Create an AWS Sandbox Account Administrator
ACM.208 Creating a user in another account using the AWS Organizations role
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | AWS Organizations | IAM | Cybersecurity
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post, we took at look at enforcing delete on AWS S3 buckets.
Now I want to create an admin user in the Sandbox account I created in this post.
We can reuse the User CloudFormation template we created earlier in the series that deploys a user and adds the password to AWS Secrets Manager. I don’t love the password solution but at the time of writing that there were not a lot of good options. We will have the OrgRoot user create the user in the sandbox account, so the password is going to end up in the Sandbox account Secrets Manager. We could have the OrgRoot user or the root user in that account retrieve the password and give it to the user, or the user could reset the password.
Here’s the user template.

Here’s our function to deploy new users.
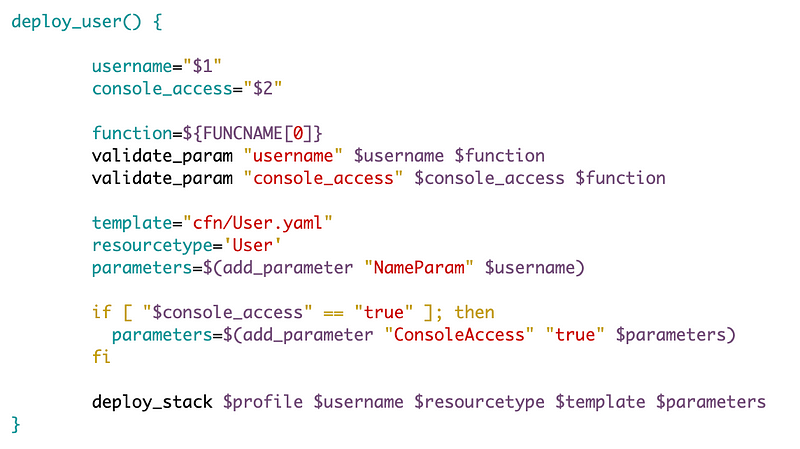
The change we need to make is to allow creation of a user the an AWS managed policy. We may want to restrict who can set what policies via Service Control Policies but for right now we are just testing things out.
I’m going to create a function to deploy a sandbox admin user.

I need to add the functionality to add the AWS Administrator Access managed policy to the user. First I’m going to to need to look up the ARN for that policy. Then I need to modify the CloudFormation template to accept that ARN as a parameter and set it on the user if passed in.
Not that we could use the following command to assign the AWS managed administrator policy to this user, but if you mix and match AWS CLI commands with CloudFormation, you’re going to ahve issues deleting resources.
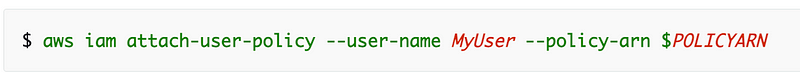
First, I’m going to query the AdministratorAccess policy to make sure I can retrieve it.
aws iam list-policies --query 'Policies[?PolicyName==`AdministratorAccess`]'I want to get the ARN here from the output below.
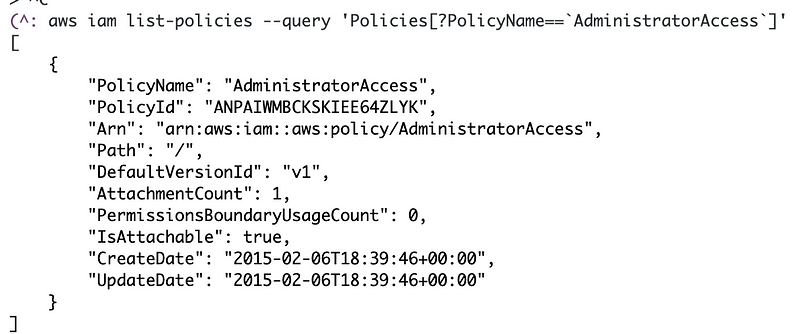
To get the ARN and remove the quotes I can query the output:
aws iam list-policies --query 'Policies[?PolicyName==`AdministratorAccess`]'.Arn --output textAdd that to the function and assign it to a variable. Pass the variable into the deploy_user function.
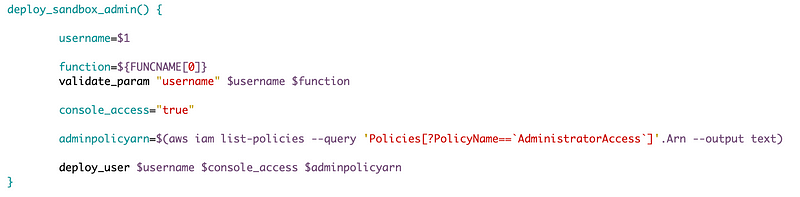
Add the new parameter to the deploy_user function.
Pass it into the CloudFormation template deployment function.
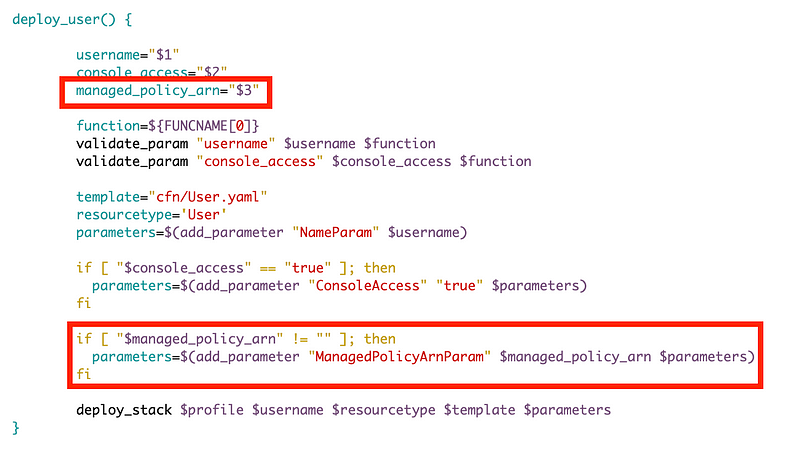
Modify the CloudFormation template to accept the parameter.
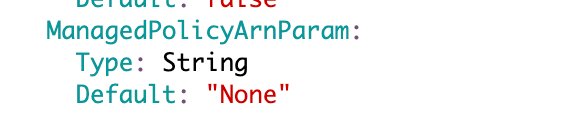
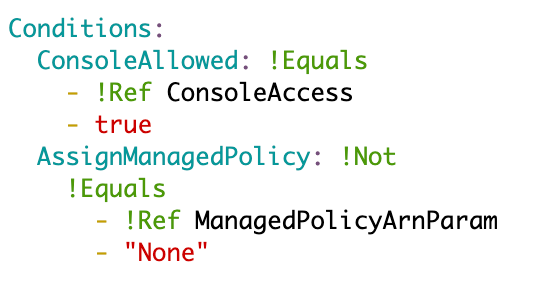
Add a condition to indicate if the managed policy exists or not:
Add the ManagedPolicyArns per the CloudFormation documentation as a list (with dashes in front of each item).
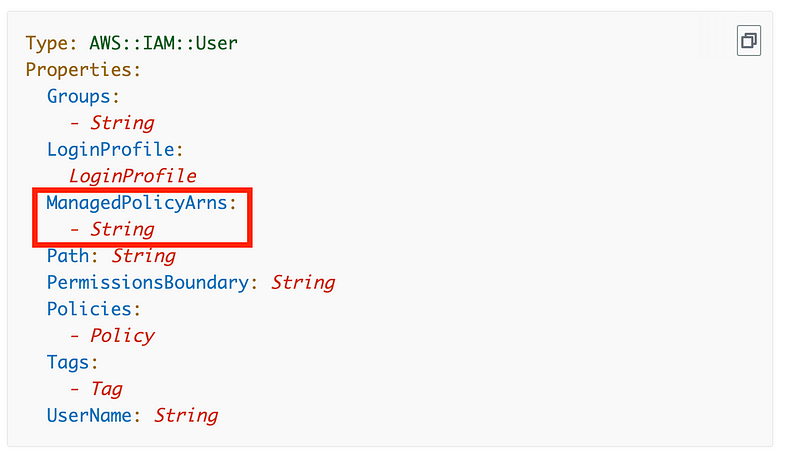
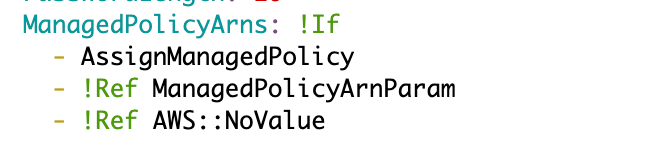
Now the above didn’t actually work becuase ManagedPolicyArns needs to be a list of strings. I would show you what the code looks like via a screenshot like but currently, AWS CloudShell has some kid of bug when two dashes exist. Here’s how it gets displayed, and if I try to edit it, it appears mangled. This is one of the reasons I want to stop using CloudShell ASAP:

Here’s what it should look like and how I originally typed and saved it:
ManagedPolicyArns:
!If
- AssignManagedPolicy
-
- !Ref ManagedPolicyArnParam
- !Ref AWS::NoValueIf takes three arguments in a yaml list (with dashes in front of each element) like this:
!If
- condition
- value if true
- value if falseBut I need to provide the value if true (managed arns) as a list. So that’s why I put the value on a second line, indent it, and precede it with a dash.
