AWS Security Best Practices
A checklist for Cloud Admins to live by
In today’s fast-paced digital world, securing cloud resources is a top priority for organizations. As more and more businesses adopt the cloud, they must level up their traditional IT strategy to face new attack surfaces on the cloud, protect sensitive data, maintain the confidentiality, integrity, and availability of resources, and comply with regulatory requirements.
In this blog post, we’ll delve into the key security best practices that organizations can follow to secure their AWS cloud environment.
#1 — Secure Identity & Access Management (IAM)
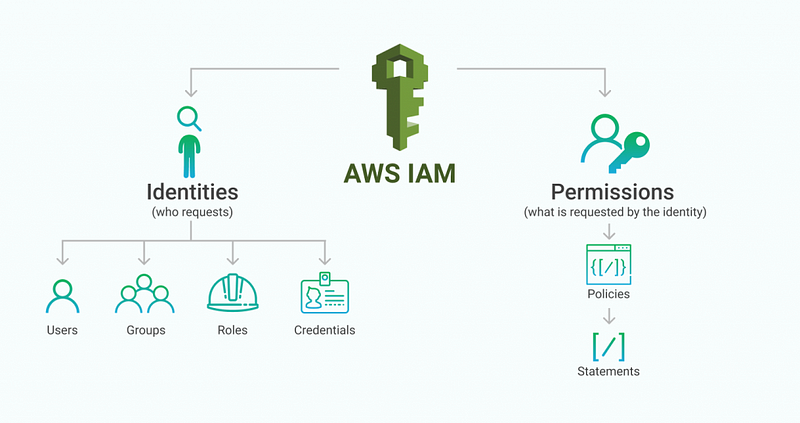
AWS IAM (Identity and Access Management) is one of the most crucial services that contribute to the overall security of your AWS infrastructure. Here are some ways to enforce and increase security for AWS IAM accounts.
✅ Set a strong password policy: Enforce the use of strong and unique passwords for all IAM users, and rotate them regularly.
$ aws iam get-account-password-policy
{
"PasswordPolicy": {
"MinimumPasswordLength": 12,
"RequireSymbols": true,
"RequireNumbers": true,
"RequireUppercaseCharacters": true,
"RequireLowercaseCharacters": true,
"AllowUsersToChangePassword": true,
"ExpirePasswords": true,
"MaxPasswordAge": 90,
"PasswordReusePrevention": 3,
"HardExpiry": false
}
}This policy:
> Specifies that the minimum password length is 12 characters.
> Requires symbols, numbers, uppercase and lowercase characters in the password.
> Allows users to change their password.
> Specifies that passwords expire after 90 days.
> Prevents users from reusing their previous 3 passwords.
> Specifies that the password policy does not have a hard expiry (users are not forced to reset their password at a specific time).✅ Enable multi-factor authentication (MFA): Require MFA for all IAM users to protect against password theft and unauthorized access.
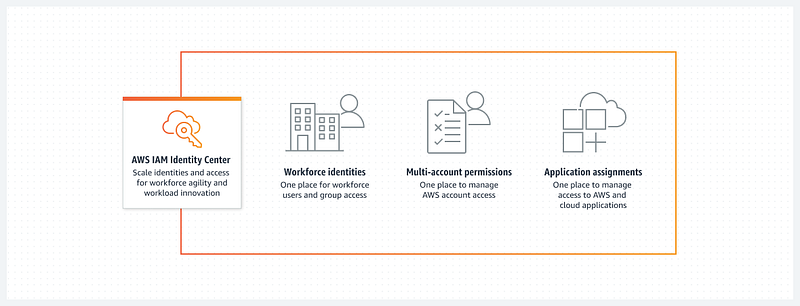
✅ Use a centralized identity provider, such as AWS IAM Identity Center (successor to AWS Single Sign-On) or a third-party provider, to simplify the management of multiple AWS accounts and federated applications. By doing so, you can eliminate the need to routinely create IAM users or use long-term access keys. Using a centralized identity provider helps ensure that authentication and authorization processes are streamlined and consistent across your organization, while also reducing operational overheads.
