AWS IAM Role Profiles with Boto3
Leveraging EC2 IAM role profiles with the AWS Python SDK
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: Cloud Governance | IAM | AWS Security | Okta
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I wrote about using IAM role profiles and MFA in a prior post in relation to AWS penetration tests. On each penetration test, I typically write new scripts and enhance existing tools that help 2nd Sight Lab evaluate client security. What if you are working on a test for a client and trying to use IAM roles in conjunction with a Python script?
If you want to write Python code to work with AWS, you’re going to use Boto3 — the AWS Python SDK. When you execute a command using this library, you have a number of options for providing credentials to call AWS APIs. If you are running your scripts from an AWS compute resources such as an AWS EC2 instance, the best practice will be to use an AWS EC2 instance profile which associates your virtual machine with an IAM role. This provides a mechanism for automatically rotating credentials, and you won’t have to upload developer keys to your EC2 instance.
How do you get the AWS Python SDK to work with AWS IAM role profiles? It’s pretty simple. I’m presuming here you already have installed Python and Boto3 on your EC2 instance and gotten that working. I’ll also presume you set up an IAM profile in your AWS CLI configuration on the host where you are running your script.
For a simple script that uses an IAM role:
- Import boto3
import boto32. Define your profile name. You could hard code the variable name in the next command, but I like to use a variable. I set the variable to the name of the profile in my AWS CLI configuration file that I want to use to run the commands:
profile='my_profile'3. Instantiate a Boto3 session using this role profile.
session = boto3.Session(profile_name=profile)4. Now, instantiate your client using this session and specify the service you want to use. Each service has several API calls, and in this case, I want to call the EC2 APIs.
ec2=session.client("ec2")From here on out, things work as per usual. You can use your client to call the commands for the particular service you are using. For example, if you wanted to list all available regions:
regions = [region[‘RegionName’] for region in ec2.describe_regions()[‘Regions’]]for region in regions: print (region)Here’s the entire script:
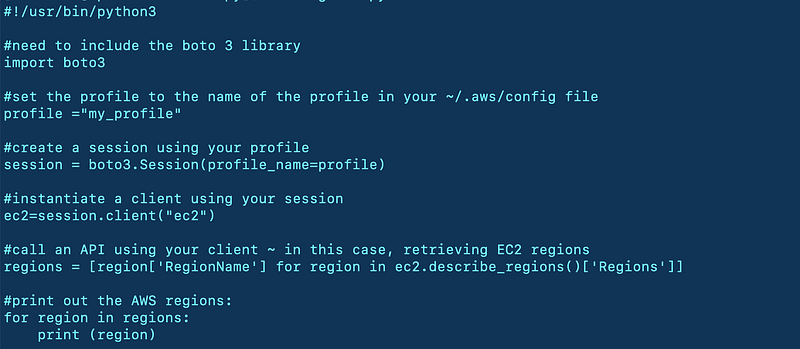
Note that I am using Python version 3. Remove the first line or change it to point to the correct version if you are using Python version 2 (default on AWS EC2 at the time of this writing).
For more information, refer to the Boto3 documentation.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2020
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab





