Using Personal Access Tokens With A GitHub Organization
ACM.478 If you are using a personal access token a GitHub organization can help you manage those tokens more securely.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Application Security | Secure Code | Github Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I wrote about setting up an organization and an enterprise in GitHub.
Now I’m going to explain how to use personal access tokens in an organization if you are doing that. Whether or not you should be using tokens is a discussion for another day. I hope to be trying out some other options in future posts as time allows.
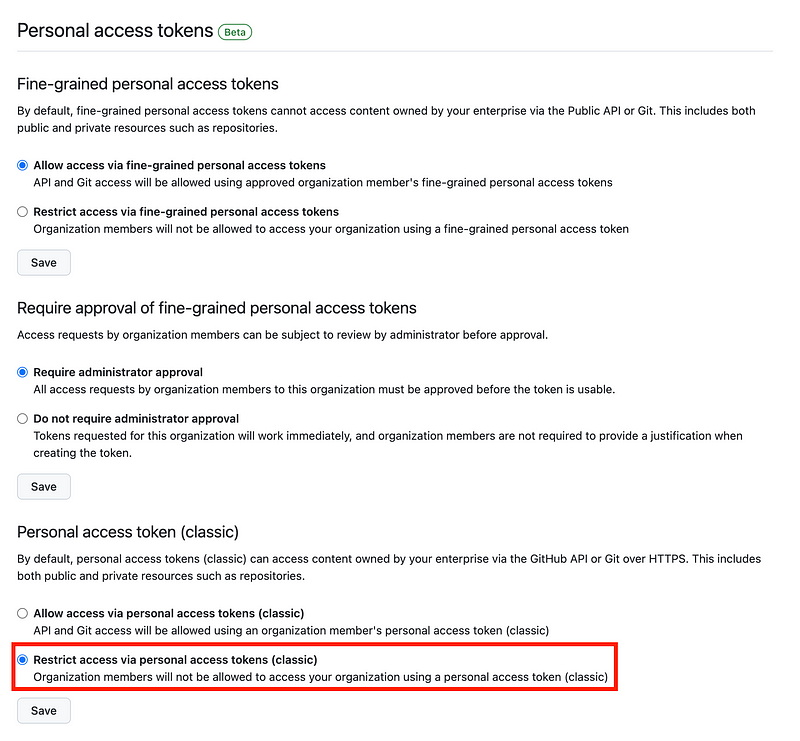
In order to use personal access tokens with an organization, you first have to click on personal access tokens on the left. Then you have to enroll in that functionality.
Restrict use of classic personal access tokens which are not fine grained tokens.
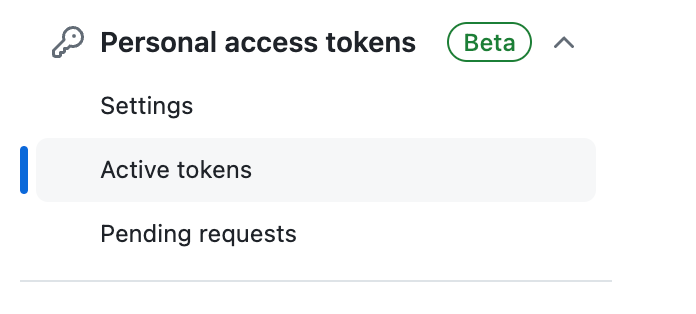
Click on Active Tokens in the settings menu for your organization. See the prior post for more on GitHub organizations and enterprises if you’re not familiar already.
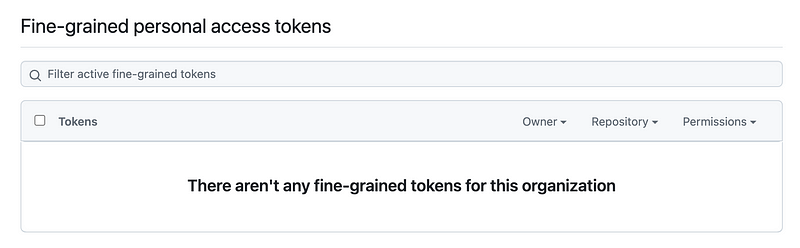
Initially there are no tokens here and no way to create them. They need to be created by a user.
