Complications with AWS CloudShell (and any CloudShell for that matter)
The idea of not having to create a compute resources is nice but…
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Bugs | AWS Security | Secure Code | CloudFormation
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~I’ve been using CloudShell to spin up my initial cloud account but want to get away from it as soon as possible. I’ve written about a number of issues with it in this blog, which AWS is probably going to fix eventually. But there are some more troubling issues from a security perspective that I’m not sure can be fixed with any CloudShell environment (easily.)
UPDATE: The same day I wrote this some great improvements have come out in CloudShell. Unfortunately solving all these problems is likely a bit complicated. But it does seem to be working a bit better from a Mac at least. :-)
.swp files
I’m seeing .swp files all over the place. Whenever I have a file open and a session times out, I end up with a .swp file because I was in the middle of editing that file with vi. If I return to editing that file I need to delete the .swp file or override or something. It’s kind of messy.
Can’t encrypt files with a customer managed key
With CloudShell you can’t encrypt the compute resource with a customer managed key as I showed you how to do here:
I’ve explained a number of times in my latest series why you might want to do that.
Can’t control network access
I’ve seen some pretty interesting IP addresses in AWS logs lately. For actions are taken through AWS CloudShell you’ll have no control over the IP address assigned to CloudShell or the ability to enforce taking those actions only from a private network or using AWS PrivateLink. If actions are taken from an EC2 instance you can limit actions to your own networks and private networks.
Can’t control S3 or compute configuration
I presume AWS CloudShell is somehow stored in S3 and some type of compute resource such as a Fargate container or similar. Organizations have no ability to control the security of the underlying platform or create S3 policies on any files stored by CloudShell.
Excessive AWS CloudTrail logs
AWS CloudShell generates a ton of traffic in CloudTrail. That’s a lot of noise that perhaps should be in a separate log for CloudShell itself. By using an EC2 instance you separate the logs for the environment running the commands from the CloudPlatform actions.
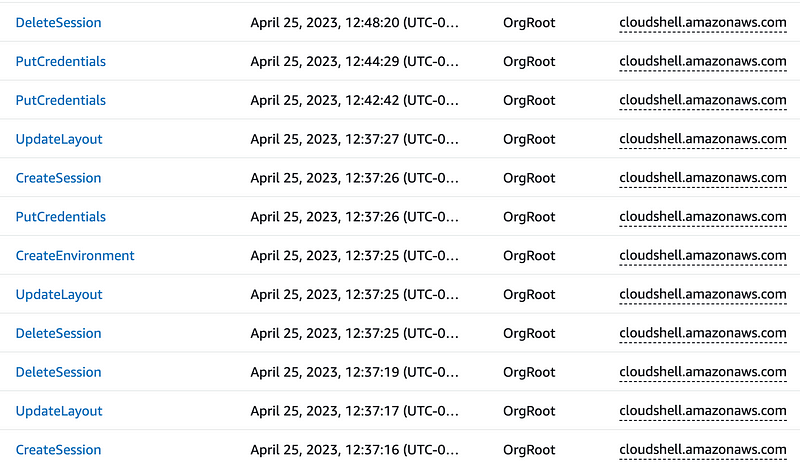
The above is one of the main reasons I no longer want to use CloudTrail as soon as I can set up an alternate resource. Maybe AWS will fix this so accounts have the option to create separate trails for each CloudShell user and environment.
Limited information in CloudTrail logs — fixed now?
I’m not sure if this is specific to CloudShell but I’ve noticed that for some actions, AWS was limiting visibility into the full request earlier today. I’m not really a fan of this. I want to see the full request and what is happening in my account similar to how Google Cloud provides access transparency logs.
However, now when I login and click on those same actions, I do see the full request again. Not sure what was causing that.
Confusing regional access
I find it confusing that when I switch to a global AWS service, CloudShell switches to a different environment and I lose whatever I was working on. I have to switch back to a regional service to get back to my code. Am I also billed for two CloudShell environments somehow in that case?
Multiple windows open for every new dashboard page you open
I generally have a bunch of different service pages open at once when using AWS. I usually show students in classes how to right click on the AWS icon to open a new service page so you don’t lose what you were working on in a related service page. Every time you do that you get a new instance of CloudShell which is a bit annoying. Closing CloudShell on the new page sometimes affects the other CloudShell instance you have open.
I just want one instance of CloudShell in a separate tab, so I try to maximize it in the new tab and close it in the other tabs. That kind of does what I want. But the other security issues are too much to overcome at the moment.
Perhaps AWS will come up with a way to fix the above issues and the other complications I have using it form a Mac but for now I’m going to try to set up a sandbox user and disable completely via an Service Control Policy in all but my Sandbox account. Even there, I generally don’t want to use it.
A few other updates:
Can’t get out of a hung up state
Somehow I got into a state where I can’t see the output of what I type. This happens sometimes in a normal terminal too. The problem is in the regular terminal I can kill the app and restart to get back to a good state. In AWS CloudShell I don’t see that the option to restart the environment does anything at all. Refreshing the page doesn’t fix the problem either. Closing and re-opening CloudShell doesn’t help using the X at the top right of the screen, nor does opening a full screen.
Ultimately, I signed out and back in again to try to resolve the problem. Nope that doesn’t work either. My CloudShell is in some king of messed up state and cant seem to get it back. I can’t see the commands I’m typing, but at least I can still get the output.
I was trying to test the AWS secretsmanager list-secrets and get-secret command when this started.
Ah finally! I figured out that if I type exit it restarts the environment for real. That’s what the restart environment action in the menu should be doing.
Copy and paste not working
Now randomly copy and and paste doesn’t work from CloudShell to something I’m writing locally. But ok weird. Upon further testing whatever CloudShell did broke Copy and Paste completely in Google Chrome.
Ctrl+ and Ctrl- on Mac in Google Chrome is not working
I can’t increase or decrease AWS CloudShell font size on a Mac using Ctrl+ and Crtl-. I have to use the Chrome menu to zoom in or out. Then I can use the popup with a plus and minus that appear from Chrome itself.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab