Safer Network Scans
Using a zero trust model for security scanning software
Related: Solar Winds Breach | Penetration Testing
This is my random thought for the day as I wrap up a penetration test. I love the granularity you can get with cloud networking and the details you can obtain to perform a safer penetration test on AWS.
The first thing I do before I perform network scans is to run a query of all the IP addresses in the AWS account I’m testing. That includes IP addresses for Lambda functions, NAT instances, etc.
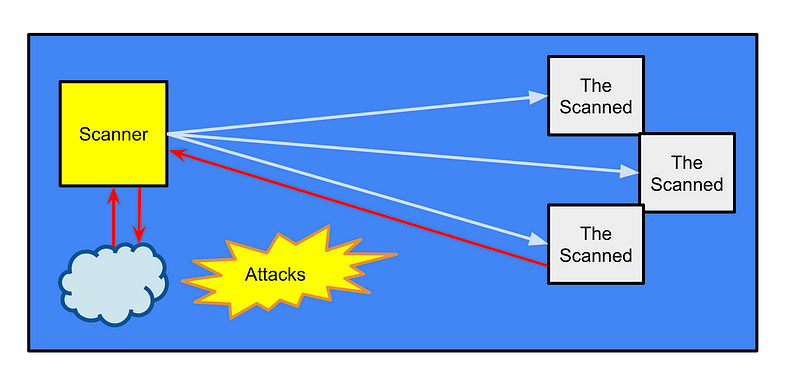
Once I have all the IPs I can construct a very specific network for an NMAP scan to scan any port and IP without exposing my scanner to the entire Internet for all those IPs and ports.
You can create a NACL that allows inbound and outbound for any traffic to or from any in scope IP address plus inbound and outbound for your remote access to your scanner on the specific port and protocol you use to access the scanner.
If you stop there, any compromised hosts in the network you are scanning may be able to attack your scanner and a compromised scanner can attack your remote access host potentially. So don’t stop there.
The next step is to create a security group that only allows your remote IP into your host and allows outbound only to the IPs you are scanning.
Let’s say one of the hosts you are scanning is compromised. Well, it can’t initiate traffic through the security group to your scanner, even though you’ve allowed all inbound and all outbound through your stateless NACL. If you stopped there, the hosts you’re scanning could turn around and attack your scanner using the inbound traffic rules and exfiltrate data out, for example.
However, when you add the security group:
- The scanner can initiate traffic to the hosts it is scanning but not to any other host on the Internet, including the one you use to connect to the scanner.
- Let’s say the scanning software is compromised and scrapes credentials. How is it going to get those credentials out to some other host? It can’t initiate traffic out of your scanner to send the credentials to some attacker controlled server. Anything is possible, but you’ve made it pretty difficult and limited the ability to steal credentials off the scanner such as was the case in the Solar Winds compromise.
- No host on the Internet can connect to your scanner to try to compromise it, such as is occurring in these attacks:
- Your scanner cannot initiate traffic back to your host that is connecting via remote access software. If you use some sketchy, often compromised method of connecting from some open source software site then you are opening yourself up to more potential attacks. But if you use a client from a reputable software vendor that frequently updates and patches security flaws and secure crypto (I wrote about some issues with xrdp lately that I need to address in more detail) then you have a better chance of avoiding that problem.
- Since having some issues with xrdp I have resorted back to SSH and Linux for all but the scans that require a GUI and I’m thinking about further limiting GUI scans in the future using Burp in headless mode.
Yes, there are probably some crafty ways to have a response do something funky that gets into your scanner through some software flaw, if there is one, and then try to go back out using some netcat pipe crazy thing. But it’s not going to be simple. And if the only thing running on that host is a scanner and it can’t reach anything else in your network the blast radius is going to be very limited.
Why the NACL? Drop those extraneous packets immediately without any state analysis. Save all the systems involved some processing power. AWS is the only major cloud provider with a stateless networking option.
The NACL won’t help though when you want to know who initiated the connection. That’s when you need a Security Group — to define which systems can initiate traffic to another system within the scope of the hosts that are allowed to communicate. Some state analysis is required.
NACLs also have deny options which security groups don’t and that can help in other scenarios but was not needed for this one.
The other thing is, I am now not simply relying on one security control. I have two in case something is misconfigured or breaks in the future with one or the other.
“But wait. My scanner has to connect to the cloud”, you say. Well, good luck with that. I know a lot of people are doing it but I don’t use scanners that work like that on penetration tests. I use them for my own systems in limited circumstances, such as simple vulnerability scanning on GitHub and tools that operate within a specific cloud network. But some people have a different risk appetite. I like to keep things as simple as they can be, while still getting the job done.
Of course, if you’re running a scan that involves connecting to cloud services to check their configurations you need to open the network for that too. This is where I wish cloud providers would make it easier by giving you a prefix list for all cloud services, for example, in any region, or a specific region. Without having to track and spell out every single CIDR block to prevent non-cloud network traffic.
Anyway, random thought for the day. I have on my list to write more about those crazy netcat attacks and similar at some point as I want to play around with them in more detail. For now I’ve got other things to finish.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