Back over in our Org/stacks/Sandbox deployment script, update the deployment script to add the user_functions.sh script and add the function call. We need to navigate to the folder containing the script so it can access the template in /cfn folder.
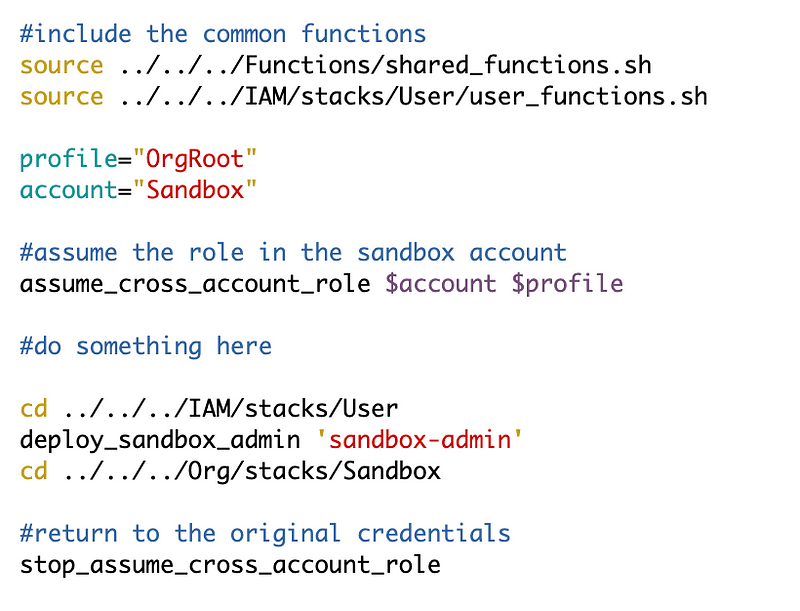
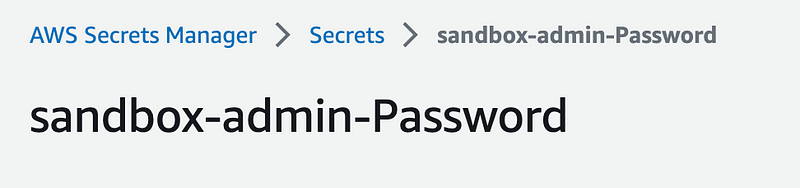
Deploy the user. Now we can check secrets to get the initial password.
Remember that the password is stored in secrets (and that I don’t particularly like this solution but I couldn’t think of a better one).
Logout as the root user, login as the sandbox administrator, reset the password, and add MFA to the SandBox user.
Note that the stack for this user does not exist in our root management account now. It exists in our Sandbox account.
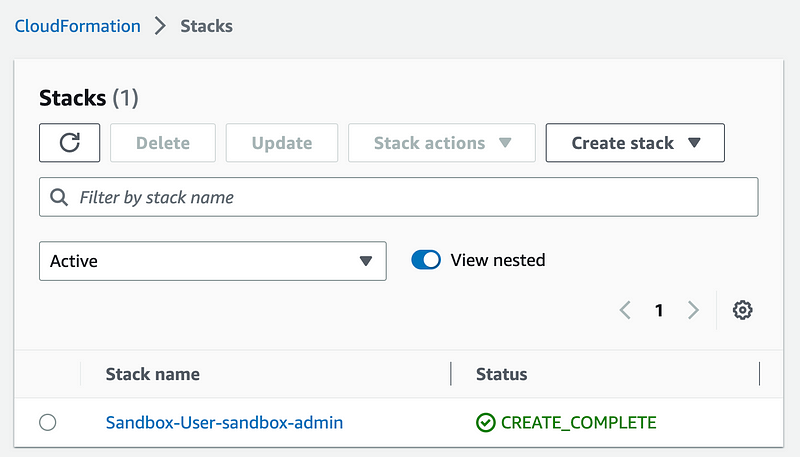
By the way, I changed the name of this user after writing this post to SandboxAdmin in line with OrgRoot.
Navigate over to IAM. Verify the user exists and has the proper policy assigned.
Next we’ll create a KMS key in the Sandbox account for testing purposes.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
