Using the Security Automation Framework with Your Own Code
ACM.211 Leveraging scripts from the ACM framework with your own code
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Part of my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: GitHub Security | Application Security | Secure Code
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Each organization is different and may have it’s own organizational structure that does not align with what I’m creating. Alternatively maybe you want to use what I’m creating as a base and extend it. Perhaps you only want to use certain pieces of the code.
Simple.
Download both the repository with your custom code, and the repository I’m creating.
The same way that I’m referencing code in different folders, you can then reference the code from the two different GitHub repository folders.
For example, 2nd Sight Lab performs cloud and application penetration tests and cloud security assessments for customers. Your company may not do that. But since I have this specialized type of work and I want to ensure work for one customer does not affect another, I create completely fresh infrastructure for every client.
I don’t want to include that in the base framework as that is organization specific. I can download both my repository I use to build out the penetration test infrastructure and the repository I’m building in this post.
My directory structure cloud look like this with each directory in the /home/ec2-user directory:
/pt
/SecurityMetricsAutomationI can create a deploy.sh file in the root of the pt directory.
Then I can create a new account for a penetration test in my penetration test infrastructure repository by referencing the code in the other directory like this:
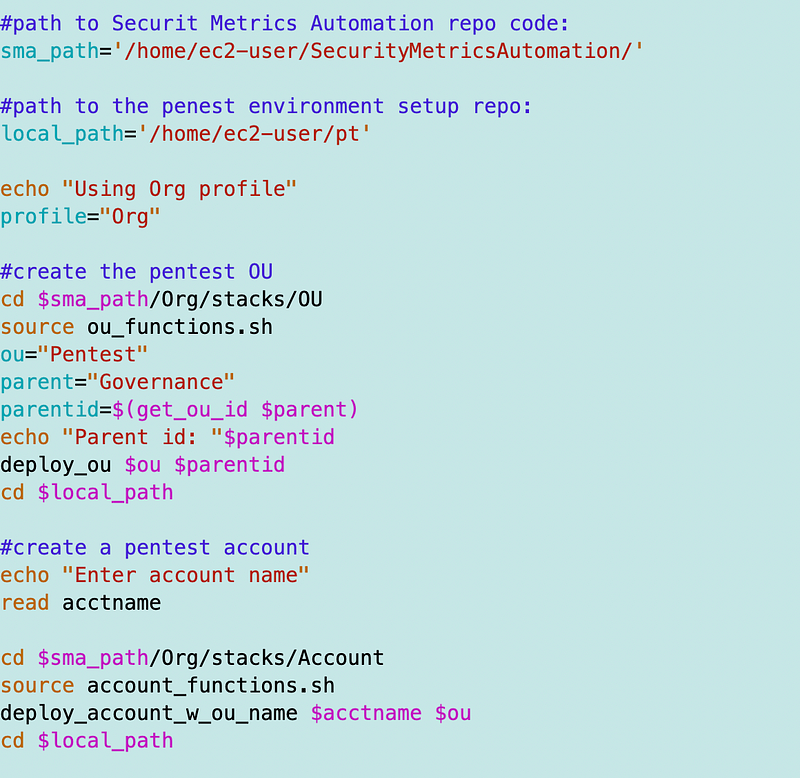
In fact, I’ll later probably split out different directories in my current repository into separate repositories owned by each role that is allowed to use and modify that code. Thankfully GitHub now has fine-grained access controls (as of October 2022) so you can easily limit a particular role in your organization to a particular repository.
Use fine-grained access tokens to limit the damage should someone get access to one of your tokens — ensure it doesn’t provide access to every repository in your GitHub account.
Now you see how to use my code without using all of it if you don’t need it all. You can leverage the parts that work for you. Of course I’m always changing it and potentially breaking it so you should probably make a separate copy of it and not run it directly in production without testing each update first in an alternate environment.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
The best way to support this blog is to sign up for the email list and clap for stories you like. If you are interested in IANS Decision Support services so you can schedule security consulting calls with myself and other IANS faculty, please reach out on LinkedIn via the link below. Thank you!
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
Author: Cybersecurity for Executives in the Age of Cloud
Presentations: Presentations by Teri Radichel
Recognition: SANS Difference Makers Award, AWS Security Hero, IANS Faculty
Certifications: SANS
Education: BA Business, Master of Software Engineering, Master of Infosec
Company: Cloud Penetration Tests, Assessments, Training ~ 2nd Sight LabLike this story? Use the options below to help me write more!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Clap
❤️ Referrals
❤️ Medium: Teri Radichel
❤️ Email List: Teri Radichel
❤️ Twitter: @teriradichel
❤️ Mastodon: @[email protected]
❤️ Facebook: 2nd Sight Lab
❤️ Threads: @teriradichel
❤️ Bluesky: @teriradichel
❤️ YouTube: @2ndsightlab
❤️ Buy a Book: Teri Radichel on Amazon
❤️ Request a penetration test, assessment, or training
via LinkedIn: Teri Radichel
❤️ Schedule a consulting call with me through IANS ResearchMy Cybersecurity Book: Cybersecurity for Executives in the Age of Cloud