✅ Audit the status of IAM user credentials regularly by generating an IAM credential report. This detailed report includes all users in an AWS account and statuses of various credentials, including passwords, access keys, and MFA devices. If you notice any non-conforming users or suspicious activity, you can take action, such as sending warnings, setting strict deadlines, or escalating to higher authorities.
✅ Rotate IAM user access keys regularly: Access keys are long-term credentials that are used to sign programmatic requests to the AWS CLI or AWS API and have access to various AWS services. Some teams create common access keys and share them among members (e.g. DBAs often share database keys). When such practice is followed, you must renew/rotate these keys regularly (e.g. especially when someone leaves the team). Also, you should never generate access keys for the root user, because it allows full access to all your resources for all AWS services. In general, as a best practice, it is highly recommended to avoid creating long-term credentials as access keys and always rely on using temporary security credentials, such as IAM roles.
✅ Use IAM roles to delegate access permissions to AWS resources such as EC2 instances, Lambda functions, or S3 buckets. This eliminates the need to manage access keys and reduces the risk of exposure.
✅ Use IAM policies to control what actions users, groups, or roles can take on resources and services. Use the principle of least privilege to grant only the permissions required for the specific task or job function. Avoid using wildcard or overly broad permissions.
✅ Use IAM groups to assign policies and roles: Create groups for users with similar roles and assign policies and roles to the groups rather than individual users. This makes it easier to manage permissions and reduces the risk of human error.
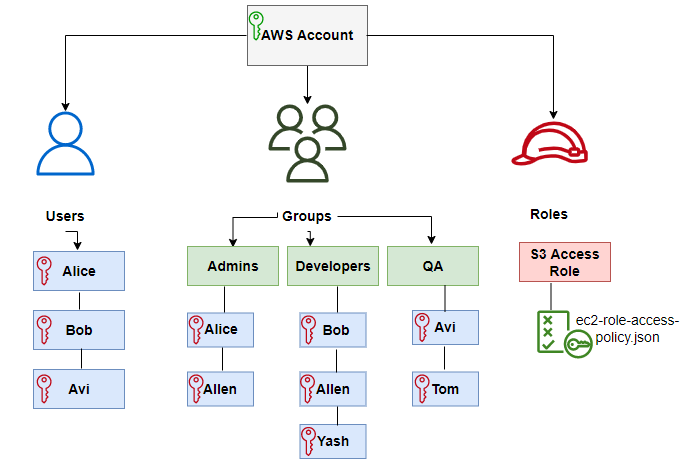
✅ Use managed policies and reduce custom policies: AWS provides a set of managed policies that define permissions for common use cases. Use these policies where possible instead of creating custom policies. This reduces the risk of errors and simplifies policy management.
✅ Avoid committing AWS access keys and credentials into source code: AWS access keys and credentials are meant to be used as secrets, hence never include them in code or any other form of exposure. Some common ways to handle this dilemma are to include them in your CI/CD pipeline secrets or a separate vault (such as AWS parameter store), and use them as environment variables or have programmatic access without any hardcoded parts.
✅ Use policy conditions to restrict access based on additional criteria such as IP address, time of day, or source AWS account. This adds an extra layer of security and reduces the risk of unauthorized access.
✅ Test policies and roles: Before assigning policies and roles to production environments, test them in a development or staging environment to ensure they work as intended. Always check for not only granted access (allow) but also restrictions (deny).
#2 — Secure Network
Network security in AWS is largely denominated by limiting the attack surface by use of multiple virtual services such as VPCs, security groups, firewalls, access control lists etc. Here are some best practices to secure and control network access on AWS.
✅ Use VPCs (Virtual Private Clouds) to separate AWS resources into isolated virtual network environments with full control over network traffic and access to resources.
