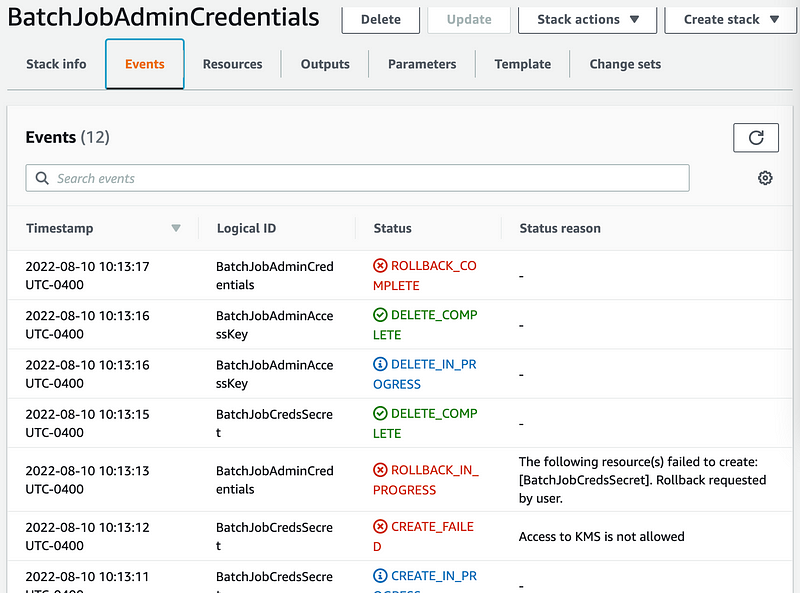
Access to KMS is not allowed
Need better error messages when KMS access is restricted on AWS
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
⚙️ Check out my series on Automating Cybersecurity Metrics. The Code.
🔒 Related Stories: AWS Security | Security Architecture | KMS
💻 Free Content on Jobs in Cybersecurity | ✉️ Sign up for the Email List
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
TLDR: If you update a role with CloudFormation it changes the ARN in the key policy to an arbitrary value (I think it’s some sort of role ID but not an ARN) that causes your policy to fail (see screenshot below). The CloudFormation update should remove and re-add the policy with the correct role, but of course that needs to be done very carefully and securely behind the scenes to prevent abuse.
So the first thing to do if you get this error is check your KMS key policy.
There’s another bug here as well. CloudFormation doesn’t recognize the change so when you update your stack to update the key policy that has the problem — it doesn’t do anything. This makes this a very tricky bug to resolve unless you’re familiar with it already.
I was able to force CloudFormation to update by adding a new Output for no other reason than to get a change to the stack. The update did not fix the invalid principals or return an error. I can see that the parameters passed into the stack are correct. I’m guessing this is because CloudFormation sees no change to the resource based on the inputs. It’s not checking for drift.
I fixed that by changing the first SID to add “and force update” to make the template change. That way CloudFormation has to deploy it to get the template into the console. That updated the ARN as well to the parameter value.
This error can cause you lock yourself out from administering your own keys if it does this to the administrator ARN.
I’ve reported this to #awswishlist but feel free to re-request it. The more popular a request is, the sooner AWS will fix it.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
I’m running a CloudFormation script to deploy some IAM credentials. I already had this working, but I’ve refactored my code a bit. Now I’m getting this error again.
I’m looking at the policy of the role that should be executing this code and it appears to have the appropriate permissions.
When getting this error it would be more helpful if the error message included the user or role ARN was that was not allowed and whether it is due to the KMS key resource policy or the IAM user policy.
This error message seems to indicate it is an IAM policy but it’s not really clear.
Then when I review the key policy I don’t see any problems there either.
A more useful error message in this case would really save me some time.
By the way, I read this blog post and it is incomplete.
Someone at AWS should review the code and document all use cases that cause this error and how to fix them. In my case, I am not performing a cross-account action. I am in a single account. I have a role that is allowed to encrypt (not decrypt) using a key and a user that assumes this role and getting this error.
The problem initially was that somehow the ARN I passed into a key policy is getting changed to a value I don’t recognize at some point after I run my CloudFormation template:
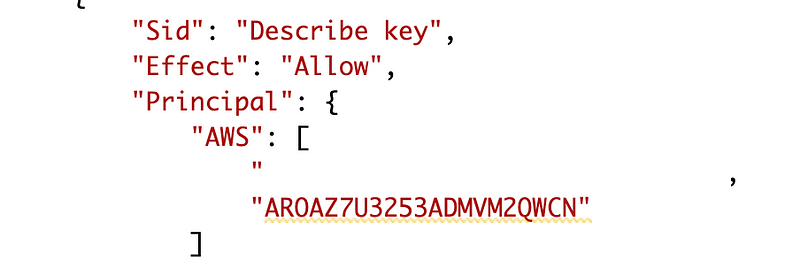
Update: I figured out what causes this. I renamed a role using CloudFormation and essentially the role got deleted and re-added. When that happened the KMS policy changes to this strange value in place of the old role name.
If I run the CloudFormation template again it fixes the problem but I have to delete the exist template first.
It would be more helpful if the error message stated that the KMS policy has an invalid value in it. That would cause the user to check the KMS policy. It also be more helpful if you could lave the role name but prepend it with “DELETED” instead of using that strange value to make it clear why the template was updated.
CloudFormation has a bug in this case because it doesn’t recognize that the policy is updated and so it doesn’t execute the template to redeploy the policy — which also could trigger a more relevant error such as the principal passed into the policy does not exist. “Does not exist” is more meaningful than “is Invalid.”
However, that above issue is not the only cause. I am now looking at a policy that seems to be correct and getting the error and struggling to find the issue. The key policy allows the role that is trying to perform the action to encrypt. The user that is assuming the role has apparently assumed it successfully because other non-KMS actions were executed successfully. This KMS error needs more information to help users pinpoint the problem.
Initially I had a hard time finding the error messages related to this but figured it out. I had hoped that looking in CloudTrail would provide more useful information.
As it turns out the error messages did finally show up. The one for Secrets Manager which is using the Key is very unhelpful:

The next error message is very strange. It says that the role is not authorized to DECRYPT. This role should not be decrypting anything and neither should Secrets Manager. I am encrypting some values I’m storing in Secrets Manager. Well if this error message bubbled up appropriately in CloudFormation it would be more helpful but either my code is incorrect or there’s an AWS bug here.

Here’s another one:
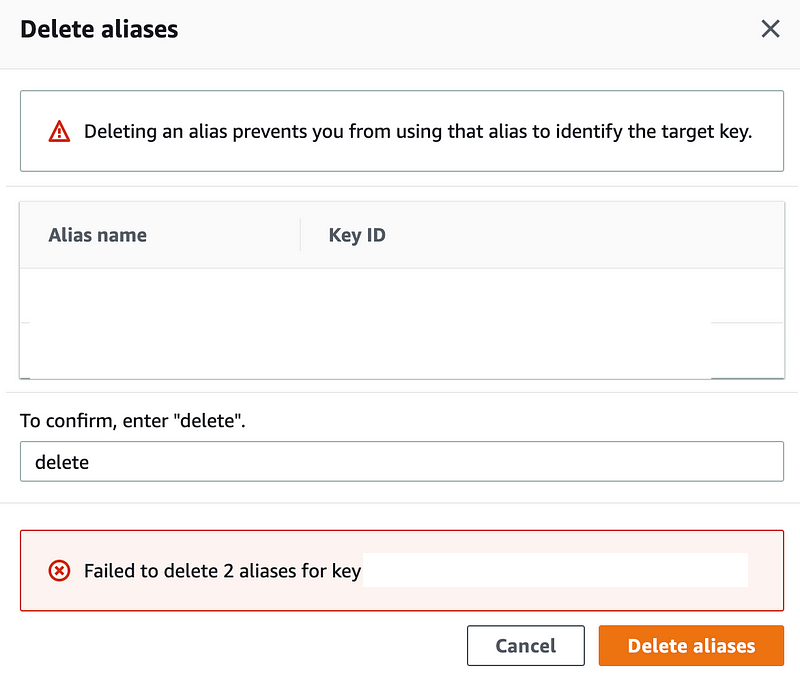
I happen to know this user does not have permission but if I didn’t that error message would be very frustrating because it doesn’t say why you cannot delete the alias.
This error is helpful, but I have a question. Why does the above screen not include “alias/” in the name and why do I even need to put “/alias” in any command, name or CloudFormation. Can’t you just add that behind the scenes if required and not present? Would be a bit more user-friendly.

Follow for updates.
Teri Radichel | © 2nd Sight Lab 2022
About Teri Radichel:
~~~~~~~~~~~~~~~~~~~~
⭐️ Author: Cybersecurity Books
⭐️ Presentations: Presentations by Teri Radichel
⭐️ Recognition: SANS Award, AWS Security Hero, IANS Faculty
⭐️ Certifications: SANS ~ GSE 240
⭐️ Education: BA Business, Master of Software Engineering, Master of Infosec
⭐️ Company: Penetration Tests, Assessments, Phone Consulting ~ 2nd Sight LabNeed Help With Cybersecurity, Cloud, or Application Security?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
🔒 Request a penetration test or security assessment
🔒 Schedule a consulting call
🔒 Cybersecurity Speaker for PresentationFollow for more stories like this:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
❤️ Sign Up my Medium Email List
❤️ Twitter: @teriradichel
❤️ LinkedIn: https://www.linkedin.com/in/teriradichel
❤️ Mastodon: @teriradichel@infosec.exchange
❤️ Facebook: 2nd Sight Lab
❤️ YouTube: @2ndsightlab