Guardrails on Github
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Related Stories: Git Security | Application Security | Secure Code
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
The term “guardrails” has become very popular in the realm of cloud security lately. If you listened to the Masters of Data Podcast I was on today with Jadee Hanson, George Gerchow, and Ben Newton you might have heard term mentioned in conjunction with DevSecOps and automation on cloud platforms. The idea is that you allow people to keep moving forward in their work but set up a mechanism to prevent them from taking unwanted actions as they go.
This idea of “guardrails” is not at all a new idea. Jason Chan, VP of Information Security at Netflix, spoke at our Seattle AWS Architects and Engineers Meetup in 2014 about how Netflix handles security by letting people do their jobs but then telling them when they’ve made a security mistake to get it corrected. Other speakers gave AWS re:Invent presentations along a similar line of thinking. Let people work within boundaries and train them about security as they work.
I took this a step further and wrote a paper about it while working at Capital One in 2016 called Event Driven Security: Balancing Security and Innovation as mentioned in my last cloud security blog post. The idea behind the paper was instead of trying to play catch up with cloud security — or block people from getting their jobs done as had been the case in the past — let’s let events drive our security decisions in an automated way. Let’s turn our rules, when possible, into code-based reactions to security problems. The paper talks about two different aspects of this event-driven approach.
1: Try to catch security mistakes up front before they reach production.
2: Monitor for unwanted events after things have been deployed to production and automate the response.
In terms of catching things before they get into production what better place to do that than by looking at your actual source code as developers check it into your source control repository? If you are following a good infrastructure as code model, this is typically where it starts right? Someone checks something into source control they shouldn’t. So why not prevent the unwanted code from moving into production from the start.
This post is sponsored by datree.io and this is the product I’m going to show as one of your options for making sure only desirable code makes it to production. Let’s take a look at how it works.
Installing datree.io is pretty easy, and they offer a free trial, so you don’t have to pay anything to give it a shot. You can add it to a test repository initially to see how it works. Just go to the datree.io web site and click sign up.

After you add datree.io to your Github repository, you’ll be able to access a dashboard you’ll see a list of options and issues.
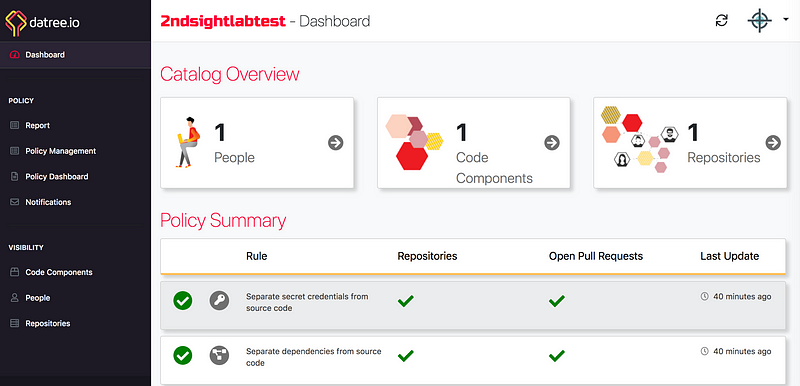
If I scroll down a little bit in my list, I see some problems — oops.
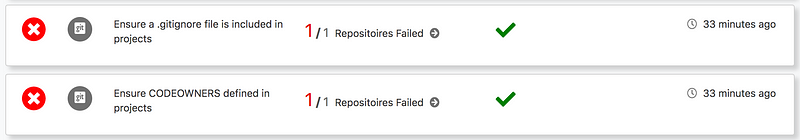
Well, that’s not good. Let’s fix one of those problems. First I’ll add a .gitignore file to my Github repository. And by the way, it’s a good idea to exclude any .pem files from being uploaded to your repository (i.e., SSH keys for AWS EC2 instances, for example) so I’m going to exclude those here while I’m at it.
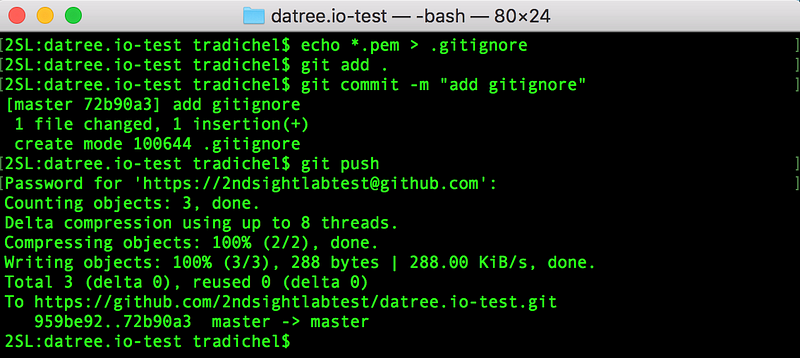
Alright now let’s check back in with datree.io and see how I did. Looks good!

That’s pretty slick, but that’s only the beginning of what datree.io has to offer. Check back later for a more advanced example showing how to prevent a common mistake with a custom rule. If you want to give it a try, visit the datree.io web site.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2019
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
