AWS Credentials and Roles for the pfSense VPN Wizard
ACM.466 Also, why I’m not going to use this wizard
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories IAM | AWS Security | pfSense | Network Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I created a VPC and configured flow logs for use with a site to site AWS VPN connected to pfSense.
In this post, I’m going to take a look at the pfSense AWS VPN Wizard. That requires creating some AWS credentials and IAM resources.
All you need to use the AWS VPN Wizard in pfSense is an access key and a VPC.
Spoiler alert:
- I’m not going to use this wizard, but I’ll show you how to create the credentials (untested).
- I don’t like giving pfSense my AWS credentials.
- I definitely don’t like the guidance that says to leave them on the pfSense after you’ve set things up.
- There is no guidance in the Netgate documentation as to what the minimal permissions required by this wizard are.
- Although this worked easily in the past, it didn’t work this time, likely due to Service Control Policy restrictions in my organization which I don’t want to change.
- I suspect it has to do with the regions I’m using or possibly my MFA requirement but there’s nothing in the logs to indicate the problem.
- If you don’t have these restrictions it will likely work for you as I used this in the past and it was really simple and worked fine.
- I provide some information to help you troubleshoot below if for some reason the IAM resources don’t work.
- You don’t need to use the wizard. I’m not going to — I just wanted to see what it created to help me create my own automation but looks like I’ll be doing that manually.
I’ve used the wizard in the past and it’s pretty simple but there are a few things I don’t love about it — one being that it leverages an AWS developer access key. But we can take some steps to try to limit what that key can do.
Refer to my posts on IAM here if you want to understand more about AWS IAM users, roles, access keys, policies, and assuming roles. But I’ll walk you through it below.
To get around this risk I’m going to set up the VPN with the wizard and then immediately delete the key. We can recreate a new access key if needed. The key is going to be limited to what is required in the IAM Policy which is primarily the EC2 service. I’m going to start with that and see what permissions this key needs or requires and add them as needed. Then I’ll use the instructions in the above posts where I already covered how to create an IAM Policy with only the essential permissions. It would be helpful if Netgate would publish the policy for you as part of their documentation.
Why should you delete the key? Because attackers are repeatedly breaking into home and business edge devices like routers and firewalls and if they obtain access to processes on that device they will obtain access to view those credentials — and can use them depending on what other restrictions you have in your AWS account.
I wrote about that here:
And has happened again recently since then:
By the way, the best protection against the above is to not use the default password and make sure your devices are up to date with the latest software. It’s also a good idea to periodically completely upgrade your router and to purchase from a secure channel (not eBay if you don’t know how to check to see if the used device you bought is already infected with malware.)
Create a NEW AWS IAM User — do not use your admin keys!
I’m going to set up a completely separate AWS IAM user account for this test. All my accounts require MFA to perform actions but we can’t do that the way this wizard works, unfortunately. But once I see what it’s doing, as you can imagine, we can construct our own process to create the required resources on the AWS side with our own scripts without the wizard.
Let’s see what the wizard does. You can find the instructions here:
That page sure does try to connect to a lot of extraneous things.
Create an AWS Access Key
The first thing we need is an AWS Access key. In order to track exactly what this key does:
- I’m going to create a new IAM user named pfSense.
- I give it a policy that allows EC2 actions only (which is really too broad but this is a test in a standalone account).
- I create developer keys specifically for this purpose.
- I’m going to disable the keys when I’m done.
I was following along in the documentation which shows a screen like this with an AWS secret key and access key:
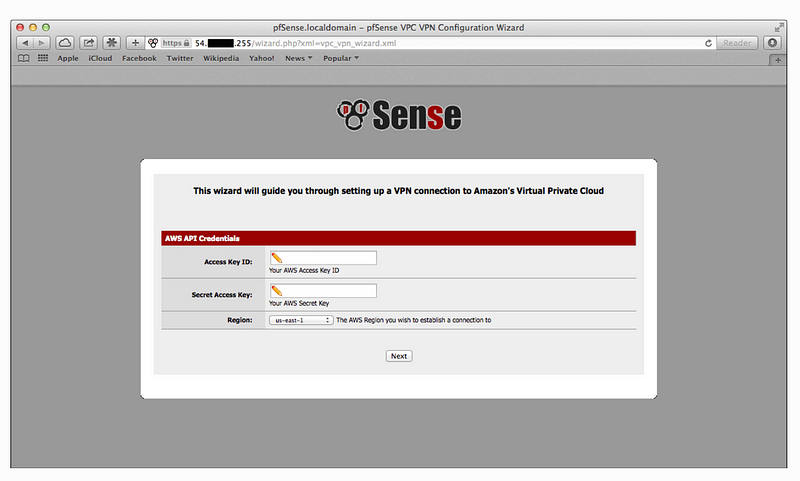
By the way, I disagree with this information in the pfSense documentation and like I said I’ll be deleting the key once this wizard is complete. Rotate this key as soon as you complete this process or delete it so it is not exposed in your pfSense device for someone else to access, should they get onto your device. You only need it for the initial configuration. If you need to change the configuration in the future, create a new key and then rotate or delete it.
Head over the IAM Dashboard.
Create a User.
Note that I am NOT going to give this user access to the AWS console.