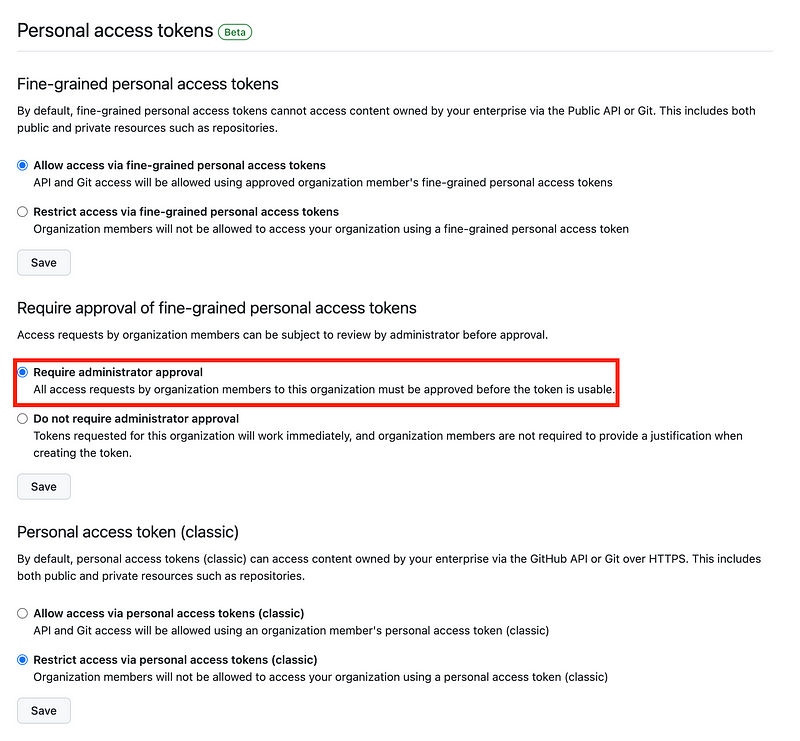
As you can see above I require an administrator to approve them when created.
Now what I can do is create a user that only has access to my test repositories not my production repositories, even if the user has access to all of them.
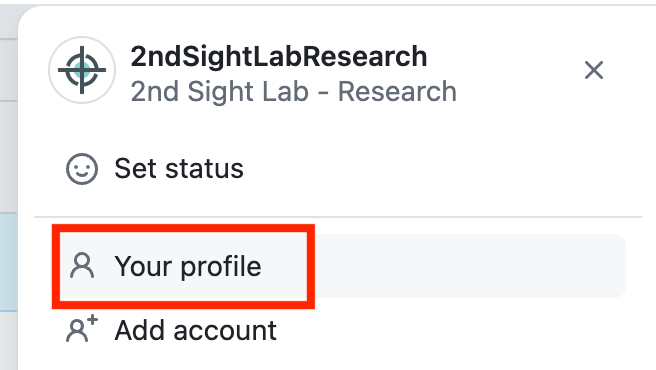
Click on your user on the top right of the screen.
Click Your profile in the menu.
