Security Flaws Due To Incorrectly Imported Libraries
Investigating why an import of boto3 throwing an OpenSSL error and pondering the implications
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Application Security | Secure Code
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I’ve had some strange problems with some code I wrote for Python that now longer works for some reason. I wrote a long post about troubleshooting that problem and how I ended up reading about differences in package precedence in Python 2 and Python 3 here:
The post is long and wandering but I want to sum it up for you.
If you have two packages with the exact same name on your system, you may think you’re running one of those packages in your program when you’re actually running a different one. The incorrect package may be malware placed onto the system or it could be that the system is just configured and pointing to an different, possibly vulnerable version of code.
I was troubleshooting just such an issue which results from this problem.
- I was using some code that was using a file in my program called ipaddress.py.
- My code was also referencing some of the code in the default ipaddress.py file that comes from Python.
- I got an error because my application was looking at the code in my own file first and erroring out because it needed some code in the ipaddress.py file that comes with Python.
- I forgot that I had this local file so I copied the file from Python over the top of my file. At that point my program successfully ran past the error that was due to not referencing the default file in Python.
- However, then my code failed when it got to the point where it needed the custom function in my own code that I inadvertently deleted.
- To fix the problem (which I’m not saying is the best solution) I overwrote my local file with the default file and added in my custom function.
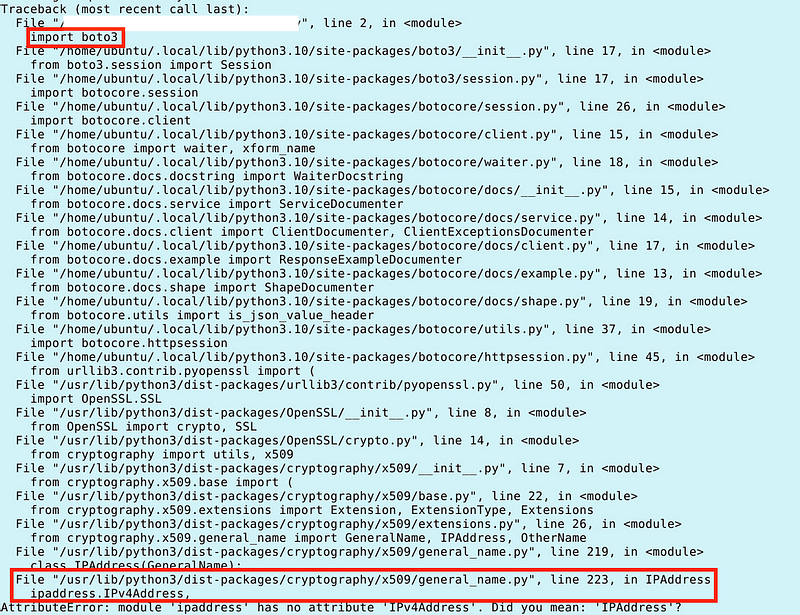
Why does boto3 import cause an error when I create a local ipaddress.py file?
The strange thing is that when I was referencing the default ipaddress.py file from Python, the error I got was triggered by the import of boto3.
So boto3 is using and expecting that default Python ipaddress.py file. But the weird thing is, the error I got was ultimately in OpenSSL.
Think about this for a minute.
When I overwrite a file in the standard Python library with a local file in my application, I am affecting the behavior of OpenSSL — a cryptography library — via a boto3 import.
Hmmmm.
Error related to OpenSSL used in Boto3 when I include a local ipaddress.py file
If you are using OpenSSL and boto3 you should probably explore this further. I’m not going to at this time. I need to deliver a penetration test report at the moment.
How to determine precedence of packages
Determining which packages and modules in your Python applications are taking precedence is a bit complicated:
By the way, the above documentation says it relates to Python 3.3. You always need to understand the precedence for the specific version you are using. It seems to me that precedence from Python 2 change in Python 3 to a mechanism that does not align with the code I’m running in Python 3.10 on an AWS EC2 Ubuntu instance — but to be honest I read it quickly and have to get some other things done. I have ensured that in my case, the code I need is coming from expected packages.
How to verify the precedence of included packages matches the documentation
I wrote about how I was trying to figure out which packages my program was expecting and which packages it’s actually gettig in this post — but it seems to mostly relate to Python2 after further investigation.
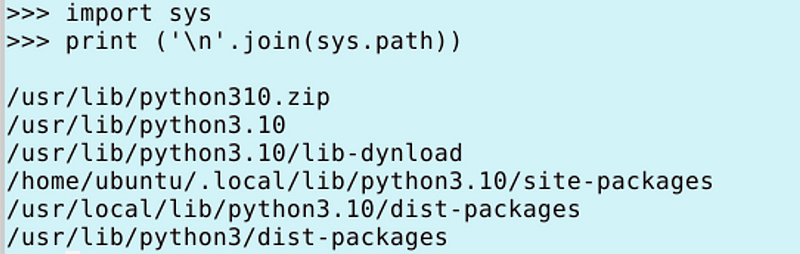
You can print out your syspath this way — this is where Python will look for files.
You can look up all the instances of a file using locate. I showed how to install that in my earlier Ubuntu post:
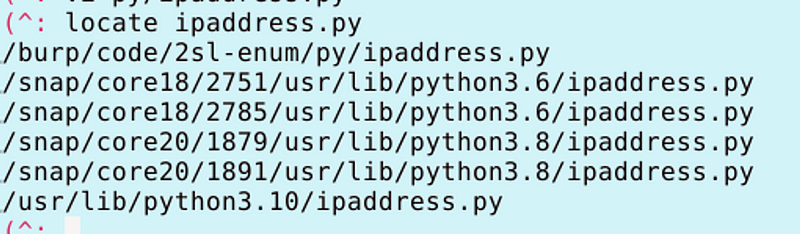
Note that the locate results may be cached. I deleted a file and it still showed up. You can update the cache with this command:
sudo updatedbWhich one is it using? Follow the rules of precedence to figure that out. Or just throw errors in each one one at a time until you figure out which one the applications is using.
😁
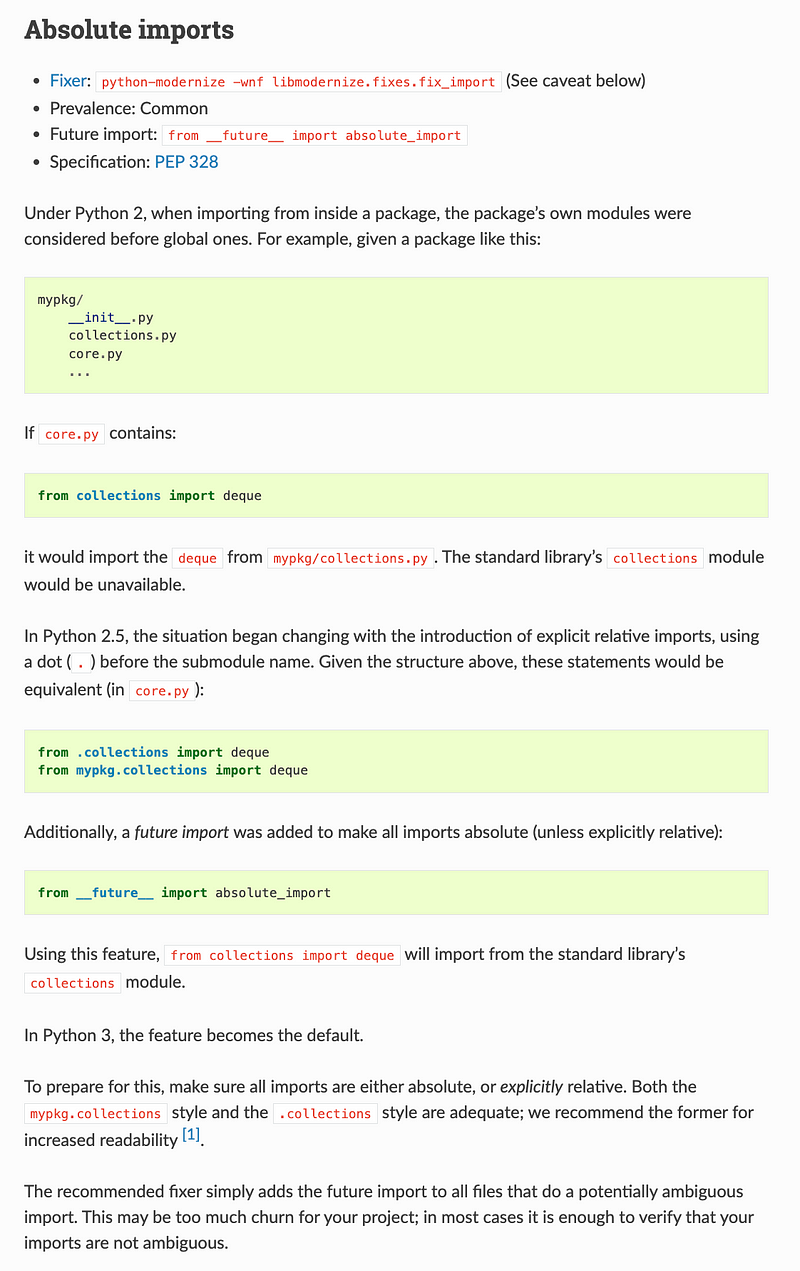
The other interesting thing is the way the Python default packages are included or not in various versions of Python. This is good to understand:
How can misaligned packages be exploited?
Someone with deep knowledge of this could probably do you some harm and go unnoticed when QA is testing and things “just work.”
Let’s say an attacker knows that if they put a package with a specific name in just the right location, it will be picked up in favor of the correct file. They don’t replace the root Python file. They don’t replace the file in your local application. They insert the file in some other location in the Python system path. They slightly modify the code so that it doesn’t trigger any alerts in vulnerability scans. It may just do something like send your data off to some other location when the code runs.
How would you find this? Know what applications are sending data from your systems. Make sure they are only sending data to valid locations. Create zero trust networks and make sure that you don’t allow outbound traffic if you don’t need it.
Oh and, understand package, dll, or jar precedence — or whatever programming language you are using and whatever it’s library construct. Make sure your applications are running the code you think they are. You may have heard the term “DLL Hell” in reference to Microsoft applications, for example. Same problem, different platform and programming languages.
Here’s my Python wishlist. Or any programming language for that matter. I want a command that I can run that shows me every module used in a program and the path the program uses to get that module. I’m sure something like that probably exists somewhere. But I want it to be a simple line of code I can execute in a Python program that spits out those details. Then I can verify that each module used in the program is coming from the expected location.
If you are working on any code involving OpenSSL with python or boto3, I suggest taking the time to make sure the files are coming from expected locations.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