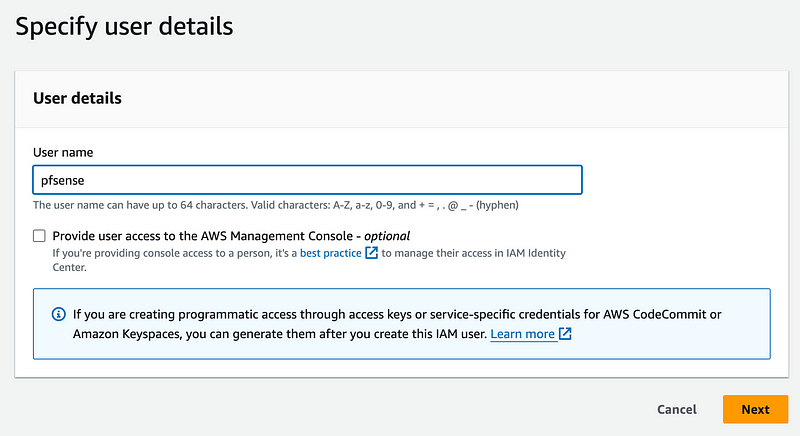
Normally I don’t do this but for this test I am going to attach policies directly:
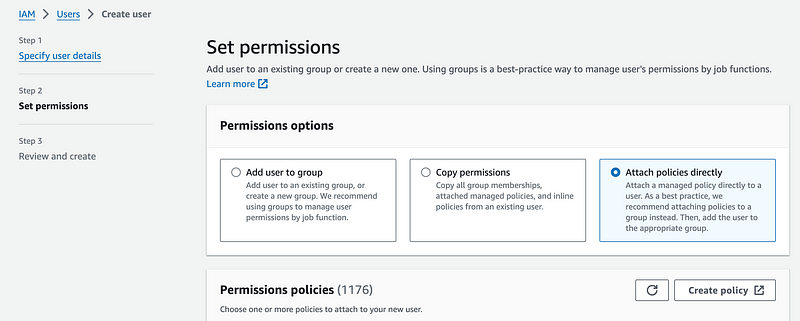
I’m giving full access to EC2 (which is very powerful and not what I will do with my final solution).
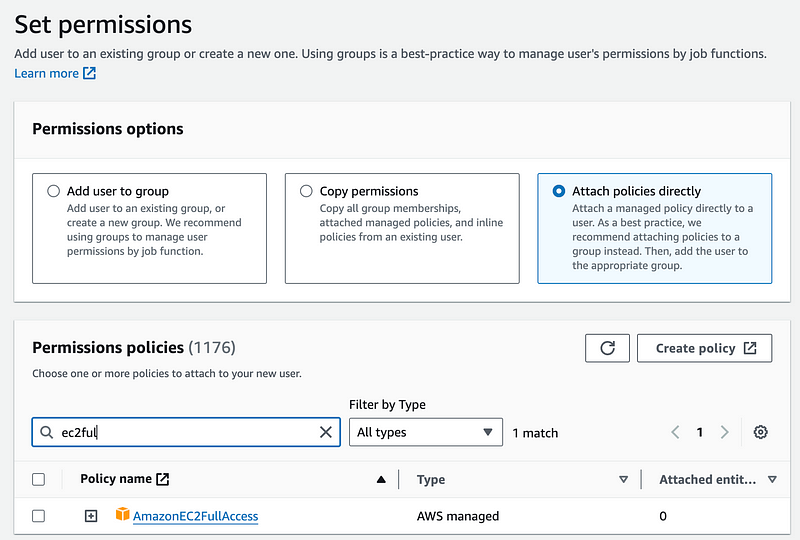
Create the user.
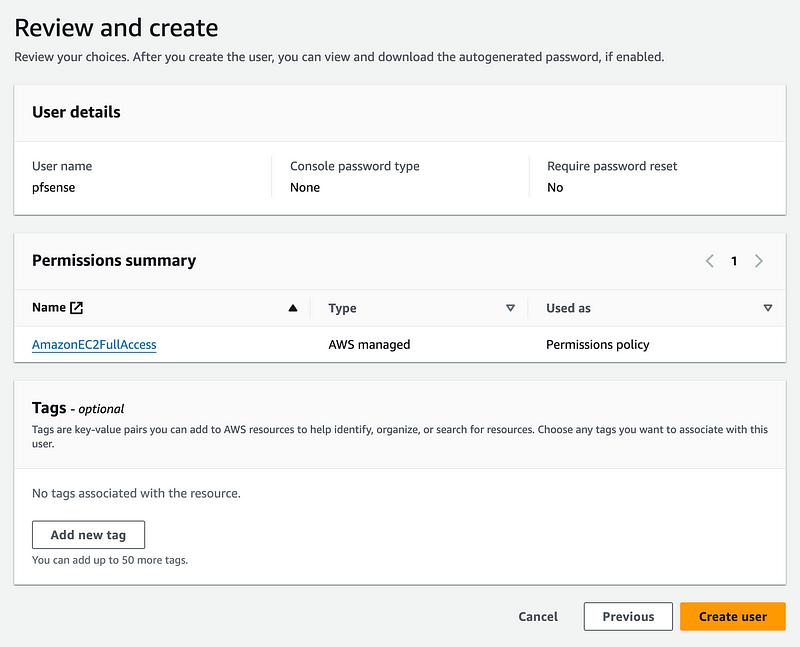
Click on the user (pfsense):
Click on Security Credentials:
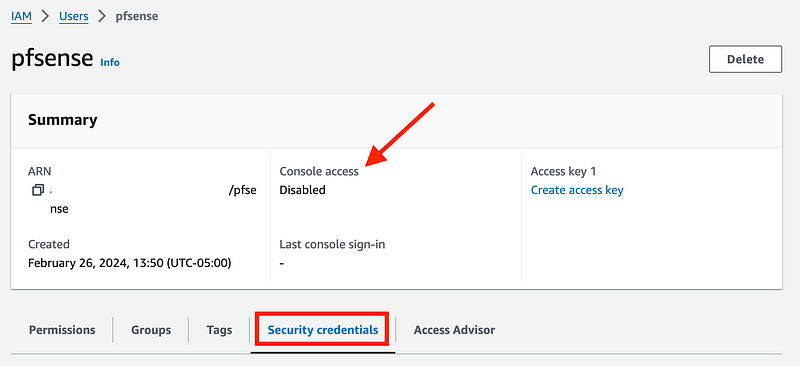
Click on Create Access Key.
Choose AWS CLI:
Note the alternatives which I don’t love as I’ve written about before. We can’t even use them in this case.
Click the box for “I understand” and click Next.
Add a description and click Create access key.
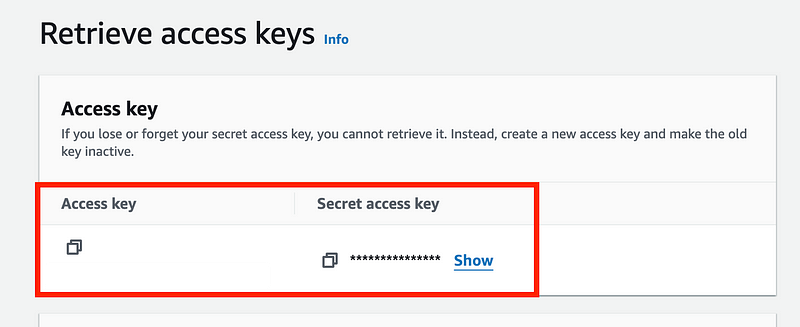
Copy your Secret Key and Access Key and store them in a safe place. You won’t be able to see them again.
Run the pfSense AWS VPN Wizard
Head back over to pfSense. We are going to use the VPC from the last post.
I’m up to this point in the wizard but really the VPC configuration should come before the point where you start using the wizard in pfSense.
This screen looks different than mine so we’ll see if this still works:
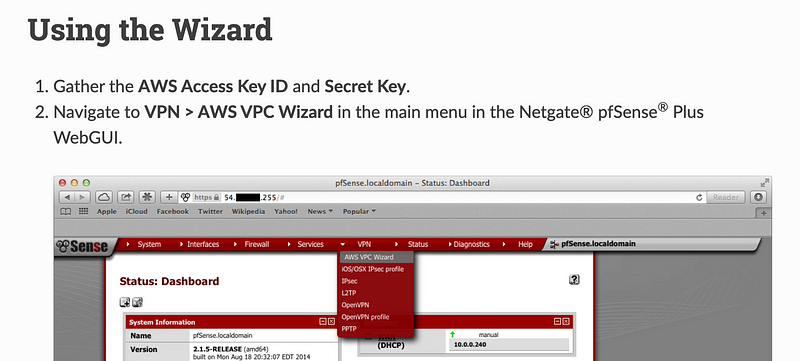
Well the first screen looks different than the documentation.
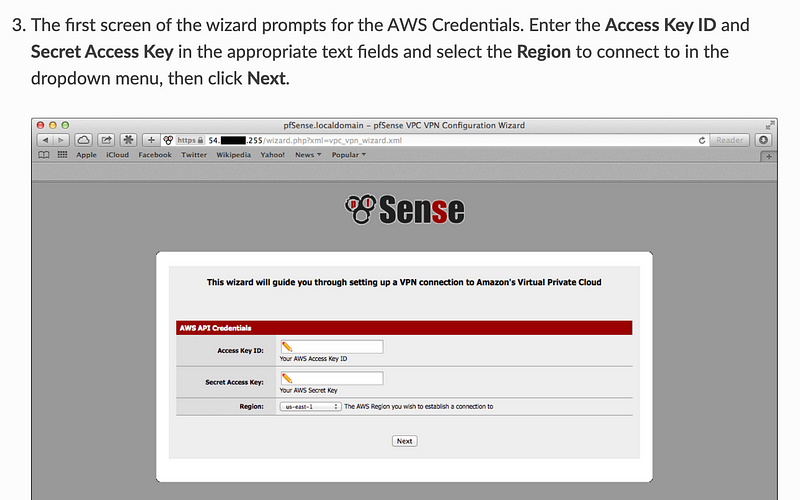
It’s asking for a role. A role doesn’t do anything for us here except expose our account number to pfSense. I’m not sure why they added it. It doesn’t offer any additional protection since you’ve already given pfSense the credentials — unless it asked for MFA but I’m not real keen on putting AWS MFA codes into pfSense.