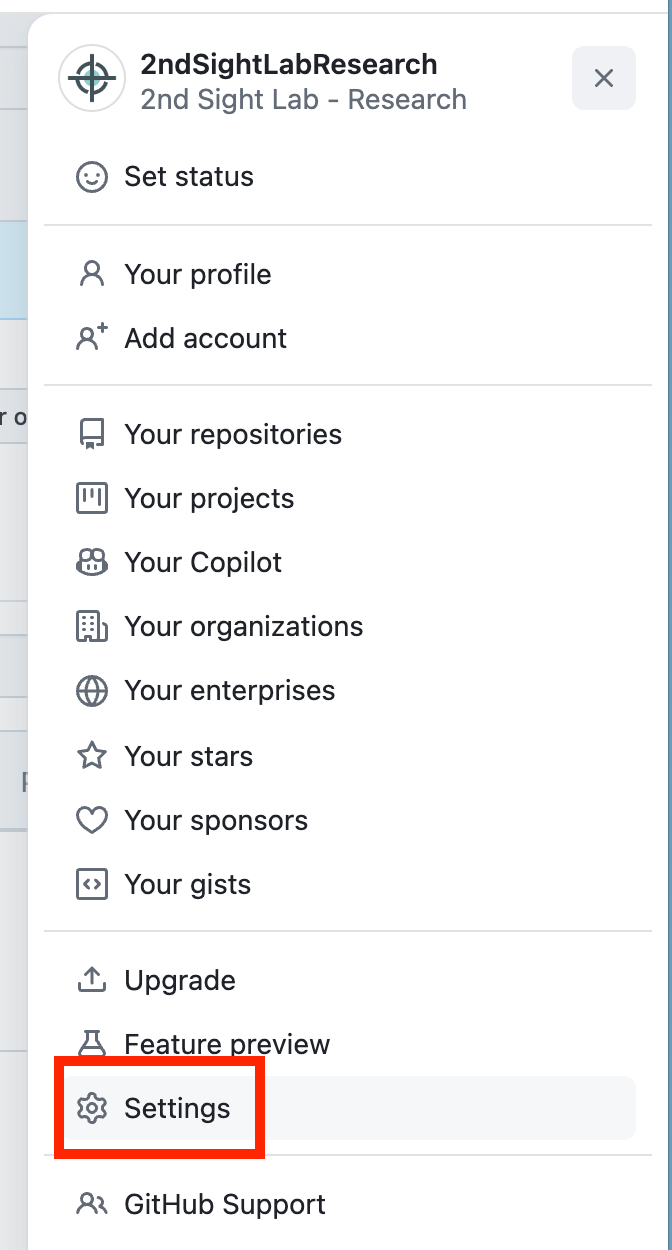
Click on Settings.
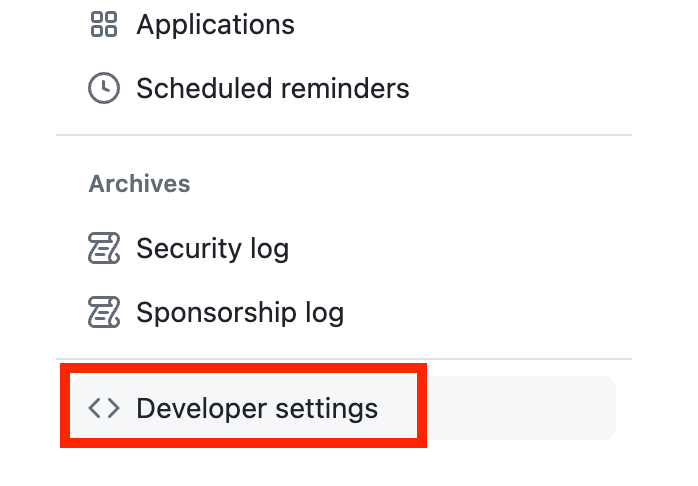
Scroll down and click on Developer settings.
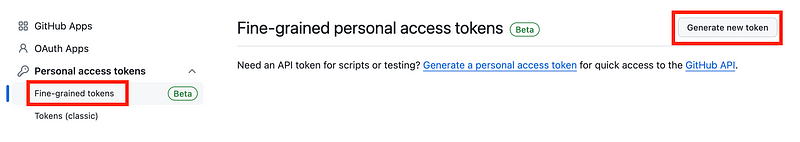
Generate a new fine-grained token.
Choose your organization.
