Automated Deployment of an S3 Bucket for a Static Website
ACM.253 A few tweaks to our reusable AWS S3 bucket template
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics | Code.
🔒 Related Stories: Application Security | Secure Code | AWS Security | S3
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In the last post I deployed a KMS key for the Sandbox Web account to test deployment of an S3 bucket for a static website. We considered the pros and cons of separate keys for each site, for each environment, and for logs versus content:
For our initial S3 bucket deployment I’m going to use one key for logs and content. I may change that later for other environments or applications.
We already have an S3 bucket template that I created in a prior post. My AWS S3 stories are here:
The S3 bucket template I created looked like this in CloudShell’s colorful editor:
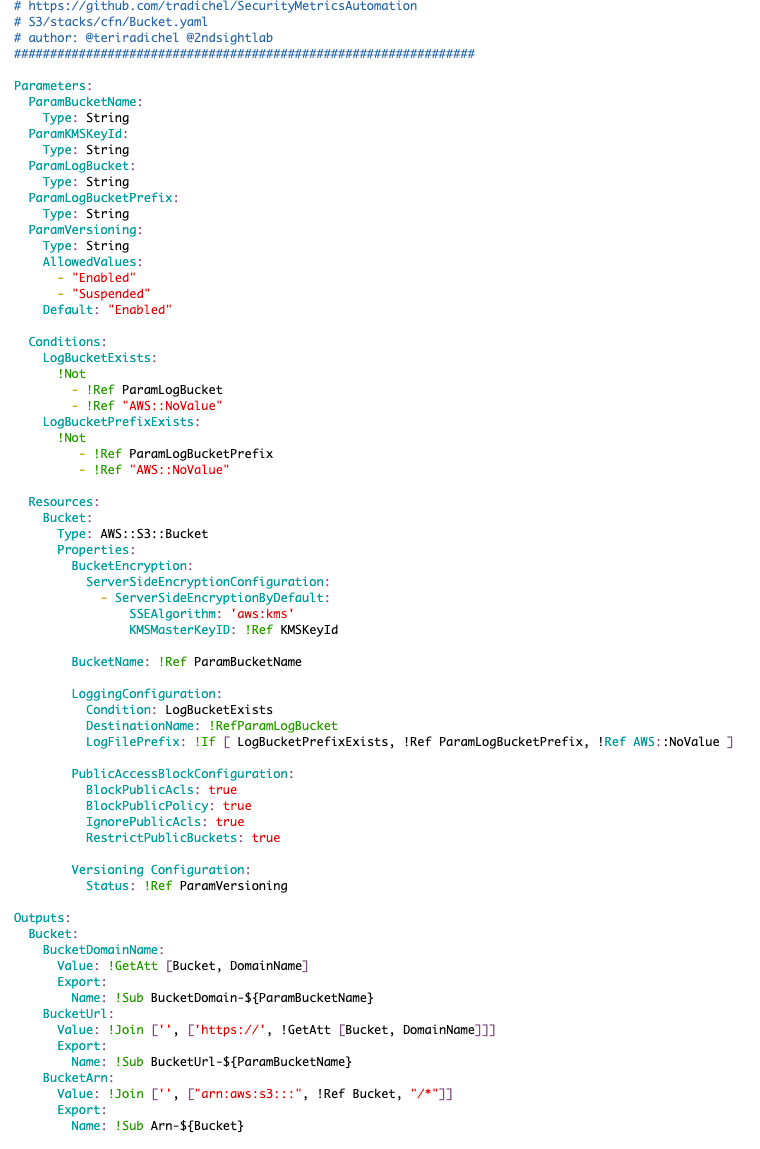
As I explained already I will not be making the bucket public. I’m going to use CloudFront, which I will explain in more detail in upcoming posts. You never need a public S3 bucket and you can easily enforce no public bucket policies if you take this approach.
The bucket policy we created in the prior posts was for an organizational CloudTrail.
Our static website bucket will definitely have a different policy, but how closely can we align the bucket configuration itself? I looked back at a template I used to create a public website in the past and it looks like this:
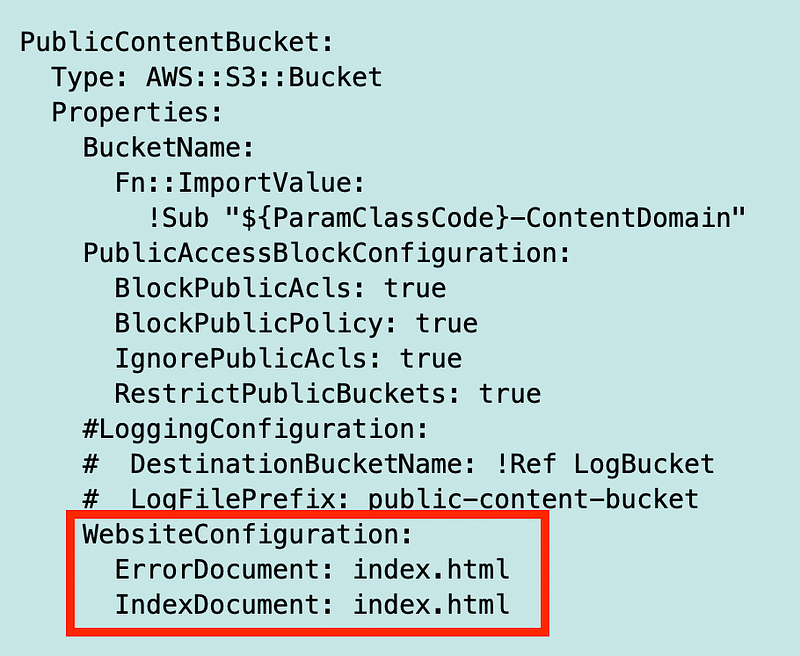
The only real difference is that Website configuration. However, we don’t need that configuration because it is not required if we are using CloudFront. You can cofigure similar options on CloudFront itself.
You can specify the default root object on CloudFront:
We can also define custom error handling:
It is important that if we skip the above configuration that we configure CloudFront and our bucket properly, otherwise someone might get a list of files in the bucket rather than a specific page or an unwanted error message. But that’s no different than a misconfigured web server that returns a list of files and folders on the server. You need to understand how things work and configure them properly.
S3 Bucket Template Changes
As you saw in the last post I thought through the bucket configuration and decided that I might want a separate KMS key for logs versus content. We’ll need to support that. I am also going to need to add the SandboxWebAccount environment. I’m going to rename all my environments to have Account at the end of the name, though that is not necessary. You may have environments that span accounts or have multiple environments in the same account, but I prefer an account per environment.
Here’s the updated environment Parameter list. I also changed the parameter name from profile which was confusing me when coming back to this. Profile is the name of the role that deployed the resource via the CLI. that doesn’t necessarily align with these names which represent the environment where the bucket is deployed. The names need to be all lowercase to work in a bucket name.
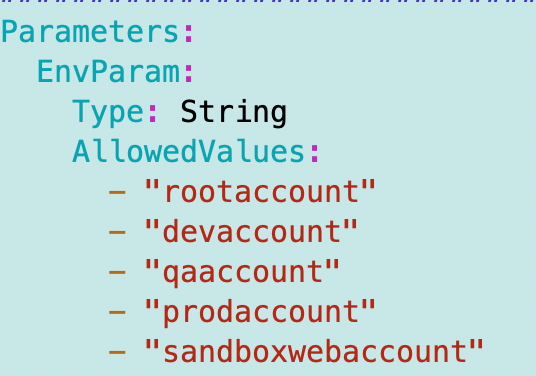
At this point I remembered that I was not deploying access logs in the dev environment previously. That was just an example of how you can alter deployments for different environments. I’m actually going to remove that so I can validate access logs across environments, but I’ll likely want to limit the time those access logs exist to save money.
I also wanted to simplify log bucket deployments. I created a parameter to indicate whether or not we are deploying a bucket that has a log bucket associated with it.