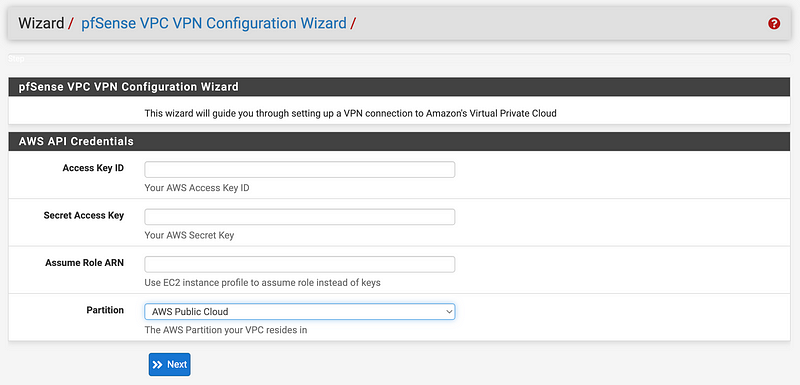
Well, back to AWS as we need a new IAM Role just to test this out. Thankfully I’m doing it in a test account before deploying it permanently because I’m not going to use this now that I see what it requires.
Create a role for the pfSense AWS VPN Wizard in AWS
Head back to the IAM dashboard.
Follow the steps above that we used to create a VPC flow logs role.
When you get to the Custom Trust Policy screen click Add next to Add a Principal.
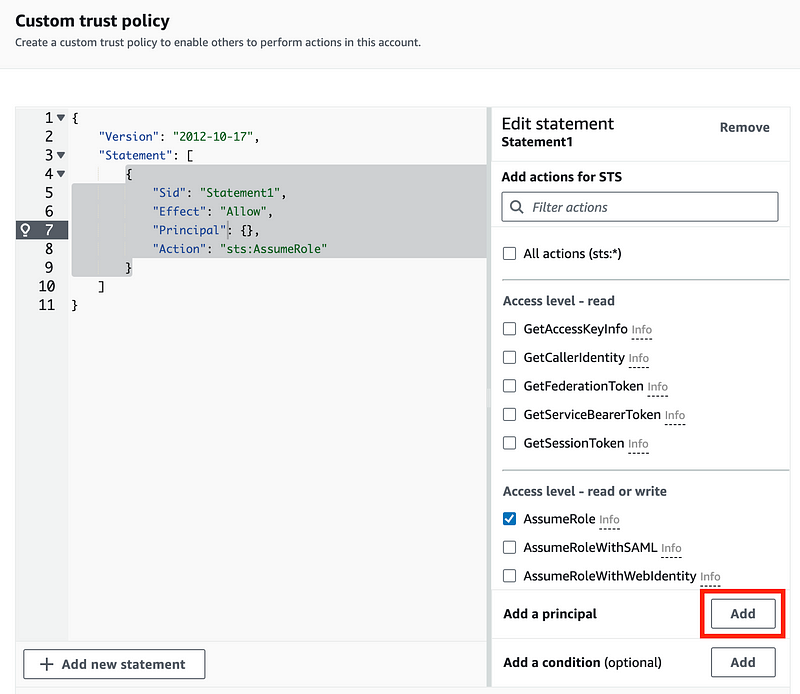
Choose IAM Users.
Replace {Account} with your AWS account number.
Replace {UserName} with the username we created above (pfsense).
Click Add principal.
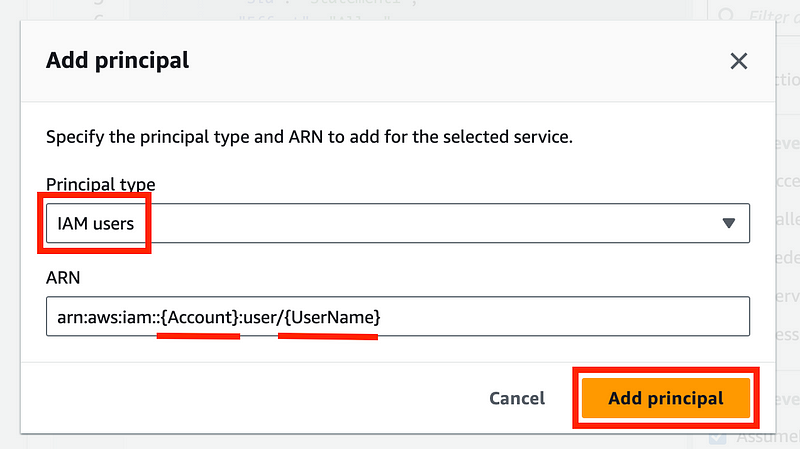
You can get the account number by clicking on the account name on the top right.
Click Next:
Choose the AmazonEC2FullAccess policy and click next.
