Remove extraneous VPC route tables
ACM.62 Eliminate unnamed and unnecessary route tables and set the main route table after deploying an CloudFormation VPC stack
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | Network Security | Cloud Security Architecture
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In my last post I explained how creating route tables for VPCs with CloudFormation does not allow you to override the main route table. What you end up with is a route table with a name you want and an extraneous no-name route table.
In this post I explain how to automate removing the primary route table so you are only left with your named route table associated with our VPC.
Should You Call Functions in CloudFormation?
There are other methods to fix this problem besides what I am going to show you. You can create a Lambda function and call it — but I personally don’t like adding executable code to what is supposed to be a description of resources so I have yet to add a custom function to a CloudForamtion template. CloudFormation is more like data or configuration. It is used by executable code but it does not, itself, execute or trigger executions. I like to keep data or configuration and executable code separate. Ideally AWS just fixes this, but there are gaps in CloudFormation here and there and we have to find a work around.
Although I can manually fix it, it causes problems due to CloudFormation drift. You should manually delete any route tables prior to trying to delete the CloudFormation stack if you take this approach.
Replacing and deleting the main route table
We can fix this problem with a few CLI commands (or we could use Python later in a batch job) with the replace-route-table-association CLI command.
We’re also going to need to get our VPC ID:
And then get our main route table ID and the ID of the route table we added to the VPC:
The we’ll delete the main route table (as long as it’s not already set to the correct route table).
I added a new function to my network_functions.sh file:
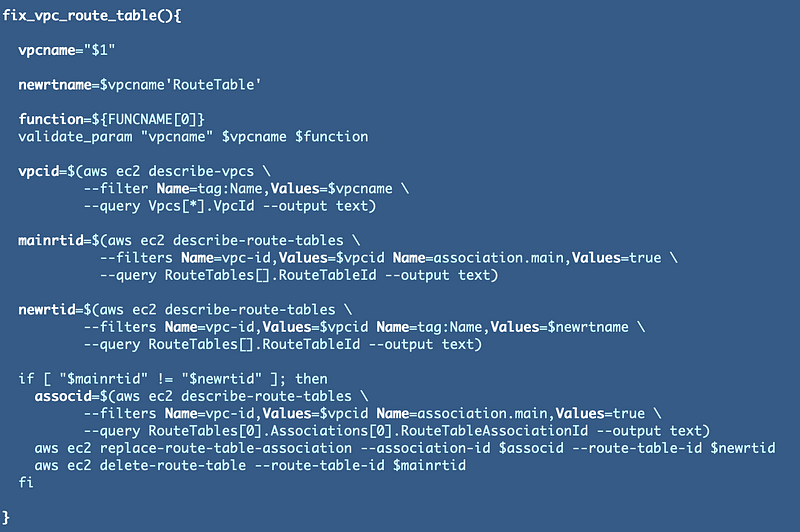
Then I added a call to this new function to the end of the deploy_vpc function:
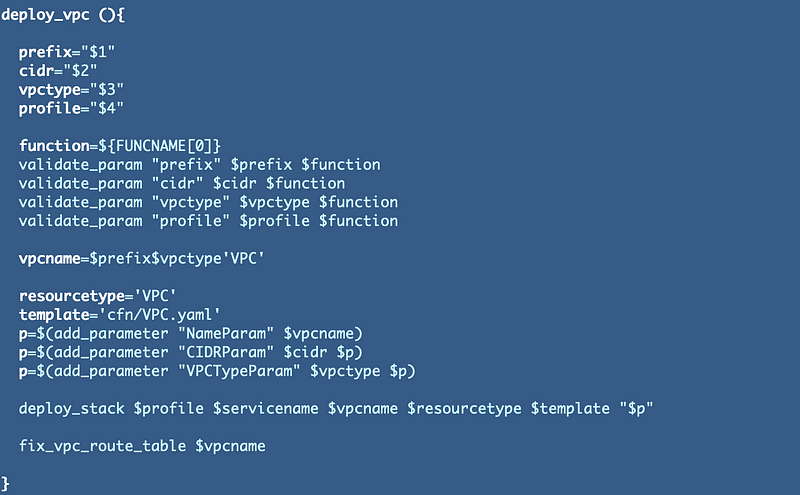
Note that when you go to delete your route CloudFormation stack after this change it will fail. Try again, check the box, and then you can delete it. If the route table ID below exists it will still be listed in your list of route tables and you will need to delete it separately.
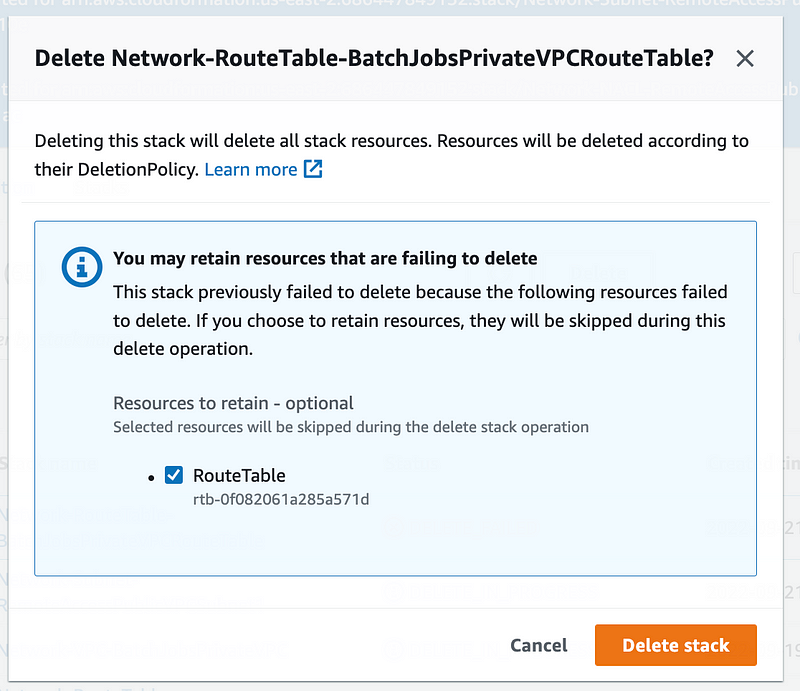
Hope that helps. Really hope AWS fixes the problem above.
Stay tuned as I get back to deploying the subnets and security groups for our VPCs. But first, let’s make sure we have VPC Flow Logs enabled for every VPC we create — an AWS security best practice.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab