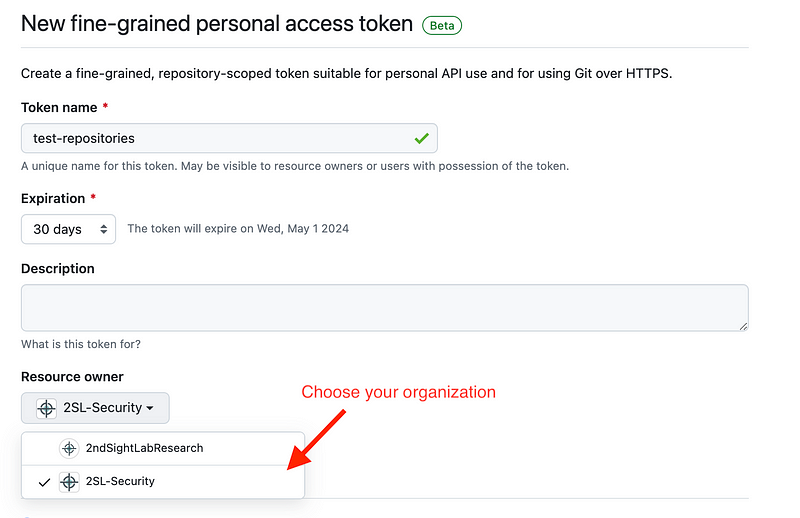
Once you do that you can limit the permission to select repositories and actions.
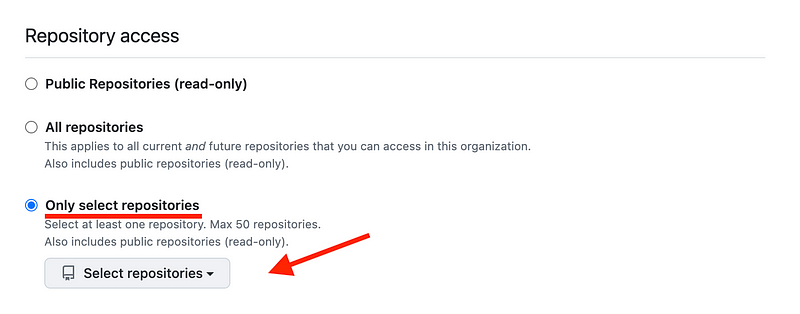
I’ve written about limiting permissions in other posts.
In this case, I am going to limit permissions to my test repositories only and not grant the token that is developing the code permission to access the public repositories.
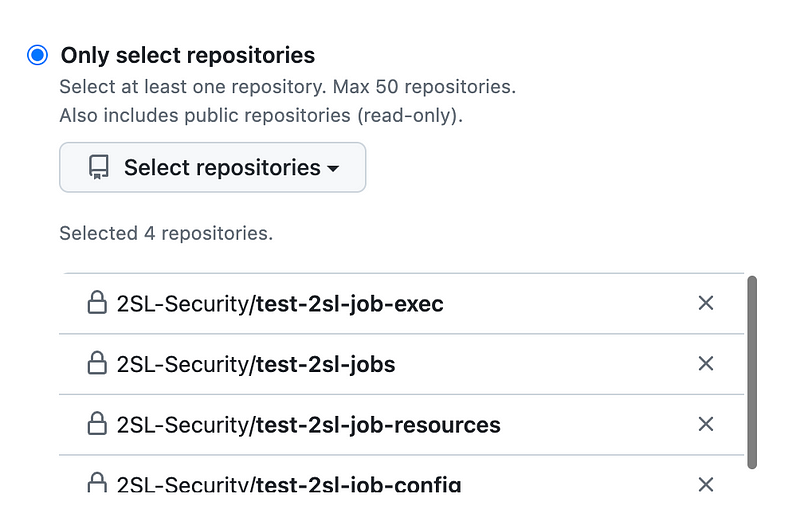
Next under permissions I can specify which actions I want this token to be able to perform. Note that I was very confused once when adding repositories and failed to select any permissions and the repository never got added to my account even though there was no error message telling me I did anything wrong. Make sure you select some permissions.