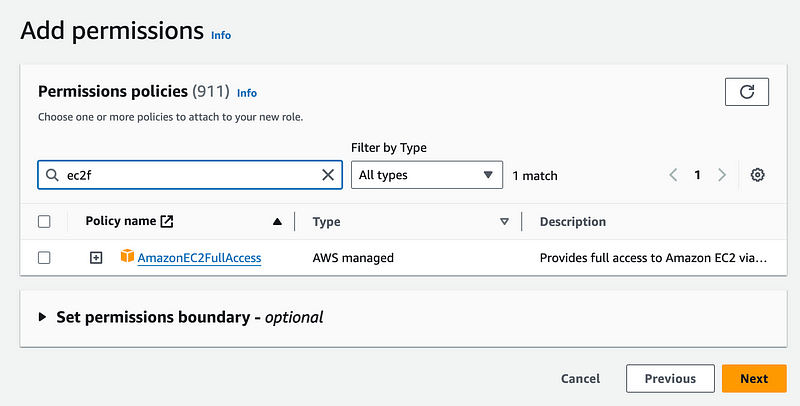
Name the role.
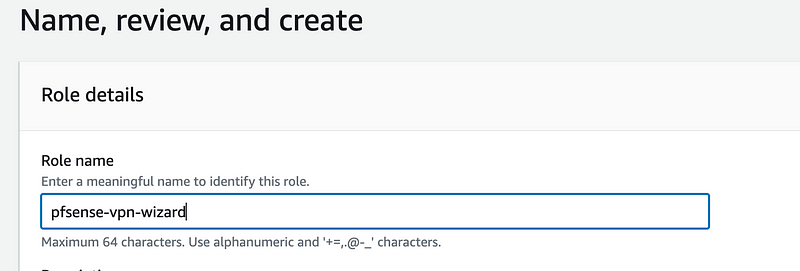
Create it:

Update your IAM user policy so it can assume the role
Click on Users and then your IAM user (pfsense).
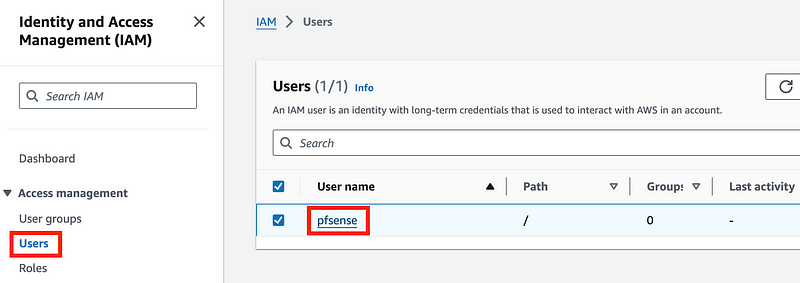
Remove the EC2 permissions:
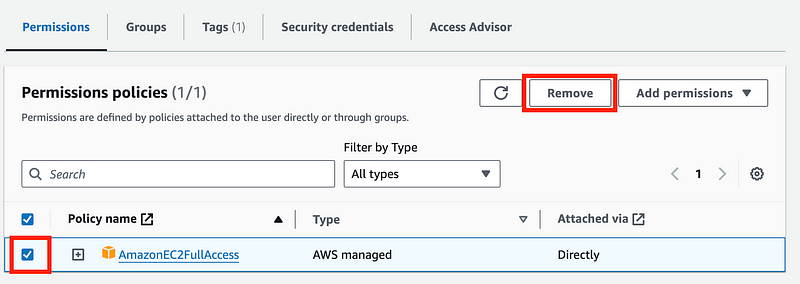
Click Add permissions. Click Create inline policy.
Note: Some best practices suggest not creating any inline policies, however if the policy is only ever going to be created in one place it might be OK. However, best practice is to store that policy in source control of course. This is only for testing purposes.
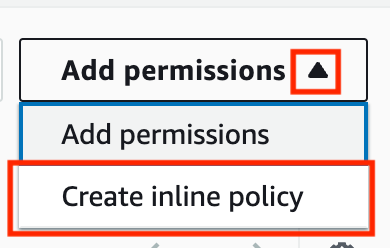
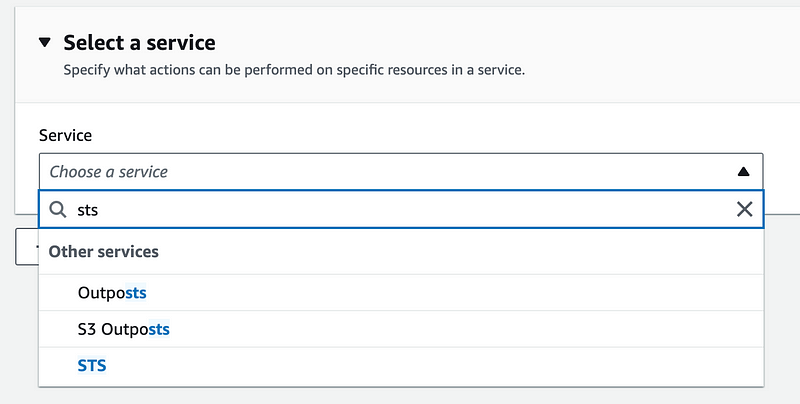
Choose the STS service.
