Azure — Fetch Key Vault Secrets Using Logic Apps
Step-by-step guide on how to fetch a secret from azure key vault using logic apps.
Using Azure Logic Apps, it is possible to retrieve secrets from an Azure key vault. You can then use the secret for any custom scenarios such as passing it to an Azure Data Factory pipeline or to a databricks notebook.
Below are the steps to get a key vault’s secret using logic app —
1. Create a New Logic App And Configure
Upon creating a blank logic app, go to Identity property. Turn the status On. This is done because logic app will be authenticated to Key vault using Azure’s Managed Identity.
Notedown the Object Id.
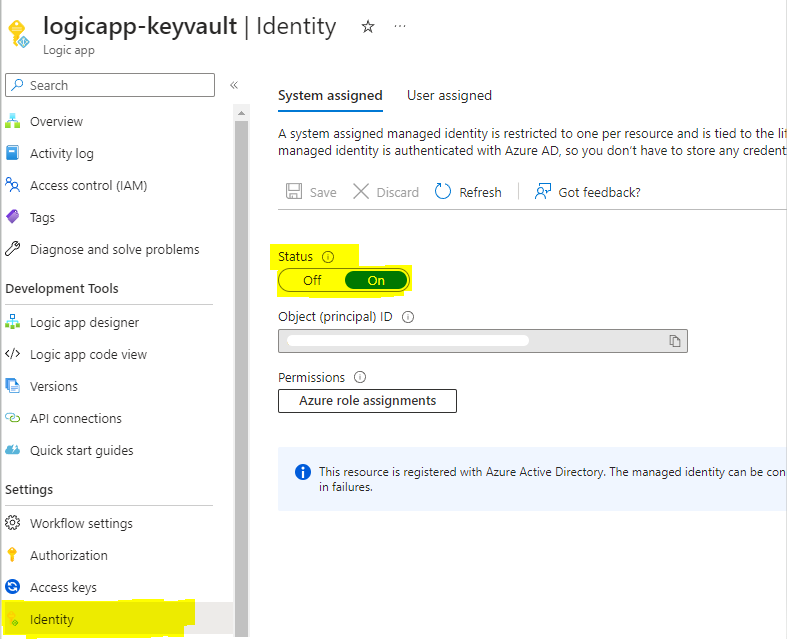
An advantage to using managed identity is that Azure uses Active Directory (AD) to authenticate a resource.
2. Add Logic App to Key Vault
At the key vault location, go to Access Policies. Click create to add a new access policy.
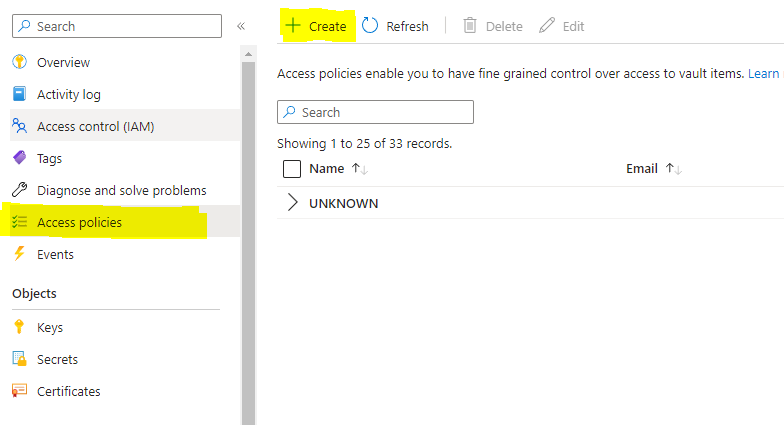
Next, select the checkboxes Get and List under Secret Permissions section. Since we are only fetching secrets and going through the list of secrets, we will select Get and List.
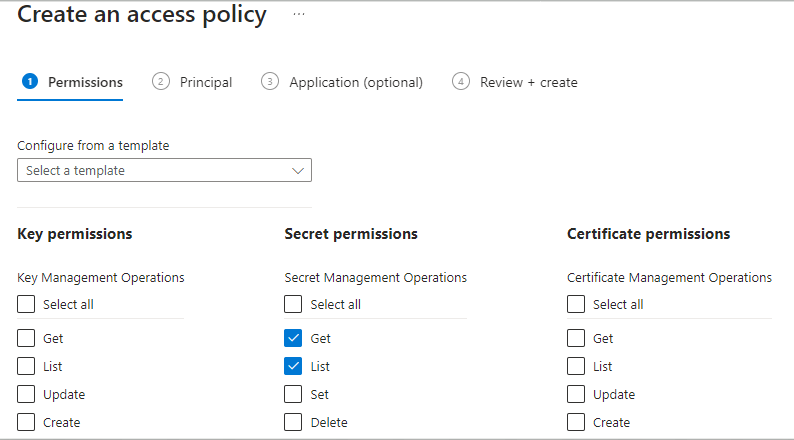
On the next screen, add the object id which we copied from Step 1. This will add Logic App as the user of the access policy.
After we complete this step, click Review + Create.
3. Get Secret Using Logic App
Go back to Step 1 where we created a blank logic app. I selected recurrence as the trigger for my logic app. Next, search for Key vault and choose Get secret activity.
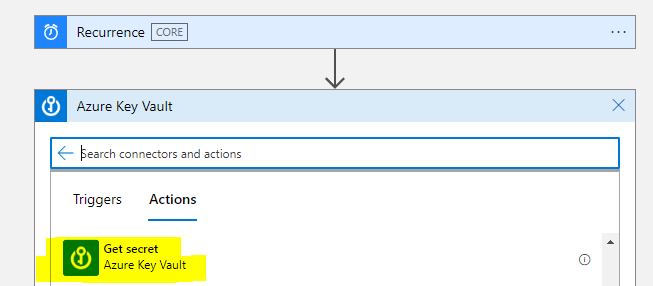
The logic app should automatically show you the list of secrets. From the list, you can select the secret name whose value you’d like to retrieve. For the purpose of this article, I created a secret called testsecret with value as mysecretvalue.
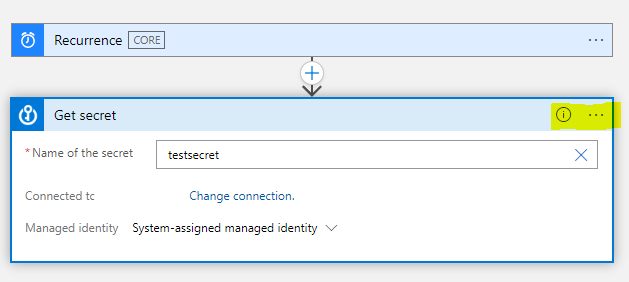
With the secret selected, let’s run the pipeline to check results.
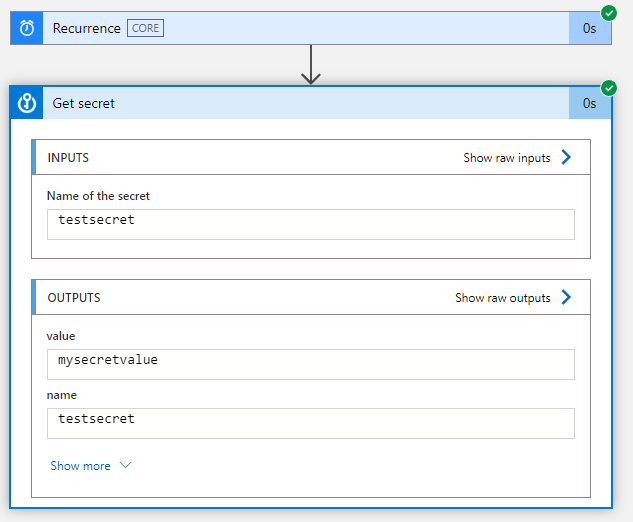
As we can see above, we were successfully able to get the value of a secret from the key vault.
TIP
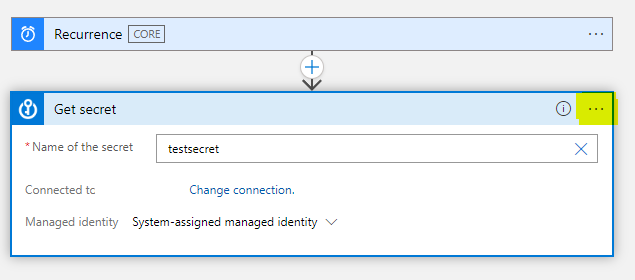
If you would like to secure the value of the secret in the output, select the 3 dots on the Get secret activity.
Click settings and then turn on Secure Outputs. This will not show the secret value in the output of Logic apps.
And that’s the end of this article. If you would like to further send the secret value to an ADF pipeline as a parameter, you can do so by following my other article where I explained that process in detail.