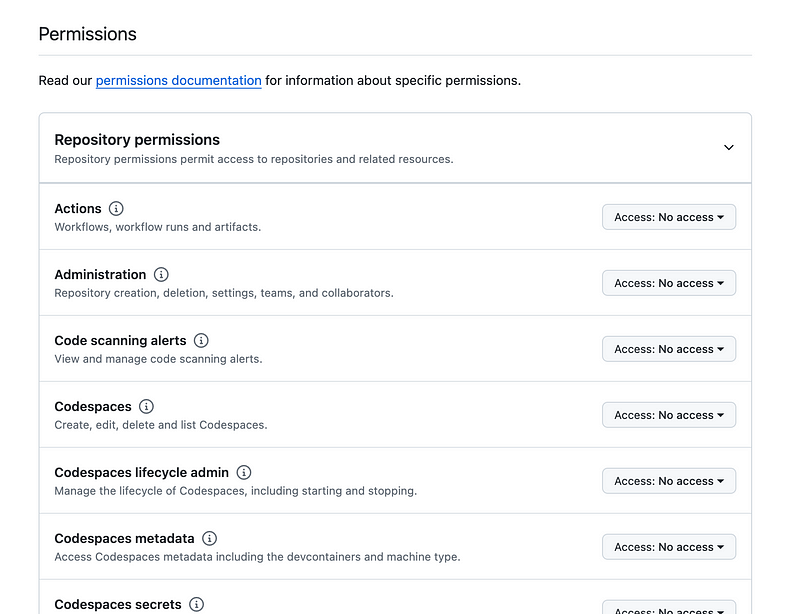
There’s also a section for organization permissions which you can configure if you are allowed to perform these actions.
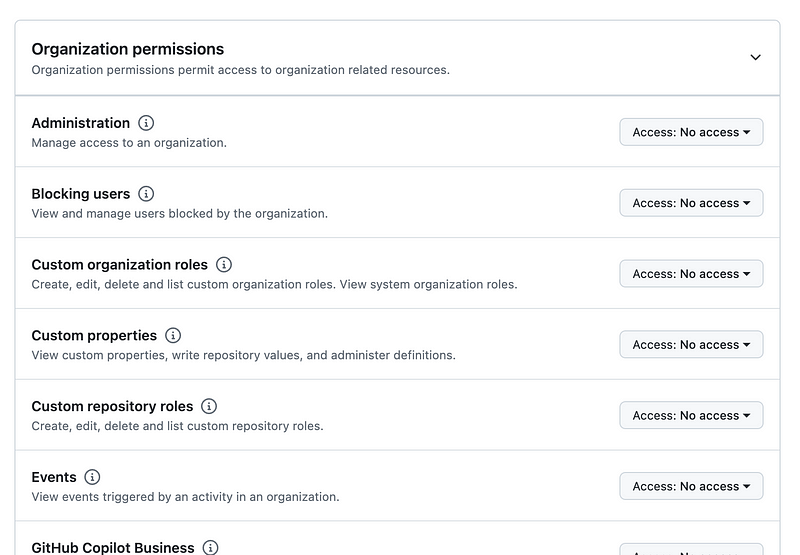
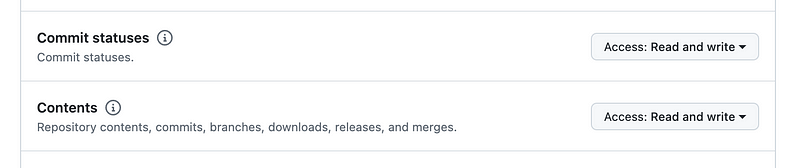
To develop code I only really need these actions:
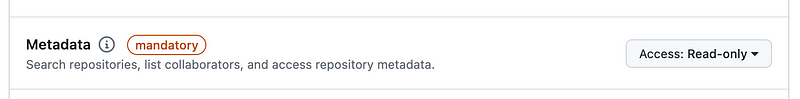
The metadata action is required by default.
You may need other things depending on what functionality your organization allows, uses, and your particular responsibilities, but if you are using a token only for working with code, limit your token to that. Create a separate token with no access to edit code but that has access to do other things if required that can be used for automation.