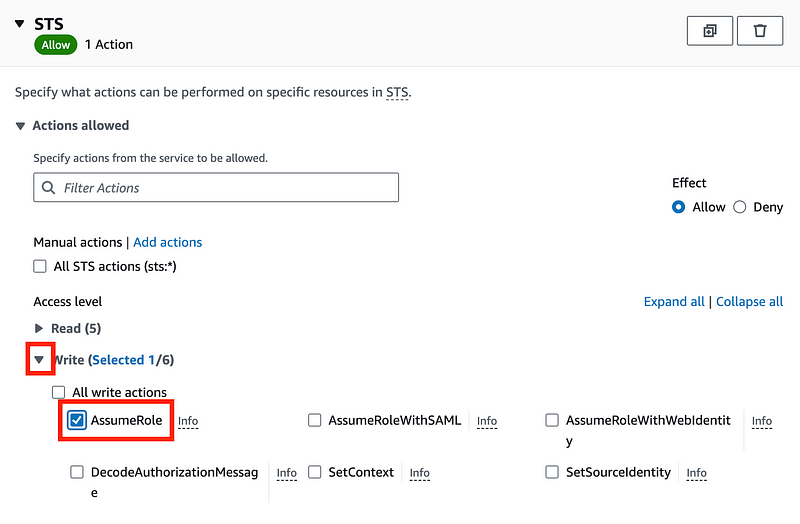
Choose Write and AssumeRole
Under Resources select Add ARNs.
An ARN is a unique identifier for a resource in AWS. In this case, it’s the ID for our role.
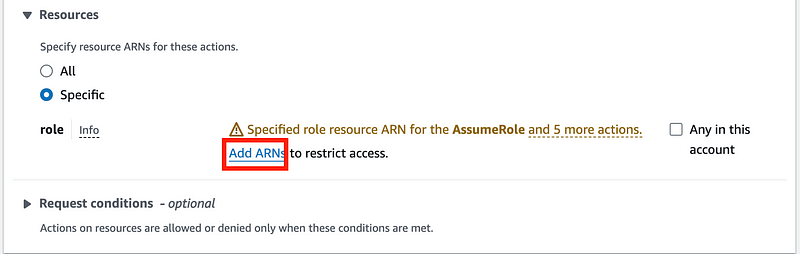
Enter the role name in the top box. Click Add ARNs.
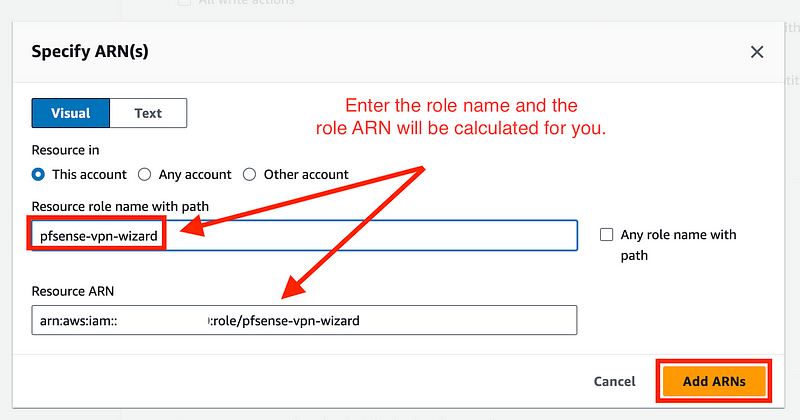
Click Next.
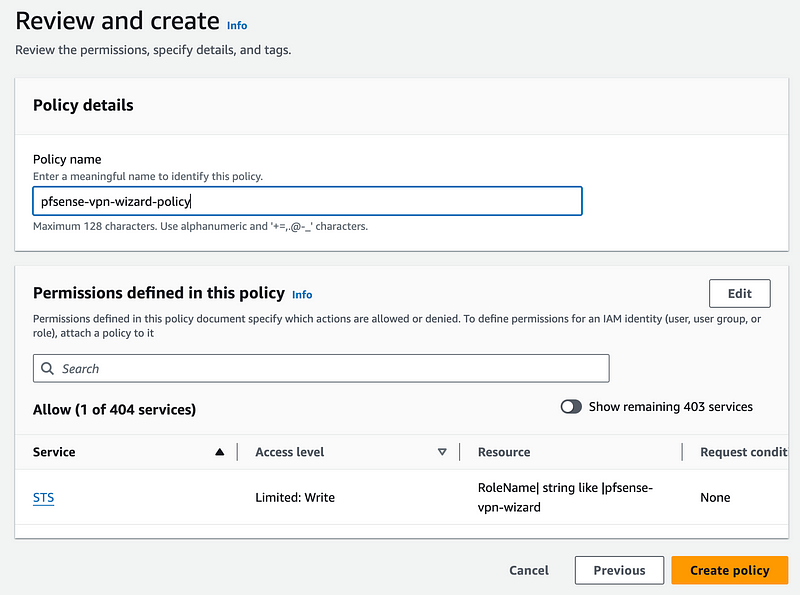
Give the policy a name and click Create policy.
The new policy should be added to your pfsense user.
