Creating an AWS Account Alias
ACM.417 Automating the creation of an alias for AWS Organizations accounts
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Cloud Governance | IAM | AWS Security
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I explained how naming conventions can help simplify the complexity of roles and policies.
Before I proceed with creating my accounts I want to add a couple of functions to my account_functions.sh file to create and delete an AWS account alias.
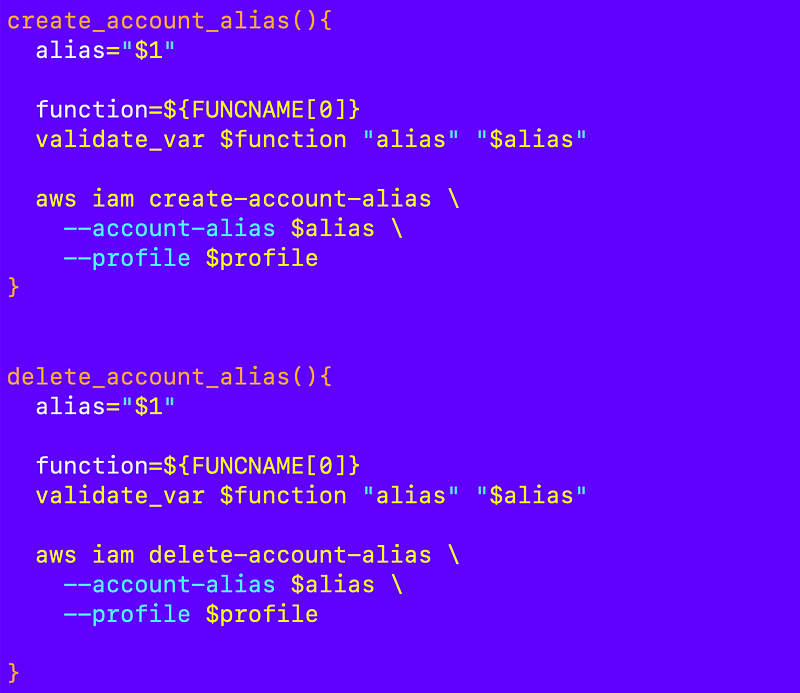
When you create an account alias it will appear on the AWS IAM dashboard. Initially you’ll only see the account number and have the option to create the alias. After you create the alias it will appear here.
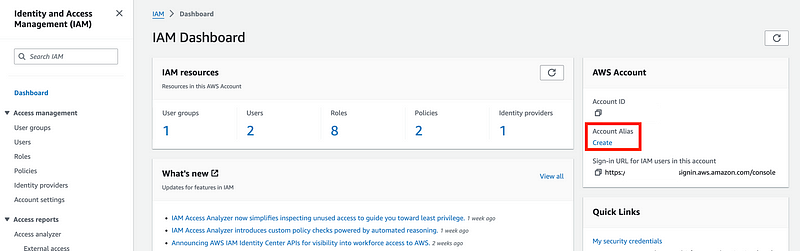
You have to call the function from the account where you’re creating the alias. I wish this was an option to add on a new account using CloudFormation but it’s not because it falls under IAM, I guess.
I’ll include my account functions file when I set the org SSM Parameter in the root account and call my function from there to match the alias on the root account to the organization value stored in SSM.
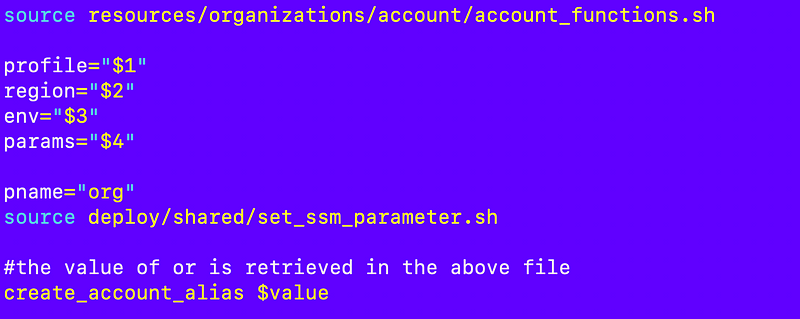
Recall that the value for the parameter is retrieved in the included file.