✅Use security groups as virtual firewalls that control inbound and outbound network traffic to and from AWS resources, such as EC2 instances, RDS instances, and other resources within a VPC.
✅Apply the principle of least privilege in security groups: Only allow traffic that is necessary for the operation of the resource. By default, security groups deny all inbound and outbound traffic, so you must explicitly allow traffic. Avoid using open security groups that allow all traffic.
✅ Limit inbound traffic to only necessary ports and protocols: Open only the ports and protocols required for the resource to function. If you’re not sure which ports are necessary, refer to the documentation of the service or application.
✅ Limit outbound traffic to only necessary destinations: Restrict outbound traffic to only those destinations necessary for the resource to function. For example, if an instance needs to access the Internet to download updates, only allow traffic to the appropriate update servers (never open to the entire internet).
✅Use separate security groups for different resource types: Use different security groups for resources that require different levels of access. This makes it easier to manage permissions and limits the risk of errors.
✅ Use security groups with IAM roles: Use IAM roles to control access to AWS resources, and assign security groups to these roles. This simplifies security management and reduces the risk of human error.
✅Use security groups in combination with network ACLs: Network ACLs (Access Control Lists) provide an additional layer of security by controlling traffic at the subnet level, and can also be used to block specific IP addresses or ranges. Use security groups in combination with network ACLs to provide comprehensive network security.
✅Use separate NACLs for public and private subnets: It is recommended that you use separate NACLs for your public and private subnets. This allows you to apply different rules for each subnet based on their security requirements.
✅Use security groups for instance-level security: NACLs are applied at the subnet level, so they do not provide instance-level security. You should use security groups to control access to your instances.
✅Regularly review and update security group rules and network ACLs to ensure they are still required and updated for any changes in the environment. Remove any rules that are no longer needed.
✅ Use AWS WAF (Web Application Firewall) service to protect your web applications from common web exploits. It allows you to create rules that block common attack patterns, such as SQL injection and cross-site scripting (XSS).
✅ Use NAT Gateway (Network Address Translation Gateway) to provide a way for resources in a highly-secured private subnet to access the internet or other AWS services while keeping them isolated from the public internet.
✅Use AWS Shield, a managed DDoS (Distributed Denial of Service) protection service that helps protect your applications from DDoS attacks by detecting and mitigating them in real-time.
✅Use AWS Firewall Manager, a centralized security management service that allows you to manage multiple AWS accounts and resources from a single location. It can be used to configure and manage AWS WAF, Security Groups, and NACLs across multiple accounts.
✅Use Amazon GuardDuty, a threat detection service that continuously monitors your AWS accounts for malicious activity. It can detect and alert you to potential threats, such as unusual API calls or unauthorized access attempts.
#3 — Secure Data
On the cloud, data must be secured both at rest and in transit. Here are some ways that you can achieve this.
✅Use Server-Side Encryption (SSE): SSE provides encryption for data at rest within AWS services such as Amazon S3, Amazon EBS, and Amazon RDS. There are three types of SSE:
- SSE-S3: Amazon S3 manages the keys used for encryption, making it easy to implement and manage. It uses AES-256 encryption and protects against unauthorized access to data by using SSL/TLS to encrypt data in transit.
- SSE-KMS: SSE-KMS uses AWS Key Management Service (KMS) to manage the encryption keys. With SSE-KMS, you have more control over your keys and can audit key usage. You can also use KMS to rotate keys automatically.
- SSE-C: SSE-C allows you to use your own encryption keys (customer-provided keys) to encrypt data at rest. You manage the keys and provide them to AWS when you upload the data. SSE-C is useful when you need more control over your encryption keys.
✅Use Client-Side Encryption: Client-side encryption encrypts data before it is uploaded to AWS. With client-side encryption, you manage the encryption keys, making it ideal when you need full control over your data. AWS services like Amazon S3 and Amazon EBS support client-side encryption.
✅Use Transit Encryption: Transit encryption provides encryption for data in transit between AWS services or between AWS services and your own infrastructure. AWS services like Amazon S3, Amazon RDS, and Amazon EFS support transit encryption.
✅Use SSL/TLS: Secure Sockets Layer (SSL) or Transport Layer Security (TLS) is a protocol that provides encryption and authentication for data in transit. Use SSL/TLS to encrypt all data transmitted over the network. AWS offers several services that support SSL/TLS, such as Amazon CloudFront, Amazon ELB, and Amazon RDS.
✅Use secure communication protocols to transmit data securely: Use HTTPS, FTPS, and SFTP instead of insecure protocols like HTTP or FTP.
✅Use private network connections, such as AWS Direct Connect, to transmit data between your on-premises data centre and AWS. AWS Direct Connect bypasses the public Internet and establishes a secure, dedicated connection from your infrastructure into AWS, which is more suitable for secure data transmission at scale without any disruptions.
✅ Use AWS VPN to create a secure, encrypted connection between your on-premises network and your AWS resources.
#4 — Monitor Usage
Regular monitoring, logging, and auditing of resources and usage activities can significantly improve the security of your AWS infrastructure and applications. Here’re some steps and services that you can make use of.
✅ Use AWS Trusted Advisor to run security checks and identify security risks in your AWS infrastructure. Trusted Advisor provides several security checks, including exposed IAM access keys and key rotations, SSL certificates, logging, S3 bucket permissions, security group rules, and others. Then, you can address the reported issues. For example, if Trusted Advisor identifies a security group with overly permissive rules, you should update the rules to reduce the attack surface.
✅ Use AWS CloudTrail, a service that provides a detailed record of all activity that occurs in your AWS account, including API calls, AWS Management Console sign-in events, and more. You can configure CloudTrail to log specific events and store logs in specific S3 buckets for further analysis. Also, you can use AWS services like Amazon CloudWatch to monitor CloudTrail logs and set up alerts to notify you of specific events too.
✅ Use AWS CloudWatch to track metrics, collect and monitor log files, and set alarms to notify you when certain security-related thresholds are breached. For example, you can set an alarm to notify you when CPU usage exceeds a certain threshold, indicating potential malicious activity. Also, by monitoring logs collected over time, you can detect potential security threats and investigate security incidents in AWS services, such as Amazon EC2 instances, AWS Lambda functions, and more.
✅ Use AWS Amazon Inspector to run security assessments using pre-configured templates that include various assessment targets and rules packages (e.g. CIS Amazon Web Services Foundations Benchmark, PCI DSS).
✅Apply software updates and security patches: Regularly monitor for software updates and security patches for the operating systems, applications, and services running on your AWS instances. AWS provides tools such as Amazon Inspector and AWS Systems Manager that can help with this process. When running such updates, always schedule maintenance windows during non-business hours to minimize the impact on your users.
✅Monitor billing: To monitor your AWS billing, you can use the AWS Billing and Cost Management console. Set up alerts and notifications to alert you when your AWS usage or costs exceed predefined thresholds. You can also use third-party tools to monitor your AWS billing and provide detailed reports and analysis. Unexpected behaviours in billing reports can expose security vulnerabilities in the infrastructure too.
Conclusion
Implementing strong security measures is critical when using AWS to protect sensitive data and applications. By following AWS security best practices, such as using multi-factor authentication, limiting access to resources, encrypting data in transit and at rest, and regularly monitoring and auditing your environment, you can significantly reduce the risk of security breaches and ensure the confidentiality, integrity, and availability of your data. AWS provides a robust set of security tools and features, but it’s essential to understand your responsibilities as a user and take proactive steps to secure your AWS environment. By prioritizing security and staying up-to-date on the latest best practices, you can confidently leverage the full benefits of AWS while keeping your data safe and secure.
What’s Next
Hope you enjoyed the read so far. In an upcoming blog post of this series, let’s discuss cost optimization tips as well. If you have any questions or suggestions, please feel free to let me know too.
Stay tuned for the next AWS tip. Until then, happy coding!