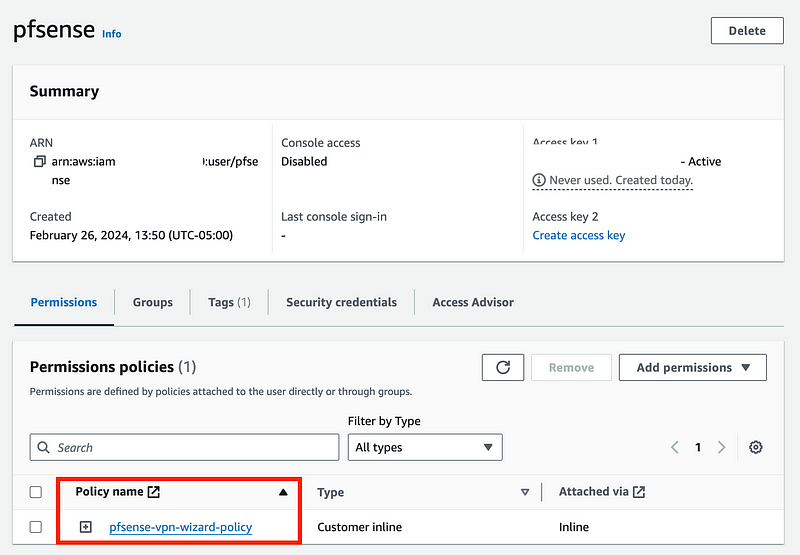
Ok so what did we just do?
- We created a new role that has full EC2 access.
- We removed EC2 permissions from the AWS IAM user named pfsense.
- We added permission for the AWS IAM user to assume the pfsense-vpn-wizard role by granting it permission for the STS service assume-role action.
Again, if you want to know more details about all of that refer to my IAM posts above.
OK now back to the pfSense wizard.
Add the AWS Access Key and Secret key we created above, the ARN for the AWS role, and click Next.
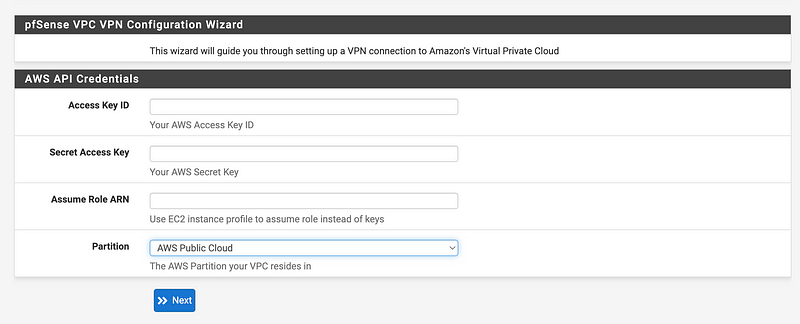
You can find the AWS Role ARN by heading back to your list of roles in the AWS console and clicking on the role we created. And remember I told you to store those credentials in a safe place above. 😊
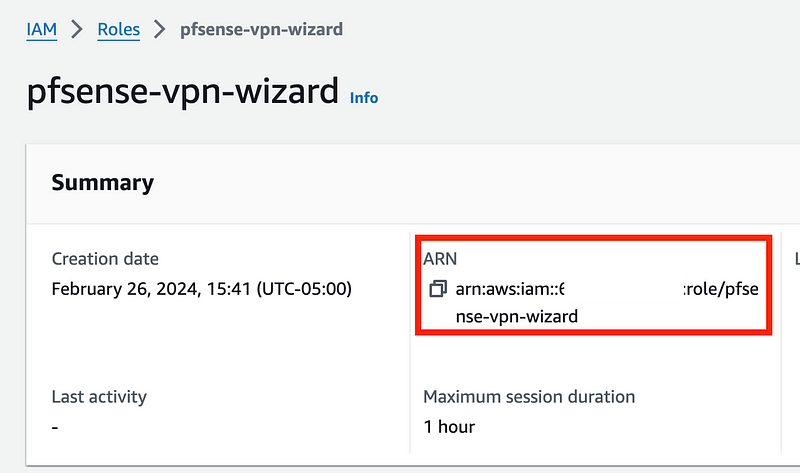
If you get an error that the wizard can’t assume the role head over to the CloudTrail Dashboard.
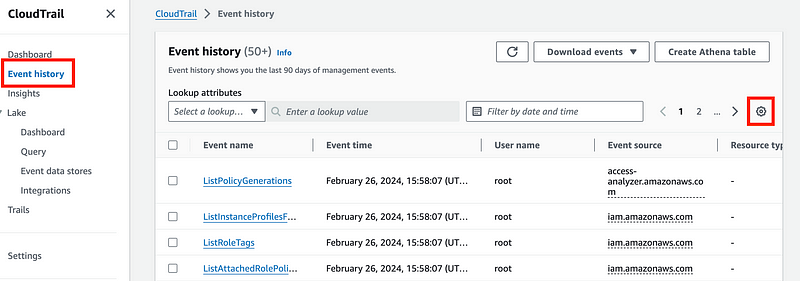
I like to configure it so the errors show up in the list by clicking on the gear and choosing the error column shown below.
Scroll down and look for errors in that column.

You won’t see any read-only events by default. You may have to delete false in that text box and hit enter to see all events.
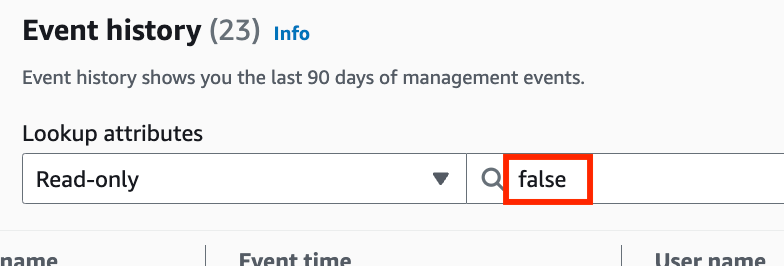
Unfortunately you can’t filter on errors here. That would be really nice. In fact, an errors-only log here would be most helpful. #AWSWISHLIST
You can also search for events specifically for the user name we created. I don’t see any errors here.
