have to follow these steps to deploy a TLS Certificate with CloudFormation:
- Deploy the certificate.
- Get a value from the CloudFormation output.
- Update the hosted zone.
- Pass in the hosted zone ID to validate the certificate.
I wish that instead of this process that leaves the stack hanging AWS would have used two separate resources but it’s what we have to work with so let’s do it.
Here’s the template:
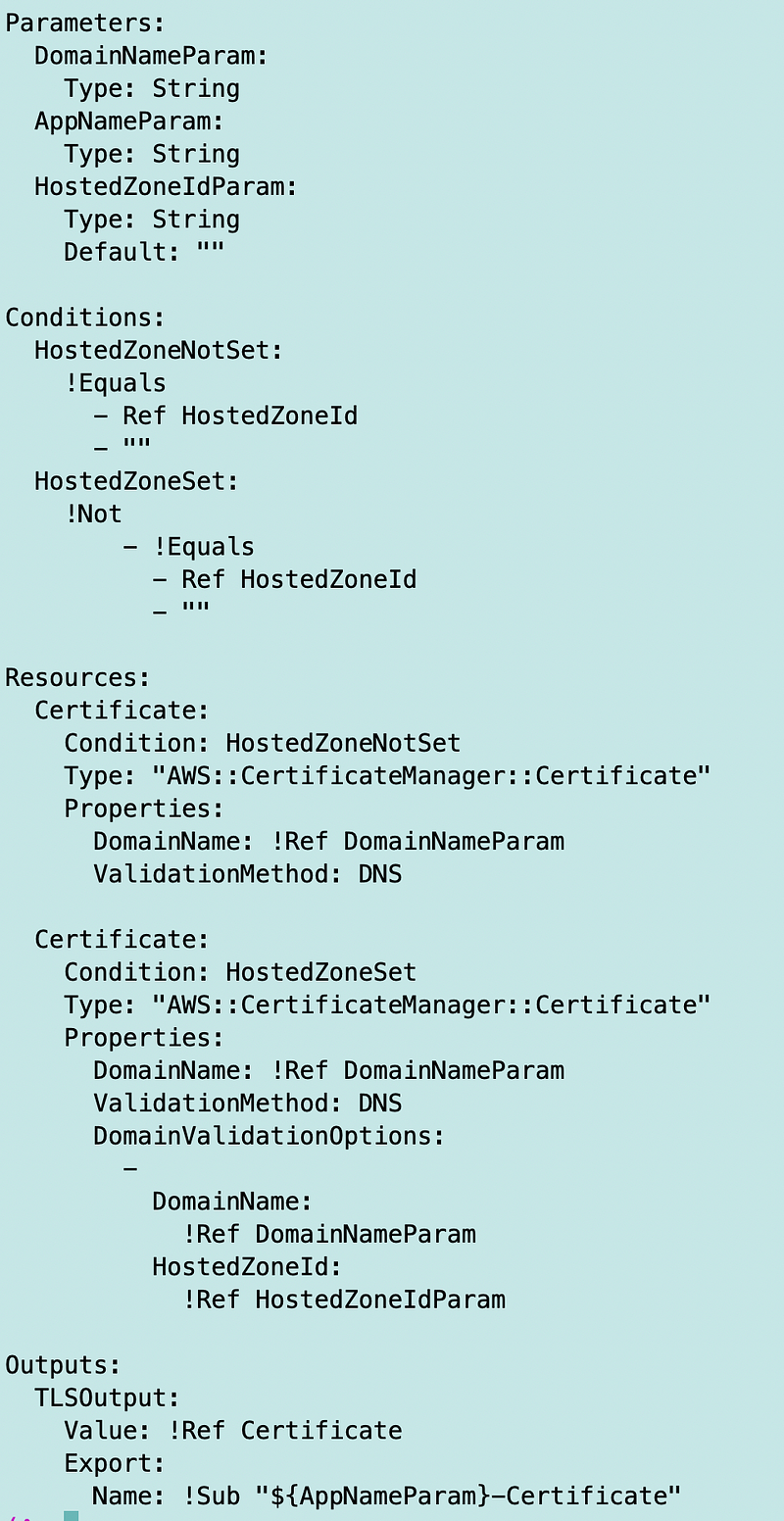
Note that there are two certificates in there. We are concerning ourselves with the first one in this post.
** Also: I greatly simply this in the next post **
I added that template to the following directory:
SecurityMetricsAutomation/AppSec/Stacks/CertificateManager/cfnFor now I’ll let the SandBox Web Admin deploy certificates since we’re testing this out in a sandbox account.
I need to make sure my change_dir function has the AppSec option:
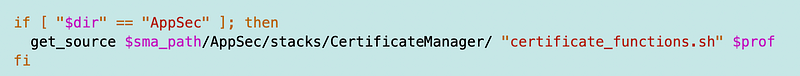
Recall the above function exists in:
SecurityMetricsAutomation/Functions/assume_role.shI need to create the function to deploy a certificate in the following file:
SecurityMetricsAutomation/DNS/stacks/certificate_functions.shHere’s the certificate_fuctions.sh function to deploy the stack the first time.
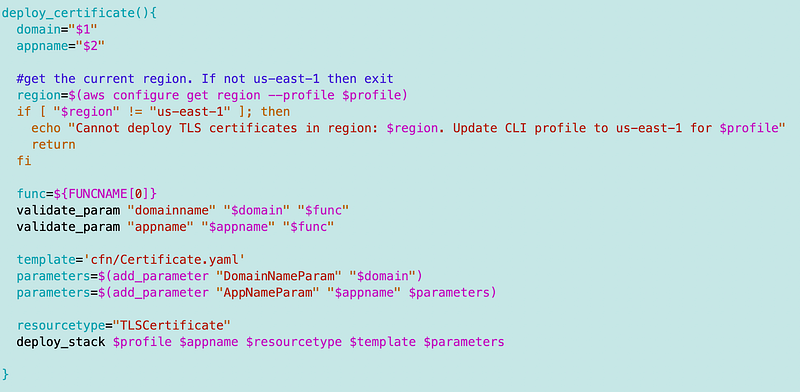
Add a call to the above in the stack that creates the website:
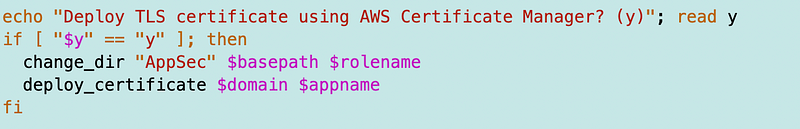
Run the script.
Now here’s where I think the implementation of TLS Certificates in CloudFormation is just odd. You deploy the stack and it sits there like this.
Waiting….waiting…waiting…
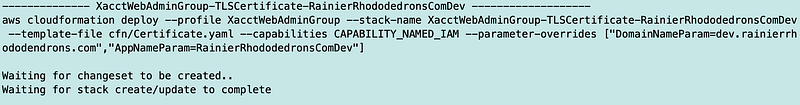
And if you keep waiting you will be waiting forever because there’s another step you have to complete to finish deploying this stack.
It’s a really strange deployment because you have to create two scripts to deploy the certificate as well or kill your script and somehow skip the in-progress CloudFormation stack. This implementation just plain feels wrong to me but it’s how it works, so we’ll just get it done with what we’ve got.
I’ll finish the deployment in the next post.
By the way I was having issues with import values and subs so I gave up. I might revisit this later:
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