Click Generate token.

You’ll see a token below. Make sure you copy it and save it somewhere safe as you won’t be able to see it again once you close this screen.
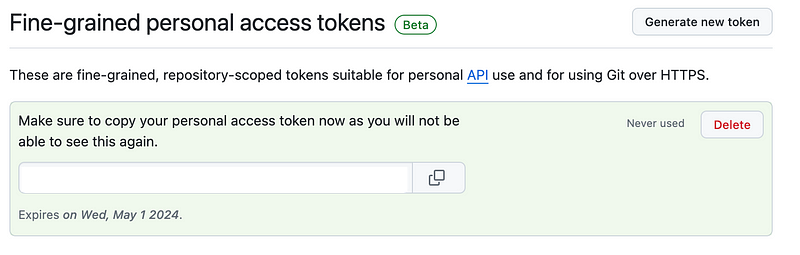
The best thing to do is put it in something like AWS Secrets Manager and use it from there as I’ve written about before in other Git and GitHub posts which you can read via the above link.
Return to the organization settings and click on Personal Access Tokens. Now you can see the token I just created as a user.
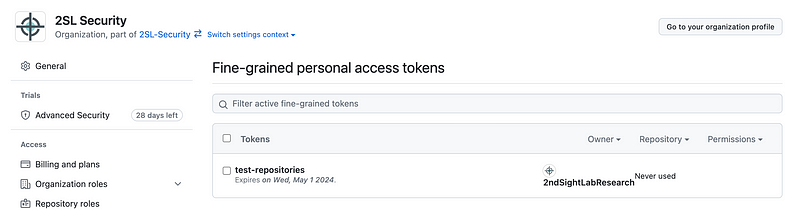
If I was not an administrator then an administrator would have to authorize this token before I could use it. You may want to have separate people authorizing tokens from those who can use the tokens. I always try to design security so the person granting the access is not the one using the access to help make it harder for an attacker to have access to all the things.
You can click on the token, see what access and permissions the token has, and revoke the token if needed.
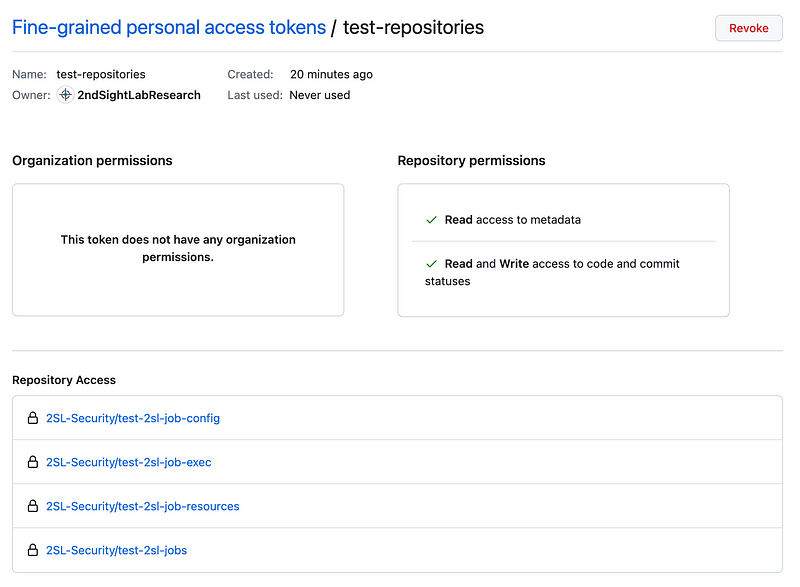
Of course you might want to automate some of this token evaluation with a script so you can easily find excessive permissions or scour the logs for sensitive actions at unexpected times or from unexpected locations, for example, possibly with the help of canaries.
One of the best sources to explain what canaries are is a company that specializes in services for creating and monitoring them. I saw the founder of this company speak at BlackHat one year and was very impressed, though I haven’t used the service.
Canaries have helped uncover some major breaches. Maybe a topic for another post later.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2024
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