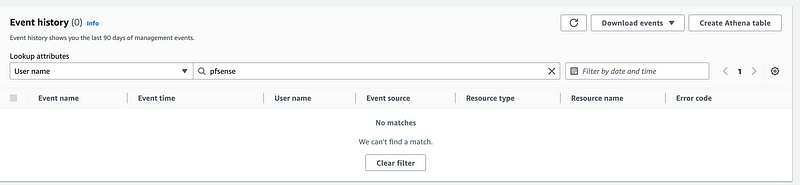
But perhaps we really need to be searching on AWS access key:
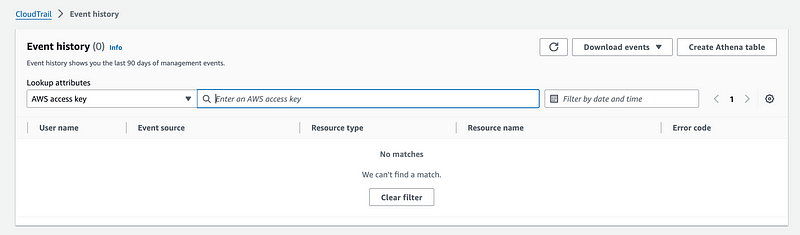
I tried that and still no events. Sometimes events don’t log all the events they should. And sometimes, events don’t get logged at all. Seems that for whatever reason whatever is supposed to be logging this error is not. But we have a clue here where it says Region selection.
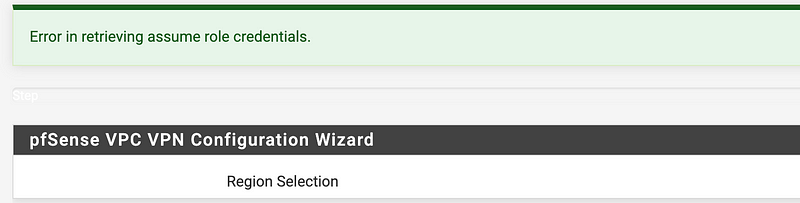
We only gave our user to access STS assume-role. In order to allow it to assume regions we need to grant it that permission.
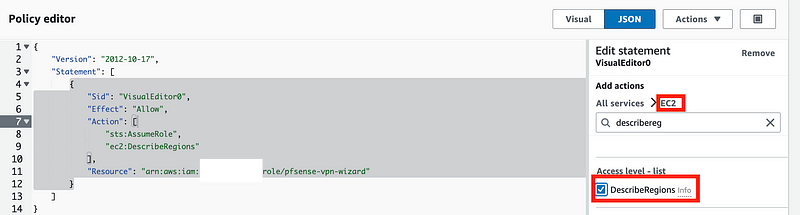
Unfortunately that wizard creates a policy that won’t work. Here’s what the policy needs to look like:
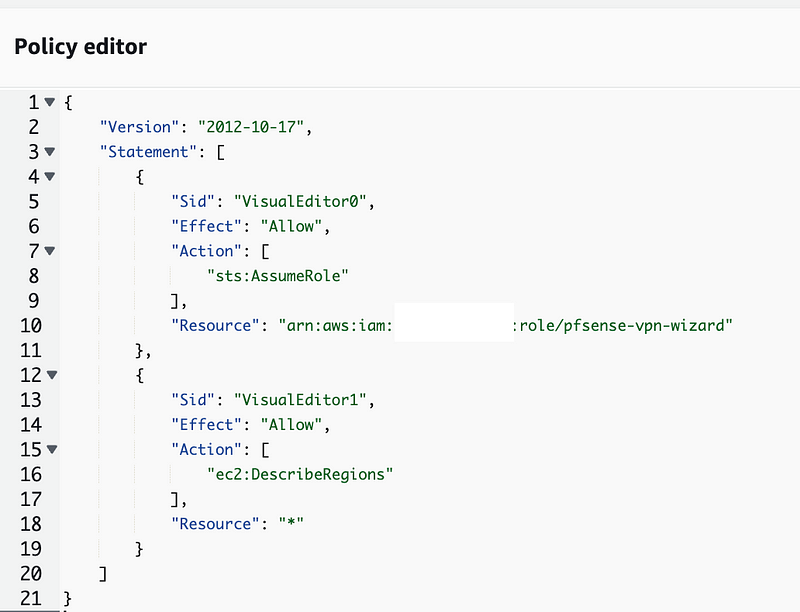
But it still doesn’t work. I checked my pfSense logs and I’m not seeing anything blocked there. If I had misconfigured roles or policies above I should be seeing errors to that effect in my logs above, but I’m not.
The only thing I can guess is happening is that pfSense is attempting to query a region that is not allowed by my organization. I don’t want to spend any more time troubleshooting this wizard so I’m going to try to just configure things myself.
But before I leave this post…I’m going to delete that pfsense AWS IAM User and its credentials.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab





