Why Does Private Networking on AWS Cost So Much?
ACM.341 VPC costs up 2,632% after installing a NAT and VPC Endpoints
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: AWS Security | Secure Code | Network Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I wrote about some thoughts I’m mulling over about batch job security and orchestration.
I moved on to do some non-blog things I need to get done. Related to that, I was just looking at my AWS costs this month and they jumped kind of dramatically. I have a small account and for some larger companies this may be a drop in the bucket, and full disclosure I have some AWS credits. But I am designing now for the day when those credits run out.
~~~
I published a later post in addition to this post that may be helpful on this topic:
~~
So I installed a NAT and some VPC Endpoints. And then I started looking at a Transit Gateway so I can install a limited number of VPC endpoints for my organization and have them shared via the Transit Gateway.
I wrote about how I improved performance by blocking traffic with an AWS NACL and using the above private network and this has been one of my most popular posts lately.
The thing is, I set up the Transit Gateway and never finished deploying it. I wanted to expand on the above topic and write about multi-VPC architectures with shared VPC Endpoints and NATs.
I also looked at a Network Firewall, packet capture, and using that with tools like Zeek, Suricata, or Snort and ruled that out due to the cost.
But I figured the VPC Endpoint I was using was worth the cost and one NAT to reach GitHub, per the example I was writing about.
Once I set up one VPC Endpoint and locked the network down to force traffic to remain on private IP addresses to reach AWS, I realized I had to set up VPC Endpoints for each other service I wanted to remain on a private network. I also had to do that in two separate VPCs, if not using the Transit Gateway.
So just now I looked at my costs and they are up 2,632% as it states in the title above.
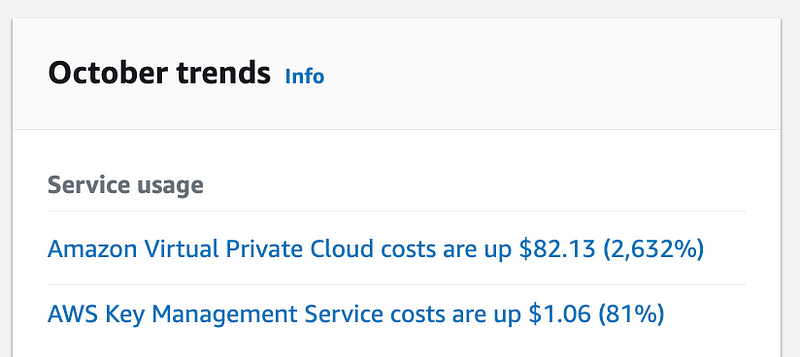
I looked at the details of my VPC costs and you can see below that a bunch of it is coming from the resources I mentioned above — the NAT gateway, a Transit Gateway that is not even in use, and the VPC Endpoints.
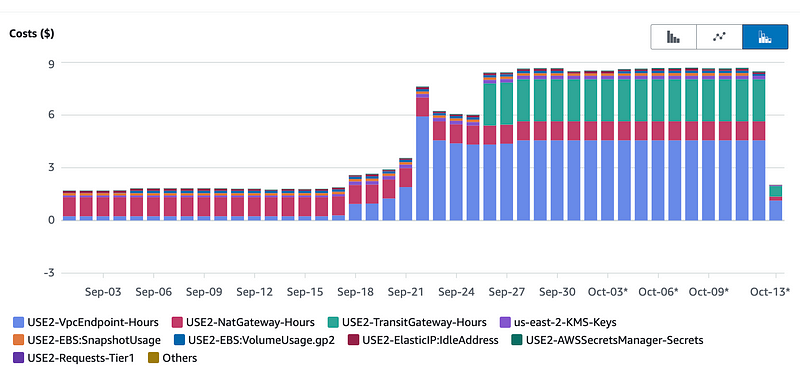
I immediately deleted the Transit Gateway because I’m not using it and now not sure I will. I also wonder — why do all these resources cost so much? Networking is free on AWS such as VPCs, Subnets, NACLs, and Security Groups.
Why is setting up a private network so much more expensive? A private network should benefit AWS in helping customers create more secure environments and as a result, have less AWS data breaches in the news. Private networks may lead to better performance for all AWS systems due to less rogue traffic hitting so many different endpoints. It seems like AWS would want to encourage and facilitate this practice with lower costs and ease of deployment.
The one thing I would really like AWS to do is to give you an option to flip a switch and just keep all traffic to services private, instead of having to install a separate endpoint for each individual service. It’s time consuming, error prone, and apparently costly depending on your budget. I still want to set up different security groups allowing different compute resources to reach different services. But isn’t there an easier way like configuring a single endpoint or resource and checking off all the services you want to allow through it instead of configuring them one by one?
It seems like making this cost less and easier would help customers stay secure more easily on AWS and possibly win AWS some business. Change for the compute resources, not the networking. I don’t know why this type of networking is so much more than other networking and other services that are free. I’m sure there is a reason but I hope AWS can somehow work this out.
I also had challenges getting the Transit Gateway working at all and submitted some feedback on the website. I never finished it because there’s always a million things to do, but I think that process could be simplified to make it easier for customers to create secure and efficient networks on AWS.
The network security concepts on AWS are really cool and if I have the budget, I may write more about that later. It’s just the cost and the challenges to implement it that are holding me back at the moment when it comes to some of the network security features on AWS.
Keep costs aligned with usage — a key tenet of the AWS pricing model from the start, that makes the service viable for businesses of all sizes.
As you can see in this graph, the networking costs are not at all aligned with my usage on the platform.
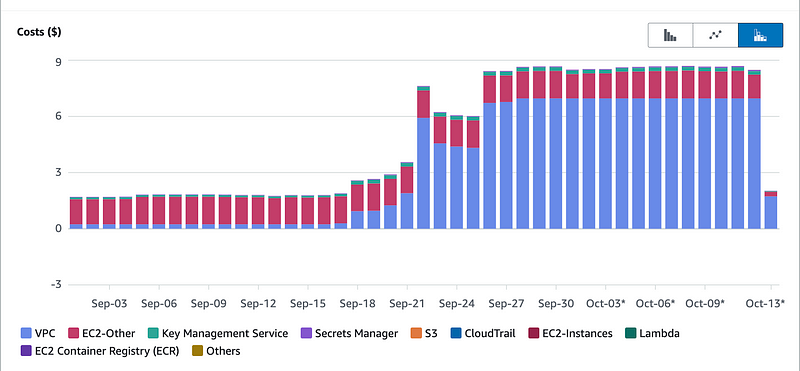
#awswishlist
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab