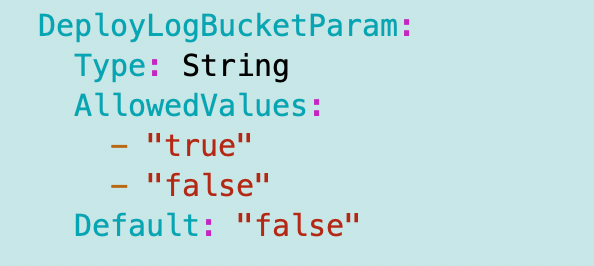
The conditions are simplified to the following:
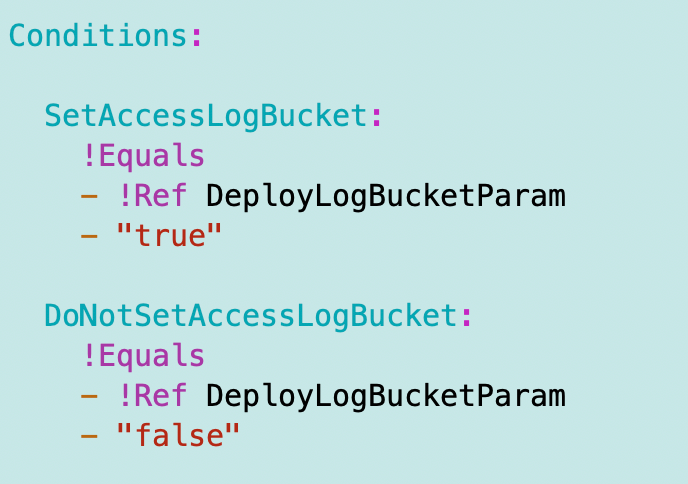
I make the name of the log bucket consistent like this — which means you pass in the same bucket suffix for a log bucket or a non-log bucket:
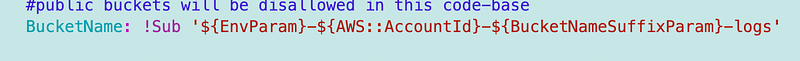
This approach presumes that all buckets that do not have a log bucket are log buckets. I may need to change that later but spent enough time on this for the moment.
Reviewing the CloudTrail deployment it looks like this:
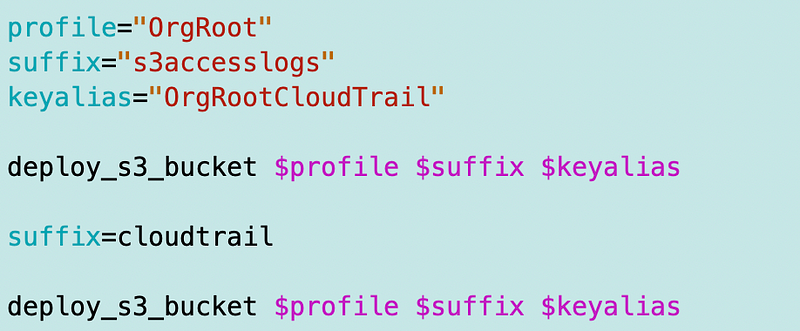
I will need to adjust the above to align with the new deployment method. Now one function call deploys both buckets.
The modified bucket function looks like this, allowing for a log bucket or not and separate KMS keys if needed. This is certainly not the last change I will make to this template but where it stands at the moment.