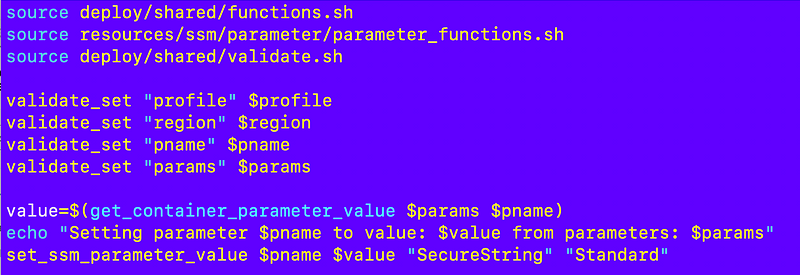
Now I can re-run the root-adminrole job that sets the parameter:
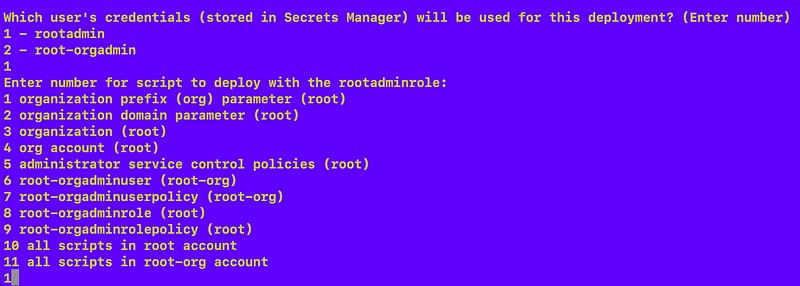
Head back over to the IAM dashboard and validate that the alias exists.
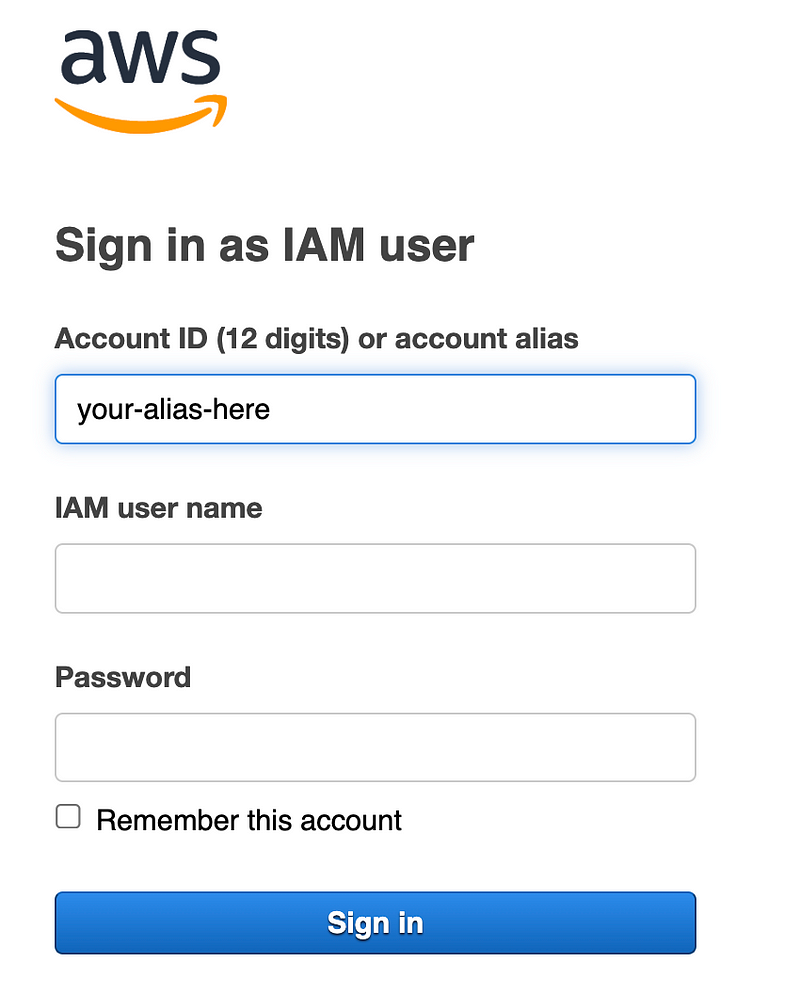
Now when AWS IAM users log into that account they can use the alias in the signing URL:
https://[your-alias-here].signin.aws.amazon.com/console
And on this screen where you login as a non-root user to an account:
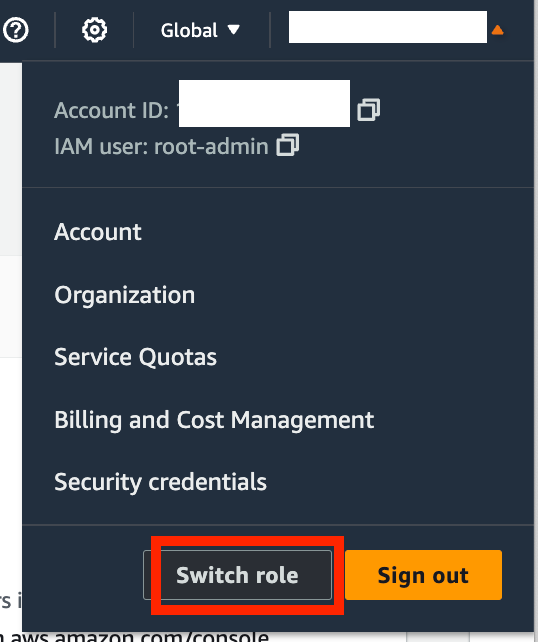
And also when you switch roles:
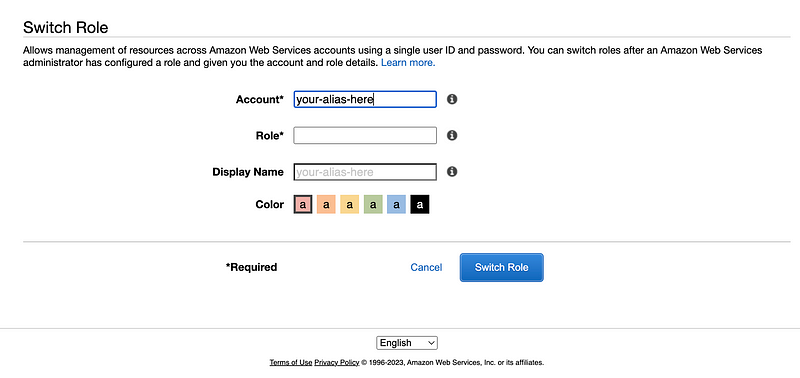
Now that I’ve got a function to create a new alias, I want to call it every time I create a new account. Note that an alias must be unique, like an AWS account number. So I am going to create my alias using the org prefix plus the account name like this:
[org]-[account name]
Hopefully that will be unique enough. If not we might need to add logic to make additional adjustments.
I can add the following to my account deployment script:
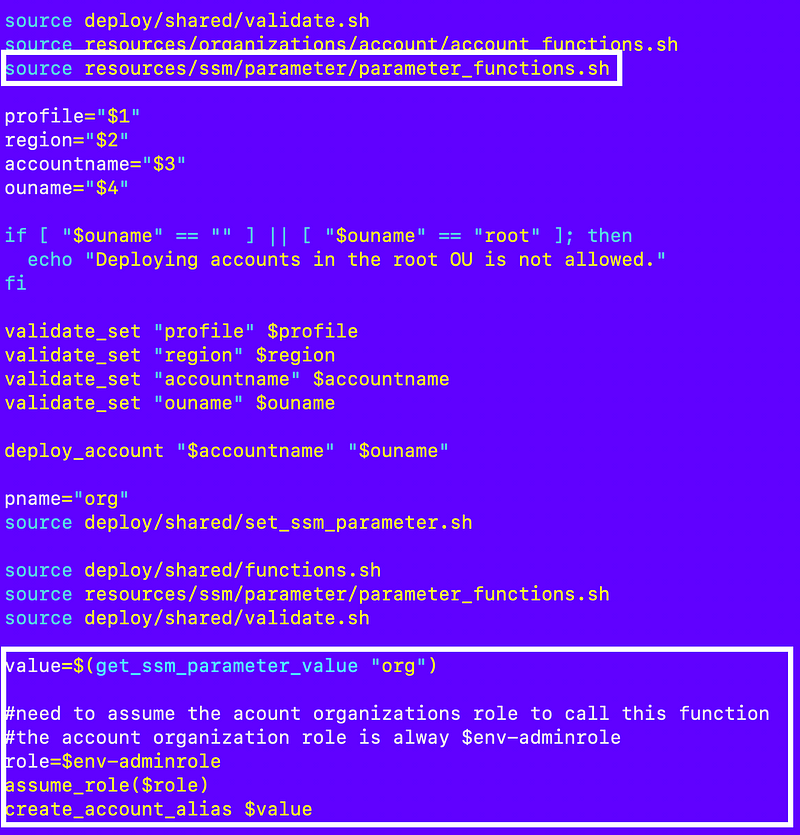
This is all quite simple except for the assume_role function which currently doesn’t exist. Calculating the name of the organization role we want to assume is simple, because I’ve named my role consistently as explained in the last post.
Assuming the role is a bit more challenging. I also realize I have an issue in my MFA SCP for organizations potentially.
I’ll fix all that in the next post.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