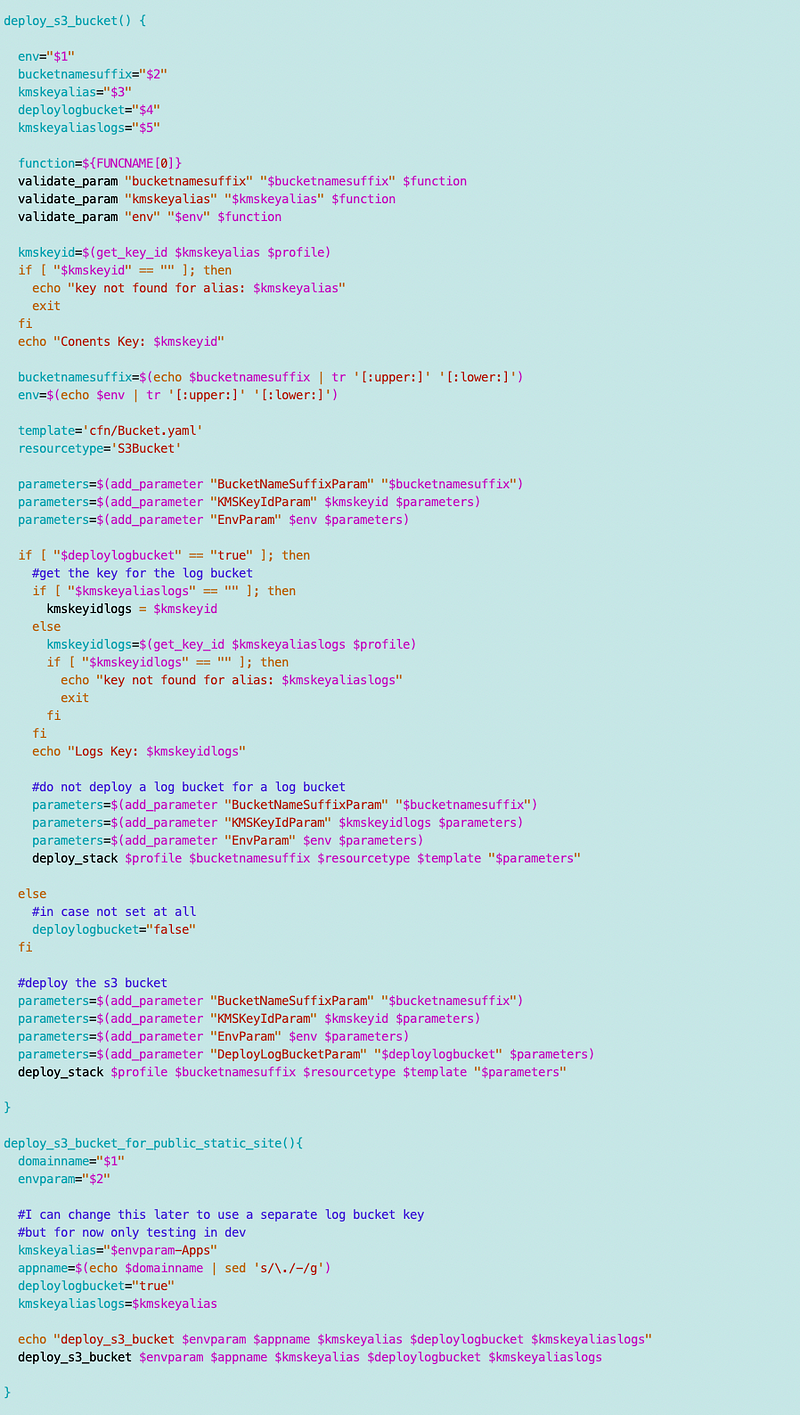
I created a simplified function for deploying a bucket for a static website that looks like this.
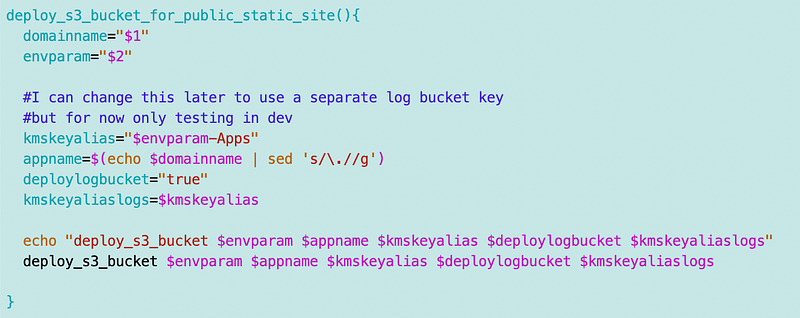
Note that I removed the dash in the web site name because it caused some problems.
And I can deploy it from my static web site script like this:
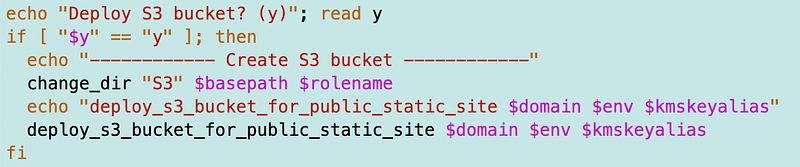
That worked. We have a bucket. Now we need contents, a policy, and CloudFront in front of it to service up the content.
Also, as I continue testing I fully expect to make improvements on this code.
Follow for updates.
Teri Radichel | © 2nd Sight Lab 2023
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab
